Dynamically unpacking using x64-dbg

Introduction
In this blog, i will be uncovering up techniques that can be used for unpacking trojan “Polyglot Duke” developed by APT29 ( The Dukes / Cozy Bear) attributed as Russia’s Foreign Intelligence Service (SVR).
Information Gathering
Let first look up the file in the PE Studio. It’s 64-bit loader of PolyglotDuke.
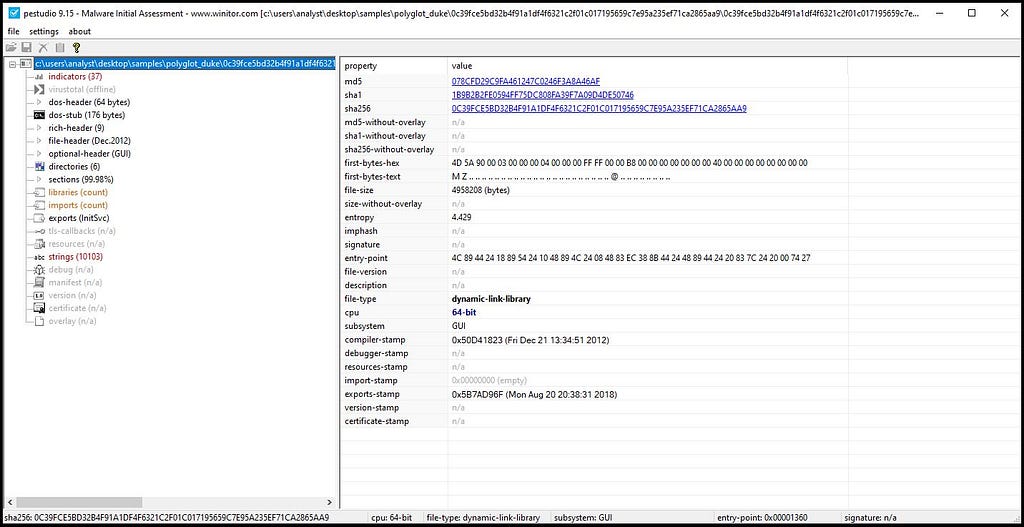 Obtaining information on loader using PE Studio.
Obtaining information on loader using PE Studio.Setting up environment for Unpacking
Firstly uncheck the System Breakpoint from Setting by going into Options-> Preferences in x64-dbg.
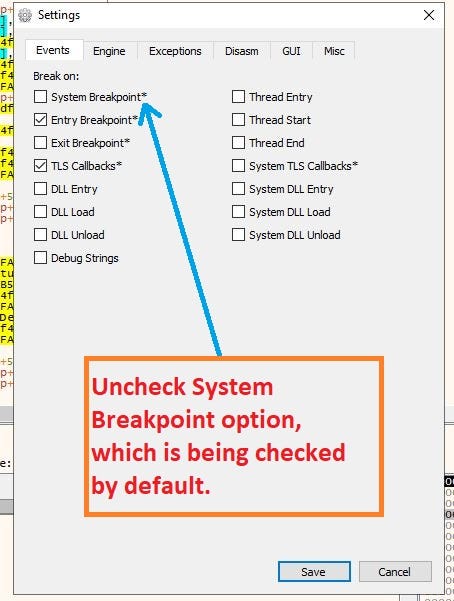 Go to Break on: uncheck System Breakpoint.
Go to Break on: uncheck System Breakpoint.Next thing that needs to be done is setting the breakpoints in the binary.
