AMSI : Anti-Malware Scan Interface
AMSI (Anti-malware Scan Interface) is a flexible interface standard that enables your applications and services to work with any anti-malware product installed on a machine. Microsoft launched it in 2015 to offer a standard interface for solutions to scan files, memory, and other data for malware. AMSI is part of various components of Windows 10, such as User Account Control, PowerShell, Windows Script Host, JavaScript, VBScript, and Office VBA macros. As an application developer, you can join the fight against malware by using AMSI to scan script content for possible threats before running it. This adds an extra level of security for the system.
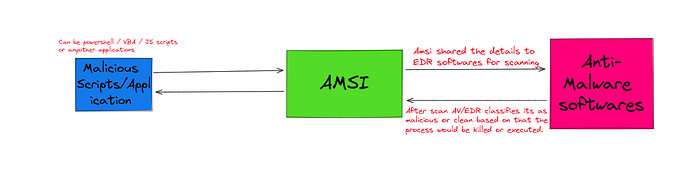 Simple working of AMSI in windows
Simple working of AMSI in windowsAnalyzing Malicious JS file via AMSI
For our analysis we will user a tool named “Logman” which is developed by microsoft which is a built-in tool for handling ETW and Event Tracing Sessions.
As a example , we are analyzing a JS script which is being propagated as secure document via phishing campaigns.
 Malicious site hosting malicious JS file.
Malicious site hosting malicious JS file.Upon clicking on download a JS file would be download , upon review in notepad we see that the file highly obfuscated.
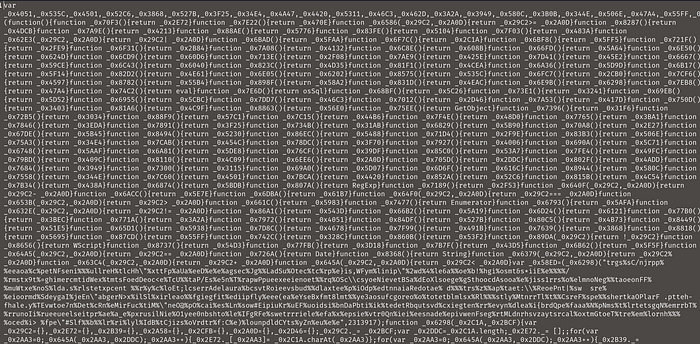 Obfuscated JS file
Obfuscated JS fileOne method is to sit and manually de-obfuscate the entire code , but this process would take a eternity. As AMSI can be used in scanning of JS files hence we will leverage its logs to review this file. Then we spawn a powershell as administrator and run the below command to start logging in AMSI logs.
logman start AMSITrace -p Microsoft-Antimalware-Scan-Interface Event1 -o AMSITrace.etl -ets
Once we sucessfully execute our payload and we stop the logging with below command.
logman stop AMSITrace -ets
As the logs are stored in file named “AMSITrace.etl” which is of type etl we use a script written by “mattifestation/AMSIScriptContentRetrieval.ps1”. below is a snip of the logs.
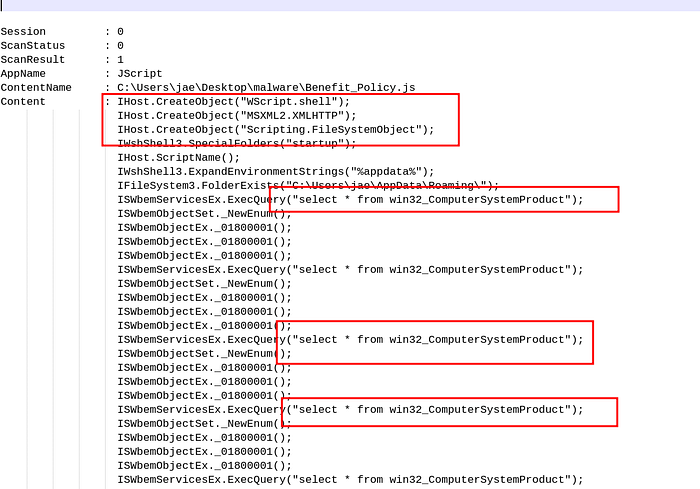 AMSI Scan Logs
AMSI Scan LogsAs Highlighted above we see that the malware is performing activities such as searching for startup and AppData folder which would be used for persistence. We also see activities w.r.t to WMI for enumerations. Also we see persistence via registry
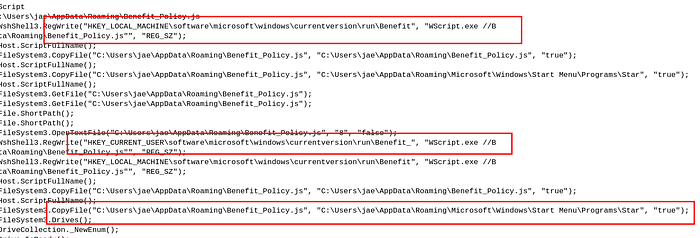 Registry based persistence
Registry based persistenceFurther reviewing logs , we also see connection to C2C server which was down during the time of analysis. Also we see that the malware trying to communicate (share data) in User-Agent field in the headers.
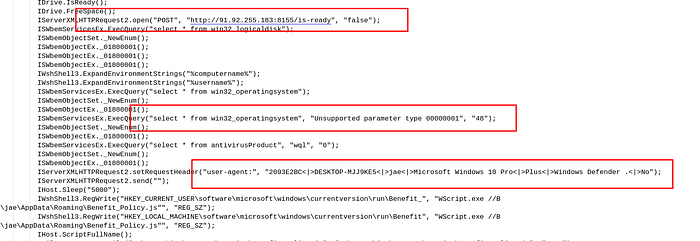 Connection to C2C and Data ex-filtration over User-Agent.
Connection to C2C and Data ex-filtration over User-Agent.Using AMSI is a better approch to understand what a malware is doing rather than deobfucation it manually. But the down side of this is that it requires execution of the malware.
Windows Security: Using AMSI to Analyze Malicious JavaScript was originally published in InfoSec Write-ups on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: Windows Security: Using AMSI to Analyze Malicious JavaScript | by JustAnother-Engineer | Feb, 2024 | Medium