Virus Bulletin Conference — Day 2
EVILPLAYOUT: ATTACK AGAINST IRAN’S STATE TV AND RADIO BROADCASTER Alexandra Gofman, Israel Gubi & Itay Cohen

- The presentation had lots of new research, not included in the paper. I hope they’ll publish that soon.
- Several different hacktivist groups managed to perform wide-range attacks in Iran e.g. take control of all IP cameras of a prison, control a steel manufacture, block a significant amount of gas pumps in the country, hacking of state’s TV and radio broadcast etc. IMHO, this research is perfect counter-example to hacktivist groups not being skilled.
- To my understanding, the malware samples were uploaded to VirusTotal, possibly by the authors themselves, very quickly after the attacks. I hadn’t ever thought a malware author would willingly upload his/her malware to VT to “prove” authorship
- The authors also uses wipers. In this case, the wipers aren’t so much to cover their traces, but rather to destruct as much as possible the systems they attack.
RUSSIAN WIPERS IN THE CYBERWAR AGAINST UKRAINE Alexander Adamov
- This paper is a comprehensive study of Russian wipers deployed against Ukraine in 2022. The discovery of wipers themselves was done by researchers at ESET and Microsoft.
- A crypto implementation error in HermeticRansom wiper made it possible to create a decryptor.
THE LONG ARM OF THE PRISONER: SOCIAL ENGINEERING FROM KENYAN PRISONS Patricia Musomba & Tim Dagori
- Prisoners in kenyan prisons use smuggled phones to carry out social engineering scams.
- The scams are not new and rely on well-known tactics (e.g. send money to transfer an alleged lottery prize).
- What’s new is the fact the operations are done by prisoners + the extent of fraud: affecting 1 in 2 kenyan using mobile payment.
WAR OF THE WORLDS: A STUDY IN A RANSOMWARE IR LEARNINGS & VICTORIES Peter Kruse & Jan Kaastrup

- Side joke: for me, “IR” is infra-red. I’ve got to focus, this is Incident Response
- According to the authors, “most attacks could have been prevented or damage reduced if a 24/7 detection and response was implemented”
- They monitored a ransomware attack, starting unfortunately from outside the monitored perimeter. After a while, the ransomware started pushing on desktops on the network and encrypting data. The encryption was contained and stopped on devices which were monitored, while it completed in 3–4 hours on un-monitored hosts.
- The attackers were uploading the encrypted data to a Dropbox account. The authors managed to get the account closed, shutting down the attackers from their potential revenue.
EXPLOITING COVID-19: HOW THREAT ACTORS HIJACKED by Daniel Blackford and Selena Larson
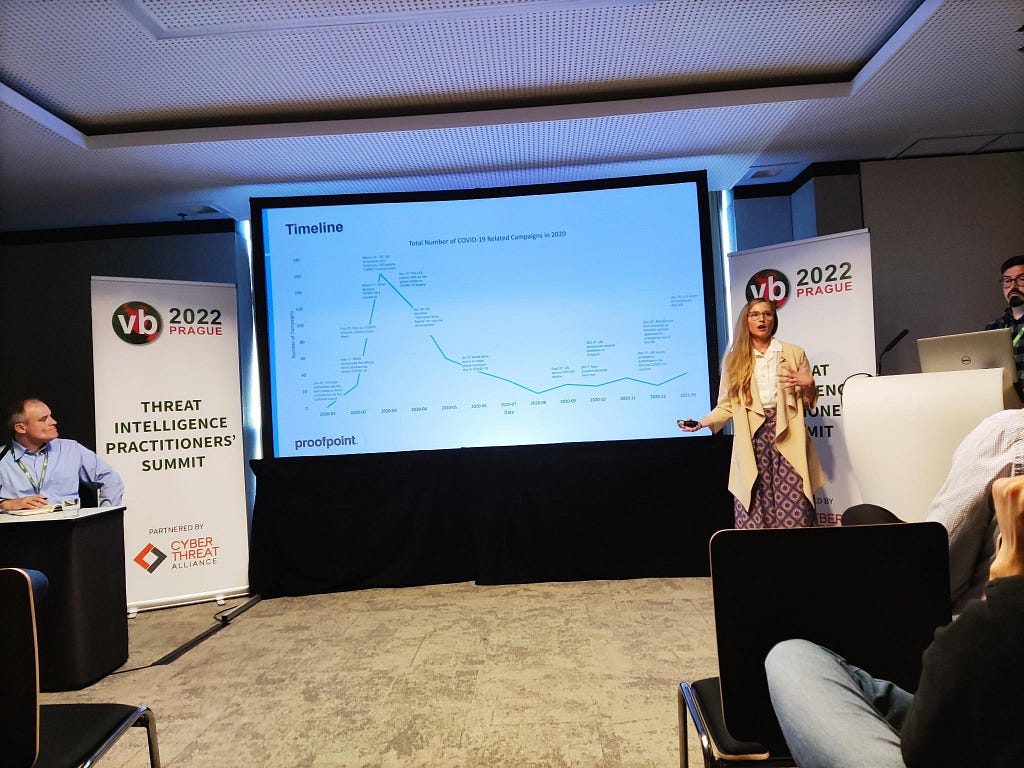
- The authors study email campaigns mentioning COVID-19 themes since 2020.
- Most threat actors used the COVID theme. When they used it, it was more efficient than other themes.
- Among the COVID theme variants, the ones involving company operations were particularly numerous.
Article Link: Virus Bulletin Conference — Day 2 | by @cryptax | Sep, 2022 | Medium