
Whether it be sending and receiving emails, transferring files or simply browsing the web, data transfer exists everywhere in our technological world.
In an age in which cybercriminals are trying to access that data at every turn, businesses and consumers alike need to be protected — and the first step is to learn what AES encryption is.
AES encryption is an encryption method that has become the industry standard due to its security, ease of use and speed. In this article, we will detail what AES encryption is, how it works and how Panda can equip you with this valuable security method via a VPN and password manager.
What Is AES Encryption?
AES encryption, or advanced encryption standard, is a symmetric block cipher used to encrypt sensitive data. With equal parts security and speed, AES has become a security standard for users and applications that need easy-to-use encryption.
This method was first conceptualized in 1997 when the National Institute of Standards and Technology (NIST) became vulnerable to brute force attacks and needed a stronger encryption method. NIST enlisted a pair of developers to tackle the problem — Vincent Rijmen and Joan Daemen — who developed the eventually selected technology, AES, in 1998.
AES has been the encryption standard for the NIST since its full-scale adoption in 2002.
How Does AES Encryption Work?
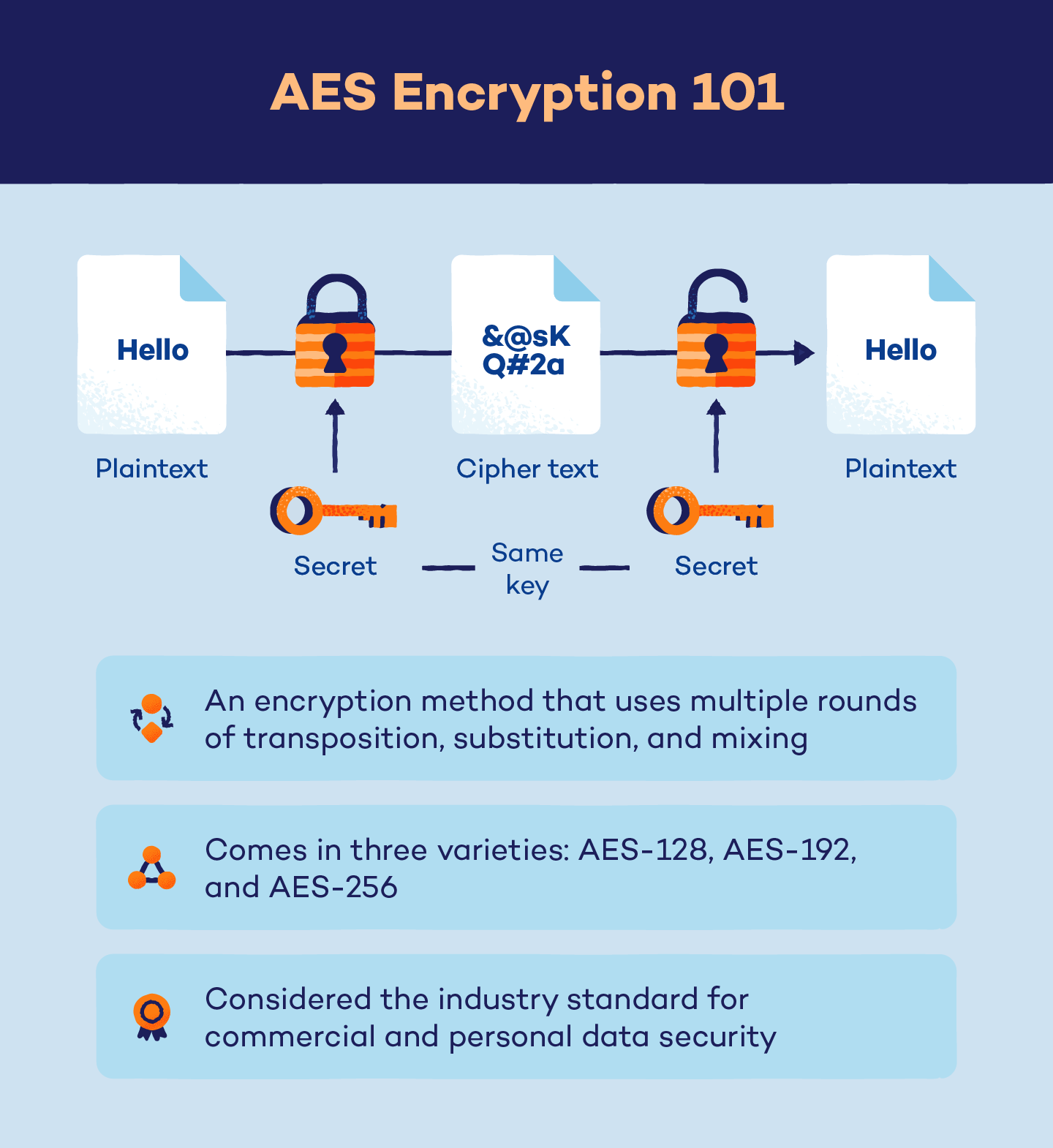
As with all encryption methods, AES works by turning plain text into a code that only someone with the key (or cipher) can decode. The main difference between AES and other encryption methods, however, is that AES uses multiple rounds of transposition, substitution and mixing rather than one single round of encryption.
Types of AES
While the AES encryption and decryption process is similar regardless of method, it works slightly differently depending on the type of AES. Overall, there are three main types of AES encryption:
- AES-128: This method uses a 128-bit key length for encryption and decryption, which results in 10 rounds of encryption with 3.4 x 1038 different potential combinations.
- AES-192: This method uses a 192-bit key length for encryption and decryption, which results in 12 rounds of encryption with 6.2 x 1057 different potential combinations.
- AES-256: This method uses a 256-bit key length for encryption and decryption, which results in 14 rounds of encryption with 1.1 x 1077 different potential combinations.
