I want to break free

with contribution from Denise Dasom Kim, Jungyeon Lim, Yeonghyeon Jeong | S2W LAB Talon
SoW (Story of the Week) publishes a report summarizing ransomware’s activity on the Darkweb. The report includes summary of victimized firms, Top 5 targeted countries and industrial sectors, status of dark web forum posts by ransomware operators, etc.
Executive Summary
- [Statistics] The number of companies infected by ransomware is 30 in one week which is 8.4% higher compared to previous week, and United States is still positioned at the highest which amounts to 53.3% among all victims infected by ransomware.
- [Cryptocurrency] As a result of tracking STOP Ransomware bitcoin address, which is the most commonly found along with recent variants, it was confirmed that some funds went into Huobi and Bitfinex exchanges, and some of them were identified as money laundering.
- [Dark Web] Payload.bin (babuk) has been rebranded as RAMP and it appears that the site has been changed to a forum for ransomware activity rather than a site posting leaked data.
- [Dark Web] The infamous ransomware group REvil suddenly disappeared and the exact reason is still unknown.
1. Weekly Status
A. Status of the infected firms (07/05~07/11)
- For a week, a total of 30 infected firms were mentioned which is 8.4% higher compared to previous week.
- 11 threat groups’ activities were detected
B. TOP 5 targeted countries
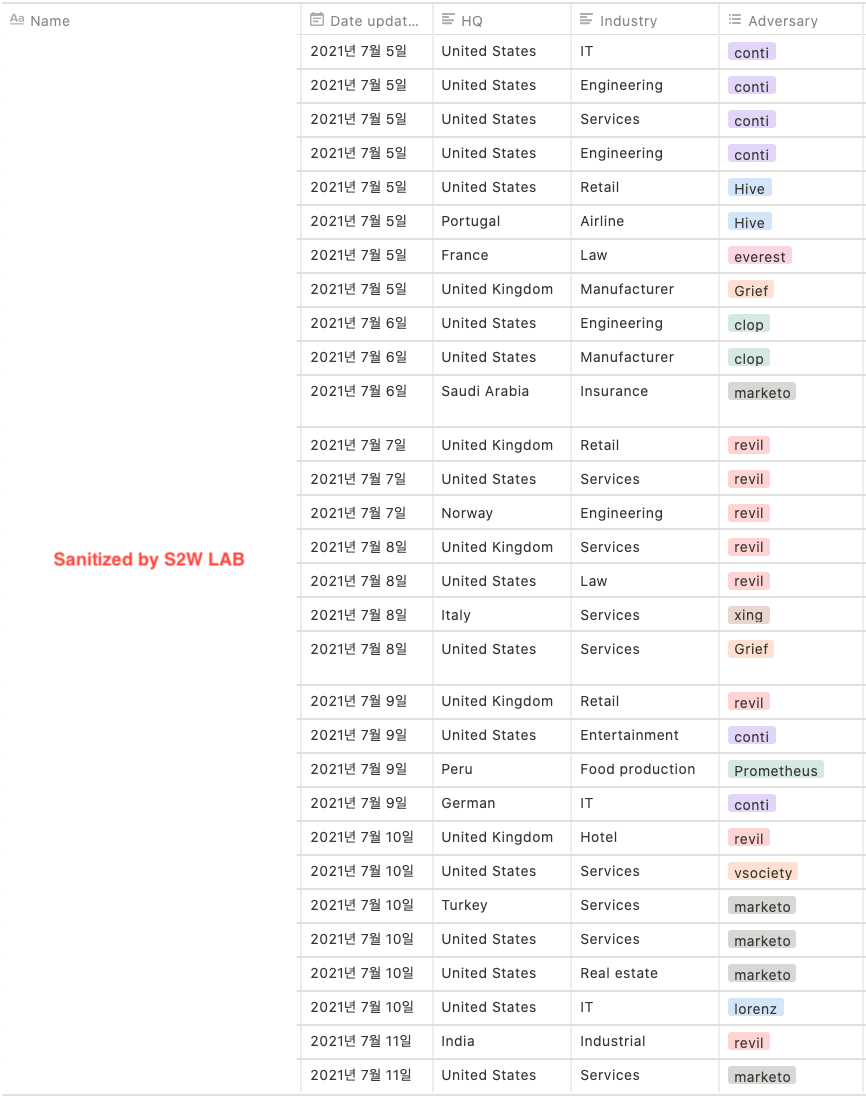
- United States — 53.3%
- United Kingdom — 16.7%
