In the ever-changing landscape of cybersecurity, staying updated with current vulnerabilities is crucial. The recent issues discovered in WS_FTP Server underscore this fact. In this article, we explore the details of these vulnerabilities, their possible consequences, and the suggested solutions.
Understanding the Vulnerabilities
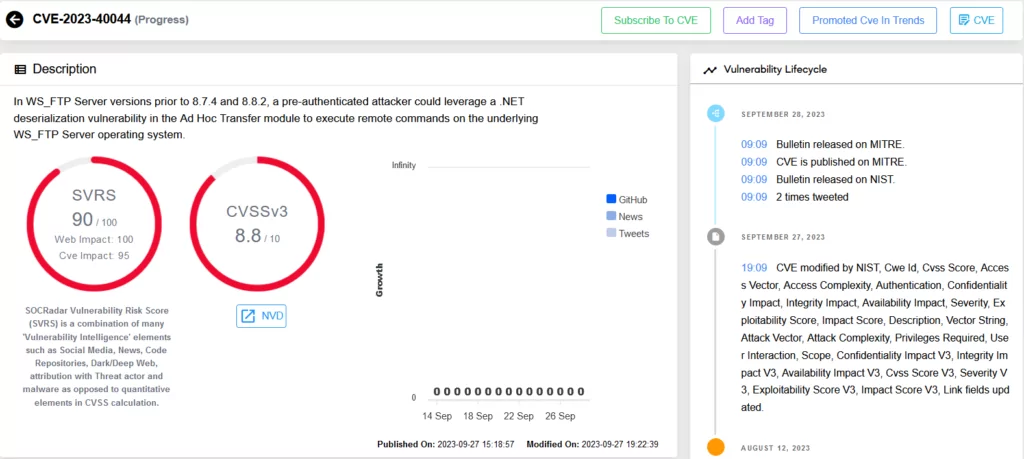 Vulnerability Intelligence page for CVE-2023-40044 in SOCRadar Platform.
Vulnerability Intelligence page for CVE-2023-40044 in SOCRadar Platform.
In September 2023, a slew of vulnerabilities affecting the WS_FTP Server came into light. The Progress WS_FTP team promptly acknowledged these security gaps and released corresponding patches. Let’s shed some light on the most severe of these vulnerabilities:
CVE-2023-40044
This is a severe .NET deserialization vulnerability in the WS_FTP Server Ad Hoc Transfer module. Exploiting this vulnerability would enable a pre-authenticated attacker to execute remote commands directly on the WS_FTP Server’s underlying operating system.
Affected Versions: Prior to 8.7.4 and 8.8.2
Severity:
- NIST CVSS score: 8.8 (High)
- Progress Software Corporation (CNA) score: 10.0 (Critical)
CVE-2023-42657
This vulnerability pertains to directory traversal. An attacker leveraging this could conduct file operations (like delete, rename, mkdir, etc.) on files and folders outside their authorized WS_FTP folder path. Moreover, the attacker could escape the WS_FTP Server file structure and operate on the underlying OS.
Affected Versions: Prior to 8.7.4 and 8.8.2
Severity: CVSS score of 9.9 (Critical)
Other Noteworthy Vulnerabilities
Apart from the above critical vulnerabilities, several other vulnerabilities were highlighted, including:
- CVE-2023-40045: Reflected XSS in the Ad Hoc Transfer module.
- CVE-2023-40046: SQL injection vulnerability in the WS_FTP Server manager interface.
- CVE-2023-40047: Stored XSS vulnerability in WS_FTP Server’s Management module.
- CVE-2023-40048: CSRF vulnerability in the WS_FTP Server Manager interface.
- CVE-2022-27665: Reflected XSS vulnerability in Progress Ipswitch WS_FTP Server 8.6.0.
- CVE-2023-40049: File enumeration vulnerability in ‘WebServiceHost’ directory listing.
Taking Action: Remedial Measures
The Progress WS_FTP team has released version-specific hotfixes. If you’re using the Ad Hoc Module and can’t update immediately, mitigation measures have been outlined here.
For the most comprehensive security, it is highly recommended to upgrade to the latest WS_FTP Server version, which is 8.8.2. The upgrade details and downloads are accessible via the Progress Community portal.
Staying Ahead with SOCRadar Vulnerability Intelligence
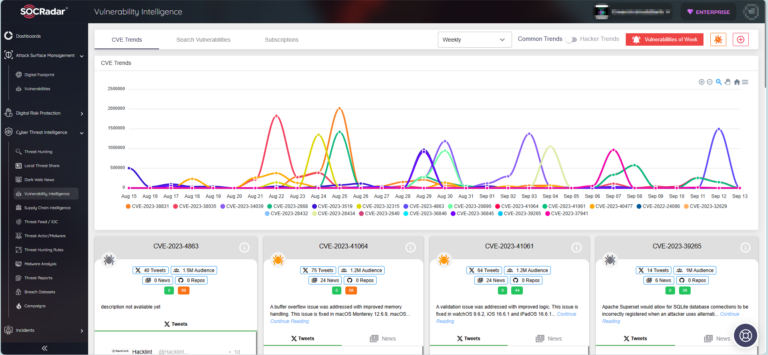 Vulnerability Intelligence module of SOCRadar Platform.
Vulnerability Intelligence module of SOCRadar Platform.
In an age of sophisticated cyber threats, staying updated with vulnerabilities is of paramount importance. Companies like SOCRadar, with its advanced Vulnerability Intelligence, empower businesses to stay ahead of potential threats. Utilizing such intelligence, businesses can timely identify, analyze, and remediate vulnerabilities, ensuring a more robust security posture. Don’t be reactive; be proactive!
The post WS_FTP Server Critical Vulnerabilities: What You Need to Know (CVE-2023-40044, CVE-2023-42657) appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: WS_FTP Server Critical Vulnerabilities: What You Need to Know (CVE-2023-40044, CVE-2023-42657)
