Uncovering APT29 tool: Trojan PolyGlot Duke — (unpacking)
Unpacking, Static and Dynamic Analysis of PolyGlot Duke.

In this blog, i will be unpacking , static and dynamic analysis of trojan “PolyGlot Duke” from APT29. For this blog we only focus on Unpacking.
Unpacking
File Information
It’s a 64-bit malware. Which is basically a packed.
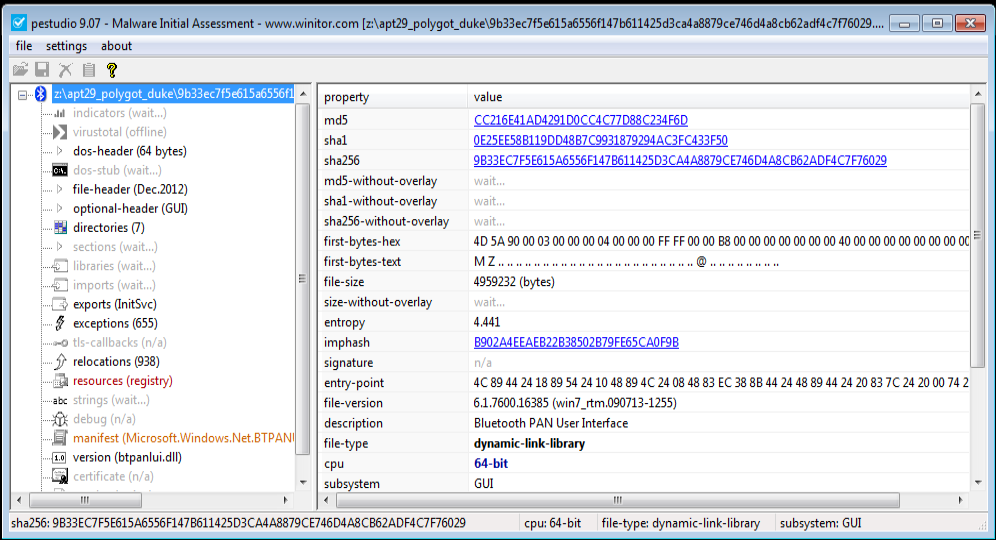 PE Studio View of packed APT29 Malware.
PE Studio View of packed APT29 Malware.Unpacking using x64dbg:
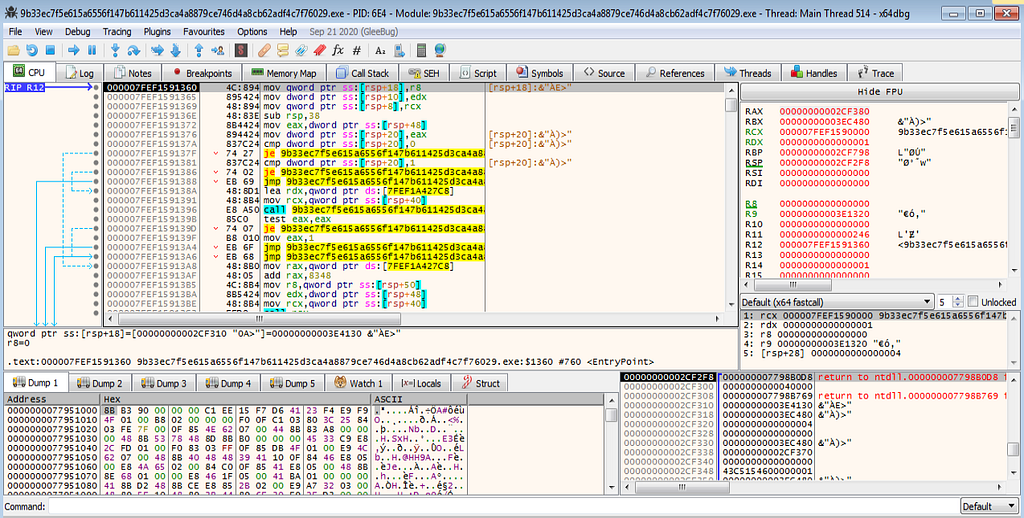 Loading packed malware in x64dbg.
Loading packed malware in x64dbg.Setting Up Breakpoints for unpacking while debugging:
Some for the process injection and some for the self injection.
….:- VirtualAlloc
…..:- VirtualProtect
…..:- ResumeThread
…..:- CreateProcessInternalW
…..:- WriteProcessMemory
Hitting Breakpoints
Firstly the breakpoint hits at the EntryPoint.
