An Unwanted Guest
Co-Author: Denise Dasom Kim, Jungyeon Lim @ Talon

SoW (Story of the Week) publishes a report summarizing ransomware’s activity on the Darkweb. The report includes summary of victimized firms, Top 5 targeted countries and industrial sectors, status of dark web forum posts by ransomware operators, etc.
Executive Summary
On May 13th, the notorious Russian hacking forum XSS banned all ransomware promoting posts and operators’ accounts. It was Darkside ransomware’s colonial pipeline infection that triggered this incident.
As the U.S. government and FBI narrowed down the investigation, the Darkside ransomware operation server was taken down, and even the Russian hacking forums announced that they are banning and deleting all the posts related to ransomware activity. Three biggest hacking forums, starting with XSS Forum, Exploit, and Raidforums, all halted ransomware operators’ activity, and of course, there were many disappointing posts from the ransomware operators regarding such decisions made by administrator. Most of active accounts such as REvil, Lockbit, and Avaddon have announced that they will either stop their activities in the forum or move out to their own independent platform.
Then, where will they go? Let’s see what will happen after the consequence of banning ransomware activity in all forums.
1. Weekly Status
A. Status of the victimized firms (5/17 ~ 5/24)
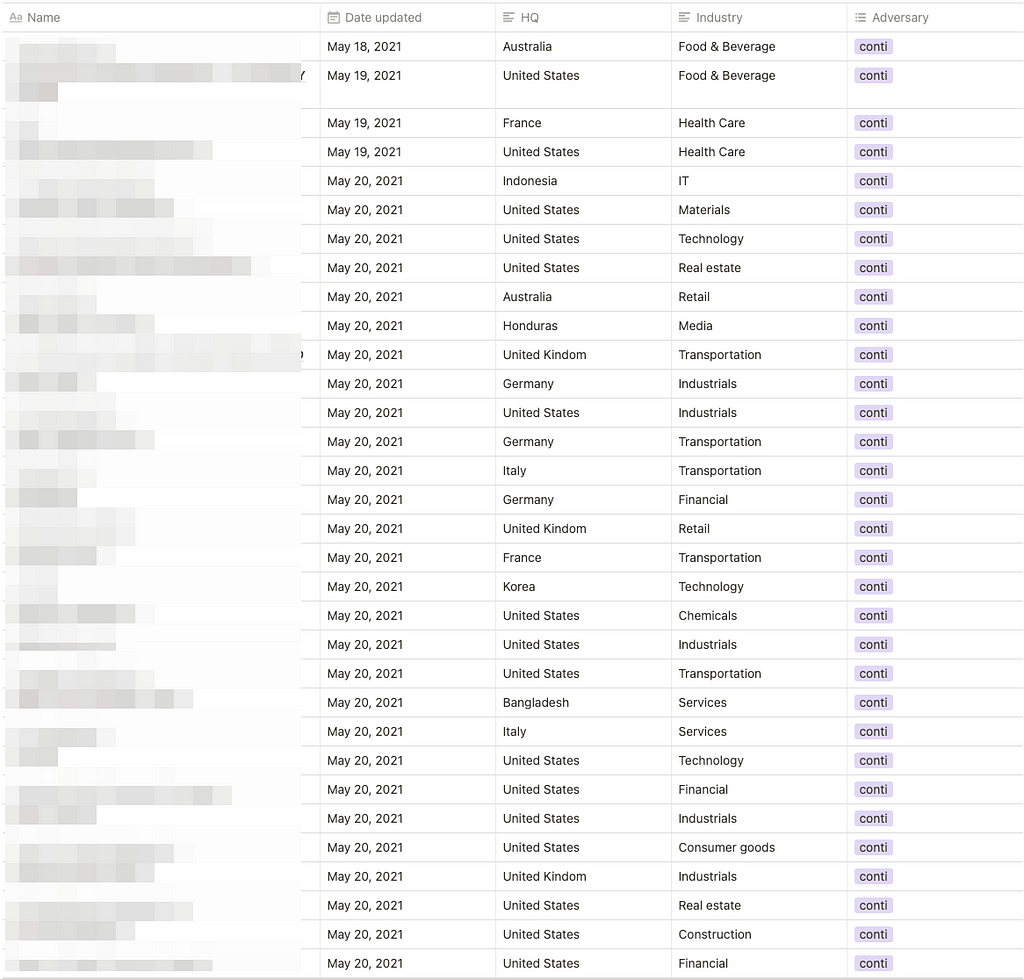
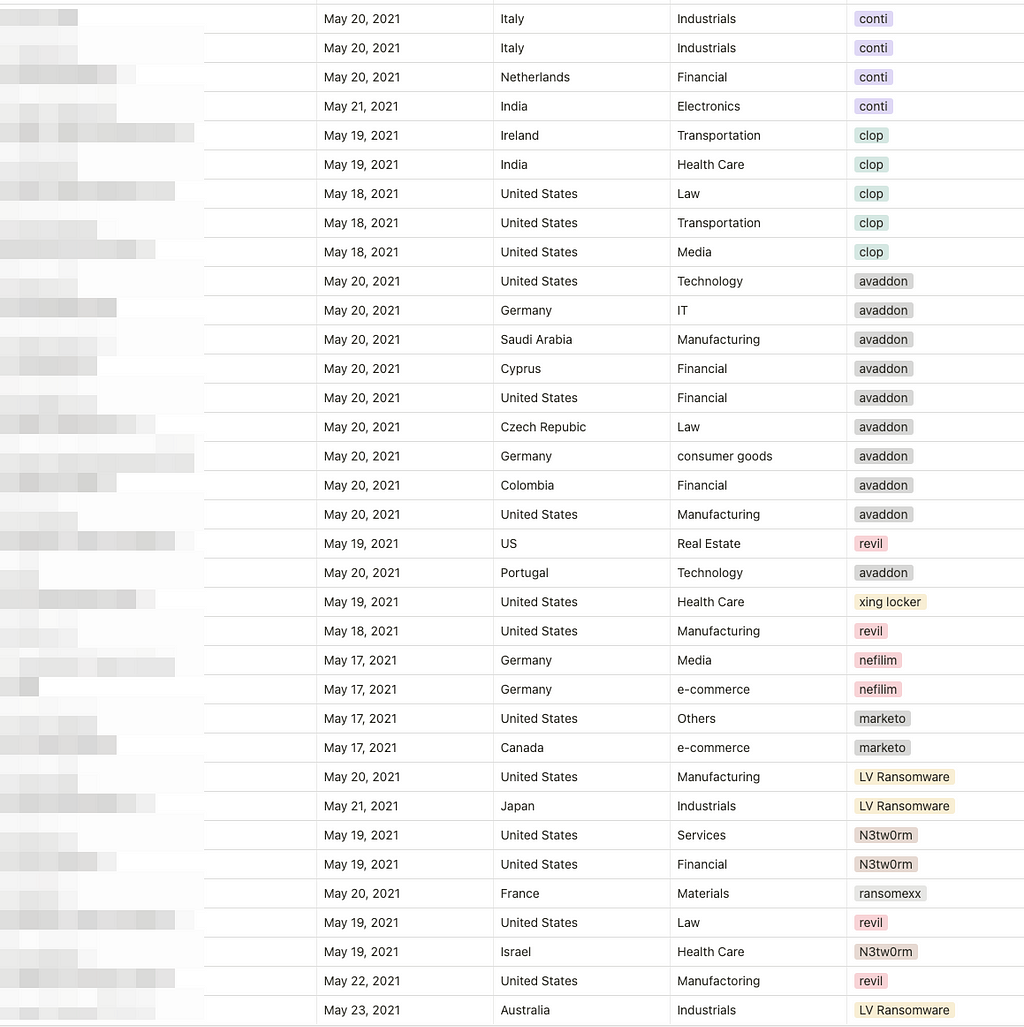
- For a week, a total of 67 victimized firms were mentioned and a change in the state of the data leaked from the victims in the ransomware site was detected
- 10 threat groups’ activities were detected
B. TOP 5 targeted countries
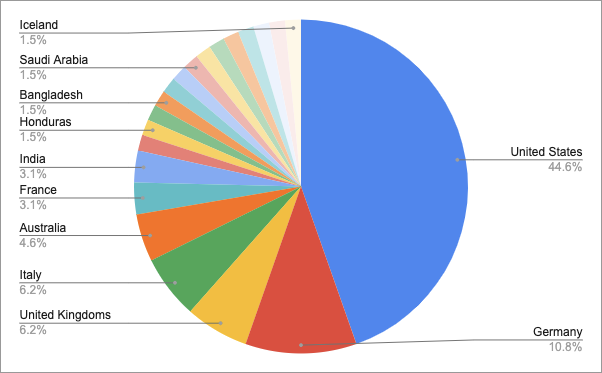
- United States — 44.6%
- Germany — 10.8%
- United Kingdoms — 6.2%
- Italy — 6.2%
- Australia — 4.6%
C. TOP 5 targeted industrial sectors