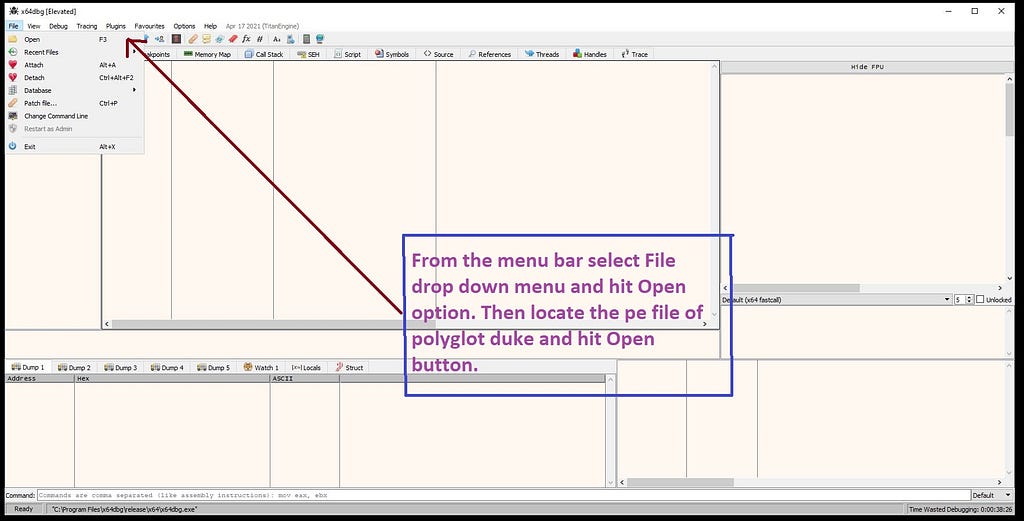 Open PolyglotDuke Loader from Disk.
Open PolyglotDuke Loader from Disk.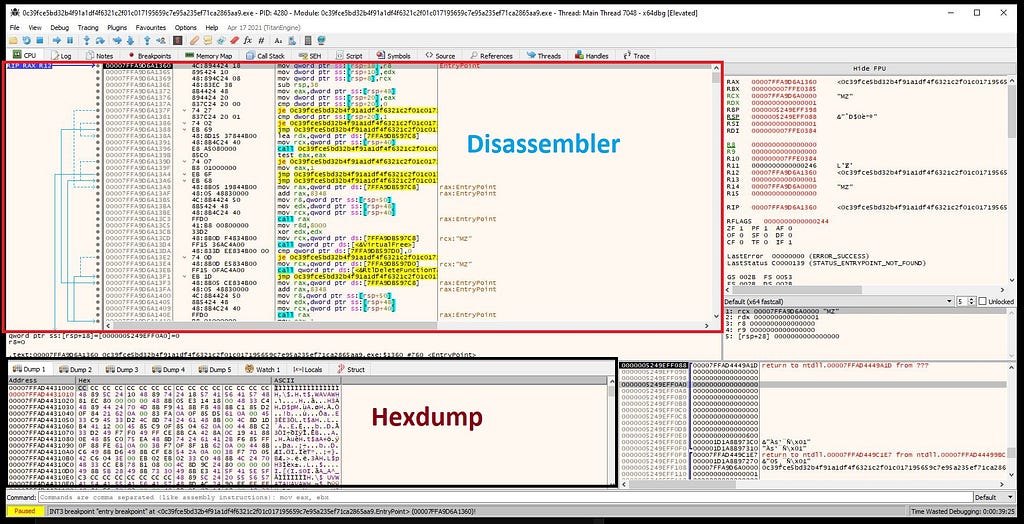 look of x64-dbg when loader is loaded.
look of x64-dbg when loader is loaded.In the command palette, type “bp” { breakpoint API }.
 Command palette at the bottom of x64-dbg.
Command palette at the bottom of x64-dbg.In this case , it will be as
bp VirtualAlloc
bp VirtualProtect .