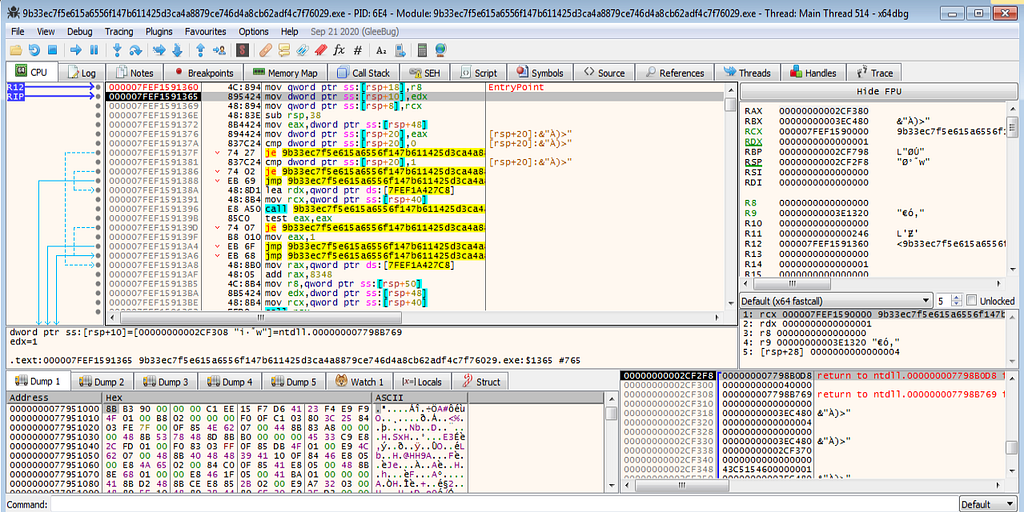 x64dbg view hitting at the entrypoint.
x64dbg view hitting at the entrypoint.Running the debugger again , hits at the VirtualAlloc.
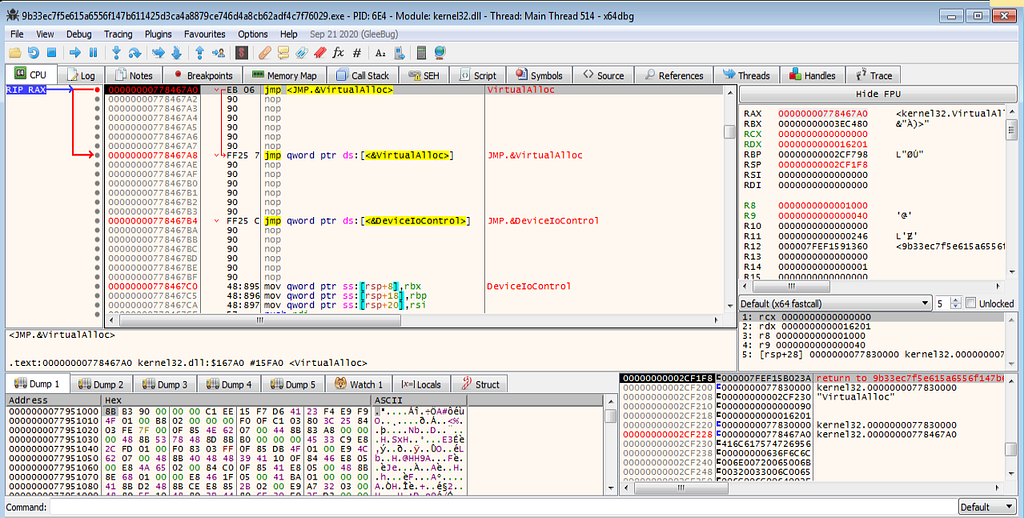 x64dbg view hitting at the VirtualAlloc.
x64dbg view hitting at the VirtualAlloc.Following several hits at VirtualAlloc and returns hits , debugger hits at the VirtualProtect and it’s return hits.
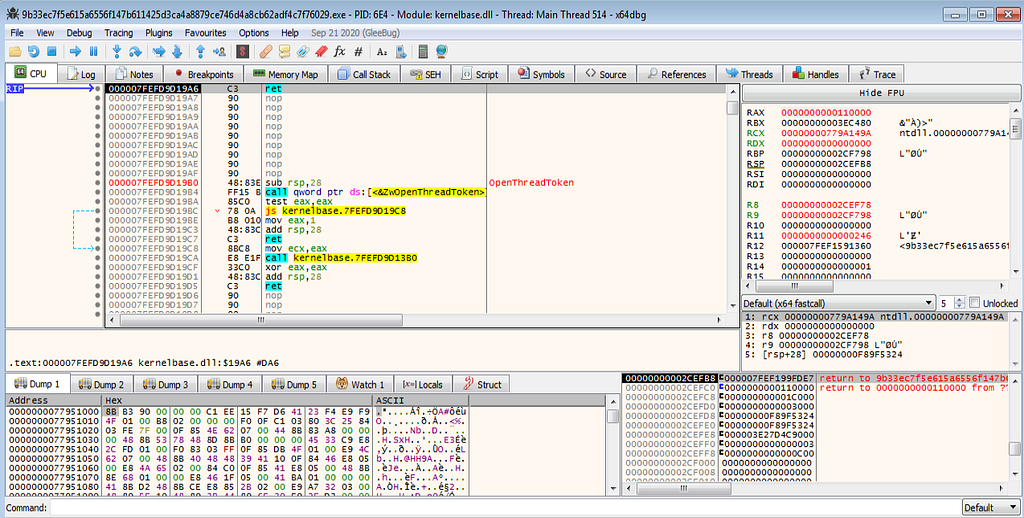
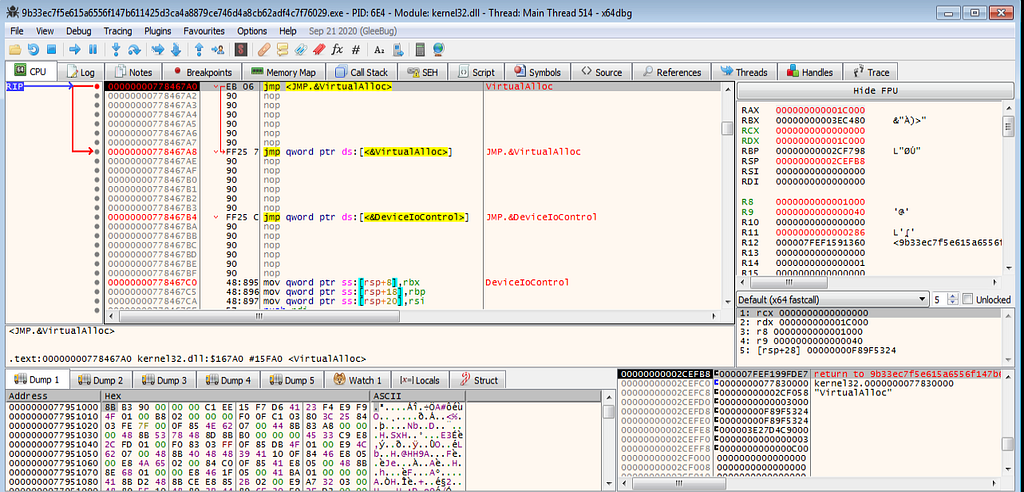
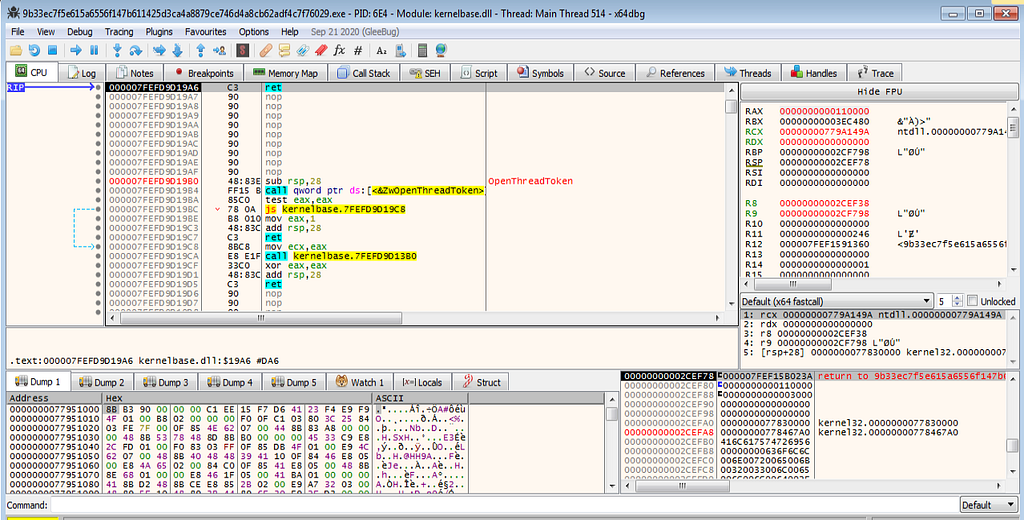
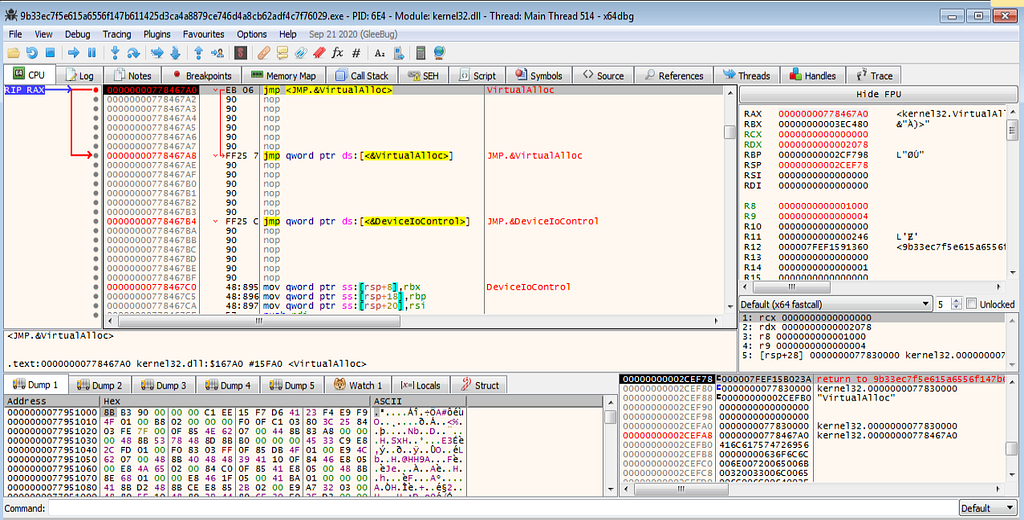
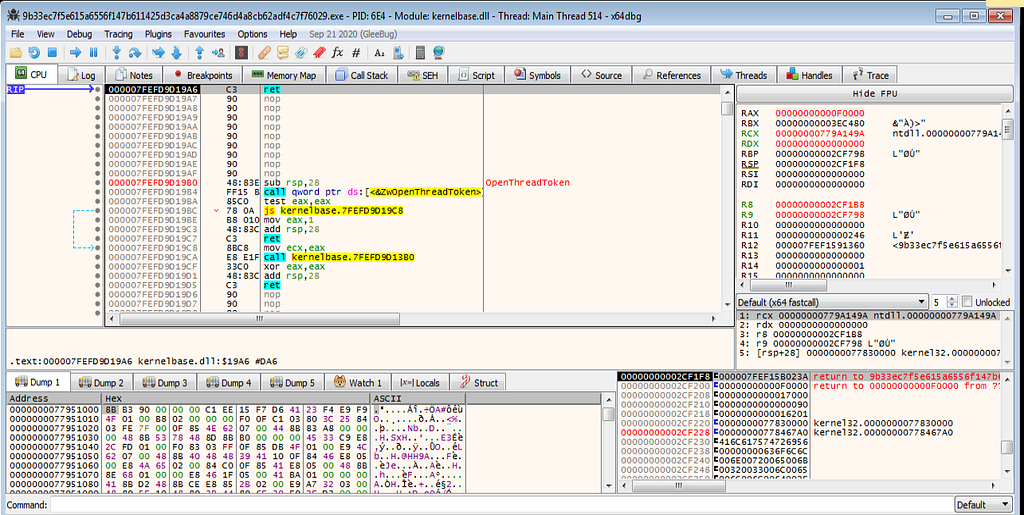 x64dbg view hitting at the VirtualAlloc and its returns.