Why the different types of AES? It’s all dependent on the specific use case. AES-256 is the strongest encryption key, but it requires much more processing power, time and resources to execute than AES-128. To secure top-secret government files, AES-256 is the clear choice. But if the goal is to secure an app on a smartphone, for example, AES-128 may be more appropriate.
AES In Action
No matter the type of AES, the encryption process is similar and can be described in a series of steps:
1. Division and Expansion
The encryption method begins by dividing the plaintext of the message you want to send into blocks of bits, or rows, which are then expanded via AES’ key schedule. The process also adds an encryption key — called a round key — during this step.
2. Substitution
During substitution, the method substitutes the plaintext with encrypted text, which is based on a pre-established table called the Rijndael S-box.
3. Shifting
Now all of the rows of newly encrypted text are shifted by one position, except for the first row.
4. Mixing
The encrypted and shifted rows are now further mixed. This prevents an unauthorized user or hacker from simply shifting the rows back to their original position.
5. Round Key
Using the round key generated in the first step, the information is once again encrypted.
6. Repeat
This process is repeated a certain number of times depending on the type of AES.
Advantages of AES Encryption
AES is the preferred encryption method because it excels in many key performance metrics. A few benefits of AES include:
- Security: Even the lowest level of AES encryption, AES-128, would take an estimated 1 billion billion years (no, that extra billion isn’t a typo) to crack if using a brute force method.
- Cost: AES encryption is available for free, as it was originally developed to be released on a royalty-free basis.
- Ease of use: The AES algorithm is easy to implement across a multitude of applications, and is known for its simplicity and ability to conform across hardware and software platforms.
- Speed: Compared to other encryption methods, AES is known for its speed, boasting faster encryption and decryption times than other methods.
What Is AES Used For?
Even though AES was first formulated in conjunction with the United States government, this encryption method is now used in both governmental and civilian applications. A few of the most common uses of AES encryption include:
- VPNs: The job of a virtual private network (VPN) is to provide secure and private online browsing. Since this process connects users to different servers, AES encryption is used to protect user data against leaks and cyberattacks.
