Japan faces consistent threat from NK APT Lazarus.
Introduction
In this particular blog , i will walk you through internals of two malware “VSingle” and “ValeforBeta” used by Unit180 in targeted hacking operations against Japan as like the hacking operations was done by Unit180 in “Operations Dream Job” against Japan where they had used “Torisma” and “LCPDot”. In this campaign also malware were build following similar tactics and techniques.
Analysis
Static Analysis (Basic)
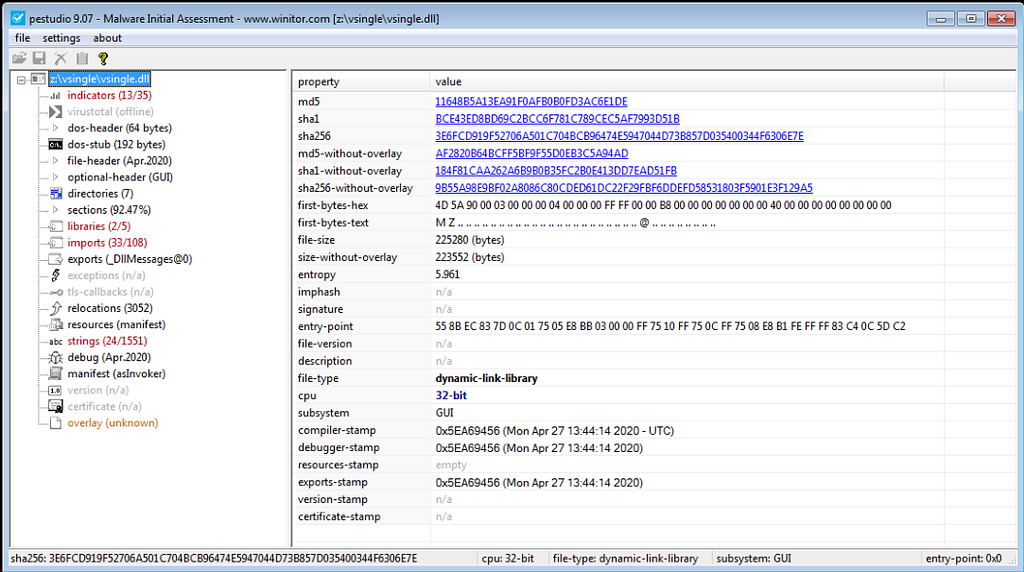 File Information of VSingle Malware.
File Information of VSingle Malware.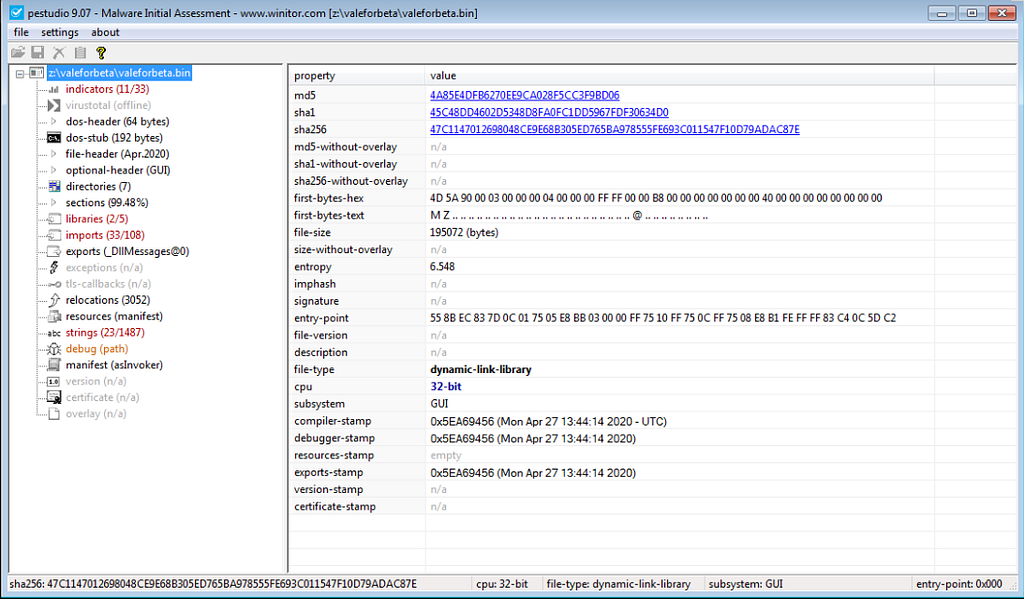 File Information of ValeForBeta Malware.