x64dbg view hitting at the VirtualAlloc and its returns.Now something hits differ in debugger VirtualProtect.
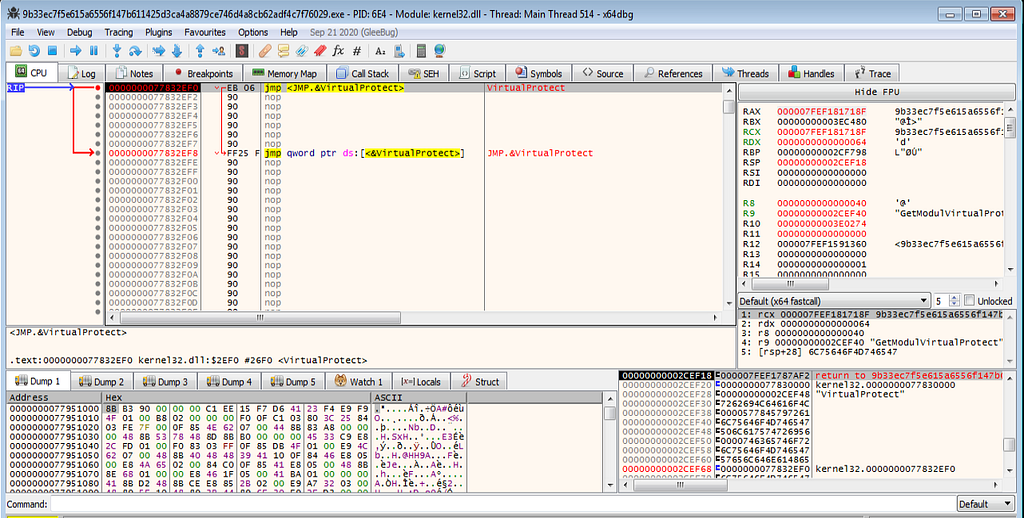 x64dbg view hitting at the VirtualProtect.
x64dbg view hitting at the VirtualProtect.Hitting the run , x64dbg hits at the return.
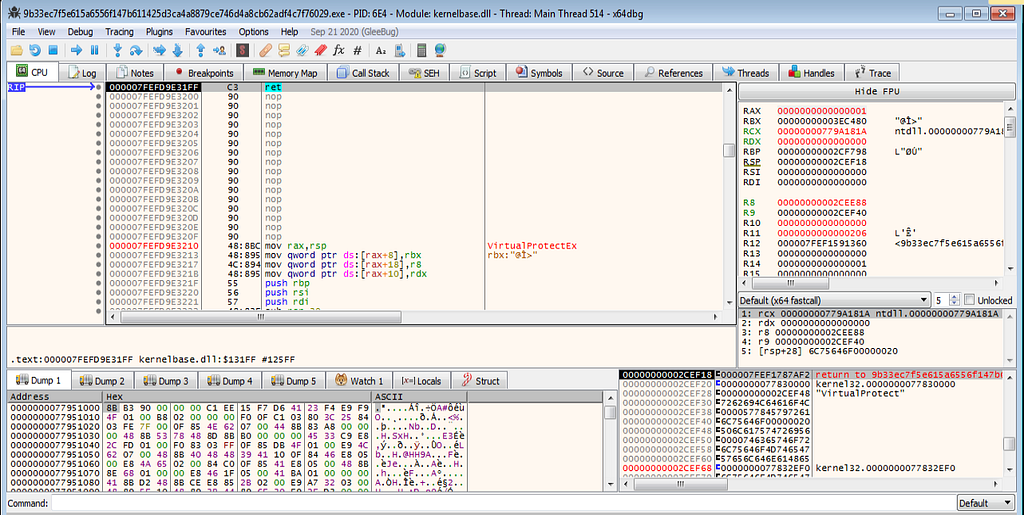 x64dbg view hitting at the return of VirtualProtect.
