
Welcome to this week’s edition of the Threat Source newsletter.
I have no idea how “Fortnite” keeps coming up in this newsletter, but here we are again.
Even though the game/metaverse has never been bigger, it had been a while since I had heard about “V-Bucks” scams. V-Bucks are the in-game virtual currency “Fortnite” uses to sell character skins and other visual elements.
After the game’s initial surge in popularity, scams claiming to get players easy V-Bucks were all over the place in the form of fake advertisements, phishing emails, scams and YouTube videos. And as the game has only become more ubiquitous, so have scams and cyber attacks centered around the game.
Wired reported last week that a central network of bad actors is responsible for compromising legitimate domains (some of them with the .gov and .edu top-level domains) and using them to trick players into sharing personal information or downloading malicious apps. This widespread campaign targets players of “Fortnite” and “Roblox,” another half-game, half-metaverse.
These compromised sites promised to send rewards in these games to players in exchange for clicking on a link, downloading a file or filling out a form.
This led me down another rabbit hole of potential Fortnite scams that I hadn’t thought about, which are the thousands of knockoffs that exist.
For some reason, just searching “Fortnite” on the Google Play store doesn’t return any results, but when you search “Fortnite game,” users are served with tons of apps of questionable origin and legitimacy. The real “Fortnite” can only be downloaded from the Epic Games Store, owned by the game’s publisher and the subject of a long legal saga with Apple.
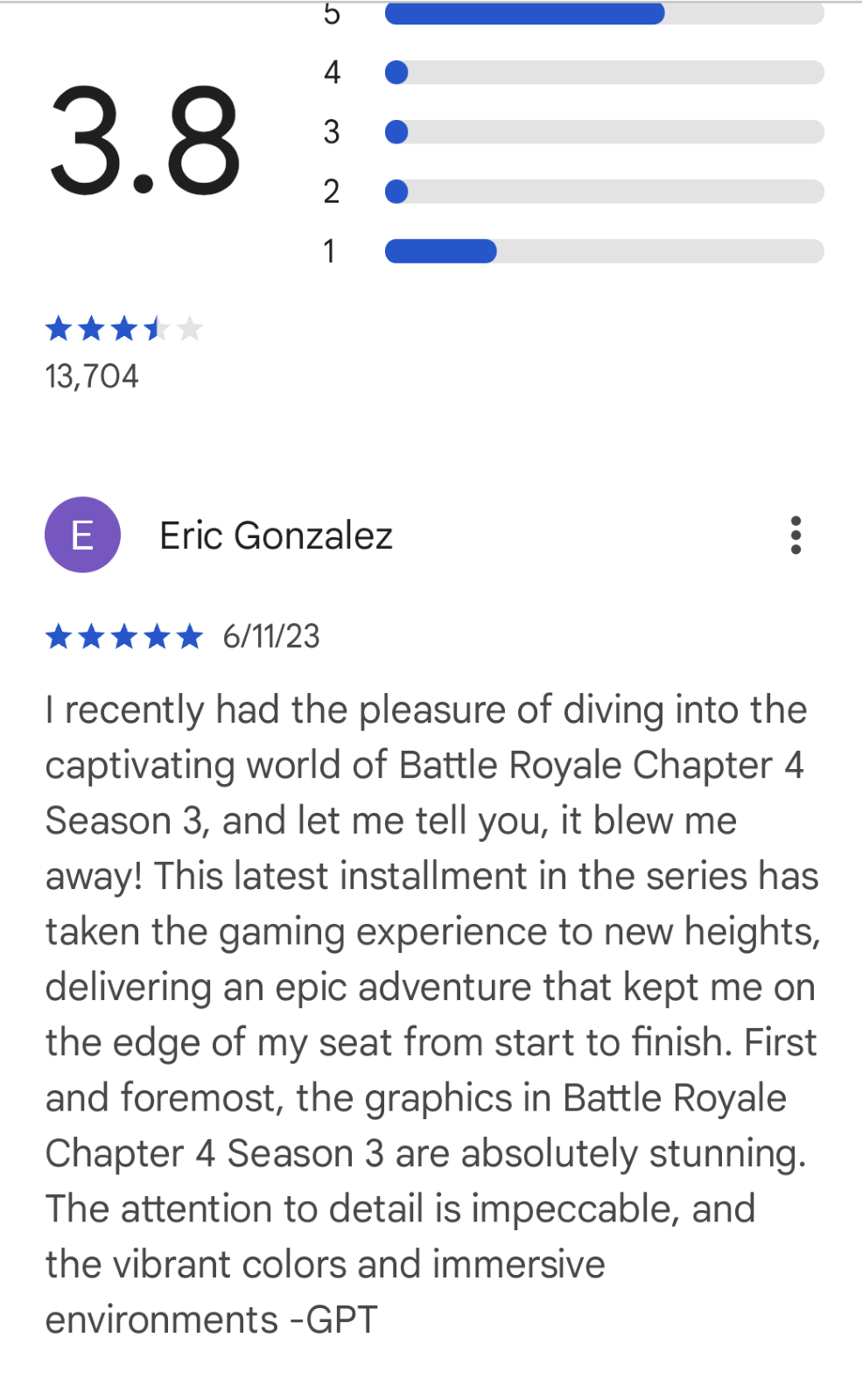
The second-most-popular result for “Fortnite game” is something called “Battle Royale Chapter 4 Season3” published on the store by the auspiciously named “EPic Games,” which wreaks of the same vibes as a typosquatted domain.