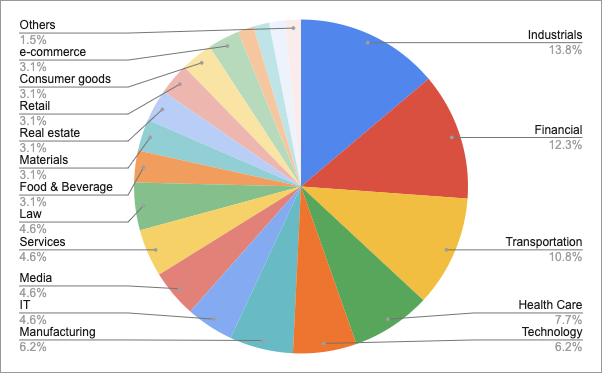
- Industrials — 13.8%
- Services — 12.3%
- Transportation — 10.8%
- Health Care — 7.7%
- Technology — 6.2%
2. Status of active Ransomware forum posts @Dark Web
A. XSS Forum
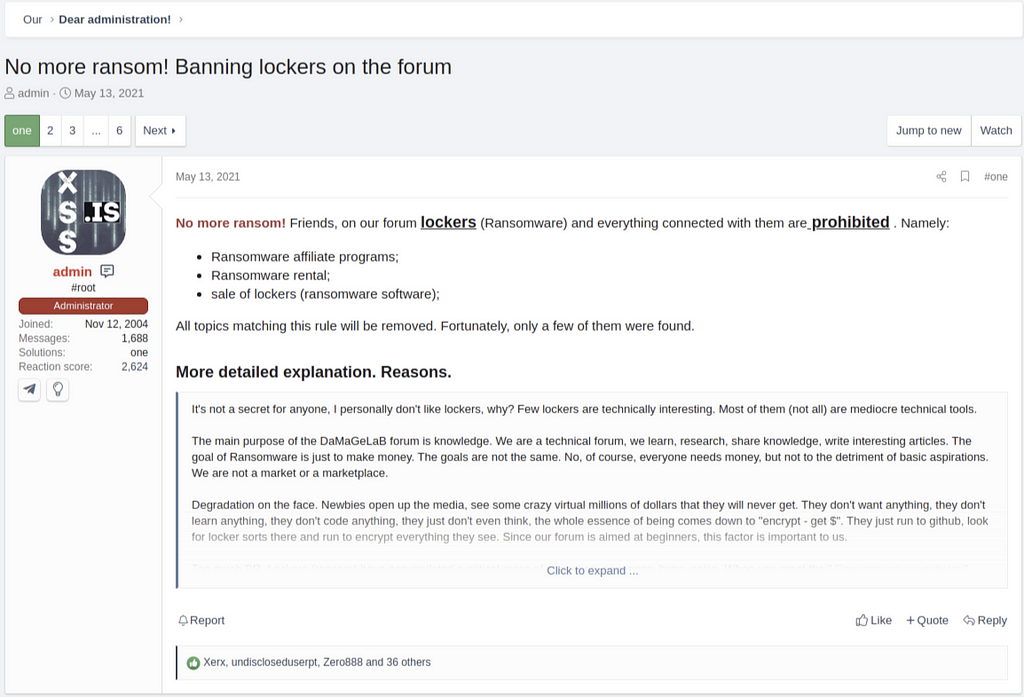
On May 13th, the administrator of the XSS Forum announced that ransomware-related content is no longer allowed. In particular, it will be limited to the following contents.
- Ransomware affiliate programs;
- Ransomware rental;
- sale of lockers (ransomware software);
In other words, ransomware affiliate program cannot be promoted for partner recruitment, and any forms of selling Ransomware-as-a-Service (RaaS) or ransomware software itself is prohibited.
Obviously, the administrator’s announcement shocked the ransomware operators who were currently running. For example, the LockBit ransomware operator seems to have felt a kind of betrayal with the comment “Suddenly”.