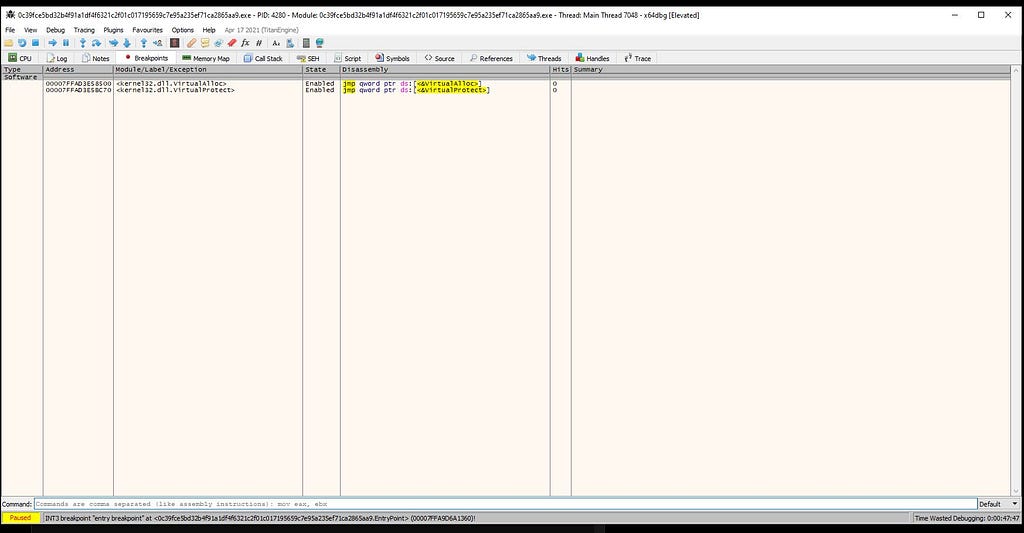 Breakpoints Window in x64-dbg.
Breakpoints Window in x64-dbg.Unpacking
Hit “Run” after setting breakpoints in binary.
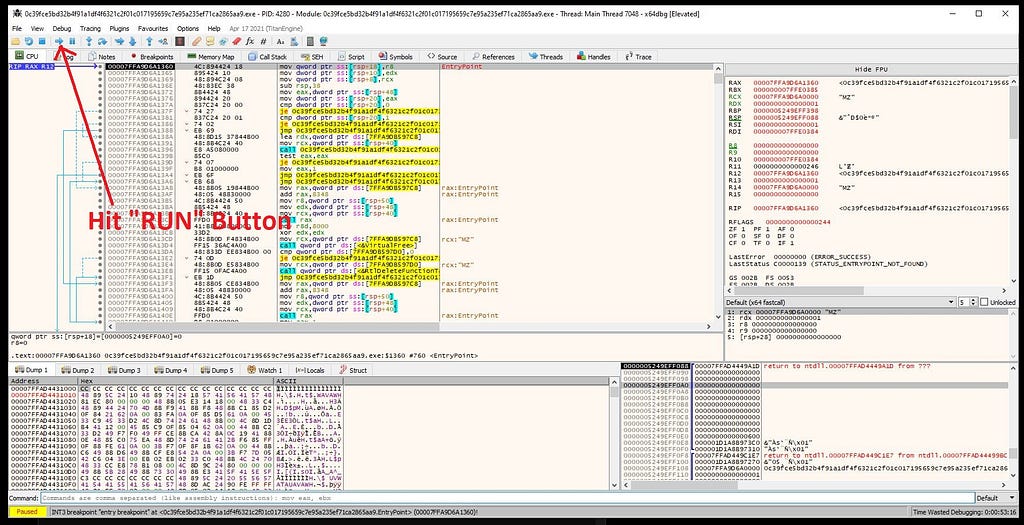 Hitting “Run” Button on x64-dbg.
Hitting “Run” Button on x64-dbg.On running debugger, it hits at the first breakpoint “VirtualAlloc” as there is no presence of “MZ” header so soon after “”VirtualAlloc” is being hit , hit the
 x64-dbg hits at the “VirtualAlloc”.
x64-dbg hits at the “VirtualAlloc”.return button in debugger after following RAX register in hexdump.
