IBM X-Force Incident Response and Intelligence Services (IRIS) identified malicious actors using the FrameworkPOS and GratefulPOS malware to harvest massive amounts of payment card data from point-of-sale (POS) systems in 2017 and 2018. Based on the alignment of tactics, techniques and procedures (TTPs) with those previously identified in similar attacks, X-Force IRIS assessed that the cybergang known as FIN6, which was first identified in April 2016, is behind the attack. This is only the second time that FIN6 activity has been publicly documented and attributed to the group since FireEye’s initial discovery in 2016.
Our team also identified several additional TTPs that will help organizations identify and respond to FIN6 attacks. Let’s take a closer look at FIN6’s history, tactics and indicators of compromise (IoCs) and outline actionable intelligence to assist in strengthening defenses against this threat actor.
Who Is FIN6?
FIN6 is an organized gang of cybercriminals that specializes in stealing payment card data from organizations in the retail and hospitality sectors. The group has stolen data on millions of payment cards, which it then monetized by selling the information on the dark web. While it is unclear how much money FIN6 has made in this manner, we estimate the group’s profit to be in the millions of dollars from 2015 to 2018.
FIN6 targets organizations that process a significant number of POS transactions, such as retail outlets and hotels. It typically uses commercial POS malware to harvest payment card data. According to data on the group’s activity, its focuses on retailers in the U.S. and Europe.
Attribution: Why FIN6?
According to X-Force IRIS research, the recent activity we observed on POS machines is attributable to FIN6, based on an alignment of over 90 percent of the TTPs our team observed with TTPs previously attributed to FIN6 activity.
In addition to commonalities with past TTPs, we observed FIN6 employing additional tactics, such as leveraging IT management software to deploy malware and using Windows Management Instrumentation Command (WMIC) to automate the remote execution of PowerShell commands and scripts.
While many of the TTPs associated with this threat group are publicly available and widely used, either individually or in small groupings, the strong correlation between observed activity and alignment of specific behavior patterns led us to make the attribution.
New TTPs Observed in This Investigation
Our investigation identified TTP’s that were not previously attributed to FIN6. Of these, we consider the following to be among the most noteworthy:
- Deploying the FrameworkPOS malware via an enterprise software deployment application.
- Using WMIC to automate the remote execution of PowerShell commands and scripts.
- Metasploit-like behavior:
- Randomly generating service names in Windows event logs associated with service installations and service starts or stops (7035, 7036, 7045, etc.).
- Dynamically generating file names for binaries on disk (usually a backdoor installed as a service).
- Dynamically generating hostnames in event logs.
- Injecting malicious Meterpreter code into legitimate Windows processes.
- Obfuscating PowerShell commands with base64 encoding and gzip compression (often base64-encoded, gzip compressed, base64-encoded PowerShell script).
- Exclusion of specific processes for FrameworkPOS targeting.
- Filename of memsniff_dll.dll for Framework POS.
- Using a winhlp.dat file as a cover file name for a malicious PowerShell script designed to inject FrameworkPOS into “lsass.exe.”
- Using specific PowerShell parameters to attempt to avoid detection and bypass antivirus application whitelisting.
- Using “1.txt”, “services.txt” and “.csv” files as reconnaissance output names.
While some of these TTPs may be side effects of tools FIN6 actors were using or specific to the environment in which the actors were operating, we believe many represent new TTPs that could become characteristic of evolved FIN6 standard operating procedures.
Of the TTPs that aligned with previously identified FIN6 activity, the most notable include:
- Widely deploying FrameworkPOS on compromised POS systems;
- Collecting compromised data in numbered “.dll” files;
- Extensive use of Metasploit and PowerShell to move laterally and deploy malware;
- Frequent use of Windows Scheduled Tasks to maintain persistence;
- Heavy SQL database reconnaissance and data theft;
- Using Secure Shell (SSH) tunnels for SQL database exfiltration;
- Compromising the Active Directory Database (ntds.dit), allowing for credential harvesting and password cracking offline; and
- Using a specific Metasploit-like downloader that generates a random 15-character filename. It is possible this is the SHIPBREAD or HARDTACK downloader previously attributed to FIN6’s use.
FIN6 Returns to the POS Attack Arena
In the recent activity investigated by X-Force IRIS, the FIN6 gang demonstrated its ability to gain systemic footholds in targeted networks, advance laterally and eventually achieve its objective of exfiltrating valuable data from the victim organization’s infrastructure.
FIN6’s Easy Does It: Unsophisticated Yet Effective
FIN6 uses a variety of publicly available tools for reconnaissance and lateral movement. For example, it deploys the FrameworkPOS malware for the phase of harvesting payment card data from POS endpoints’ memory.
