Using Jupyter Notebook for CTI using PyMISP
In Cyber Threat Intelligence (CTI), Jupyter Notebook and PyMISP are transformative tools. Just as Bash commands empower defenders, these platforms offer dynamic solutions for analyzing threats, collaborating effectively, and fortifying cyber defenses.
Jupyter Notebook’s interactive environment merges code and narratives, while PyMISP provides seamless access to threat intelligence via MISP. Together, they enable agile responses to digital threats, shaping a new frontier in CTI practices.

PyMISP illustration by Bing Image Creator
In this blog post, we will delve deeper into leveraging Jupyter Notebook alongside PyMISP for Cyber Threat Intelligence purposes.
What is Jupyter Notebook?
The Jupyter Notebook is a standard tool for creating notebook documents. These documents feature code, mainly in Python but not restricted to it, and combine it with text, images, and equations. Then, showcase the code and its corresponding output side by side, creating a cohesive narrative of the computational process.
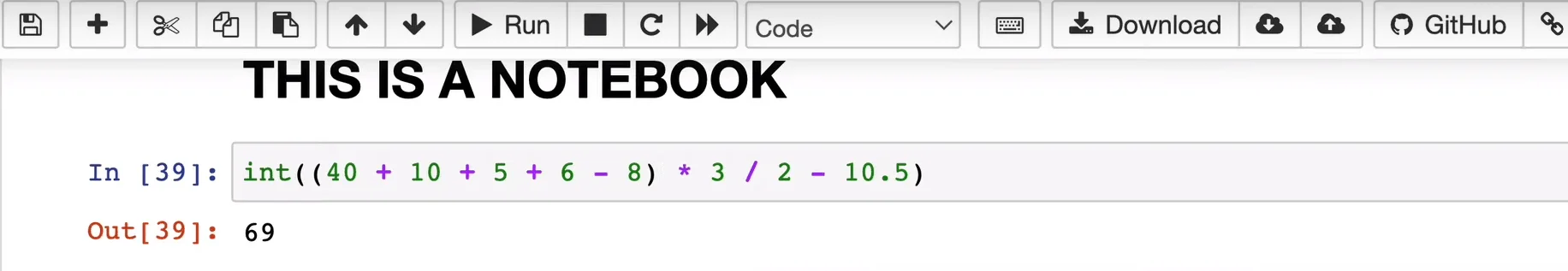
An example of a Jupyter Notebook format
CTI Operational Procedures with Jupyter Notebook
In Cyber Threat Intelligence (CTI), users can manifest operational procedures through Playbooks, Standard Operating Procedures (SOP), or Workflows. While each may differ in structure and function, they collectively serve as consistent guides for executing activities effectively and repeatedly, ensuring automation.
Incorporating Jupyter Notebooks into CTI operational procedures enhances the efficiency and effectiveness of threat intelligence practices. Here’s how:
- Utilizing the capabilities of Jupyter Notebook, users can conduct threat hunting activities, automate repetitive tasks, and analyze extensive datasets. By merging live code with explanatory text, they can document their methodology and share insights with colleagues effectively.
- Jupyter Notebooks are a conduit for integrating with diverse Threat Intelligence (TI) providers. Users query multiple TI repositories, investigate Indicators of Compromise (IoCs), and gather pertinent threat intelligence seamlessly.
- Jupyter Notebooks excel in advanced hunting scenarios, including using advanced hunting capabilities offered by platforms like Microsoft Threat Protection (MTP). Analysts leverage Jupyter Notebooks to execute intricate queries on security events and telemetry data, helping with identifying and mitigating potential threats.
Threat hunting represents a proactive cybersecurity strategy aimed at actively seeking out potential threats within an organization’s network and systems. To facilitate this process with an easier approach, you can leverage SOCRadar’s Threat Hunting module.
With the Threat Hunting module, you can conduct word-based searches, tapping into SOCRadar’s extensive data repository. SOCRadar’s intelligence is based on big data collected by selected research analysts and automated tools configured by expert analysts; it includes the latest vulnerabilities across diverse products and operating systems, as well as IoC, botnet data, IAM data exposure, PII data exposure, and information from the black market.