- France & India & Peru & Turkey & German & Italy & Saudi Arabia & Norway & Portugal — 3.3%
C. TOP 5 targeted industries
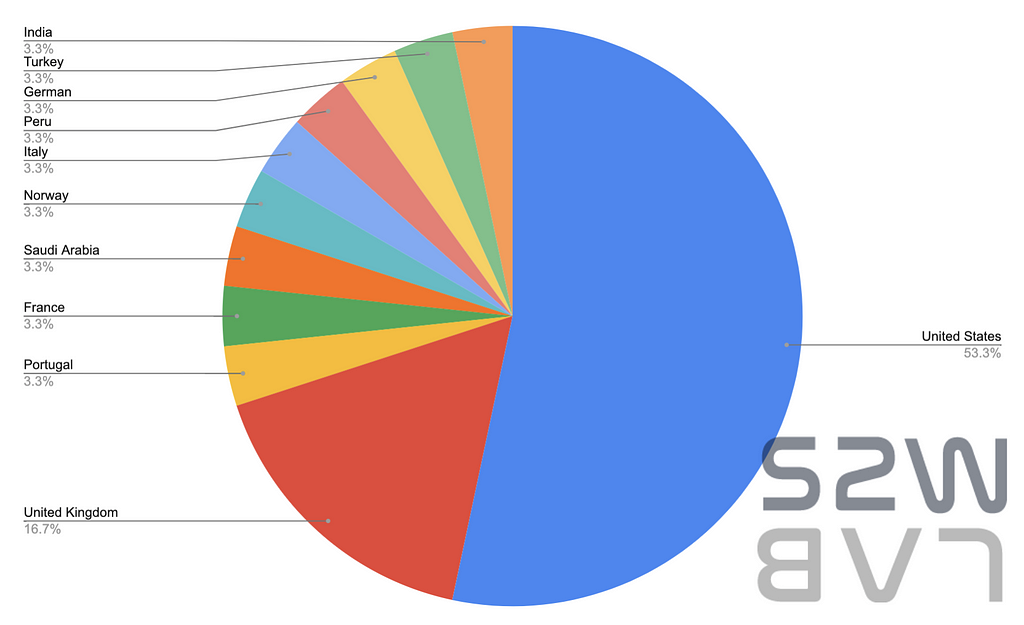
- Services- 30.0%
- Retail — 10.0%
- Manufacturer & Law — 6.7%
- Industrial & Real estate & Food production & Entertainment & Hotel & Insurance & Airline — 3.3%
D. Current status of data leak site operated by ransomware groups
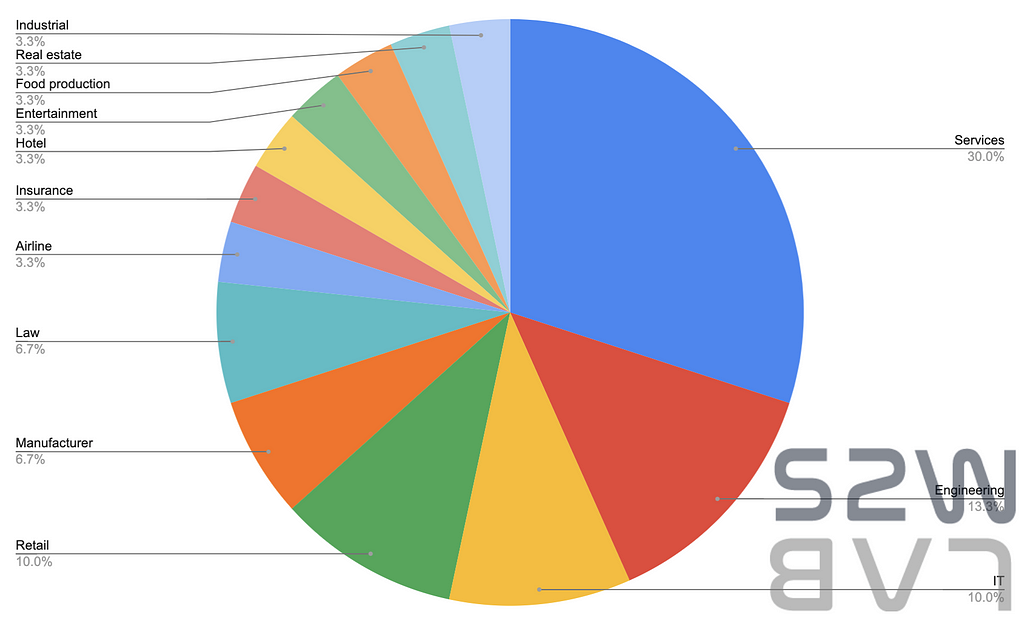
- We are keep monitoring the status of data leak sites operated by ransomware groups and approximately 22 sites operate stably while 6 sites are unstable.
- “Latest Updated” is based on the date the victim’s company information was updated.
Current status of monitoring data leak site operated by ransomware

- Among the currently monitored ransomware leak sites, an average of 22 sites are stable and show steady activity.
2. Posts related to Ransomware threat actors @Dark Web
A. STOP Ransomware
A-1. Summary of STOP Ransomware
- STOP Ransomware was first discovered in February 2018, also known as the Djvu Ransomware.
- STOP Ransomware receives ransom money in Bitcoin.
- As a result of tracking the Bitcoin wallet address that the operator of the STOP ransomware is presumed to be using, the history of Coinjoin of Wasabi Wallet was confirmed (see A-4 for more detail).
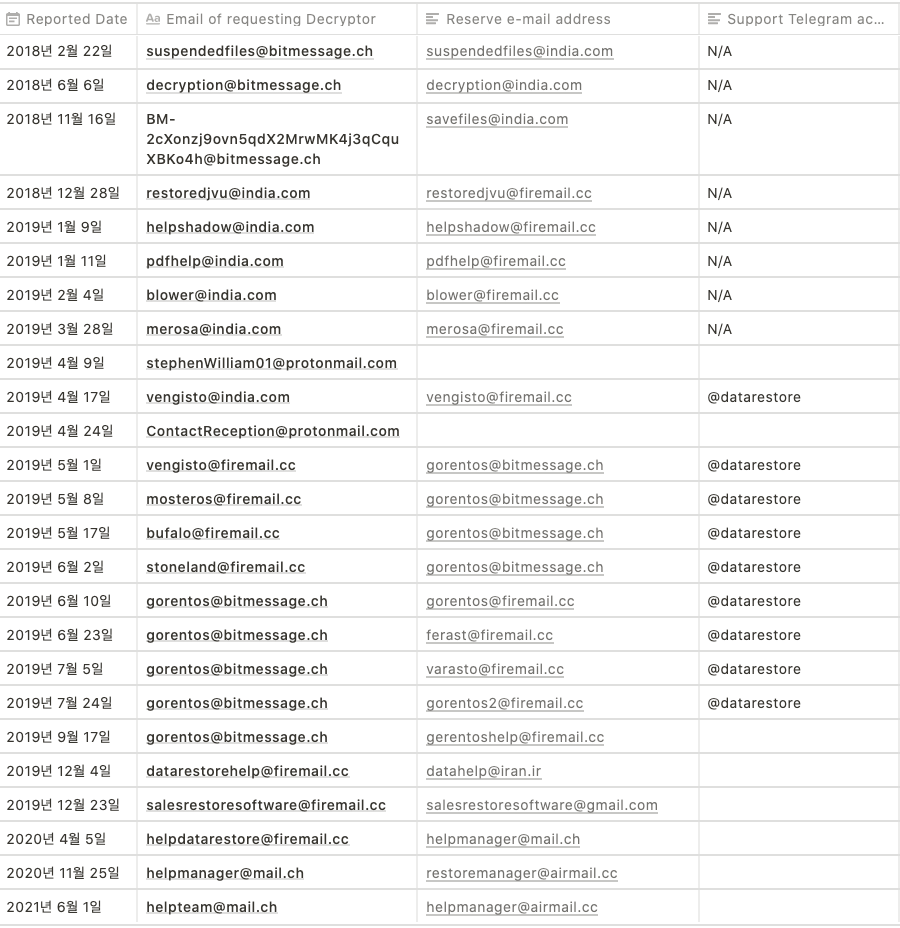
A-2. The history of Ransom note

- In 2019, you can see that my friend has been added at the beginning and the email address to be contacted has changed.
