What is Invoice Fraud?
Invoice fraud has become a rampant concern in today’s digitally-driven business environment. According to the 2024 AFP Payments Fraud and Control Survey Report, a staggering 80% of organizations fell victim to payment fraud attacks or attempts in 2023, marking a significant 15-percentage point surge from the previous year. This statistic reminds us of businesses’ escalating threat landscape, particularly in fraudulent activities like invoice fraud, which we will discuss in this article.
Invoice fraud stands out as one of the top methods used in payments-related fraud, especially given the ease with which fraudsters can manipulate invoices to deceive unsuspecting businesses. Fraudsters exploit vulnerabilities in payment processes, often targeting checks, which remain the payment method most vulnerable to fraud, according to 65% of respondents in the mentioned survey.
These fraudulent schemes often send fake invoices that appear legitimate at first glance, tricking businesses into paying for fraudulent accounts. The urgency created by these scams, with fraudsters demanding immediate payment, leaves little time for businesses to detect the fraud before funds are transferred.
The consequences of falling victim to invoice fraud can be severe. The survey reveals that 30% of organizations that experienced payment fraud in 2023 were unsuccessful in recovering their lost funds. This loss impacts the bottom line, tarnishes the reputation of businesses, and erodes trust with legitimate vendors.
Given these concerning statistics, businesses must focus on enhancing their fraud detection and prevention measures. Let’s first delve into what invoice fraud entails before exploring strategies for prevention and mitigation.
How They Abuse Invoice
Invoice fraud can unfold in various ways, showcasing the adaptability and cunning of fraudsters in exploiting vulnerabilities within businesses. Let’s delve into a scenario where invoice fraud takes shape and unfolds step by step.
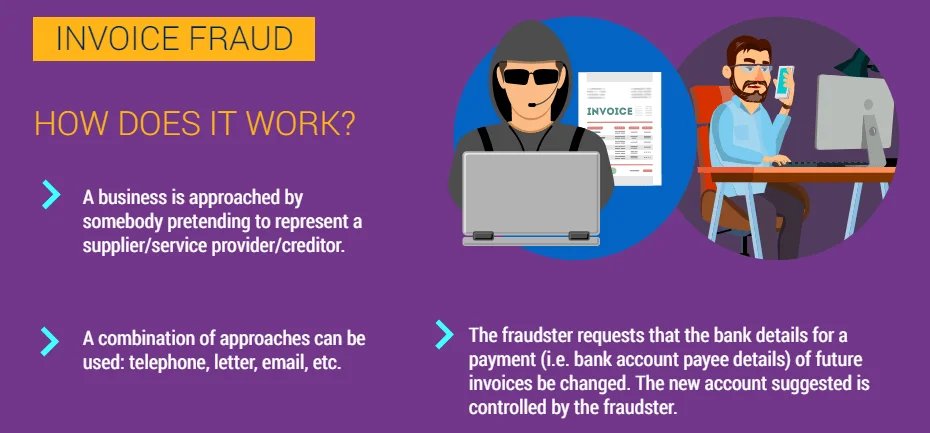
How does Invoice Fraud work? (Europol)
Imagine a mid-sized manufacturing company, ABC Manufacturing, that procures raw materials from multiple suppliers across the globe. One day, the accounts payable department receives an email from what appears to be a long-standing supplier, XYZ Suppliers, requesting an urgent payment for an upcoming shipment. The email is well-crafted, mimicking the language and format typically used by XYZ Suppliers, and it includes an attached invoice detailing the transaction.
The Initial Deception: The email and invoice seem legitimate at first glance. The invoice contains all the usual information, including product details, quantities, and prices. The payment amount is within the usual range for such transactions, and there are no glaring red flags that catch the attention of the accounts payable clerk.
- You might wonder how the invoice contains all the usual information. It’s important to note that many ransomware or extortion groups include invoice attachments in their data leaks. This means it’s crucial to be aware that such information could have been compromised, particularly during an attack on your supply chain, and to implement preventive measures moving forward.
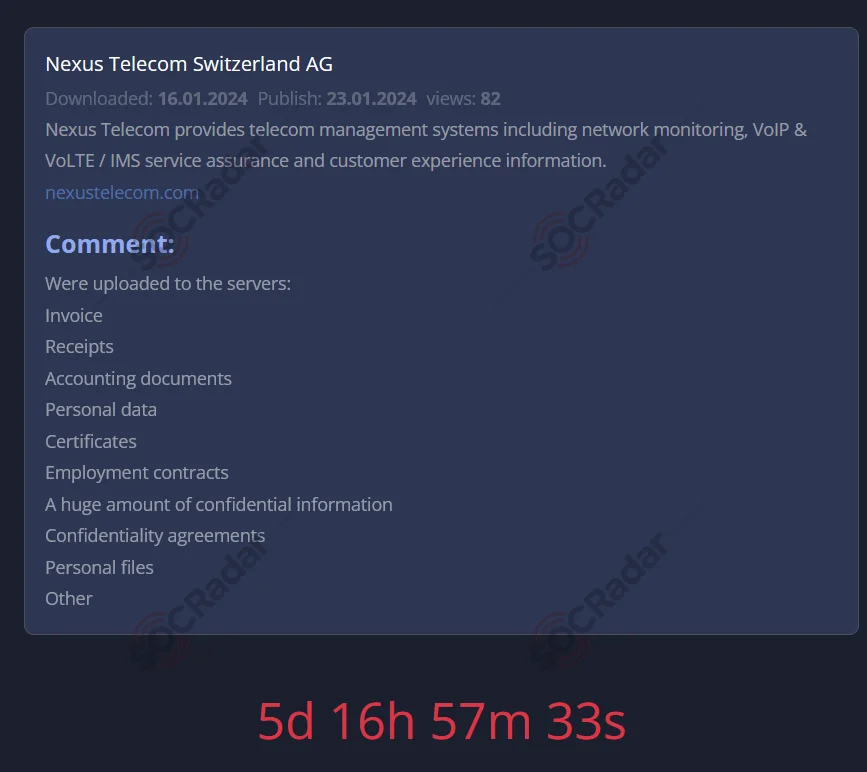
A victim listing of 8Base Ransomware, data includes invoice files
Urgency and Trust: The email stresses the urgency of the payment, citing tight production schedules and upcoming deadlines. It also mentions a slight change in banking details, attributing it to an internal restructuring at XYZ Suppliers. The language used is persuasive, invoking trust built over years of successful transactions.