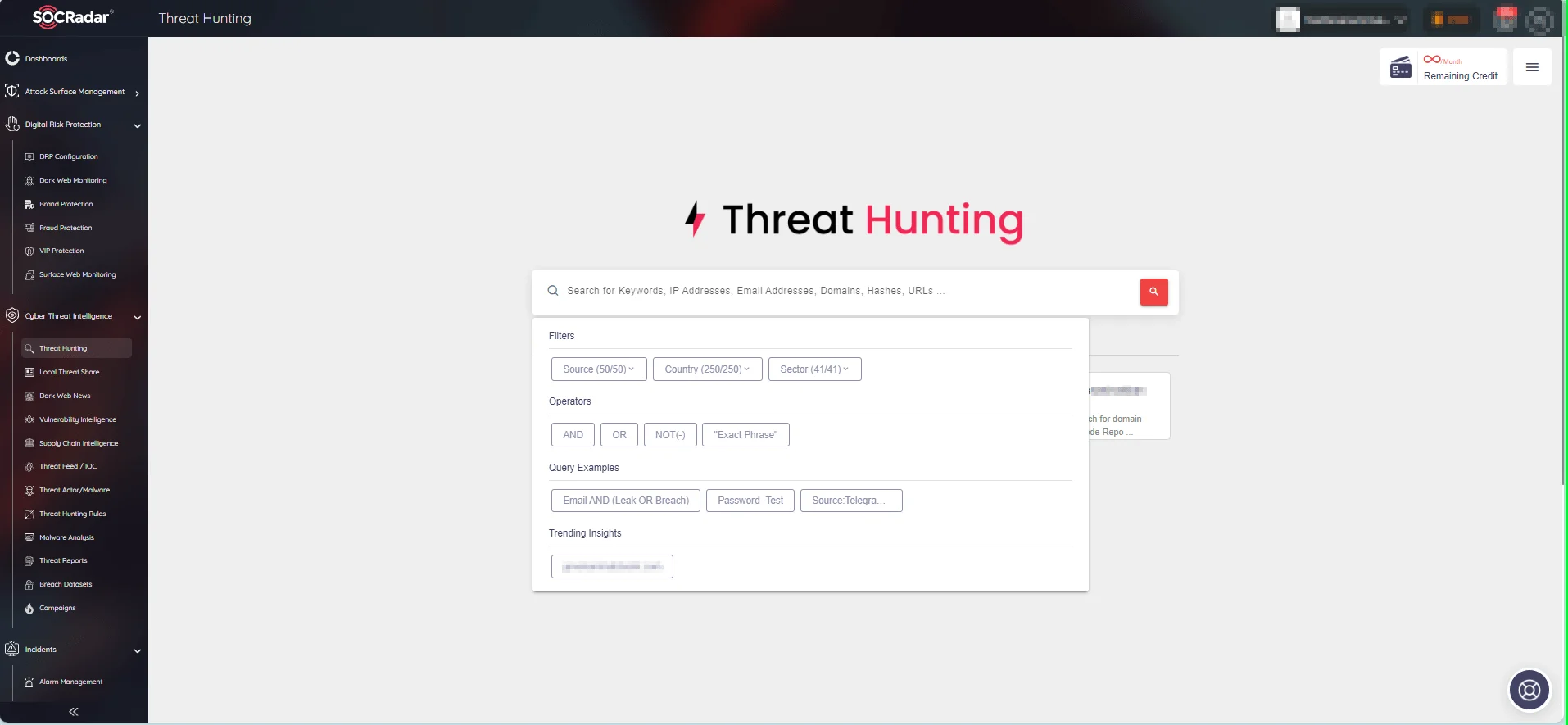
SOCRadar Threat Hunting Module
Learn more about SOCRadar XTI’s Threat Hunting capabilities on our blog post: How SOCRadar Can Help You with Threat Hunting?
Exploring PyMISP: A Python Library for MISP Integration
PyMISP Library
PyMISP emerges as a Python library designed to interact with MISP platforms via their REST API. This library empowers analysts to manipulate data, add new intelligence, and integrate with MISP repositories. With PyMISP, analysts can retrieve events, update attributes, manage samples, and execute attribute searches effortlessly.
CTI Operational Procedures with PyMISP
- Running Jupyter Notebooks directly from the MISP server poses inherent security risks, potentially exposing the server to remote code execution vulnerabilities. Instead, it is encouraged to execute Jupyter Notebooks from separate, managed environments. API keys or URLs facilitate access to the MISP server, ensuring a secure workflow.