Some of the top reviews for the app also seem to be written by bots, and in one case, the most recent 5-star review came from a user who appeared to credit ChatGPT with writing the text.
I’m not blaming anyone or any company for the existence of these types of scams, I just think it’s worth noting to parents and potential players that bad actors are still trying to backpack off the popularity of these games. It likely doesn’t fall on the companies making these games to regulate this space and make sure scammers aren’t capitalizing off their popularity — after all, no one blames the bank if an attacker uses their name in a phishing email to steal login credentials.
But I also don’t know who it falls to, either. As users, it again falls on us to just be hyper-vigilant and prepared, knowing attackers will try to leverage anything, even fake money used to buy virtual hot dog suits, to scam people.
The one big thing
The infamous Lazarus Group APT is back at it again with two new remote access trojans. The North Korean state-sponsored group is well known for using a variety of malware to generate revenue for the hermit government and trying to spy on their various adversaries. Now, they have two new RATs that Talos recently discovered, largely based on open-source tools or previously leaked malware code. Lazarus Group is increasingly using the Qt framework to create their malware, which poses new challenges for defenders. It increases the complexity of the malware’s code, making human analysis more difficult.
Why do I care?
Any time the Lazarus Group is active, everyone should take notice. This is one of the most high-profile APTs on the threat landscape right now, and they’ve shown that they will not hesitate to exhaust all options to try to generate money for North Korea’s government. With this specific set of RATs, they are smaller than Lazarus’ usual payloads, which makes their operations slimmer, faster and harder to detect. Once infected, Lazarus Group can carry out a wide range of malicious actions on targets, ranging from deploying ransomware to completely lock down targeted machines, stealing personal information, or hijacking hardware for cryptocurrency mining.
So now what?
Both the blogs we published Thursday morning include guidance on remediating these threats. The use of open-source tooling can sometimes make it easier for security researchers to spot Lazarus Group activity, and in the case of the two new RATs, Talos has a wide range of Snort and ClamAV detection available.
Top security headlines of the week
The FBI warned that North Korean state-sponsored actors are preparing to cash out up to $40 million worth of cryptocurrency after multiple heists. The Lazarus Group reportedly is holding onto six separate crypto wallets holding a combined 1,580 Bitcoin over the course of 24 hours earlier this week. This APT is known for carrying out data breaches and cyber attacks to generate funding for the country’s illegal nuclear weapons program. The Lazarus Group previously stole $60 million and $37 million in cryptocurrency from Alphapo and CoinsPaid, respectively, in July, and $100 million from Atomic Wallet in June. In its alert, the FBI shared the Bitcoin addresses associated with the attacks so cryptocurrency agencies could examine their blockchain data and “be vigilant in guarding against transactions directly with, or derived from the addresses.” (TechCrunch, SecurityWeek)
A previously unknown hacking group appears to be behind a supply chain attack targeting roughly 100 computers located in Hong Kong and other areas of Asia. Security researchers attributed the attack to a new actor known as “Carderbee” that is currently not tied to any state affiliations. The attackers exploited the legitimate Cobra DocGuard software — made by a Chinese software company — to deliver a malicious software update that compromised the machines. Because only about 2,000 machines worldwide use DocGuard, researchers believe it is a highly targeted attack looking to compromise specific victims. Each attack tried to deploy the Korplug (the predecessor of PlugX) backdoor onto victim computers. (CyberScoop, The Record by Recorded Future)
The Clop threat actor was responsible for more than a third of all ransomware attacks in July, according to multiple industry reports. Clop continues to carry out follow-on attacks associated with its massive breach of the MOVEit file transfer software. More than 4 million Colorado residents may have been affected because of the MOVEit breach, with the state’s Department of Health Care Policy & Financing (HCPF) disclosing this week that it was affected through a technology partner, IBM. HCPF stated that the MOVEit data breach leaked sensitive data but did not compromise the state agency’s internal systems. As of this week, some estimates state that more than 730 organizations have been affected by the MOVEit breach. (Cybersecurity Dive, CPO Magazine)
Can’t get enough Talos?