- Password managers: Password managers are used to safely store login credentials under a single master key. Given a single breach could compromise a user’s entire collection of passwords, AES is often used to secure this software.
- Wi-Fi: Wireless internet typically uses many encryption methods such as WPA2, and AES can often be found in these connections as well.
- Mobile apps: Any app that involves messaging or photo sharing typically utilizes AES to aid in data security.
How Does AES Compare to Other Encryption?
While AES is an impressive encryption method, how does it compare to other options available? Here is how AES stacks up against similar systems.
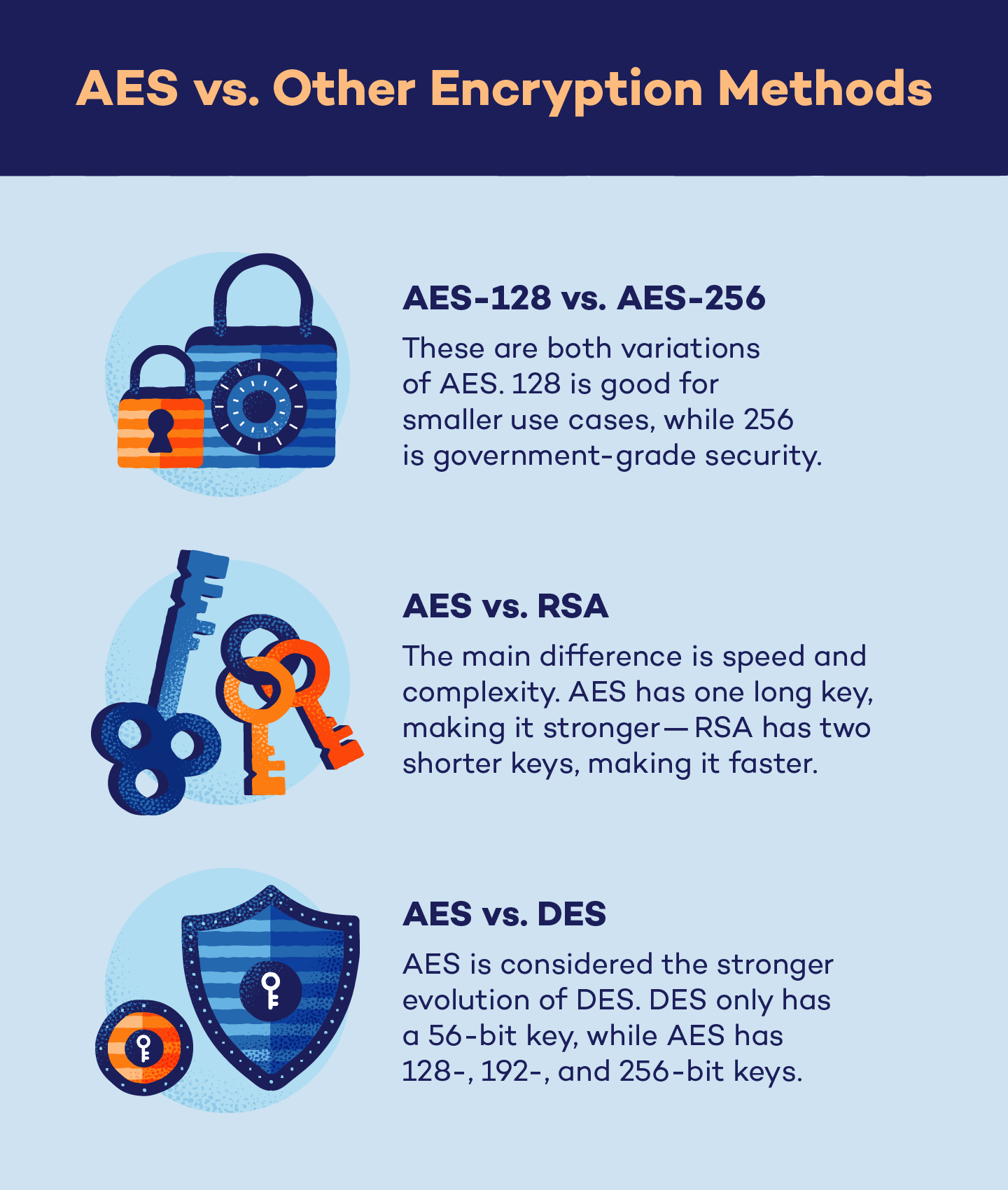
AES-128 vs. AES-256
AES-128 and AES-256 may seem like two different systems, but they are simply two variations of the same encryption method.