- Jupyter Notebooks inherently support single-user access. To acclimate multiple users, organizations may consider using JupyterHub, a multi-user server for managing Jupyter Notebooks.
- Given the sensitive nature of credentials required for PyMISP integration (API keys, MISP URLs), it’s imperative not to store them directly within the notebook. Instead, adopt secure credential management practices, such as storing credentials in separate files and accessing them using secure methods.
Automation and Orchestration
Automation plays a pivotal role in streamlining CTI workflows and reducing response times to potential threats. Jupyter Notebook, coupled with PyMISP, enables the automation of repetitive tasks, such as data ingestion, enrichment, and analysis.
Users can create scripts and workflows to automate the retrieval of threat intelligence feeds, the enrichment of security events with contextual information from MISP, and the execution of predetermined reaction actions by operating Python’s scripting capabilities within Jupyter Notebook.
Integration with Machine Learning and AI
Techniques for Artificial Intelligence (AI) and machine learning have great potential to improve CTI capabilities. The Jupyter Notebook offers an ideal environment for building predictive models, testing with machine learning methods, and detecting anomalies in security telemetry data.
By integrating PyMISP with machine learning libraries such as scikit-learn, TensorFlow, and PyTorch, analysts can enhance threat detection capabilities, identify emerging patterns of malicious behavior, and proactively defend against sophisticated cyber threats.
Exploring Examples for Using Jupyter Notebook for CTI
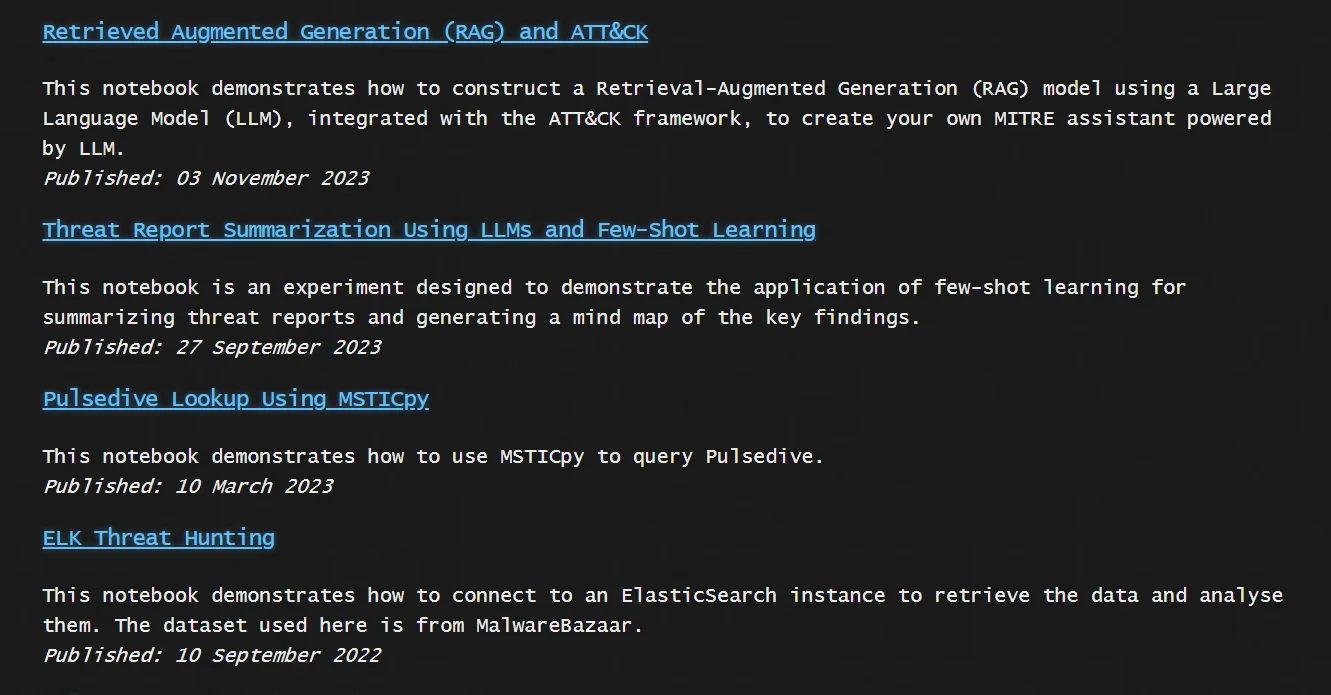
Some examples of Jupyter Notebook usages (Source: securitybreak)
1- Jupyter Notebook is a powerful tool for creating threat report summaries and facilitating the consolidation and analysis of vast threat intelligence data. Projects like “The Intel Brief Newsletter” showcase its exemplary use, where Jupyter Notebook, aided by Artificial Intelligence (AI) algorithms, enhances the process of summarizing threat reports.