x64dbg view hitting at the return of VirtualProtect.Again x64dbg hitting at the VirtualProtect at next run and it’s return.
 x64dbg view hitting at the VirtualProtect.
x64dbg view hitting at the VirtualProtect.Now scrolling a bit in window right to hexdump window you will found “PE” string mentioned
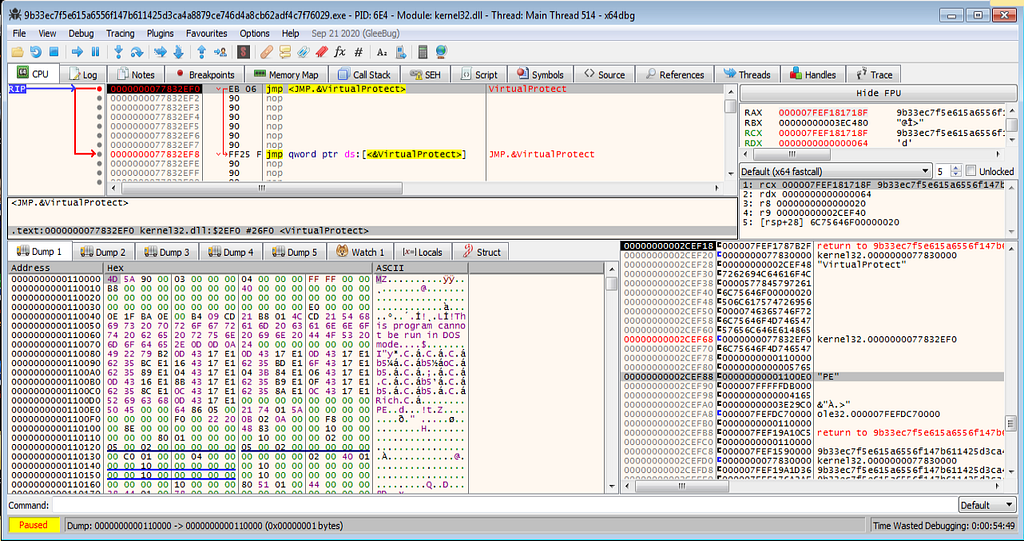 “PE” string we can found in window right to hexdump.
“PE” string we can found in window right to hexdump.Now following it in the hexdump and scrolling of bit up we will get MZ (magic header) header. As we get the MZ header we will follow it in the Memory Map.
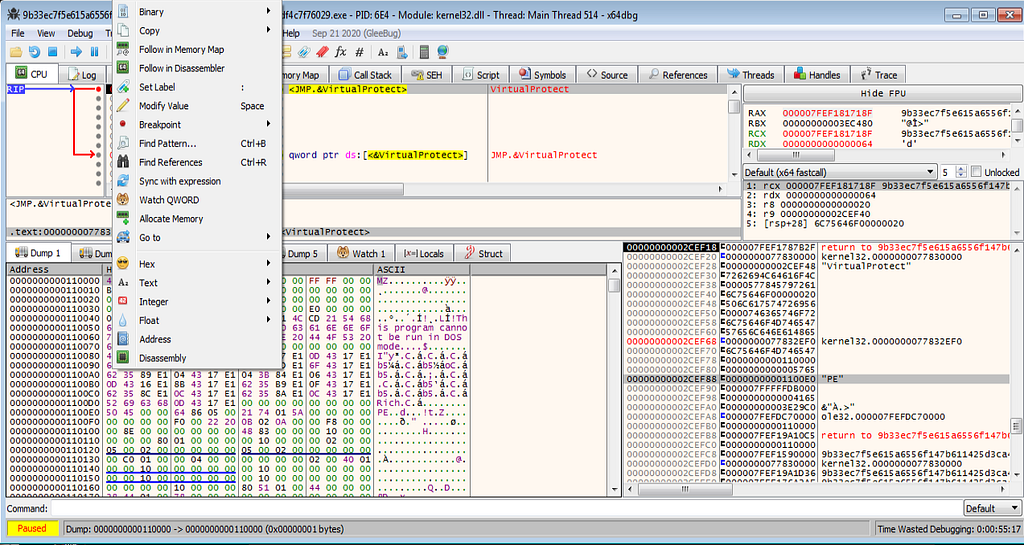 Following the MZ header in the Memory Map.