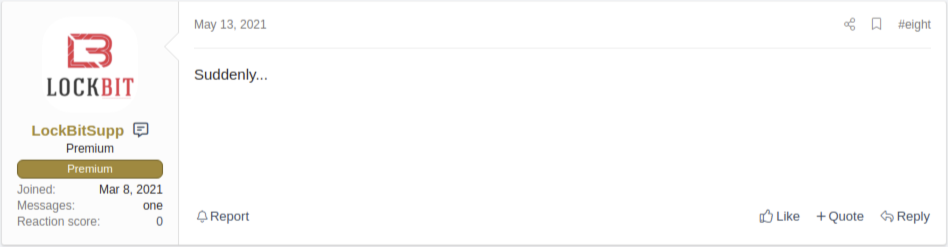
Shortly after this announcement from XSS forum, the administrator of Exploit and Raidforums announced the same rules about banning ransomware-related posts.
B. Exploit & Raidforums
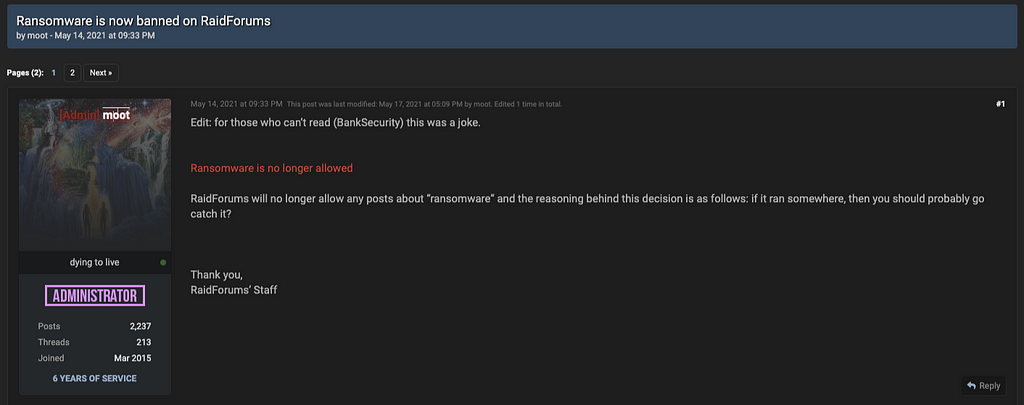
2021.05.14 Raidforums posts that will not allow ransomware related content

2021.05.15 Exploit forum posts that will not allow ransomware related content
3. Ransomware operators’ next move
A. Revil (Sodinokibi)

- Due to the change in the policy of the administrator of XSS forum, REvil also declared retirement in Exploit and will switch to a private platform
B. Babuk
 Source: Bleeping Computer (https://www.bleepingcomputer.com/news/security/babuk-ransomware-readies-shut-down-post-plans-to-open-source-malware/)
Source: Bleeping Computer (https://www.bleepingcomputer.com/news/security/babuk-ransomware-readies-shut-down-post-plans-to-open-source-malware/)- 2021.04.29 Bleeping computer reported that Babuk ransomware would close the BABUK project and release the source code to the outside by leaving a note titled ‘Hello World 2’
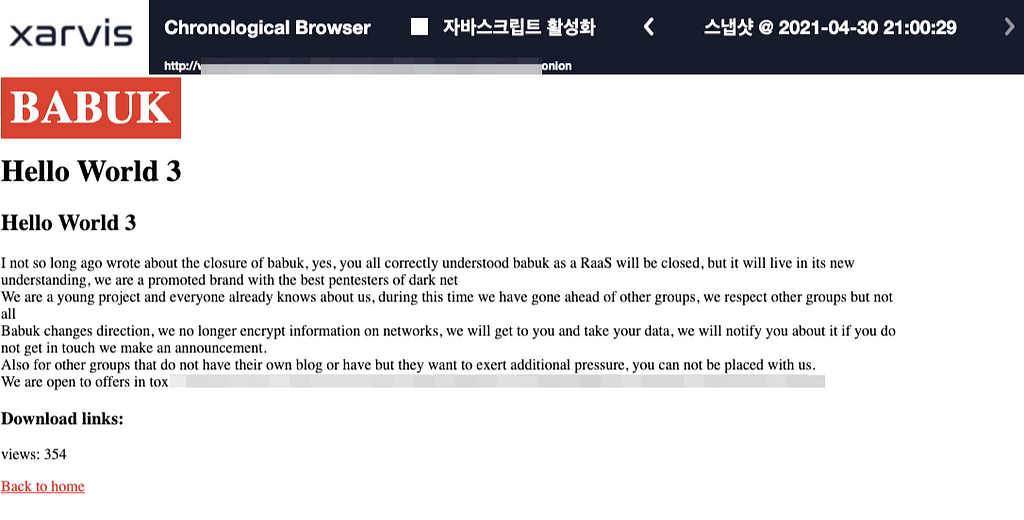
I not so long ago wrote about the closure of babuk, yes, you all correctly understood babuk as a RaaS will be closed, but it will live in its new understanding, we are a promoted brand with the best pentesters of dark net
We are a young project and everyone already knows about us, during this time we have gone ahead of other groups, we respect other groups but not all
Babuk changes direction, we no longer encrypt information on networks, we will get to you and take your data, we will notify you about it if you do not get in touch we make an announcement.