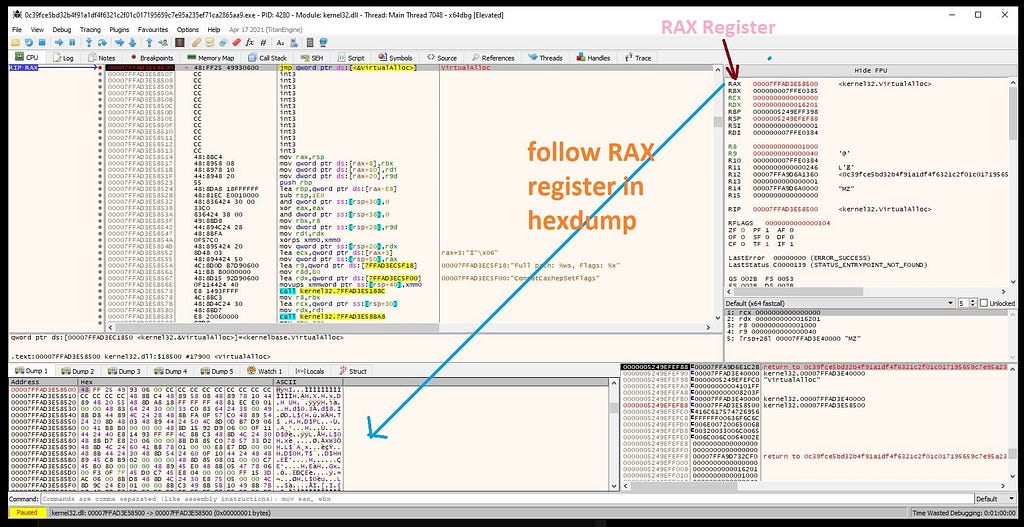 Following RAX register in hexdump.
Following RAX register in hexdump.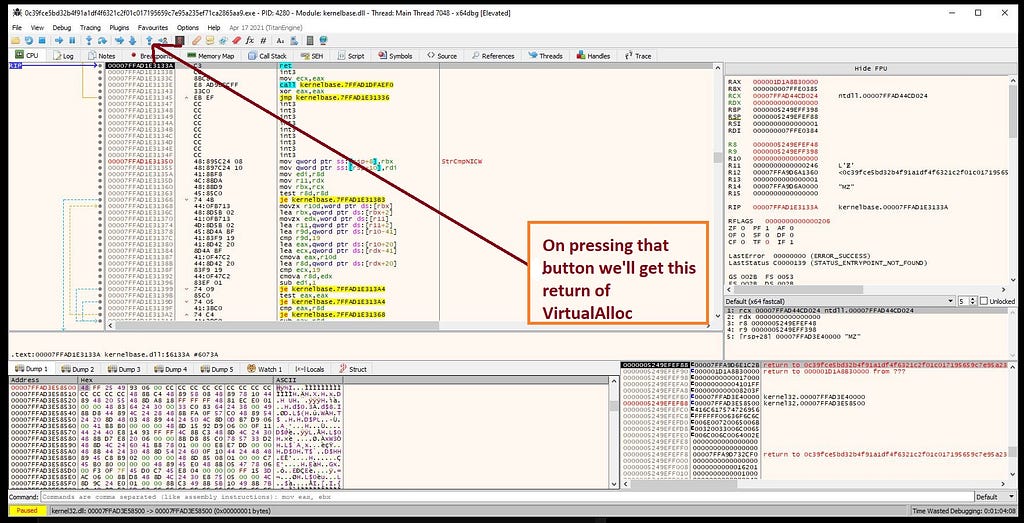 x64-dbg hitting at return of “VirtualAlloc”.
x64-dbg hitting at return of “VirtualAlloc”.And as again when you hit the “Run” in debugger it hits “VirtualAlloc” for two more times & then it hits “VirtualProtect”.
