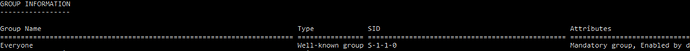SID is one of the core data structures in the NT security infrastructure
A Security Identifier (commonly abbreviated SID) is a unique, immutable identifier of a user, user group, or other security principal.
A security principal has a single SID for life (in a given domain), and all properties of the principal, including its name, are associated with the SID.
This design allows a principal to be renamed (for example, from “Jane Smith” to “Jane Doe”) without affecting the security attributes of objects that refer to the principal.
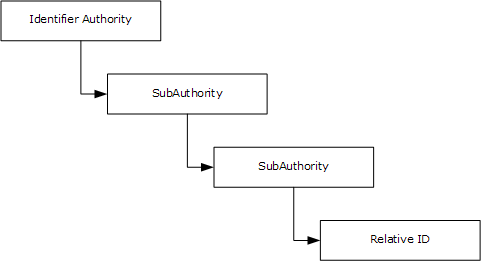
The SID is variable in length and encapsulates the hierarchical notion of issuer and identifier.
It consists of a 6-byte identifier authority field that is followed by one to fourteen 32-bit subauthority values and ends in a single 32-bit relative identifier(RID).
When displayed textually, the accepted form is the following:
S-1-<identifier authority>-<sub1>-<sub2>-…-<subn>-<rid>
where S and 1 are literal strings, identifier authority is the 6-byte value, sub1 through subn are the subauthority values, and rid is the RID.
The IdentifierAuthority is an array of 6 bytes, which describes which system “owns” the SID.
NT defines 6 IdentifierAuthorities, they are:
- SECURITY_NULL_SID_AUTHORITY: The NULL Sid authority is used to hold the “null” account SID, or S-1–0–0.
- SECURITY_WORLD_SID_AUTHORITY: The World Sid authority is used for the “Everyone” group, there’s only one SID in that group, S-1–1–0.
- SECURITY_LOCAL_SID_AUTHORITY: The “Local” Sid authority is used for the “Local” group, again, there’s only one SID in that group, S-1–2–0.
- SECURITY_CREATOR_SID_AUTHORITY: This Sid authority is responsible for the CREATOR_OWNER, CREATOR_GROUP, CREATOR_OWNER_SERVER and CREATOR_GROUP_SERVER well known SIDs, S-1–3–0, S-1–3–1, S-1–3–2 and S-1–3–3.
- SECURITY_NON_UNIQUE_AUTHORITY: Not used by NT
- SECURITY_RESOURCE_MANAGER_AUTHORITY: The resource manager authority is a catch-all that’s used for 3rd party resource managers.
- SECURITY_NT_AUTHORITY: Describes accounts that are managed by the NT security subsystem.
There are literally dozens of well known SIDs under the SECURITY_NT_AUTHORITY sub authority.
They range from NETWORK (S-1–5–2), a group added to the token of all users connected to the machine via a network, to S-1–5–5-X-Y, which is the SID for all authenticated NT users.
For more information, please refer to this article:
RID is a Relative IDentifier. Relative to the SID that is. The RID is the last part and should be unique for a certain object within a domain.
Windows allocates RIDs starting at 1,000.
RIDs having a value less than 1,000 are considered reserved and are used for special accounts.
For example, all Windows accounts with a RID of 500 are considered built-in Administrator accounts in their respective issuing authorities.
So, the format of a SID can be illustrated using the following example:
“S-1–5–21–3623811015–3361044348–30300820–1013”
Machine SIDs
The machine SID is stored in the SECURITY registry hive located at SECURITY\SAM\Domains\Account, this key has two values F and V.
The V value is a binary value that has the computer SID embedded within it at the end of its data (last 96 bits).
Decoding Machine SID
The SID number is used in file, registry, service and users permissions.
The machine SID is determined in hexadecimal form from here:
- Registry: \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\V (last 12 bytes)
- Filesystem: \%windir%\system32\config\SAM
If the SAM file is missing at startup, a backup is retrieved in hexadecimal form here:
- Registry: \HKEY_LOCAL_MACHINE\SECURITY\Policy\PolAcDmS\@ (last 12 bytes)
- Filesystem: \%windir%\system32\config\SECURITY
Example
2E,43,AC,40,C0,85,38,5D,07,E5,3B,2B
- Divide the bytes into 3 sections:
2E,43,AC,40 — C0,85,38,5D — 07,E5,3B,2B
2. Reverse the order of bytes in each section:
40,AC,43,2E — 5D,38,85,C0–2B,3B,E5,07
3. Convert each section into decimal:
1085031214–1563985344–725345543
4. Add the machine SID prefix:
S-1–5–21–1085031214–1563985344–725345543
Service SIDs
Service SIDs are a feature of service isolation, a security feature introduced in Windows Vista and Windows Server 2008.
Service isolation lets administrators control what local resources (e.g., files, registry keys on the local machine) a Windows service can access.
The purpose of Service SIDs is to allow permissions for a single service to be managed without necessitating the creation of service accounts, an administrative overhead.
Each service SID is a local, machine-level SID generated from the service name using the following formula:
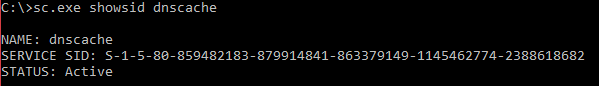
S-1–5–80-{SHA-1(service name in upper case)}The sc.exe utility can be used to generate an arbitrary service SID:
C:\>sc.exe showsid dnscache
NAME: dnscache
SERVICE SID: S-1–5–80–859482183–879914841–863379149–1145462774–2388618682
STATUS: Active
The service can also be referred to as NT SERVICE\<service_name> (e.g. “NT SERVICE\dnscache”).
References
- Security Identifiers (Windows)
- Well-known SIDs (Windows)
- Service isolation explanation
- The Machine SID Duplication Myth (and Why Sysprep Matters)
Windows Security Identifiers (SIDs) was originally published in So Long, and Thanks for All the Fish on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: https://andreafortuna.org/windows-security-identifiers-sids-2196a5be2f4d?source=rss----bf18ac17f001---4