Most of FIN6’s tools are either simplistic or publicly available, and the group’s encoding mechanisms are relatively easy to decipher. The malware used to steal the card data is available commercially on dark web markets. While it might seem that the group is not highly sophisticated, this is not the case.
FIN6’s skill lies in its ability to bypass security controls and employ stealthy techniques, which allows the group to steal large amounts of data and sell at least some of it for a profit in dark web markets.
X-Force IRIS’s investigation into the destination of the stolen cards harvested by FIN6 found that the group most likely used the dark web forum Joker’s Stash to advertise and collect payments for batches of credit card data. Various reports on the value of payment card data on the dark web estimate the price of a newly stolen card at about $20 per card.
Breach and Internal Reconnaissance
Available evidence did not conclusively confirm how FIN6 gained the initial access to systems it compromised, although previous publications on its techniques noted that the group appears to use legitimate login credentials. The use of these credentials — either stolen or bought — is a plausible scenario in this case.
Once within an environment, FIN6 uses several reconnaissance techniques to locate the data it wishes to exfiltrate. In particular, X-Force IRIS observed the group running WMIC queries, which were then used to automate the remote execution of PowerShell commands and scripts, among other functions designed to run queries, search databases, access directories and connect to systems of interest.
We observed the attackers extensively targeting internal SQL databases during the attack. They then dumped the database’s contents using output filenames that were often named “1.txt” and “services.txt” for reconnaissance on the processes and services running on the system, as well as various .csv files for database tables.
In addition, the attackers compromised the majority of domain controllers in the environments they accessed and probably collected the Active Directory Database (ntds.dit), which would provide access to password hashes that they could then crack offline or attempt pass-the-hash attacks to expand their access and privilege levels.
Lateral Movement
To move laterally inside the breached networks, the attackers made extensive use of PowerShell and Metasploit throughout their operation.
To avoid detection and bypass antivirus application whitelisting, the attackers used PowerShell scripts with parameters such as:
The “-w hidden” and “-noni” parameters prevent PowerShell windows from popping up on victim systems or accepting any interaction, while “-ep bypass” allows PowerShell scripts to run even on systems that limit PowerShell use.
In addition, FIN6 used PowerShell to create backdoors by leaving a running PowerShell process on a system with a base64 encoded payload. The attackers then used SSH and Remote Desktop Protocol (RDP) for access and lateral movement.
The Metasploit framework was another favorite tool in the FIN6 arsenal, probably selected for several purposes, including creating backdoors that downloaded or listened on a particular port for shellcode to execute.
X-Force IRIS observed FIN6 using Metasploit to inject the Meterpreter payload into legitimate Windows processes, including “services.exe” and “WinLogon.exe.” We also observed several examples of the actors using Metasploit modules for lateral movement within the environment.
POS Malware Deployment
Once the attackers identified POS systems in the target environment, they deployed the FrameworkPOS malware as well as its variant, GratefulPOS, on those systems. In some cases, the actors employed an enterprise software deployment application to place the malware on a system.
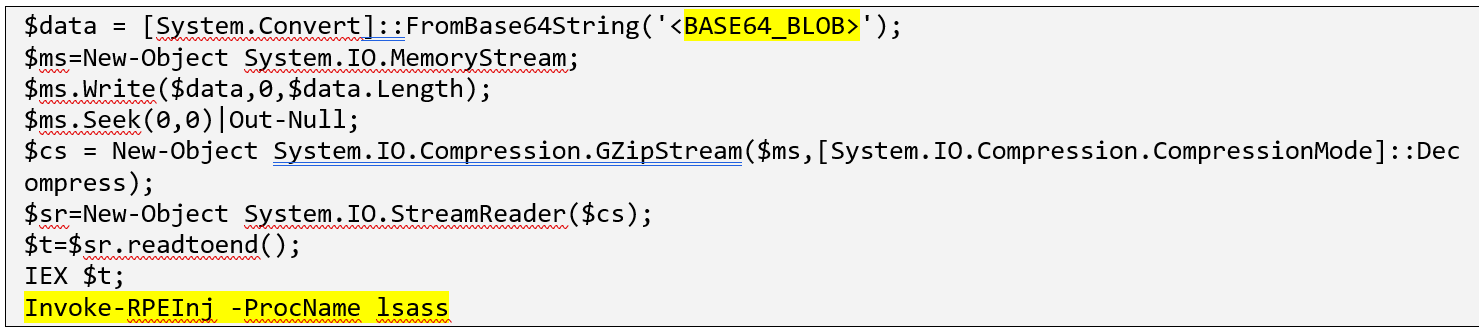
The attackers deployed the FrameworkPOS malware with its original filename, “memsniff_dll.dll.” Our forensic experts observed the actors using the name “winhlp.dat” for a PowerShell script that injected FrameworkPOS into the “lsass.exe” process, using a component of the PowerSploit framework.