Following the MZ header in the Memory Map.Highlighted line in the memory map is the executable for us to analyse. Right click ,dump and save it.
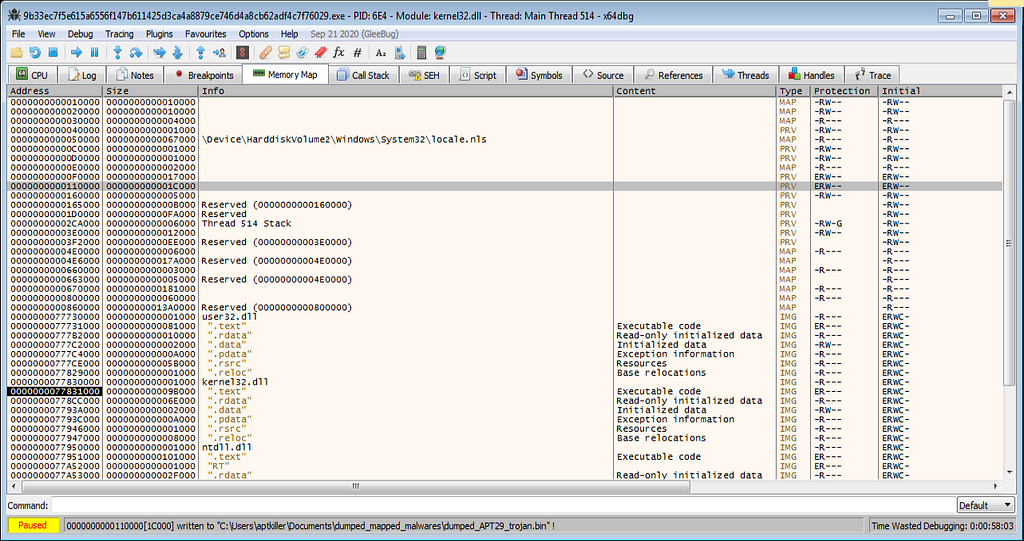 Following View of Memory Map from HexDump we get to the executable.
Following View of Memory Map from HexDump we get to the executable.Checking up for proper executable
Opening up the dumped file in the PE Studio.
 PE Studio View of mapped file.
PE Studio View of mapped file.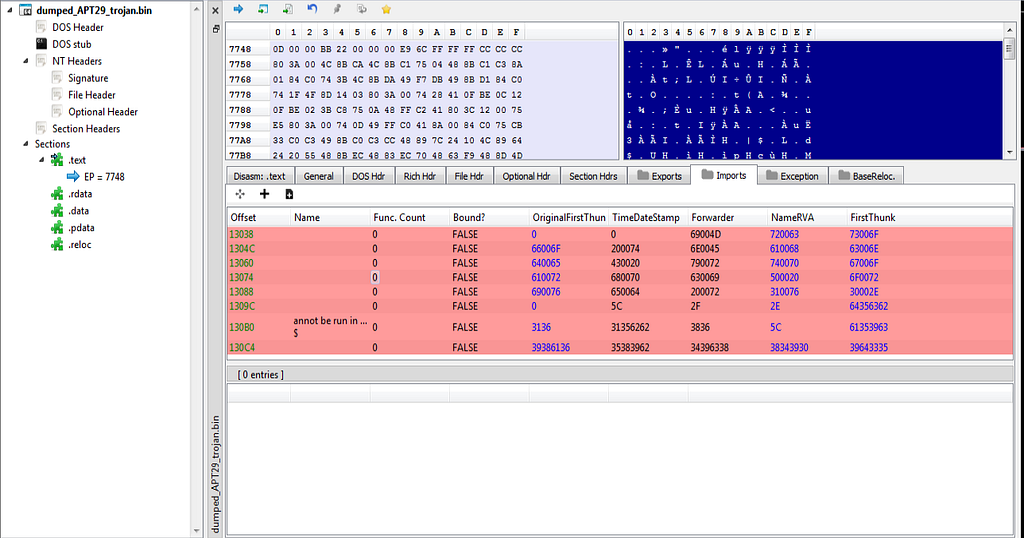