- Talos Takes Ep. #151: Hacktivism is quietly growing, especially when it comes to Russia’s invasion of Ukraine
- Three vulnerabilities in NVIDIA graphics driver could cause memory corruption
- Generating FLIRT signatures for Nim and other non-C programming languages
- Cisco: Bringing More Intelligence to Bear on the Threat Landscape
Upcoming events where you can find Talos
LABScon (Sept. 20 - 23)
Scottsdale, Arizona
Vitor Ventura gives a presentation that’s a detailed account and timeline of one such mercenary organization, from almost bankrupt to having a fully working spyware targeting iOS and Android with a one-click zero-day exploit.
Grace Hopper Celebration (Sept. 26 - 29)
Orlando, Florida
Caitlin Huey, Susan Paskey and Alexis Merritt present a “Level Up Lab” titled “Don’t Fail Knowledge Checks: Accelerating Incident Response with Threat Intelligence.” Participate in several fast-paced activities that emphasize the importance of threat intelligence in security incident investigations. Attendees will act as incident responders investigating a simulated incident that unfolds throughout this session. Periodic checkpoints will include discussions that highlight how incident response and threat intelligence complement each other during an active security investigation.
ATT&CKcon 4.0 (Oct. 24 - 25)
McLean, Virginia
Nicole Hoffman and James Nutland discuss the MIRE ATT&CK framework in “One Leg to Stand on: Adventures in Adversary Tracking with ATT&CK.” Even though ATT&CK has become an industry standard for cyber threat intelligence reporting, all too often, techniques are thrown at the bottoms of reports and blogs without any context never to be seen again after dissemination. This is not useful for intelligence producers or consumers. In this presentation, Nicole and James will show analysts how to use ATT&CK as a guideline for creating a contextual knowledge base for adversary tracking.
Most prevalent malware files from Talos telemetry over the past week
SHA 256: 24283c2eda68c559f85db7bf7ccfe3f81e2c7dfc98a304b2056f1a7c053594fe
MD5: 49ae44d48c8ff0ee1b23a310cb2ecf5a
Typical Filename: nYzVlQyRnQmDcXk
Claimed Product: N/A
Detection Name: Win.Dropper.Scar::tpd
SHA 256: a31f222fc283227f5e7988d1ad9c0aecd66d58bb7b4d8518ae23e110308dbf91
MD5: 7bdbd180c081fa63ca94f9c22c457376
Typical Filename: c0dwjdi6a.dll
Claimed Product: N/A
Detection Name: Trojan.GenericKD.33515991
SHA 256: 9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
MD5: 2915b3f8b703eb744fc54c81f4a9c67f
Typical Filename: VID001.exe
Claimed Product: N/A
Detection Name: Win.Worm.Coinminer::1201
SHA 256: 4c3c7be970a08dd59e87de24590b938045f14e693a43a83b81ce8531127eb440
MD5: ef6ff172bf3e480f1d633a6c53f7a35e
Typical Filename: iizbpyilb.bat
Claimed Product: N/A
Detection Name: Trojan.Agent.DDOH
SHA 256: 5e537dee6d7478cba56ebbcc7a695cae2609010a897d766ff578a4260c2ac9cf
MD5: 2cfc15cb15acc1ff2b2da65c790d7551
Typical Filename: rcx4d83.tmp
Claimed Product: N/A
Detection Name: Win.Dropper.Pykspa::tpd
Article Link: Years into these games’ histories, attackers are still creating “Fortnite” and “Roblox”-related scams