Why SS7 Attacks Are the Biggest Threat to Mobile Security, Exploiting Global Telecom Networks
You may or may not have heard of Signaling System 7 (SS7), but it’s the invisible force behind the phone calls and text messages you send every day. For decades, this system has been the lifeblood of global telecommunications, quietly handling the routing of calls and SMS across networks. But beneath its critical function lies a dangerous secret: SS7 is riddled with vulnerabilities.

An illustration of “SS7 telecommunications system and its vulnerabilities” (DALL-E)
These flaws, known for years, allow attackers to intercept calls, read text messages, bypass Two-Factor Authentication (2FA), and even track user locations. Moreover, SS7 attacks could enable Denial-of-Service (DoS) and fraud. Despite advancements in telecom networks, SS7’s weaknesses remain under risk of exploitation by cybercriminals and state-sponsored actors.
In this post, we’ll take a closer look at how SS7 attacks work, the potential damage they can cause, and how to protect yourself from these persistent threats.
What is SS7 and Why is It Vulnerable?
Signaling System 7 (SS7) is a protocol suite essential to global telecommunications, responsible for routing phone calls, SMS messages, and data between networks. It facilitates services like call setup, text transmission, and international roaming, allowing communication across network operators.
Whether you’re traveling abroad or sending a text overseas, SS7 ensures your communications reach the right destination by linking your device to the appropriate network.
But even with all of its features, SS7 was developed in a time when security was not a top priority.
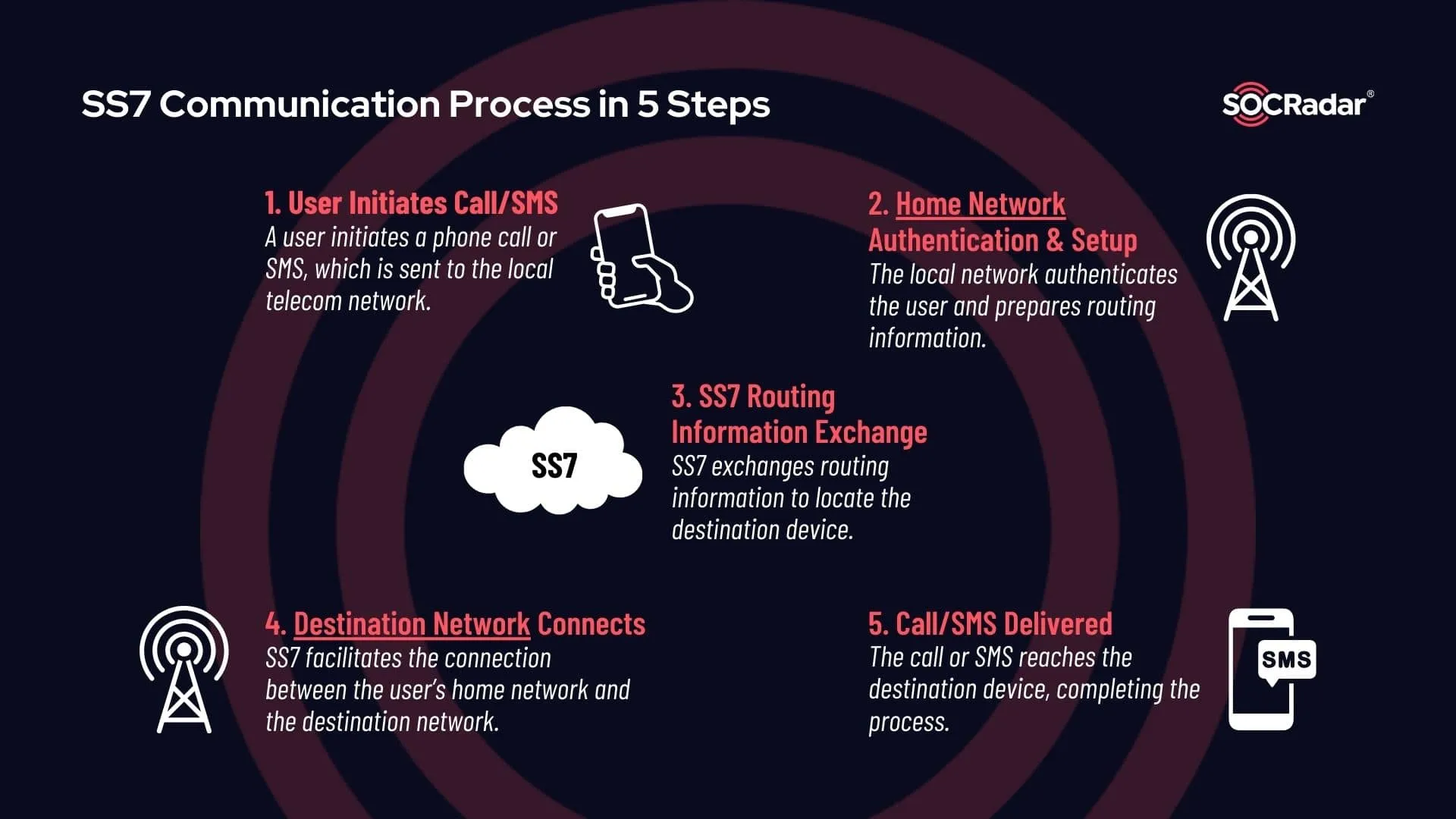
Diagram of the SS7 Communication Process
Designed for closed, trusted telecom networks, SS7 lacks fundamental security features such as encryption and authentication. This inherent lack of protection makes SS7 highly susceptible to attacks, with cybercriminals able to intercept calls, monitor messages, track user locations, and even conduct fraudulent activities.