The contents of the file “winhlp.dat” shown in the figure below revealed that the attackers were running a base64-encoded instruction set within PowerShell to inject the FrameworkPOS malware into the lsass.exe process via Invoke-RPEInj.
Figure 1: Contents of winhlp.dat file
To evade detection by antivirus solutions, which may only look for malware on the disk, the instructions were converted into a memorystream, compressed, injected and then eventually executed into the “lsass.exe” memory space. It is also worth noting that Invoke-RPEInj, or Invoke-ReflectivePEInjection, is a PowerSploit module that injects an executable into a PowerShell or remote process.
Find and Amass Card Data
FrameworkPOS’s functionality has been well-documented in existing security literature, and most of what we observed with this malware aligns with previous observations about it.
Once executed on the system, FrameworkPOS searched running processes for track 1 and track 2 payment card data, and then wrote a string (<machineIPAddress>;<;MachineName>;runOK64) to a log file called “Perflib_perfdata_f44.dat” in “%WINDIR%\temp” on the POS terminal.
When writing data, the malware marked track 1 data with tt1 and track 2 data with tt2. The malware also used a simple XOR encoding mechanism to obfuscate the payment card information.
Of note, the FrameworkPOS malware targets all running processes — with the exception of the process it is injected into. It will further ignore processes with fewer than five characters of module path and processes with the following names:
Figure 2: List of hardcoded processes where FrameworkPOS does not search for payment card data
Data Exfiltration
To exfiltrate the stolen data, the attackers employed scheduled tasks with innocuous names such as “WindowsSys” from compromised servers to collect and put the data into numbered .dll files.
Previous studies have detailed FrameworkPOS’s use of Domain Name System (DNS) tunneling for data exfiltration, and the 2016 attribution of FIN6 noted that the group had used FTP command lines for exfiltration. X-Force IRIS did not observe a particular exfiltration methodology in the cases we researched; however, we consider DNS tunneling to be a plausible method based on tactics used by other groups that operate the FrameworkPOS malware.
Similar to previous cases in which the GratefulPOS variant was used, we observed communications with a command-and-control (C&C) domain the malicious actors created to appear as a legitimate security vendor’s website. Once we identified the domain in the samples we analyzed, we sinkholed it to help prevent further criminal use.
Attack Flow Illustration
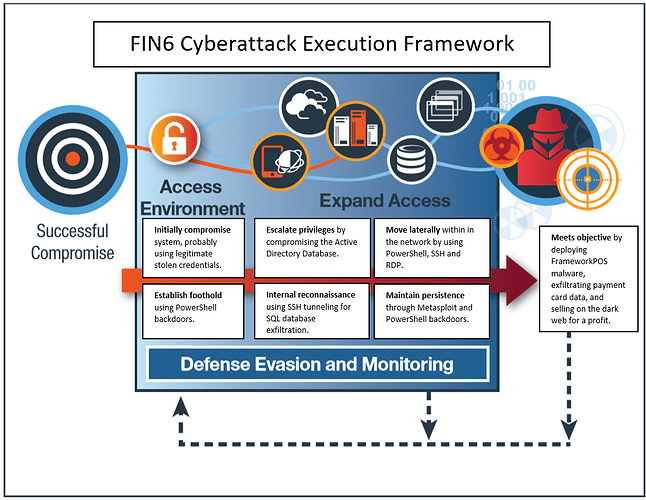
The graphic below illustrates FIN6’s attack flow according to the activity X-Force IRIS observed. This attack behavior corresponds with the steps X-Force IRIS observed and are characteristic of most attackers. This is illustrated in more detail in our Cyberattack Preparation and Execution Frameworks, which were released in July 2018.
Figure 3: X-Force IRIS observed FIN6 activity establishing a foothold in the environment, escalating privileges, moving laterally, conducting internal reconnaissance, maintaining persistence and meeting its objective by exfiltrating payment card data.
Dig Deeper to Enhance Defenses
FIN6’s skill at acquiring legitimate login credentials, bypassing antivirus systems, and quietly exfiltrating data on millions of credit cards underscores the value of digging deeper into threat data to identify and eradicate potential POS malware. Basic antivirus services are unlikely to provide sufficient protection against cybercriminal groups who specialize in POS Malware operations, particularly in high-risk verticals such as the retail sector.
By continuing to track and share the TTPs of POS malware groups, X-Force IRIS aims to identify additional security measures to help organizations mitigate the threat to both their networks and their valued customers.
To help lower the risk of mass credit card data theft from POS machines, organizations that deploy point-of-sale endpoints can consider the following security practices:
- Decrease the potential for login credential theft by enhancing employee education of credential harvesting techniques, ensuring robust physical security, employing software to detect phishing emails and implementing a strong password policy.
- Allow Domain Administrator accounts for POS systems to interact only with Domain Controllers to segregate these accounts from internet-facing systems and reduce their risk of credential compromise.