File Information of ValeForBeta Malware.Static Analysis (Advanced)
Since both of the malware have been almost similar code as what we have been encountered with during our research. In there previous campaign targeting Japan where they had used ‘Torisma” and “LCPDot” for the hacking operations they had been using similar techniques.
Exports in both malware is same.
 Exports of VSingle and ValeforBeta malware.
Exports of VSingle and ValeforBeta malware.DllEntryPoint function
This function present in “ValeforBeta” and “VSingle” malware shares similar code to “Torisma” and “LCPDot” in “Operation Dream Job”. As in this function buffer overflow , anti VM and anti analysis checks is being performed using “Bof_with_anti_VM_check” and “buffer_overflow_and_anti_analysis” function. Whereas there is the another function in the “DllEntryPoint” which is “dllmain_dispatch” which is mainly does the anti analysis and anti VM checks for malware.
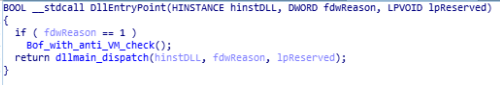
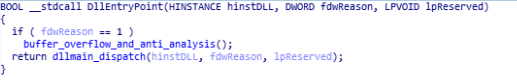 reversed code of DllEntryPoint function of ValeforBeta and VSingle malware.
reversed code of DllEntryPoint function of ValeforBeta and VSingle malware.
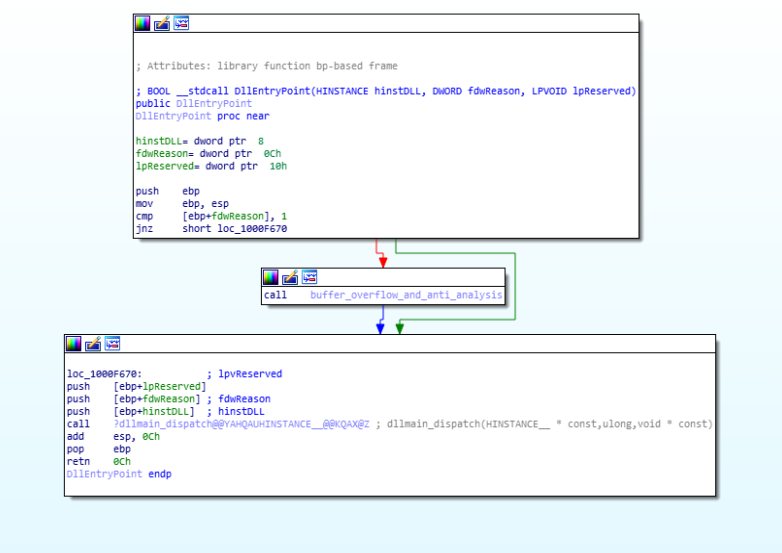 Disassembly call graph of ValeforBeta and VSingle malware.
Disassembly call graph of ValeforBeta and VSingle malware.bof_with_anti_VM_check function
This function is being used by Unit180 for setting up Buffer Overflow in the victim system and also checking for VM and runs all anti analysis against infected victim system.
 code of bof_with_anti_VM_check function.
code of bof_with_anti_VM_check function.dllmain_dispatch function
This function is also similar to the previous function as it also does the anti VM and anti analysis checks.