To make matters worse, SS7 is globally accessible. Telecom operators around the world are interconnected through SS7, and with the right access, cybercriminals can exploit these vulnerabilities remotely.
This global reach, combined with SS7’s outdated security design, makes it a prime target for attackers, despite being a long-standing issue in the telecom industry.
Common SS7 Attacks: How They Work
The vulnerabilities in Signaling System 7 (SS7) expose telecommunications networks to a range of dangerous attacks. Here are 5 common SS7 attack methods, how they work, and the risks they pose:
1. Location Tracking
Attackers can exploit SS7 to track a mobile device’s real-time location by sending specific queries to the network. Using SS7, attackers can retrieve information about which cell tower a device is connected to, allowing them to pinpoint the user’s location without the user’s knowledge. This makes SS7 a tool for tracking anyone, anywhere, as long as they are connected to a cellular network.
2. Call and SMS Interception
One of the most troubling SS7 attacks involves intercepting phone calls and text messages. Attackers can reroute these communications through their own servers by exploiting SS7’s routing functions. Once intercepted, calls can be listened to in real-time, and SMS messages – often containing sensitive information – can be read. This is especially dangerous when it comes to confidential conversations or messages containing financial or personal data.
3. SMS Redirection and 2FA Bypass
SMS-based Two-Factor Authentication (2FA) is widely used to secure accounts, but SS7 vulnerabilities allow attackers to intercept these codes. By redirecting the SMS messages containing 2FA codes, attackers can gain access to bank accounts, email accounts, or other sensitive platforms without the victim’s knowledge. This can lead to serious security breaches, as the attacker bypasses what many consider an extra layer of protection.
Another SMS-based threat is SIM swapping, where attackers manipulate mobile carriers into transferring a victim’s phone number to a new SIM card, allowing them to receive SMS messages intended for the victim. While SIM swapping and SS7 attacks differ in method, both enable attackers to bypass 2FA by gaining access to verification codes. In SIM swapping, attackers control the phone number directly, whereas in SS7 attacks, they intercept messages through network vulnerabilities.
Nevertheless, access to sensitive information can be the key to unlocking a series of damaging actions. Through vulnerabilities like those in SS7, attackers intercept 2FA codes, eavesdrop on calls, and read SMS messages – all without the target ever suspecting a thing. This captured data becomes the foundation for further malicious activities, from account takeovers to fraud. And moreover, for cybercriminals, fraud isn’t merely a transaction; it’s a carefully crafted process, often orchestrated through hidden online channels where sensitive information circulates freely.