AES-128 involves a 128-bit key length in which data goes through 10 rounds of encryption. While this method is extremely secure against brute force attacks, it has the lowest security specs of all AES variations. 128 is a good option for securing information in which memory or battery life is important, like with mobile devices.
AES-256 involves a 256-bit key length in which data goes through 14 rounds of encryption, and has the highest security specs of all AES variations. While 256 is slowly being adopted into everyday uses due to continuous advancements in technology, this method is good for when information security is absolutely critical — such as with top-secret documents.
AES vs. RSA
RSA, or Rivest, Shamir and Adleman, is a type of encryption that uses an asymmetric algorithm to encrypt and decrypt data. This method can be paired with other encryption methods such as PGP encryption to generate a pair of related keys — otherwise known as public and private keys.
While both algorithms are secure, the main difference between AES and RSA comes down to speed and complexity.
Since AES uses the same key to encrypt and decrypt data, it is more user-friendly, cheaper and more secure against brute force attacks due to the length of the password. RSA, on the other hand, is faster in processing data because the length of the keys are shorter.
Despite their differences, both AES and RSA are reliable methods to encrypt and secure data.
AES vs. DES
DES, or data encryption standard, is the now-outdated encryption method used by government agencies starting in the 1970s.
DES and AES are similar in functionality, but the difference is simply that AES is more efficient and secure. While DES uses a 56-bit key, AES uses 128-, 192-, and 256-bit keys which results in increased security. AES is also faster than DES, resulting in quicker encryption.
Overall, AES has replaced DES in nearly every capacity.
AES Encryption FAQ
Finally, we will wrap up with a few frequently asked questions about AES encryption.
What Is AES 128 vs. 192 vs. 256?
AES 128, 192 and 256 are all variations of the same algorithm, but the difference lies in the key length and rounds of encryption.
AES-128 uses a 128-bit key length for encryption and decryption, which results in 10 rounds of encryption; AES-192 uses a 192-bit key length for encryption and decryption, which results in 12 rounds of encryption; and AES-256 uses a 256-bit key length for encryption and decryption, which results in 14 rounds of encryption.
Is 128-Bit AES Secure?
Yes, 128-bit AES is secure. In fact, if using brute force methods, it would take 1 billion billion years to crack.
Is AES Free to Use?
Yes, AES is free to use. It was originally developed to be released on a royalty-free basis.
Is AES the Best Encryption Method?
The best encryption method for you depends on what’s important for your situation. That said, AES is one of the leading encryption methods on the market, trusted by the National Institute of Standards and Technology since 2002.
Panda Security Can Help With Encryption
AES encryption is an extremely secure and user-friendly algorithm that can protect your most sensitive data. Found in a number of everyday applications, this method is the go-to for defending sensitive data against brute force attacks.
If you want the power of AES encryption in your everyday cyber activity, enlist the help of Panda’s VPN and password manager services to expertly secure your data against cyberthreats.
The post What Is AES Encryption? A Guide to the Advanced Encryption Standard appeared first on Panda Security Mediacenter.
Article Link: What Is AES Encryption? - Panda Security