A-3. The information of STOP Ransomware
A-4. Tracing the transaction of Bitcoin wallet related to STOP Ransomware
- Tracing the flow of victims that they paid to STOP Ransomware
- Bitcoin Address : 1HhTu3GAhZ46h5Vur6K9N2kcDMx4dyk83B
- Amount : 0.12 BTC

As a result of the analysis, The operator of STOP Ransomware sent BTC to 1st Manage Wallet Address, and next, they did the function of Coinjoin serviced by Wasabi Wallet
- Manage Wallet : 1B7ijufSMAqJPmntH6xD7eUgH8yWmHfLaL
The remaining about 0.014 BTC went through several wallets and finally flowed to the virtual currency exchanges Huobi and Bitfinex.Huobi Wallet : 1LyMmR62okZXPnLaZPmW9mnVrGBw9im5xo
- Bitfinex Wallet : 36cwj291sykdps7cWGzAGWf3W4tFtLPTMy
B. Qlocker
B-1. Summary of Qlocker
- Qlocker was first discovered in April 2021 and targets QNAP NAS devices. (https://www.qnap.com/static/landing/2021/qlocker/response/en/)
- Attacker uses 7-zip to archive files on infected victims’ QNAP devices into encrypted .7z files.
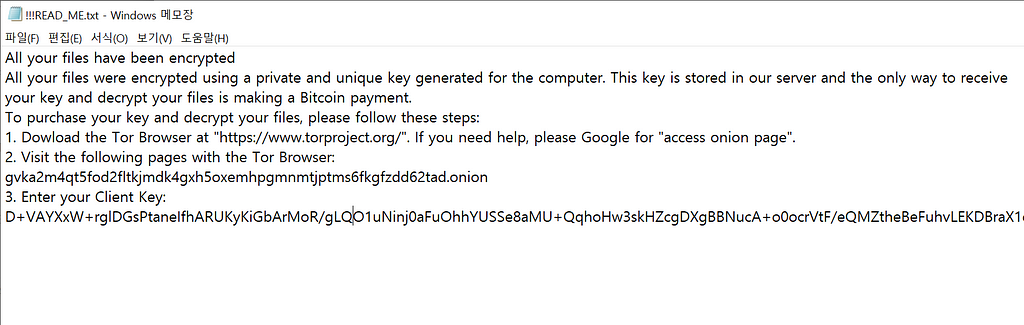
- Victims infected with Qlocker have to pay about 0.01 BTC to the Qlocker operator for decryption, Leaves a ransom note as below.
B-2. Tracing the transaction of Bitcoin wallet related to Qlocker
Bitcoin Wallet address of presumed to have paid by victims.
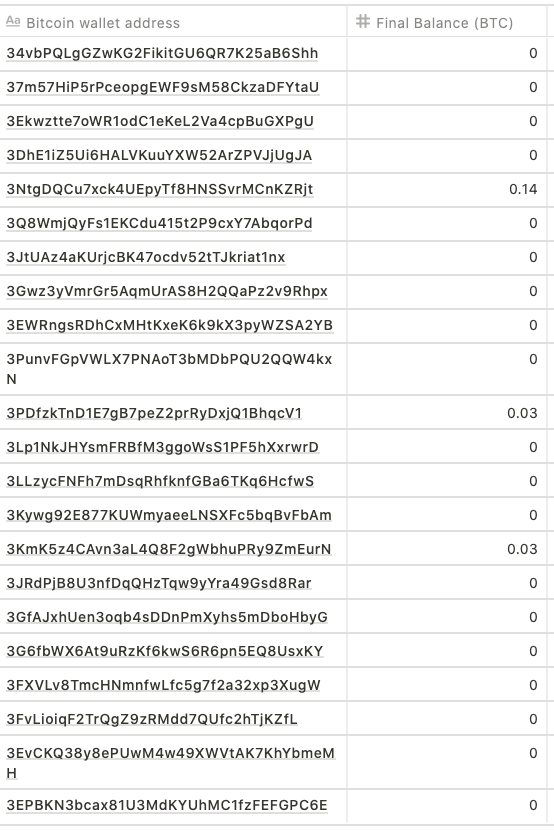
Below is the result of tracing the flow of BTC paid with 22 victim addresses infected by Qlocker.