Lack of Verification: Due to the apparent urgency and the perceived trustworthiness of the supplier, the accounts payable clerk, overwhelmed by the daily influx of invoices and payments, processes the payment without conducting thorough verification. The slight change in banking details is noted but not questioned, as it seems plausible given the mentioned restructuring.
The Unraveling: Weeks pass, and ABC Manufacturing’s finance team notices discrepancies during a routine audit. Upon closer inspection, they realize that the payment made to XYZ Suppliers matches an invoice that was never authorized or verified by the procurement department. Further investigation reveals that the banking details provided in the email were fraudulent, leading to funds being diverted to an offshore account controlled by fraudsters.
Repercussions: ABC Manufacturing now faces a series of repercussions. They’ve lost a significant sum of money to invoice fraud. Legal and financial teams scramble to trace the funds and initiate recovery procedures, but the chances of full restitution are slim. The company’s reputation takes a hit as news of the fraud spreads, leading to concerns among investors, partners, and customers about ABC Manufacturing’s financial controls and integrity.
This scenario highlights how invoice fraud can unfold within a seemingly secure business environment. It underscores the importance of vigilance, verification, and continuous adaptation in combating this pervasive threat. As businesses evolve and embrace digital technologies, so do the tactics of fraudsters, making it imperative for organizations to stay ahead with robust anti-fraud measures and a culture of skepticism tempered with trust.
How to Protect Your Organization
Invoice fraud can strike swiftly and subtly, often exploiting rushed decisions or overlooked details. To shield your organization effectively, adopting a multifaceted approach that combines vigilance, automation, and strategic checks is paramount. Let’s delve into actionable steps based on expert insights to fortify your defenses against invoice fraud.
Exercise Caution and Thoroughness:
One of the primary tactics to counter invoice fraud is to resist the urge to act hastily. Emails demanding urgent payments or featuring unfamiliar vendors should raise immediate red flags. Here’s what to watch for:
- Emails from unknown vendors
- Demands for immediate payment
- Changes in payment details, methods, or addresses
- Suspicious links or attachments
Take time to scrutinize sender email addresses, verify the legitimacy of payment requests, and cross-check against original purchase orders. Instituting controls to validate all transactions and assigning distinct personnel for invoice approvals and payments can add a layer of security.
Even if there’s a slight doubt, it’s important to seek confirmation through alternative channels like a phone number. However, it’s crucial to recognize that this approach may not be foolproof given the advancements in Deepfake scenarios.
To help you in this endeavor, in addition to its many features, SOCRadar can help your efforts with its Malware Analysis module, allowing you to analyze a very extensive array from Binary to Office files including EML files while getting instant reports of the files you have uploaded. Furthermore, our Malware Analysis module also acts as an Email Analyzer since it could analyze EML files. You might check it on SOCRadar Labs for free!
SOCRadar Labs, EML Analyzer
- Although SOCRadar can help you with this problem, we would like to give you an additional quick tip. The reputation of such scam emails is expected to be low, and you can also check the reputation with basic tools such as Simple Email Reputation.
Leverage Technology:
Embracing technology can be a game-changer in combating fraud. Here are two vital strategies:
- Automate Accounts Payable (AP) Processes: Implement AP automation software to streamline invoice verification and reduce human error. Automated systems can flag irregularities instantly, minimizing the chances of fraudulent invoices slipping through.
- Use 3-Way Matching: Employ the three-way matching process to align invoices with purchase orders and goods received notes. This ensures that orders were placed, and goods were received before invoices are processed, thwarting fraudulent attempts.
Verify Payment Details:
Maintaining a careful approach to payment verification is crucial:
- Confirm Payment Changes: Always validate any alterations in vendor payment details directly with the vendor. Establish direct contact through reliable means to authenticate changes before releasing payments.
- Regular Bank Statement Reviews: Periodically reviewing bank statements aids in identifying suspicious transactions promptly, allowing for swift action.
Spotting Fake Invoices:
Recognizing signs of fake invoices is essential. Here are key indicators:
- Discrepancies in vendor contact or payment information
- Inconsistencies between invoice details and finance or ERP data
- Invoices for services not yet rendered, situations where an invoice is issued for services that have not been provided or completed
By integrating these strategies and remaining vigilant, your organization can significantly reduce the risk of falling victim to invoice fraud. Remember, training your team on cybersecurity best practices and investing in robust email security solutions are crucial pillars in fortifying your defenses against evolving fraud tactics.
Protecting your organization from invoice fraud demands a proactive stance and a combination of technological advancements, stringent checks, and ongoing awareness. Stay vigilant, stay secure.
Article Link: What is Invoice Fraud? - SOCRadar® Cyber Intelligence Inc.