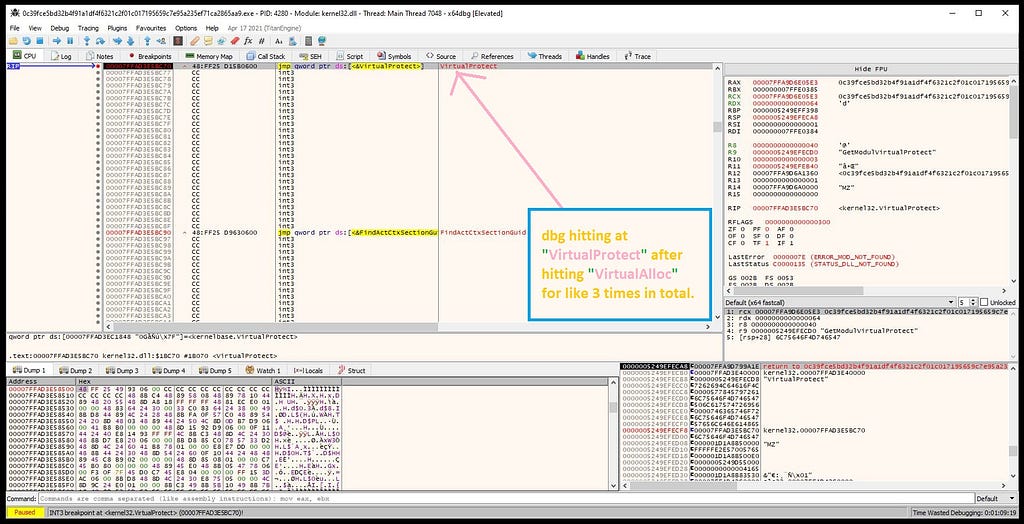 x64-dbg hits at “VirtualProtect”.
x64-dbg hits at “VirtualProtect”.Now, as if see in the bottom right of the debugger , you will see the presence of “MZ” header. Then following it in the hexdump. And as you clearly see the unpacked payload in the hexdump.
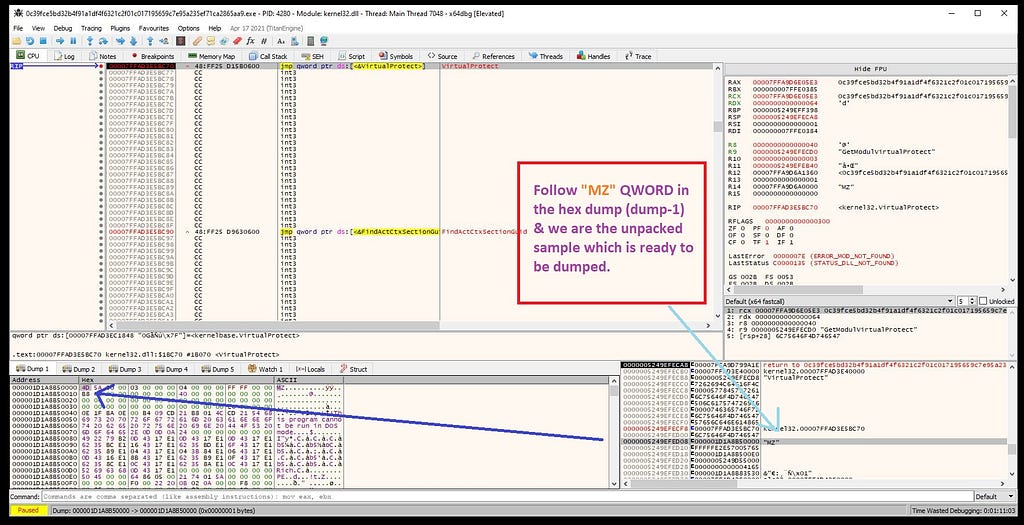 “MZ” header of payload of PolyglotDuke.
“MZ” header of payload of PolyglotDuke.Now follow it in the memory map & dumping unpacked payload from there on disk.