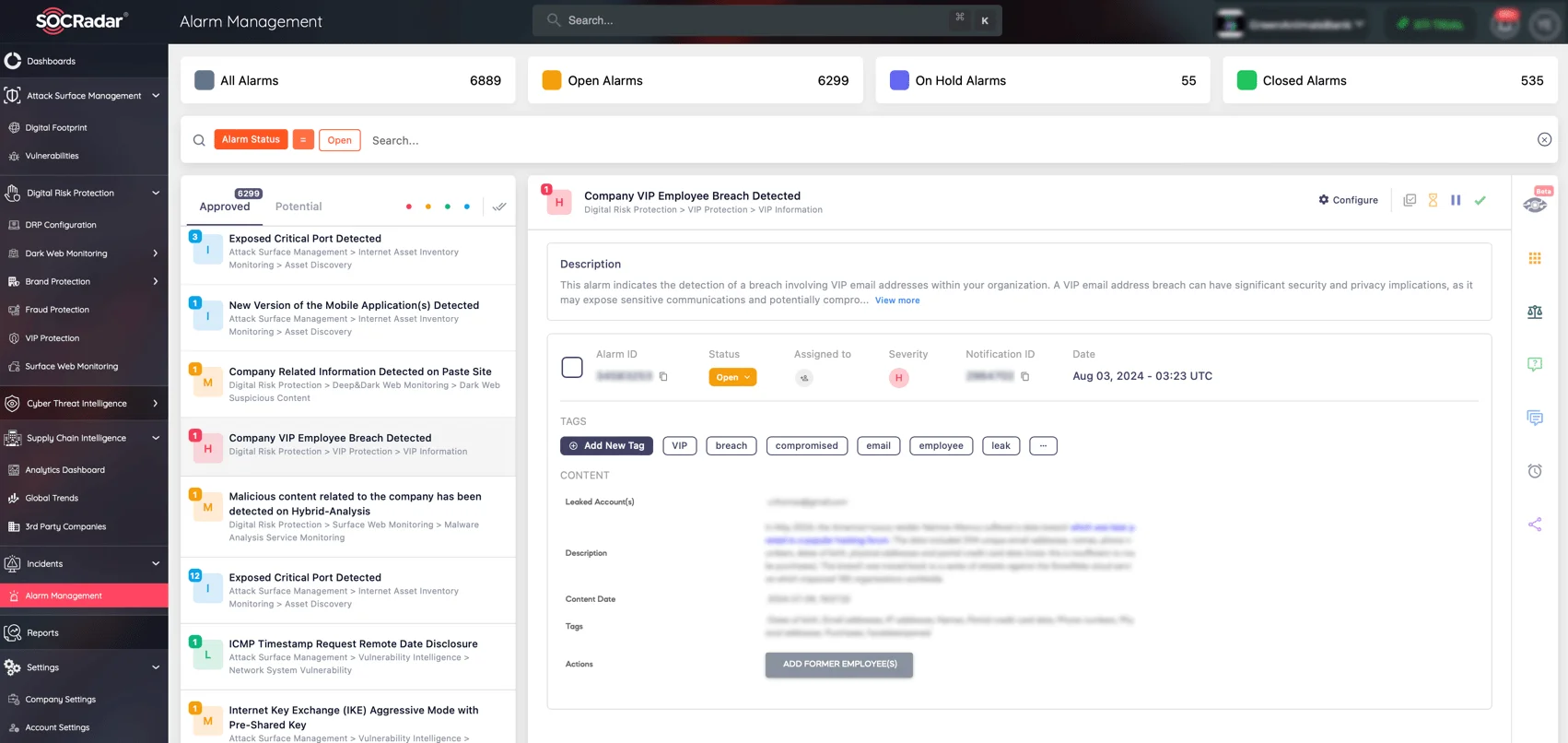
Alarm: Company VIP Employee Breach Detected (SOCRadar Alarm Management)
With the SOCRadar Extended Threat Intelligence (XTI) platform, you gain proactive defense against these risks. SOCRadar XTI scans Dark Web forums, hacker channels on platforms like Telegram, and underground markets to alert you when your sensitive information is exposed or misused. Through real-time alerts and incident reporting, you’re equipped to react immediately to potential threats, helping you protect the integrity of your data and, ultimately, your security.
4. Call Hijacking
Attackers can also manipulate SS7 to hijack calls, rerouting them to another number while making it appear as though the call is still connected to the intended recipient. This allows attackers to impersonate the victim, potentially leading to social engineering attacks, phishing, or other forms of fraud. For the victim, it’s often difficult to detect that anything is amiss until damage is done.
5. Denial of Service (DoS)
By exploiting SS7, attackers can de-register a user’s phone from the network, effectively disconnecting them. This Denial-of-Service (DoS) attack leaves the victim unable to make or receive calls and messages, isolating them from communication. This attack could be used to disable a target’s phone during crucial moments, causing significant disruption.
This type of DoS attack differs significantly from the commonly known ‘SMS bombing’ attacks, which operate independently of SS7. While both methods disrupt communication, an SMS bomber does not sever connections entirely; instead, they overwhelm the target’s phone with an influx of messages.