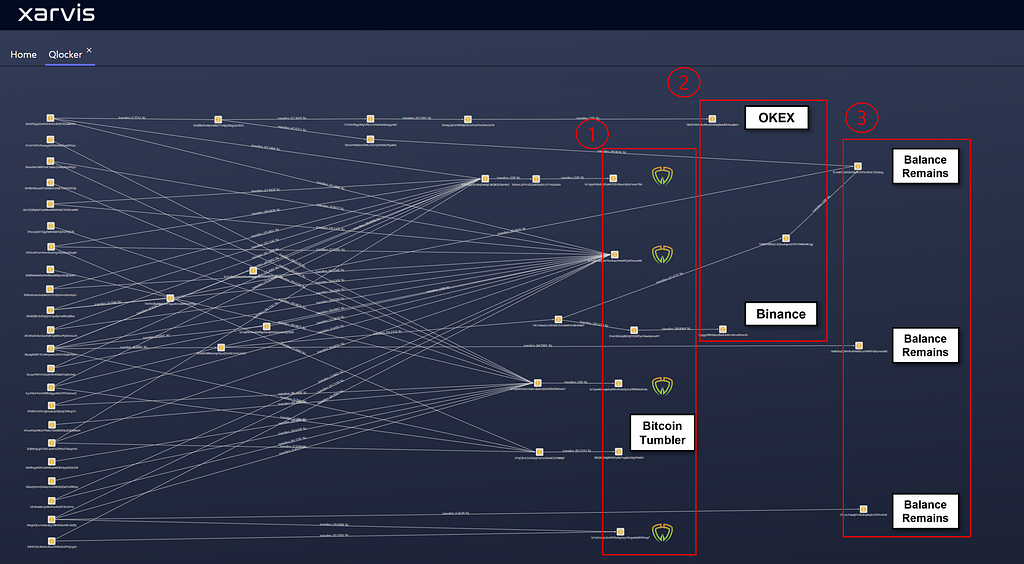
- Qlocker operator collected BTC deposited from different victims to 5 addresses, and then performed mixing through Coinjoin and Tumbler of Wasabi Wallet, respectively.
- Wasabi Wallet : bc1qyydnlds2c622q4rk722m0qum5jcle7suas7f4a
(2.99 BTC) - Wasabi Wallet : bc1qll5cqlej7ke75sz4vyszhwze97jpkt5wusar6k
(4.31 BTC) - Wasabi Wallet : bc1qwk437wgefsqf49rzxhv6sdy3uxhf899vkd2n4a
(3.05 BTC) - Wasabi Wallet : bc1q7mcgcu5rck970zdxgs5py74ugu4e2605l5wxj7
(3.00 BTC) - Tumbler(Mixing) : 38tQNKEt6jBhWbTp8stTwgkkxE2gKPA4KX
(0.06 BTC)
2. Address estimated to be the funds moving to the wallet of the cryptocurrency exchange
- OKEX : 1BtSE7AXX5RuRRcnbhiM3qBwMhEYwxqBsm (0.01 BTC)
- Binance : 3MB2NaZgWrHFo6NWEfLnLNWPXH2RumanWX (0.04 BTC)
3. After the transfer of funds, there is a wallet with no additional transactions or transfers yet.
- 1CnvBFQZ4iS3b5SkGCFDPJmPb3C7Gc82og (1.13 BTC)
- 3MB2NaZgWrHFo6NWEfLnLNWPXH2RumanWX (0.03 BTC)
- 31iUrU1dsetjFH3bc6cqRqXx15YhFmPxi2 (0.05 BTC)
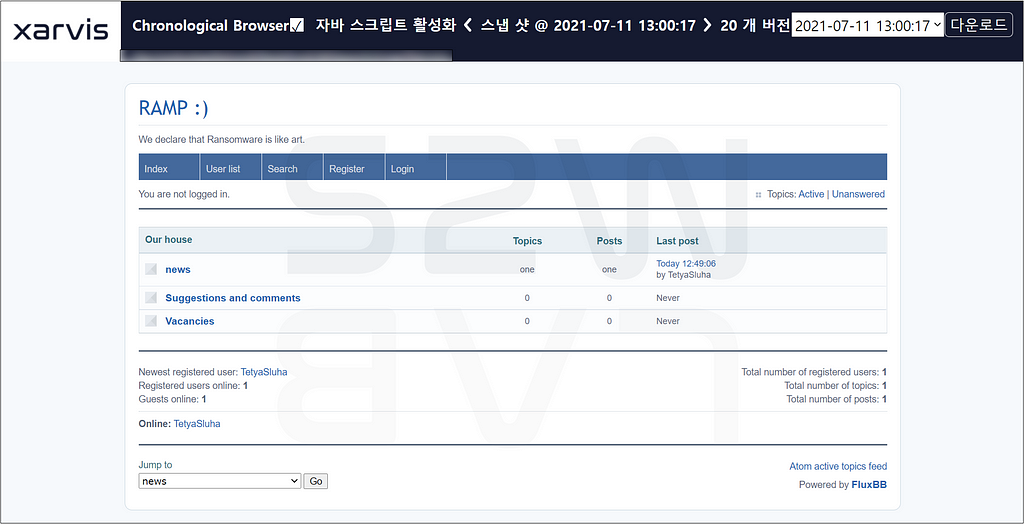
C. RAMP
C-1. Summary of RAMP
- On July 11, 2021, the Tor website, known as Payload.bin (babuk), was rebranded as RAMP, adding a sign-up function and the ability to create posts between members during the rebranding process.
- Babuk ransomware has changed the web interface 4 times so far. There were two rebrandings in this process, and in the process of rebranding, it seems that RaaS service activities will be stopped and a forum on the topic of ransomware will be operated.