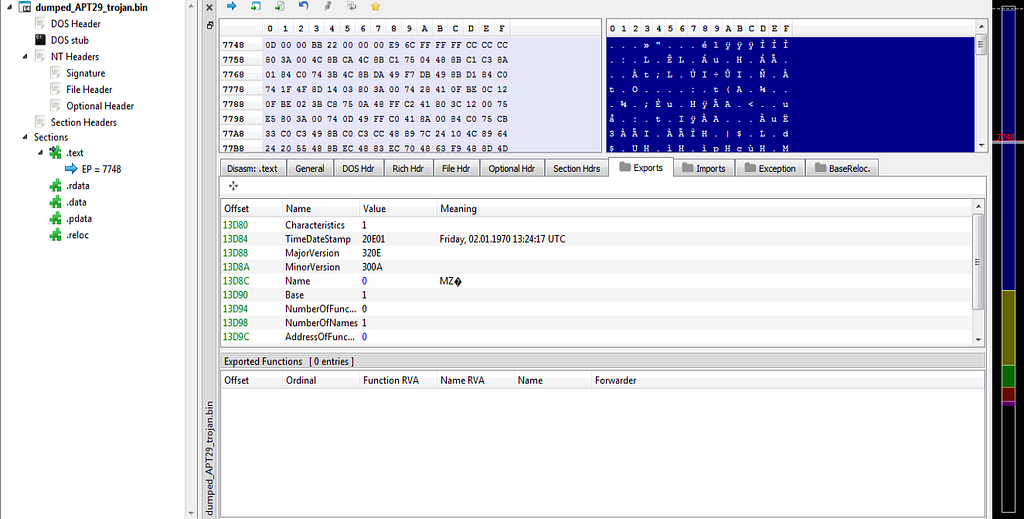
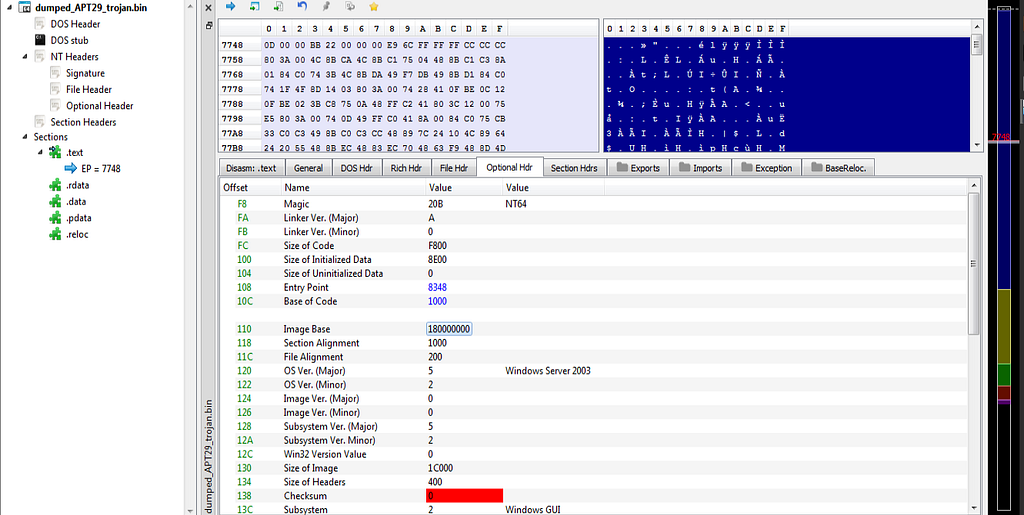 PE Bear view of mapped file.
PE Bear view of mapped file.Fixing Raw and Base Address in PE Bear
Replace all the raw and base addresses with the Virtual Address and Virtual Size respectively.
 PE Bear mapped file.
PE Bear mapped file.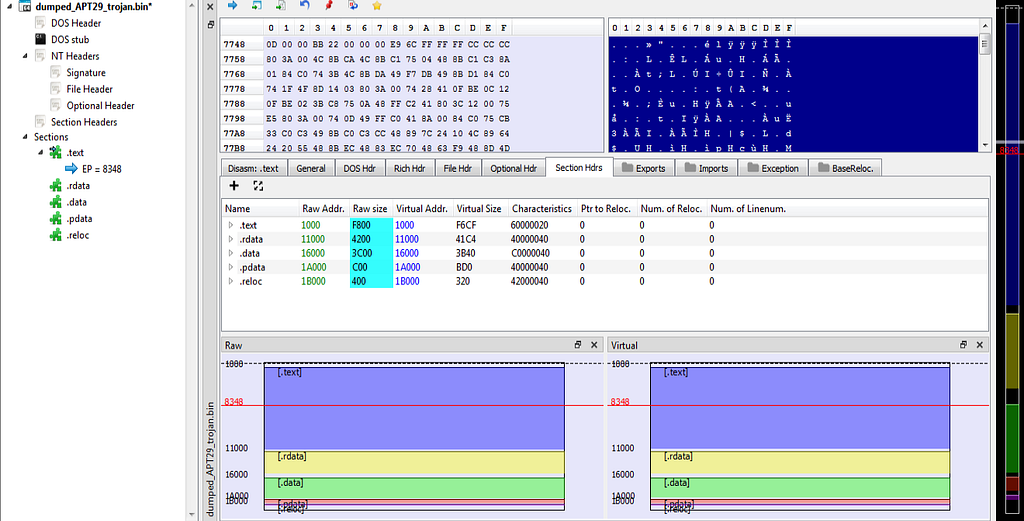 PE Bear unmapped and fixed file.
PE Bear unmapped and fixed file.Now fixed file information.