Real-World Examples of SS7 Attacks
SS7 vulnerabilities have been exploited globally, enabling cybercriminals to intercept sensitive data, commit fraud, and compromise user security. Here are a few notable examples demonstrating the impact of these attacks:
In 2017, hackers exploited SS7 weaknesses to drain funds from mobile bank accounts in Germany. Using malware, attackers stole victims’ online banking credentials, then intercepted SMS-based two-factor authentication (2FA) codes via SS7 to authorize fraudulent transactions. By rerouting these codes to their own devices, the attackers bypassed security measures intended to protect online accounts. This incident raised concerns across Europe about the security of SMS-based verification.
In 2018, Positive Technologies documented a sophisticated SS7 attack targeting subscriber data in a report for the GSMA. Attackers used SS7 protocols to identify a subscriber’s IMSI (International Mobile Subscriber Identity) through their phone number. They then registered the subscriber in a fake network, gaining access to their incoming calls and SMS messages.
Attacker’s attempt to locate the user (PT)
PT identified this attack pattern through suspicious SendRoutingInfoForSM and ProvideSubscriberInfo message sequences, which pointed to location tracking attempts. The attackers exploited weaknesses in the operator’s SMS Home Routing system, bypassing security and gaining access to sensitive data that enabled further communication interception.
In 2019, Metro Bank in the U.K. fell victim to an SS7 attack, where cybercriminals intercepted SMS-based 2FA codes sent to customers. With access to these codes, the attackers gained unauthorized entry to customer accounts and transferred funds.
Practical Steps for Mitigating SS7 Attacks
There are several key steps that individuals and organizations can take to reduce exposure to SS7-based threats:
- Switch to App-Based 2FA: Avoid SMS-based 2FA by switching to app-based authentication solutions like Google Authenticator, Authy, or Microsoft Authenticator. These apps generate 2FA codes locally on your device, reducing the risk of interception.
- Use Encrypted Communication Apps: For secure messaging, use end-to-end encrypted applications such as Signal, WhatsApp, or Telegram. These platforms provide encryption that SS7 cannot compromise, ensuring that messages and calls remain private and secure.
- Telecom-Level Defenses: Telecom providers play a crucial role in securing SS7 networks. They can implement firewalls and anomaly detection tools to identify and block suspicious SS7 activity, preventing unauthorized requests from reaching their networks. Enhanced monitoring and filtering systems can reduce exposure to SS7-based attacks on a large scale.
- User Awareness and Education: Educate users on the risks associated with SMS-based communications and promote best practices for security. Encourage individuals to avoid SMS for sensitive interactions and remind them of the limitations of SMS-based security. Raising awareness can help individuals and organizations alike make informed choices to protect their data.
While SS7 remains an integral part of telecom infrastructure, these steps can help mitigate the risks associated with its vulnerabilities. Organizations and individuals alike can benefit from adopting alternative authentication methods and secure communication practices to stay protected in a world where SS7 attacks continue to pose real threats.
Conclusion
With SS7’s vulnerabilities, sensitive data exposure becomes a constant threat, as attackers can intercept private messages and calls. Compromised authentication is another danger, with SMS-based 2FA often vulnerable to interception, leading to potential data breaches or financial loss. The risks extend to national security, where government agencies reliant on SS7 risk having critical communications exposed and high-profile individuals tracked.
Mitigating these risks requires proactive security measures. From adopting app-based 2FA solutions to using encrypted communication platforms, individuals and organizations can reduce their exposure to SS7-based attacks. At the telecom level, providers can implement firewalls, monitoring, and filtering to detect suspicious activity and improve network security.
Looking ahead, telecom networks are gradually transitioning to more secure protocols, like Diameter, which is used in 4G and 5G networks. Although Diameter offers improved security features, it is not without its own vulnerabilities, as noted by the Federal Communications Commission. In its Legacy Systems Risk Reductions report, the FCC emphasizes that all telecommunications protocols, including Diameter and SIP, remain vulnerable due to potential access points across global networks. Still, protocols like Diameter show fewer vulnerabilities than SS7, which marks progress toward more secure telecom infrastructure.
As we move forward, by pushing for better security practices across the telecom industry and adopting safer communication methods, we can navigate the digital landscape with greater resilience against SS7 and other protocol-based threats.
Article Link: https://socradar.io/why-ss7-attacks-are-the-biggest-threat-to-mobile-security-exploiting-global-telecom-networks/