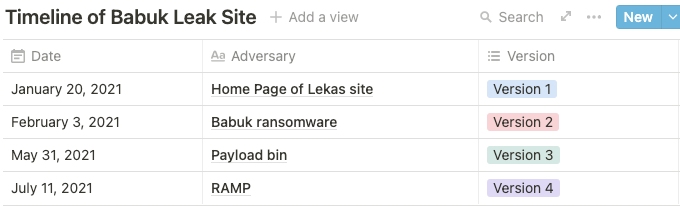
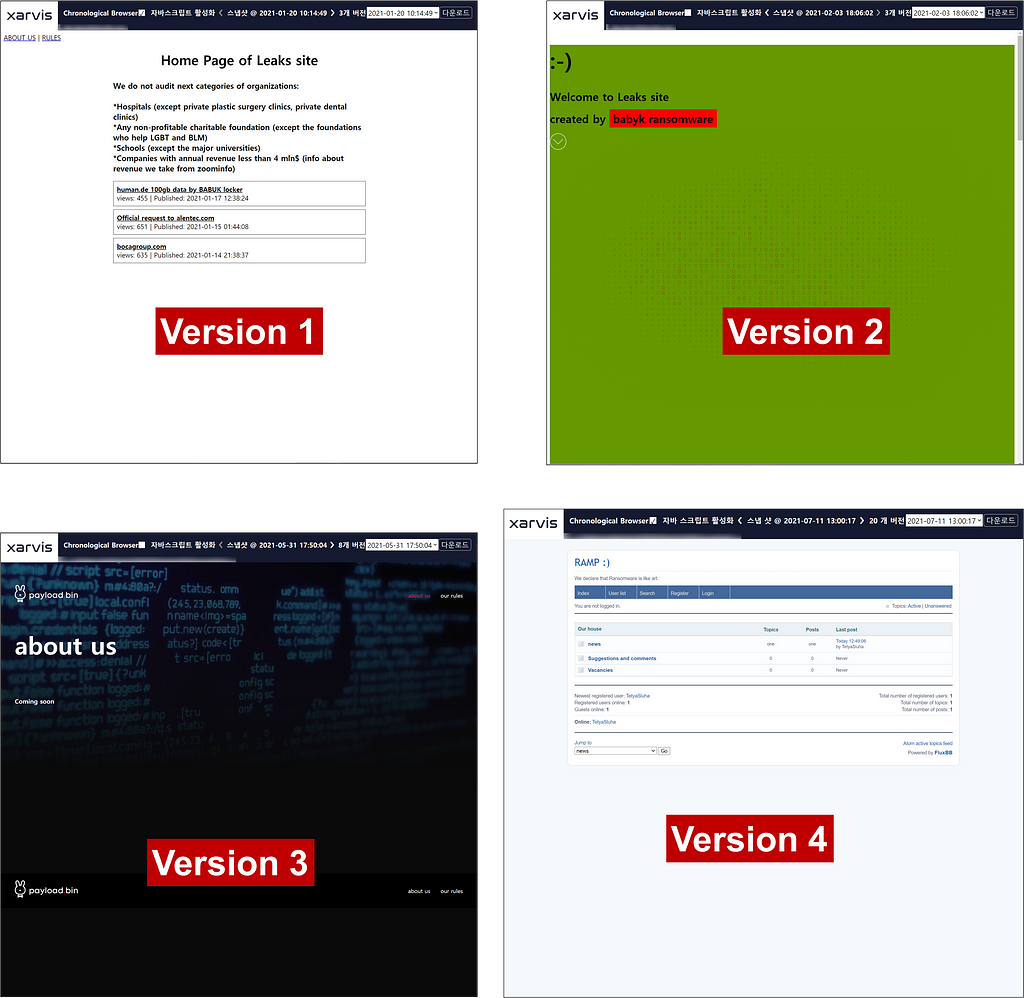
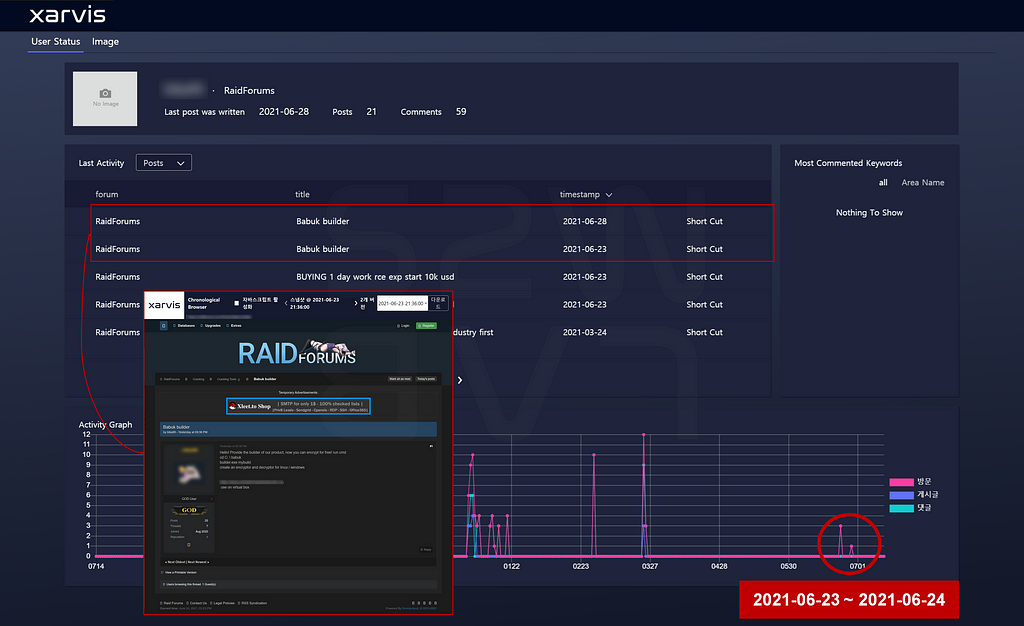
- The rebranded Payload.bin was shut down after 13 days of operation, after which the last activity of the Payload.bin operator identified on Xarvis revealed the Babuk ransomware builder on the deep web Raidforums.