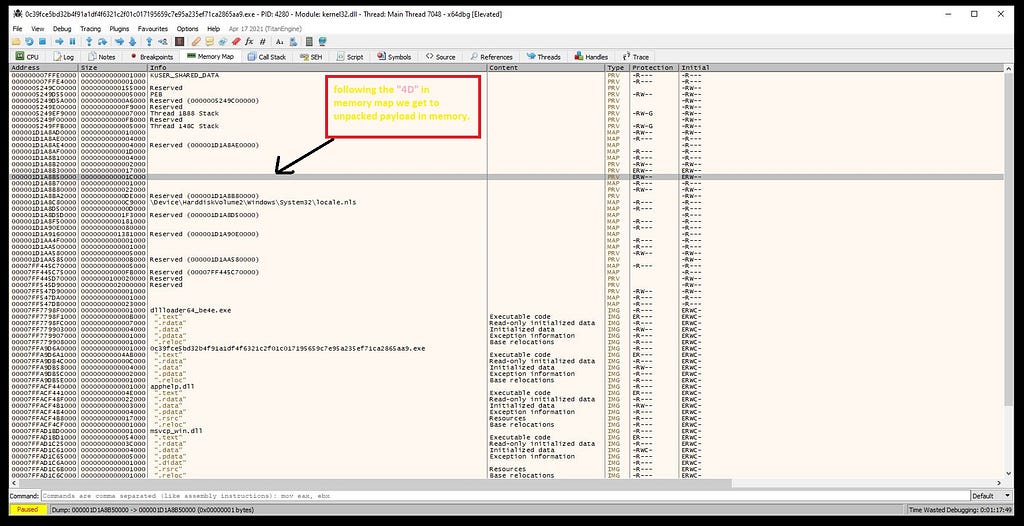 On following “4D 5A” in the memory map.
On following “4D 5A” in the memory map.Loading payload in PE-Bear for fixing PE structure, now by going in the Section Hdrs replace the Raw Addr. of PE with Virtual Addr.
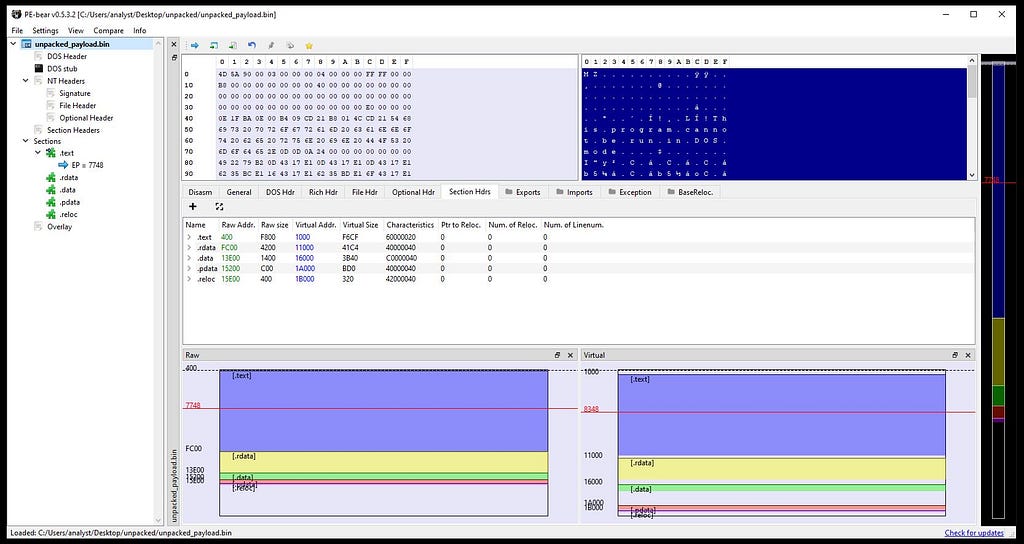
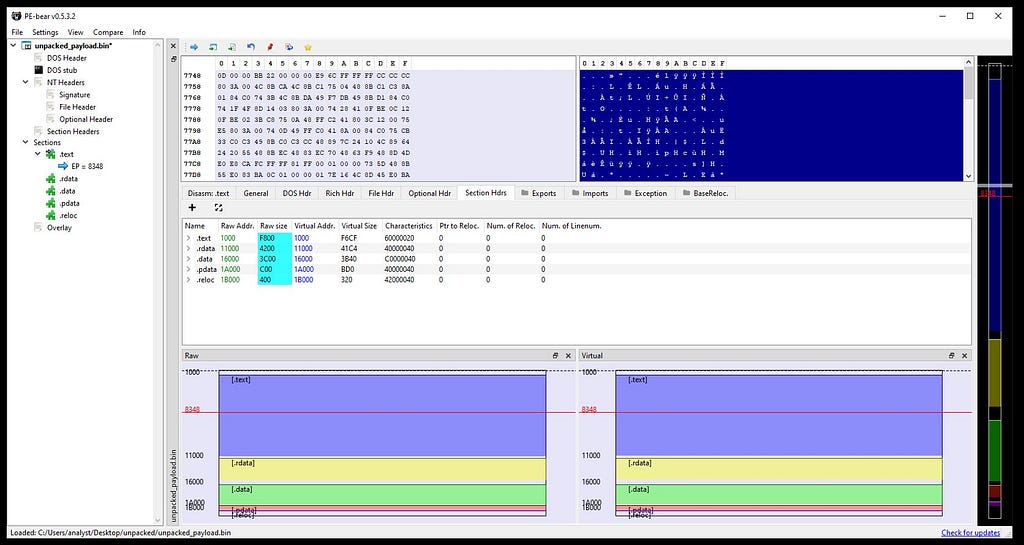 In left: Unfixed Raw addr. In Right: Fixed Raw addr. .