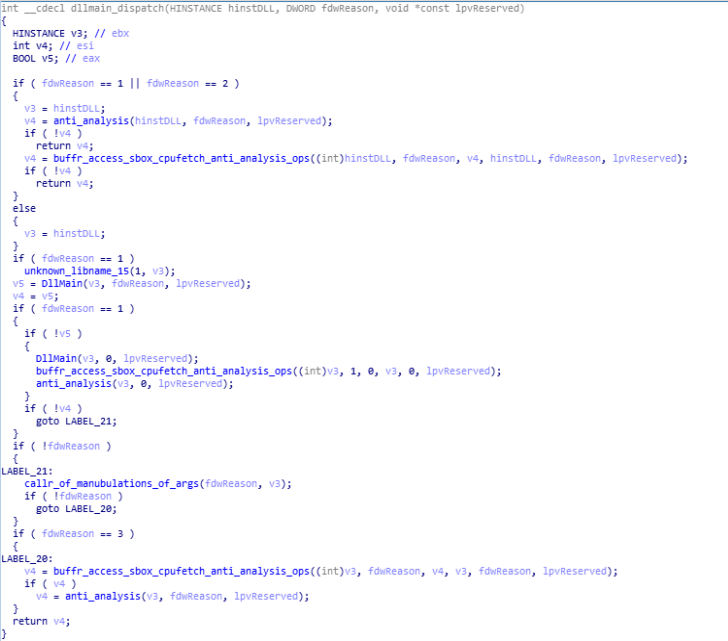 code of dllmain_dispatch function.
code of dllmain_dispatch function.Now moving on to function used for setting up server for communication with command and control server (C2) and function for carrying out operations for command and control server.
StartAddress function
In this function mainly what happen is that Unit180 developers had used similar technique as we have seen in “Torisma” and “LCPDot”. As they are creating same pipe server for setting up communication with the command and control server (C2). Also in this function some shell command is also being executed using “execute_shell_command” function. After the file operations are being carried out in this function.
 code of StartAddress function.
code of StartAddress function.command_and_control_ops function
for carrying out the operations of command and control server this function is being developed by Unit180 developers.
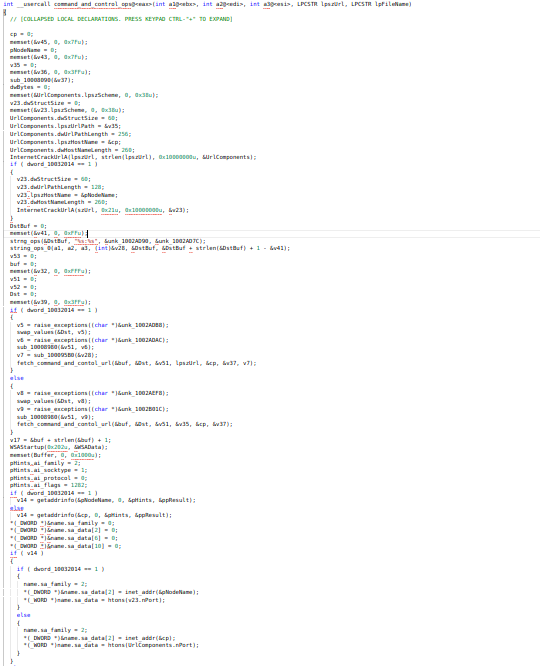
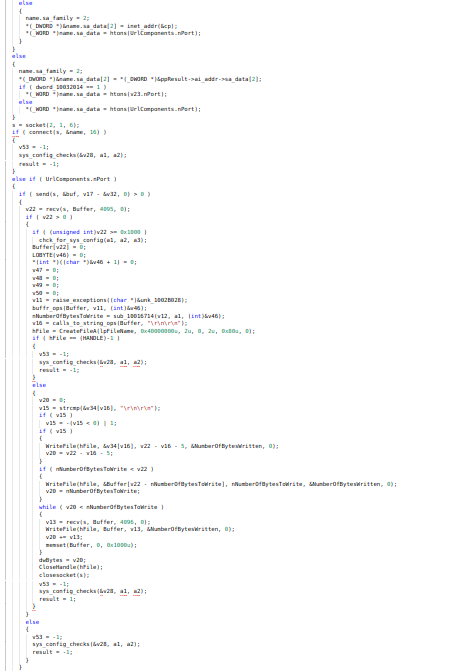
 code of command_and_control_ops function.
code of command_and_control_ops function.References:
- Lazarus Attack Activities Targeting Japan (VSingle/ValeforBeta) - JPCERT/CC Eyes
- Internals of Lazarus Operation Dream Job
Thanks for reading.
Article Link: https://0xthreatintel.medium.com/unit180-lazarus-targets-japan-ea2478f9399?source=rss-a15183055fd6------2