C-2. Rebranding (PayloadBin -> RAMP)
- On July 11, 2021, the Tor website, known as Payload.bin (babuk), was rebranded as RAMP, adding a sign-up function and the ability to create posts between members during the rebranding process.
- Through this, it appears that the site has been changed to a forum for ransomware activity rather than data leakage site.
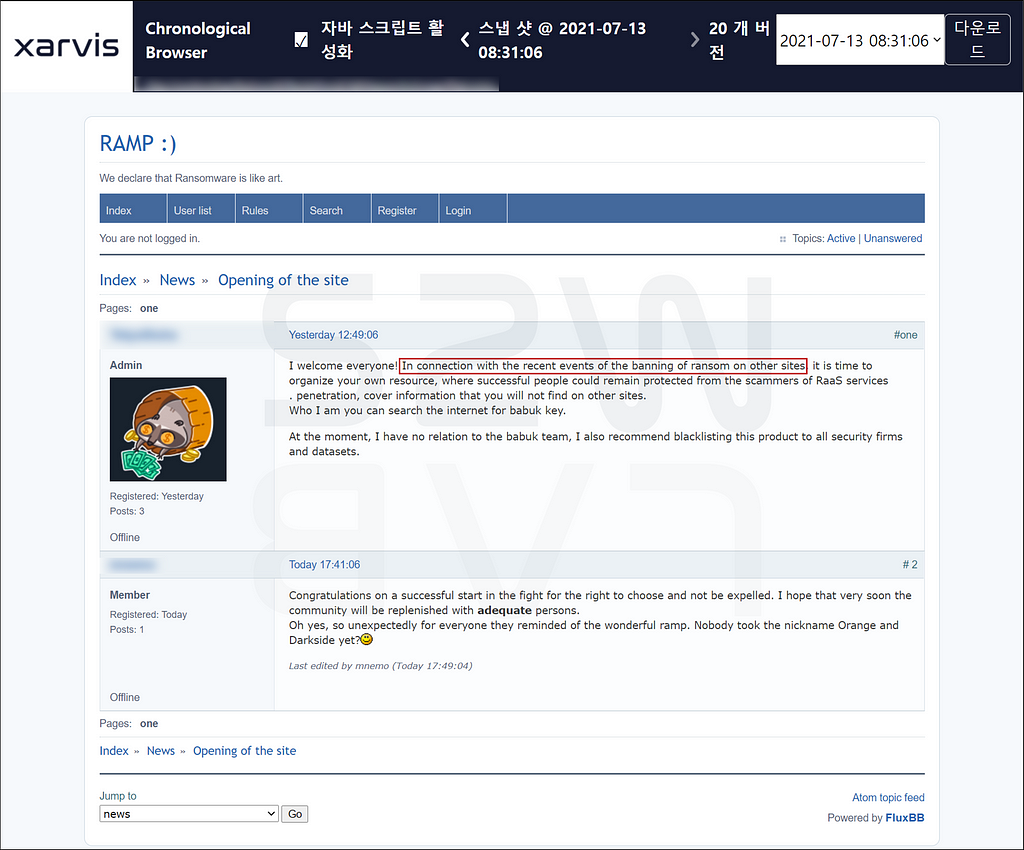
- According to a post by the AMP operator, it was created “to protect against fraudulent RaaS and ransomware partner job advertisements on deep web and dark web forums”, which were banned after the Colonial Pipeline incident.
D. The case of Ransomware scam
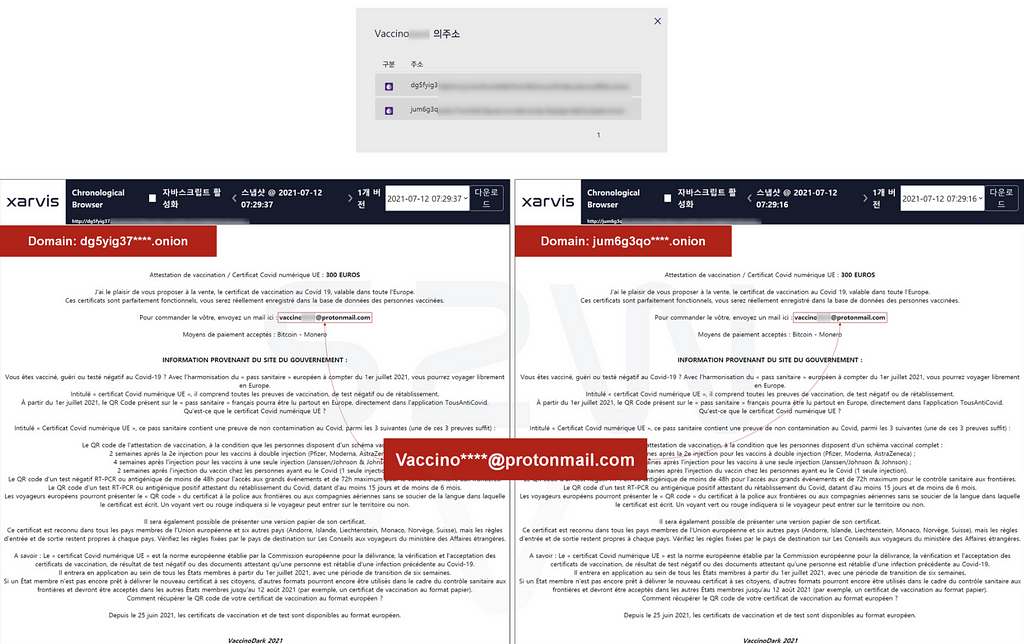
- On the dark web, there are often scam suspicious sites that abuse the characteristic of being difficult to track.