This document exemplifies the application of Jupyter Notebook in using Large Language Models (LLMs), such as GPT-4, to distill key insights from lengthy threat reports such as Indicators of Compromises (IoCs) and Tactics, Techniques, and Procedures (TTPs).
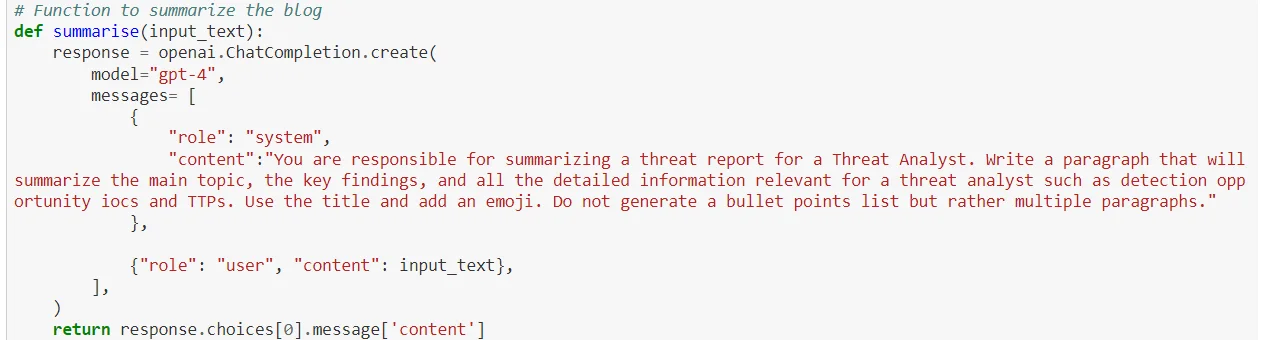
An example of a code used in Jupyter Notebook for Threat Report Summarization.
2- Another notebook explores the Conti Jabber leaks to provide a comprehensive analysis workflow. It covers data transformation, Jabber logs visualization, and extracting relevant Indicators of Compromise (IoCs) for threat intelligence purposes.
The extraction of IoCs from threat reports uses the MSTICpy library. This notebook efficiently demonstrates how to retrieve IoCs from URLs, although it may encounter