In left: Unfixed Raw addr. In Right: Fixed Raw addr. .Finally replace the dumped address location of payload in x64-dbg to base address in PE-Bear.
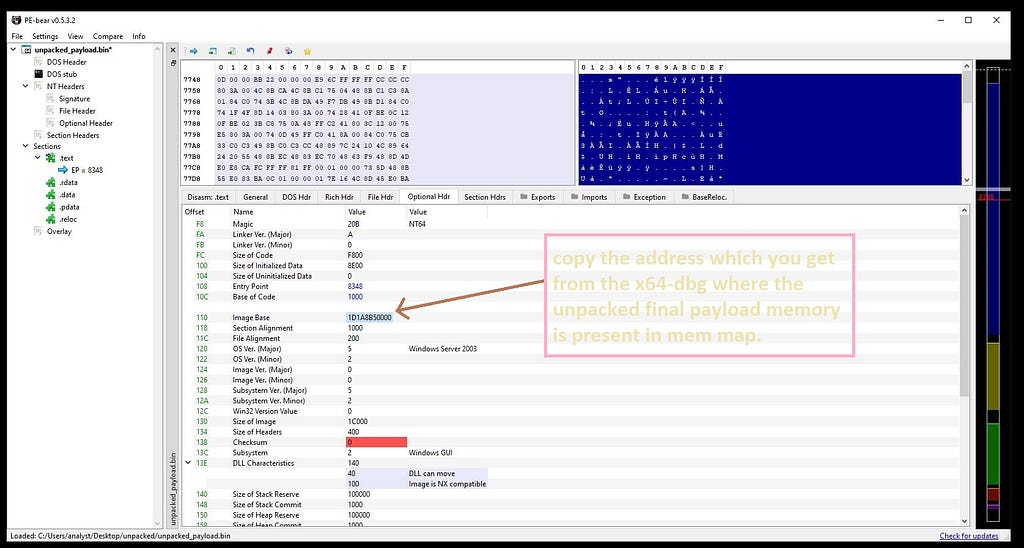 Copy the dumped Addr. location of payload from x64-dbg to base addr. in PE-Bear.
Copy the dumped Addr. location of payload from x64-dbg to base addr. in PE-Bear.Now you can save unpacked payload of PolyglotDuke.