- Use additional segregation techniques to isolate POS systems from the rest of the network, including firewalls and separate login accounts for authorized users.
- Strictly limit the number of individuals with access to the POS portion of the network based on job duty and necessity. Implement careful audit logging and multifactor authentication (MFA).
- Harden internet-facing systems by disabling unused ports, unused accounts and other functionalities not necessary for system operations.
- Whitelist processes and not just applications, such as allowing the execution of only signed PowerShell scripts.
- Employ threat hunting to proactively discover advanced threats that often evade traditional detection techniques.
- Follow threat intelligence on the POS malware threat and incorporate up-to-date IoCs into internal security mechanisms to improve the likelihood of identifying known FIN6-related activity on the network.
- Contract periodic penetration testing services for both software and hardware of the POS installations used across the business.
Indicators of Compromise
Below are the indicators of compromise (IoCs) associated with this attack.
File Hashes and File Size
-
First Stage PowerShell Script
- MD5 : 0d30c2748e70246acbfa726e9d5ae289
- SHA1 : 3fc9c9826a454bb121787f6b5b8849cf323e93ba
- SHA256 : 3e745df7511308b18bab51a08e929bbf96aa69df91c077497db33a6390b09493
- Size : 354,391 bytes
-
Second Stage PowerShell Script
- MD5 : b793c45911b99f6bb1be8cb6e9403e7a
- SHA1 : 98aab54447f182f98d4c2f1a71162dabd62189f2
- SHA256 : 864af4f3e9e9e77bfcc443fcacd1a478c511fd997cd4b76a937e6903ce8a8c02
- Size : 1,050,557 bytes
-
FrameworkPOS Malware (32bit)
- MD5 : b8dfbdd7b8d23295bb800804ec8d5fe6
- SHA1 : a493c58aa8b931bbc9dd6f2919e47aac89d8e590
- SHA256 : 81e870caebc9b4e6e886a9bb0c9c03c117275c9bf377fd6d9fa3f1fa15cb29e4
- Size : 111,104 bytes
-
FrameworkPOS Malware (64bit)
- MD5 : 964f6b08a5bd0c4455262b20e07cb4b7
- SHA1 : 0ae937fdb26b08e3878c0301676329f7189bcb8e
- SHA256 : 3d9ef7a0a768aff27301606b60d72b6c43f06f2003f81f477b8163a82183ffed
- Size : 133,632 bytes
-
GratefulPOS
- MD5 : 117df747e05bfcf5b522de28b8d0193a
- SHA1 : 4828103a4e37442a54376d92e852029def2a661e
- SHA256 : 60b2d56e71cfb46ec98576eaa5f8d5649fd73bfa792c9e8412b70dfc8bb97bde
- Size : 155,136 bytes
-
Shellcode Loader (via an open TCP port)
- MD5 : 93c1efc5ae0932cdbf89778d4414168c
- SHA1 : 01c40a7b571ea8452cab9009802f93a1bb22a3f1
- SHA256 : f5c7910327299ca1fdb8cfe6e56f4e978964207730318e08fb0c17ea29417803
- Size : 115,200 bytes
-
Downloader
- MD5: d07592865f601d5238535fc4500479b7
- SHA1: 22d665e25cd00d3d16b0b97b040d74d40ec75be3
- SHA256: fde15da4af0e966bba2988dbeb7787f4547a7338054053bb532c82ce275b88fc
- Size: 128,730 bytes
-
Stager Shellcode
- MD5: 316c9547c7568b8c8b77642aa06b533c
- SHA1: d338285aabbb15e3efa802eed1bac16cb4451a07
- SHA256: 506c9c7817409c9706f100d1bf2d24862bf1ea2ebb766c106d8d90fb03ee01a3
- Size: 471 bytes
-
Downloader
- MD5 : 117df747e05bfcf5b522de28b8d0193a
- SHA1 : 4828103a4e37442a54376d92e852029def2a661e
- SHA256 : 60b2d56e71cfb46ec98576eaa5f8d5649fd73bfa792c9e8412b70dfc8bb97bde
- Size : 155,136 bytes
File Information (Respectively)
- 1st Stage PowerShell Script: PowerShell script
- 2st Stage PowerShell Script: PowerShell script
- FrameworkPOS Malware (32bit): Win32 DLL
- FrameworkPOS Malware (64bit): Win64 DLL
- Shellcode Loader: Win32 EXE
- Downloader: Win32 PE
- Stager Shellcode: Binary blob
- Downloader: Win32 EXE, File name: bodvbhjg.exe
The post X-Force IRIS Identifies FIN6 Activity on POS Networks appeared first on Security Intelligence.
Article Link: https://securityintelligence.com/x-force-iris-identifies-fin6-activity-on-pos-networks/