false positives due to its early-stage development. The process involves leveraging the IoCExtractor module from MSTICpy to enhance threat intelligence gathering and analysis.
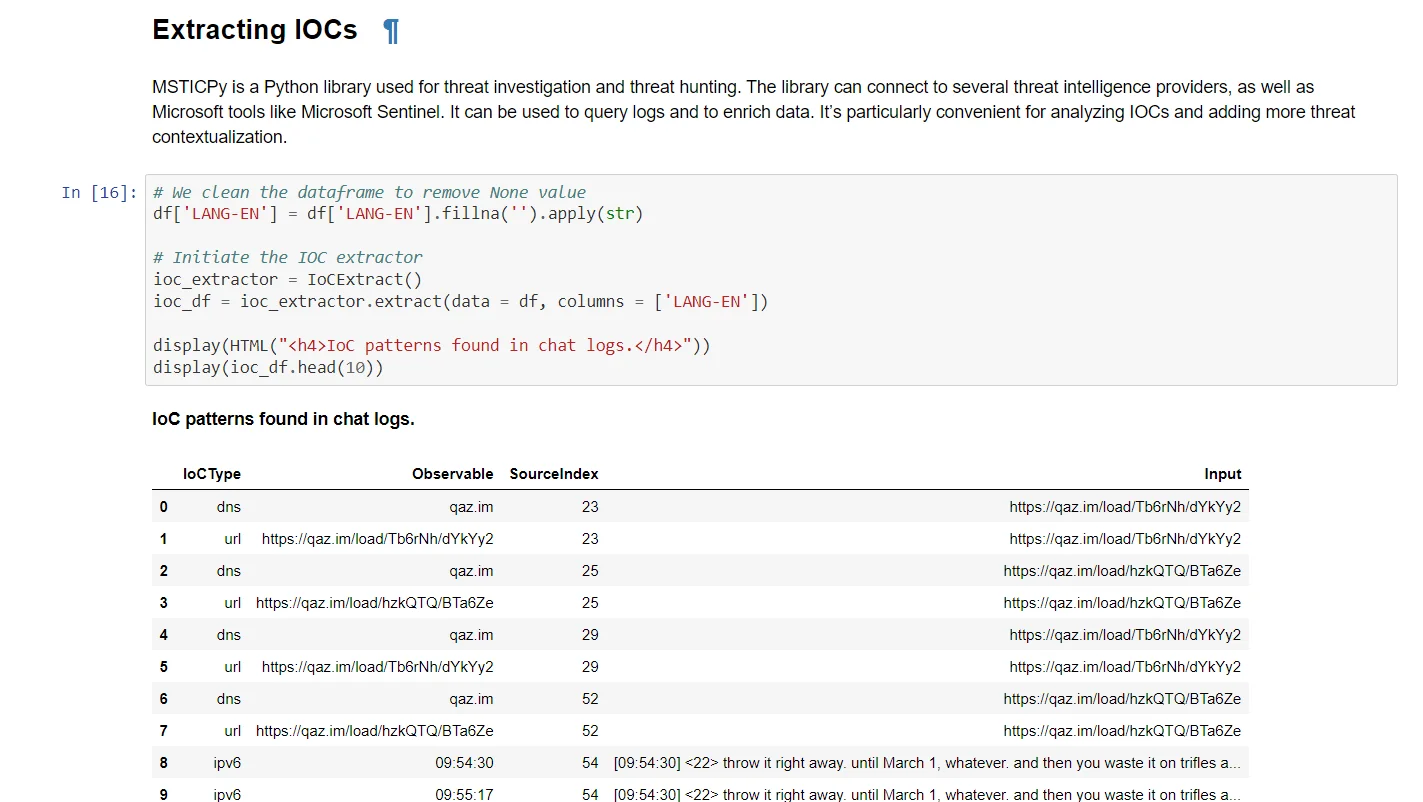
Jupyter Notebook example that showcases some IoC patterns, (Source).
SOCRadar’s Threat Feed & IoC Management module revolutionizes IoC discovery, empowering cybersecurity teams to swiftly locate Indicators of Compromise (IoCs) with unparalleled efficiency. By consolidating threat intelligence sources into a unified platform, security professionals streamline their IoC searches, saving valuable time and effort. You can search for IoCs in SOCRadar platform to find their connections to Threat Actors/Malware.
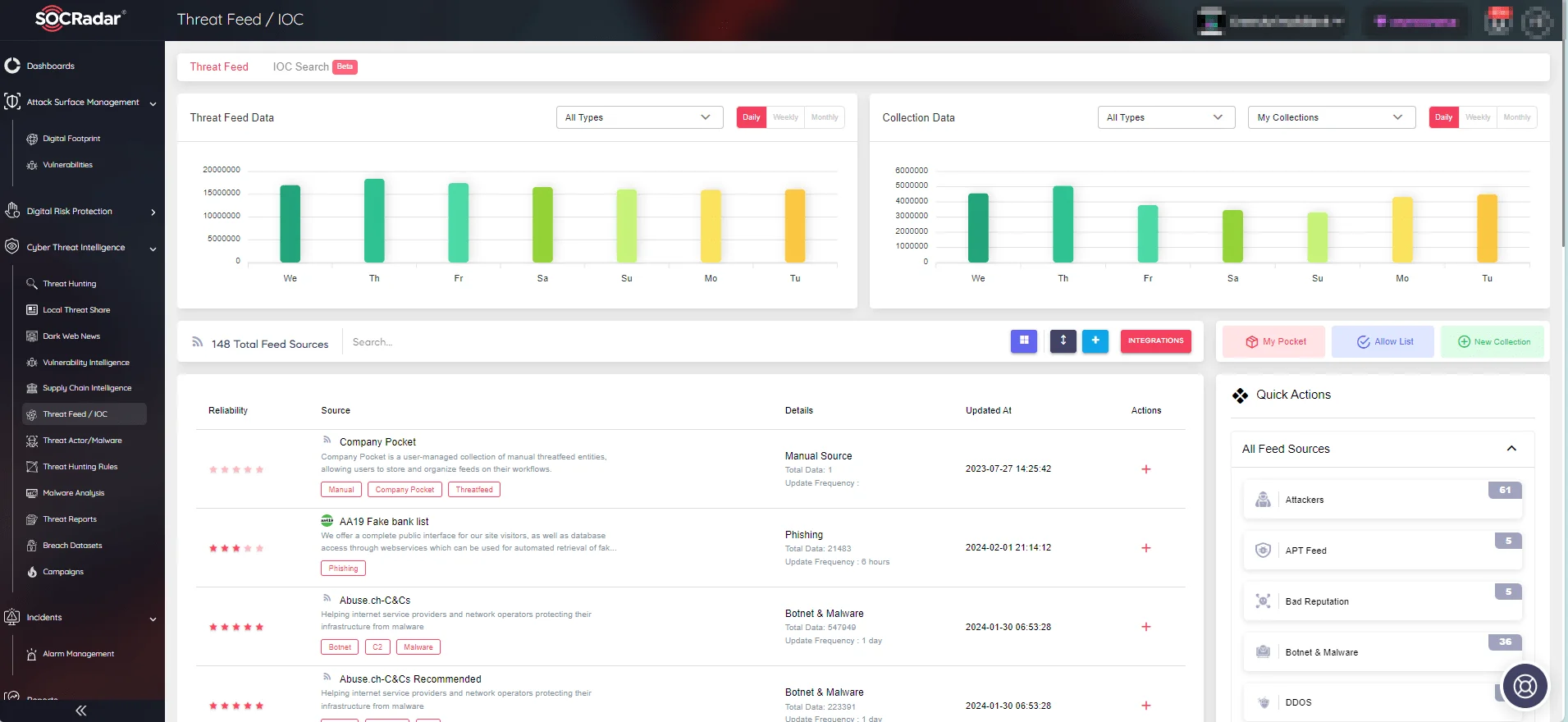
SOCRadar’s Threat Feed & IoC Management module