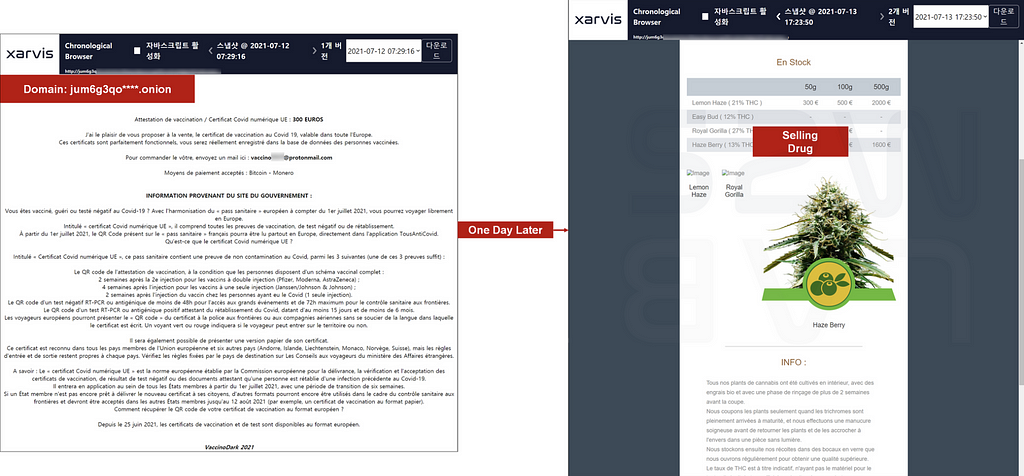
- The websites below appear to be selling counterfeit vaccination certificates on two websites by the same user (Vaccino****@protonmail.com) with different onion addresses (page created on July 12, 2021)
- One of these pages quickly turns into ransomware selling site, which is highly likely to be a scam targeting dark web users taking advantage of the popularity of ransomware.
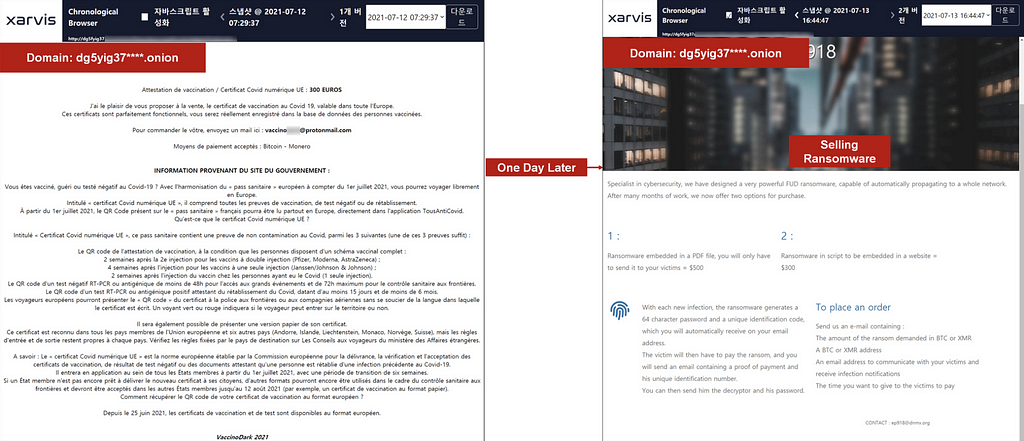
- The same two sites shown above are changed to a ransomware sale site and a drug sale site, respectively, as shown below after a day
(All the cases D-1 and D-2 below changed on 2021.07.13)
D-1. Case 1: Domain: dg5yig37****.onion
- Date: 2021.07.13
- Changed to ransomware site.
D-2. Case 2: Domain: jum6g3qo****.onion
- Date: 2021.07.13
- Changed to drug site.
E. REvil
E-1. REvil disappeared on Deep Dark Web
- It was confirmed that REvil was continuing its activities by disclosing the affected company until July 11, 2021
- Although active until recently, all infrastructure, including leak site, has been down since July 12
- This suggests that there is a possibility that they may have stopped their activities or were arrested by the investigative agency.

- Currently, there are no reports of REvil’s expression of this position or arrests by investigative agencies, and the fact that he was Banned was confirmed in the Deep Web Forum

- Social media and some articles claim that REvil has been suspended or shut down.