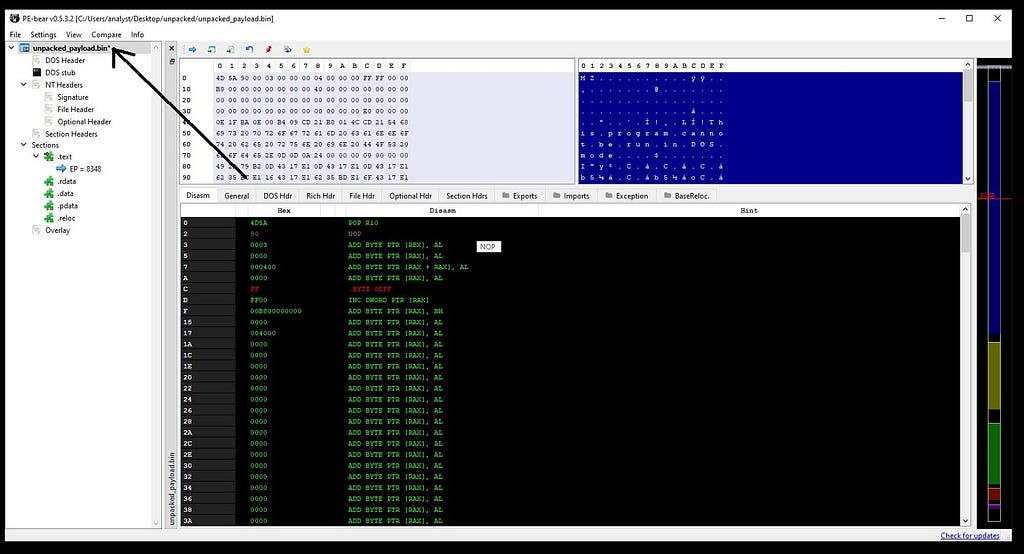 Saving PolyglotDuke payload.
Saving PolyglotDuke payload.Confirming payload.
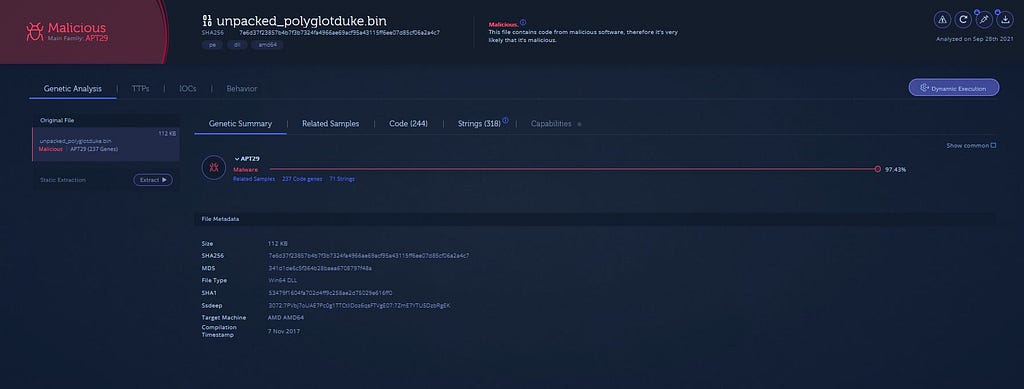 Confirming APT29 Polyglot Duke payload on Analyze.Intezer.
Confirming APT29 Polyglot Duke payload on Analyze.Intezer.IoCs
Loader:-
MD5: 078cfd29c9fa461247c0246f3a8a46af
SHA1: 1b9b2b2fe0594ff75dc808fa39f7a09d4de50746
SHA256: 0c39fce5bd32b4f91a1df4f6321c2f01c017195659c7e95a235ef71ca2865aa9.
Payload:-
MD5: 341d1de6c5f364b28baea6708797f48a
SHA1: 53479f1604fa702d4ff9c258ae2d75029e616ff0
SHA256: 7e6d37f23857b4b7f3b7324fa4966ae69acf95a43115ff6ee07d85cf06a2a4c7
References
https://bazaar.abuse.ch/sample/0c39fce5bd32b4f91a1df4f6321c2f01c017195659c7e95a235ef71ca2865aa9/
Thanks for reading. And your precious time for my research blog.
Article Link: https://0xthreatintel.medium.com/unpacking-of-apt29-polyglotduke-6b3544ccd637?source=rss-4844031faab4------2