3- Another notebook exemplifies how MSTICpy can be employed in threat hunting, particularly in malware analysis. It offers insights into the utilization of YARA rules, providing a comprehensive approach to identifying and mitigating potential threats within the cybersecurity landscape.
Imports for the malware analysis
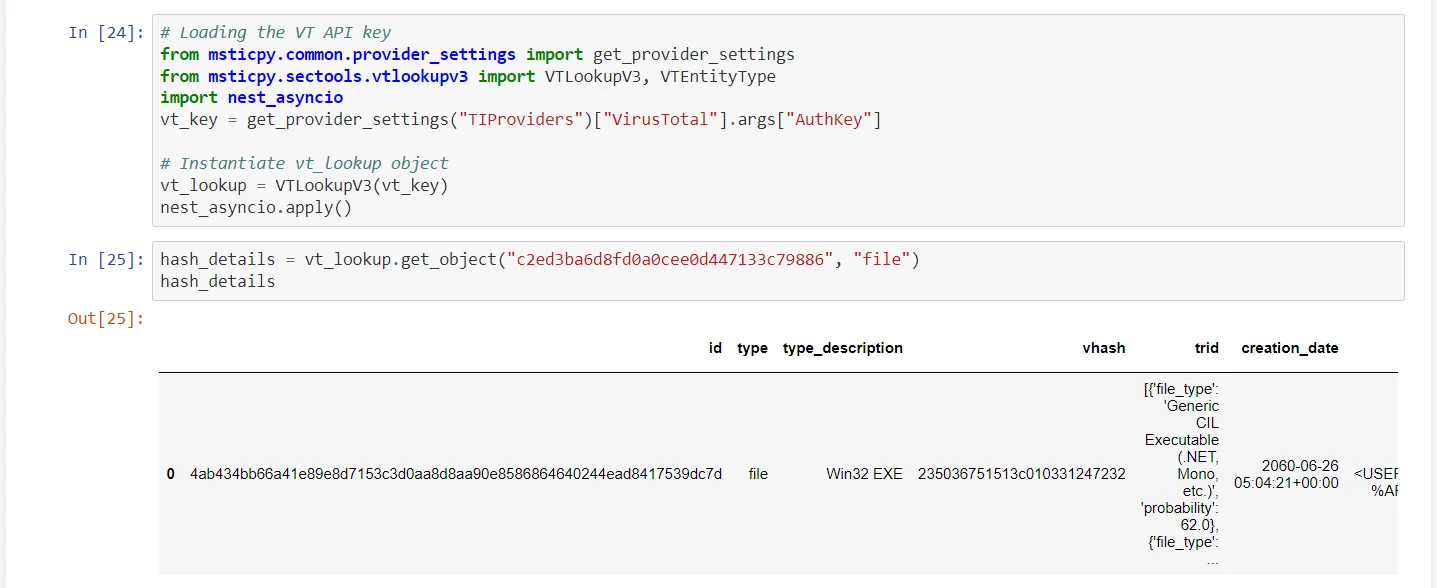
Using VT API for malware analysis, (Source)
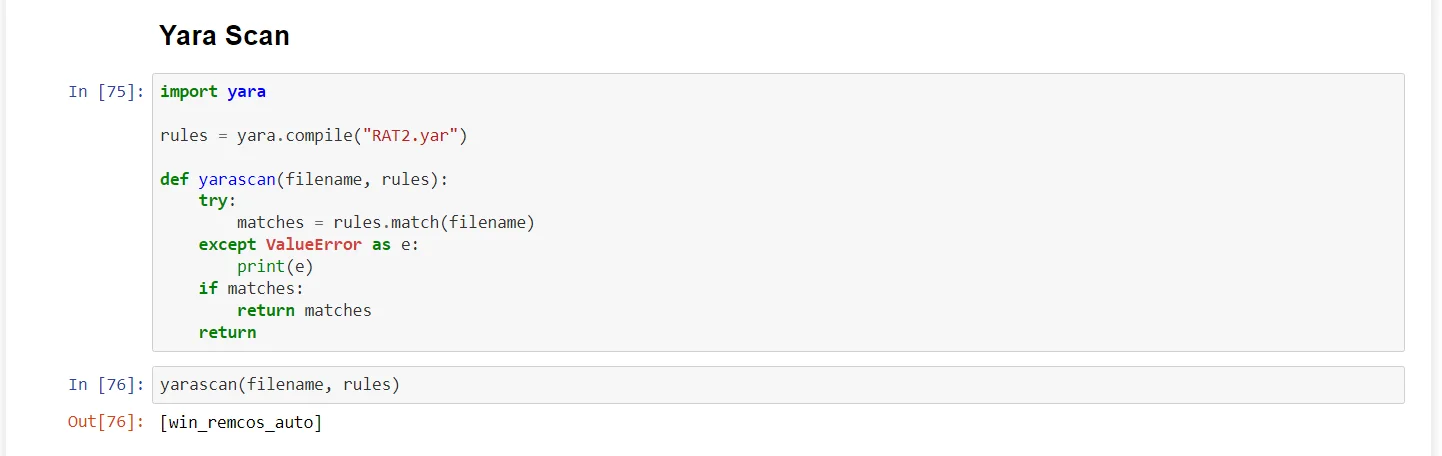
Checking for YARA rules in files
Conclusion
In conclusion, the integration of Jupyter Notebook and PyMISP into the Cyber Threat Intelligence (CTI) workflow heralds a transformative era marked by innovation, agility, and collaboration, which provides a robust framework for proactive threat mitigation and response, from threat hunting and investigation to vulnerability analysis and intelligence sharing.
The interactive environment of Jupyter Notebook, coupled with its seamless integration with MISP through PyMISP, empowers analysts to conduct advanced threat analyses, automate repetitive tasks, and leverage machine learning techniques for enhanced threat detection. This paradigm shift enables organizations to elevate their CTI capabilities to new heights, fostering a more resilient cybersecurity posture in the face of evolving threats.
In essence, the marriage of Jupyter Notebook and PyMISP signifies a convergence of tools and methodologies, enabling defenders to stay ahead in the ever-evolving landscape of cybersecurity.
Article Link: https://socradar.io/using-jupyter-notebook-for-cti-using-pymisp/