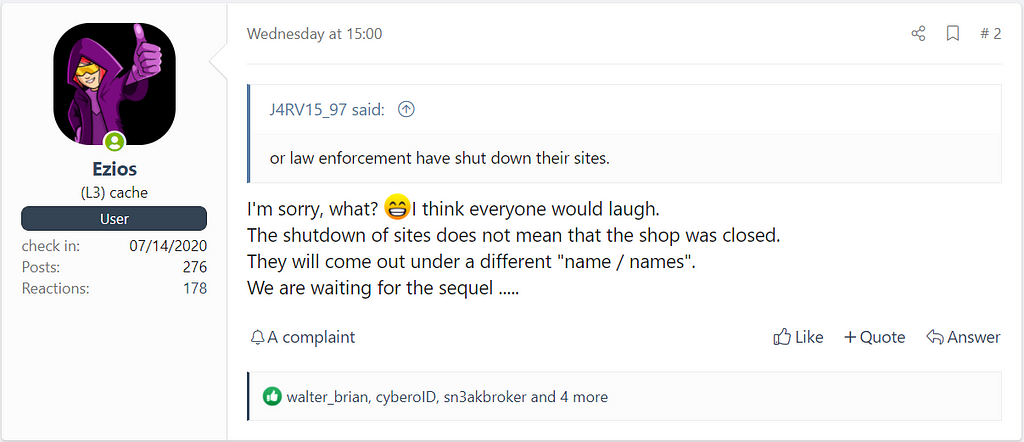
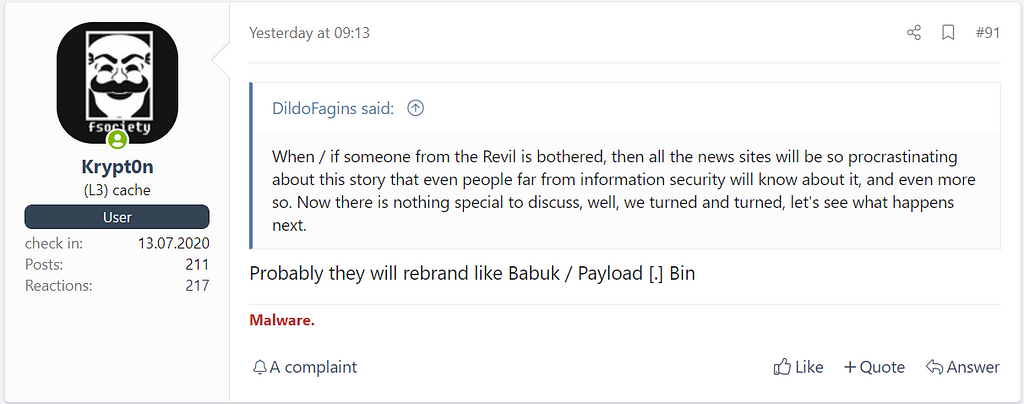
- According to sellers and users active on the deep web forums, there are also opinions that REvil will be rebranded as Babuk / Payload.bin / RAMP.
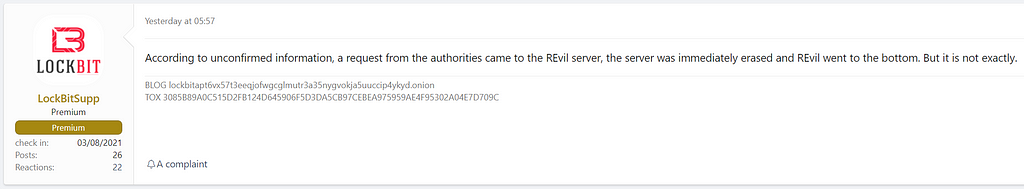
- The LockBit operator has not been confirmed, but rumored information suggests that REvil’s servers were immediately taken down and were presumed to be shut down due to pressure from the authorities.
E-2. Status of victimized companies and institutions infected by REvil
The number of institutions, companies, and countries that Revil attacked during the period of activity on the dark web (2019.04 ~ 2021.07) for about 1 year and 3 months is as follows
- Total number of infected companies : 264
- Total number of infected countries : 36

- Manufacturer was the hardest hit, but across a wide range of industries.
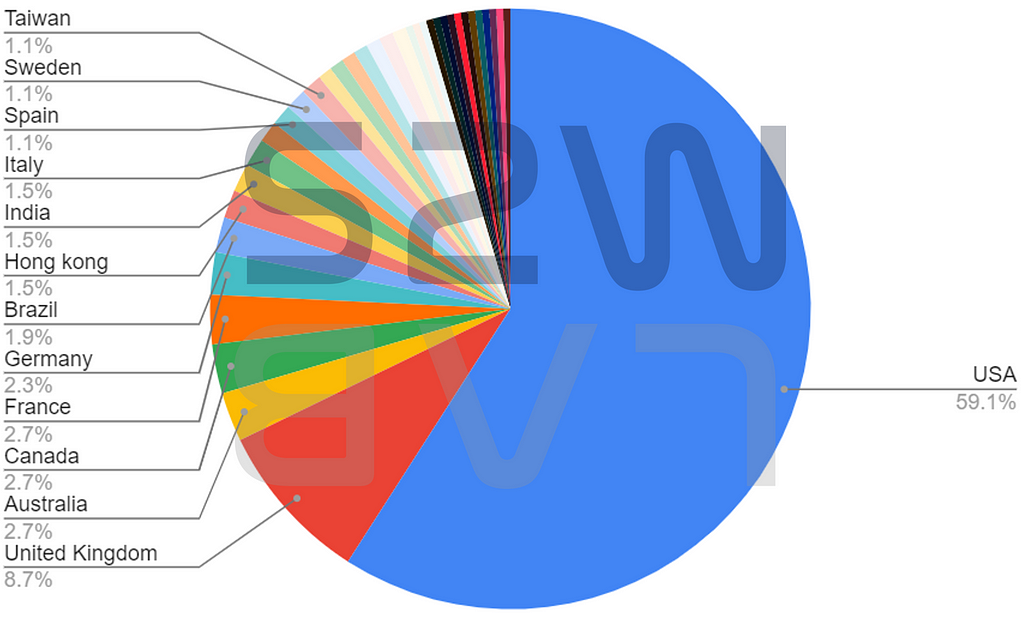
- The United States, which accounted for 59.1% of all affected countries, suffered the most, and again, Russia (Eastern Europe) showed no cases of infect.
Conclusion
- As the reason for REvil’s sudden disappearance has not yet been clearly identified, it remains to be seen whether it will reappear under a new name or disappear into history.
- Since there is a possibility that those who have lost their way due to the prohibition of ransomware-related activities in the existing dark web forums may gather in the newly rebranded RAMP, continuous monitoring of users and posts in RAMP forum is necessary.

- Homepage: https://www.s2wlab.com
- Facebook: https://www.facebook.com/S2WLAB/
- Twitter: https://twitter.com/s2wlab
W3 July | EN | Story of the week: Ransomware on the Darkweb was originally published in S2W LAB BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: W3 July | EN | Story of the week: Ransomware on the Darkweb | by Hyunmin Suh | S2W BLOG | Medium