Also for other groups that do not have their own blog or have but they want to exert additional pressure, you can not be placed with us.
We are open to offers in tox: ****Sanitized by S2W LAB
- However just a day after, Babuk reappeared with a post titled ‘Hello World 3’ saying that it will no longer focus on data encryption but rather exfiltrating data.
- It also states that other ransomware groups either do not have a data leak site or have but they want to exert additional pressure, shall not work with Babuk.
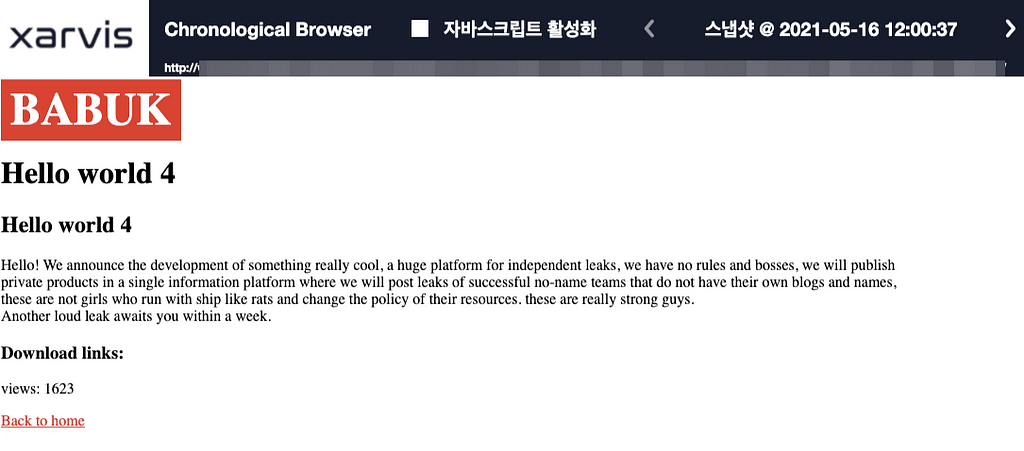
Hello! We announce the development of something really cool, a huge platform for independent leaks, we have no rules and bosses, we will publish private products in a single information platform where we will post leaks of successful no-name teams that do not have their own blogs and names, these are not girls who run with ship like rats and change the policy of their resources. these are really strong guys.
Another loud leak awaits you within a week.
- After that, in ‘Hello World 4’, Babuk is planning a huge platform for data leakage, and it is stated that ransomware groups that do not operate their own data leakage sites will join together.
- A huge leak will happen very soon (they mentioned a week or soon)
Conclusion
Most of renowned hacking forums banned ransomware-related content, but the number of victimized firms was not significantly reduced.
Operators who have been kicked out of forums are likely to switch to their own platform and additional ransomware groups that do not operate leak sites will likely join the crews.
Such sanctions against ransomware operators are just temporary, and this does not mean any termination or downfall of ransomware gangs, so we strongly recommend never let loose the guard.

- Homepage: https://www.s2wlab.com
- Facebook https://www.facebook.com/S2WLAB/
- Twitter https://twitter.com/s2wlab
W4 May | EN | Story of the week: Ransomware on the Darkweb was originally published in S2W LAB BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: https://medium.com/s2wlab/w4-may-en-story-of-the-week-ransomware-on-the-darkweb-5f5b8d4c3b6f?source=rss----30a8766b5c42---4