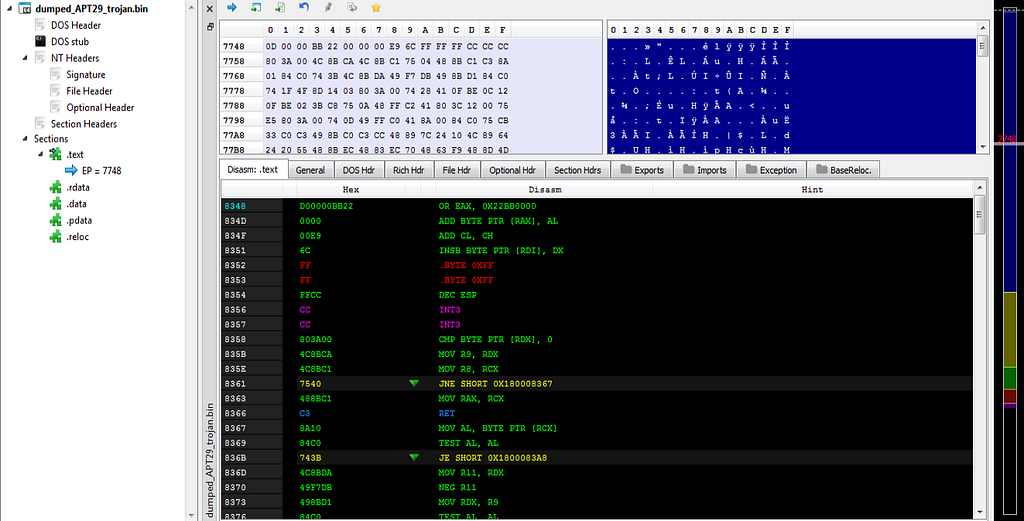
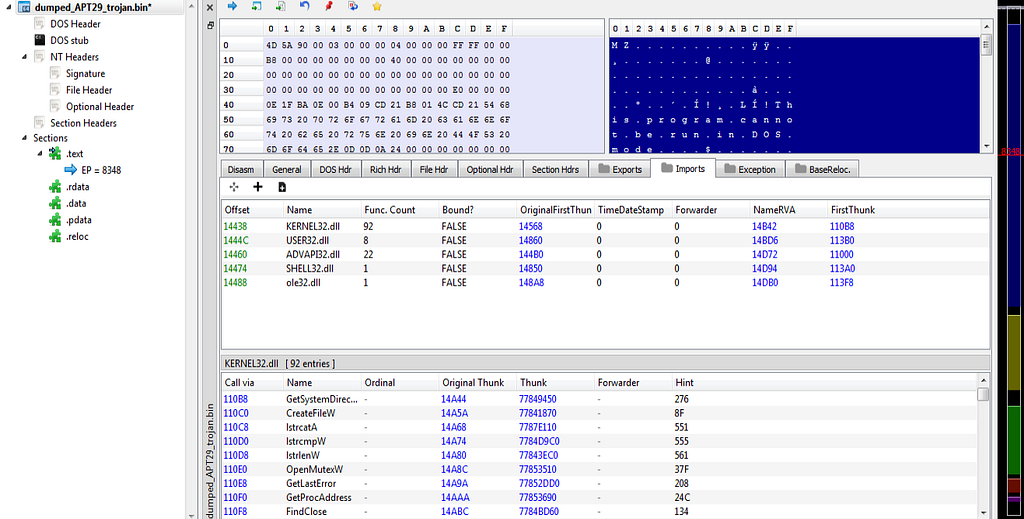
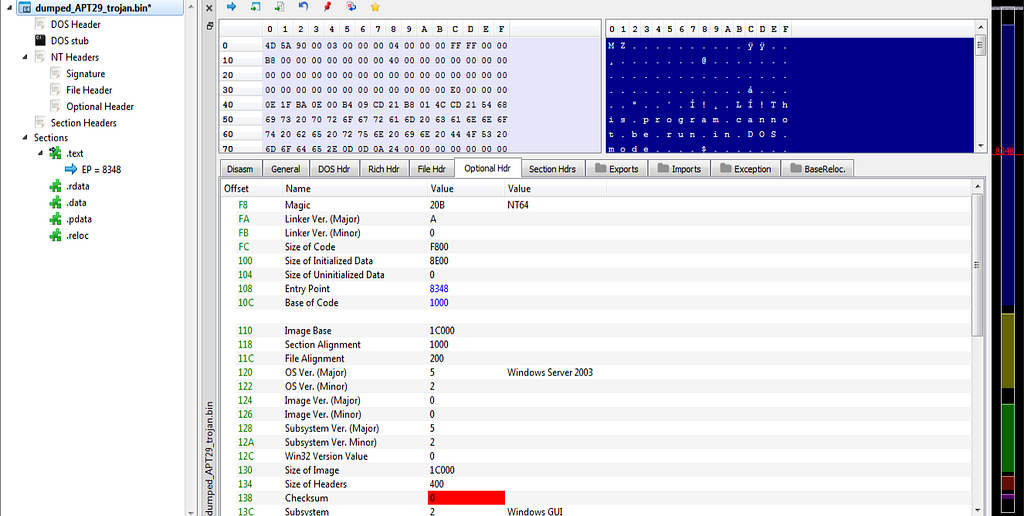
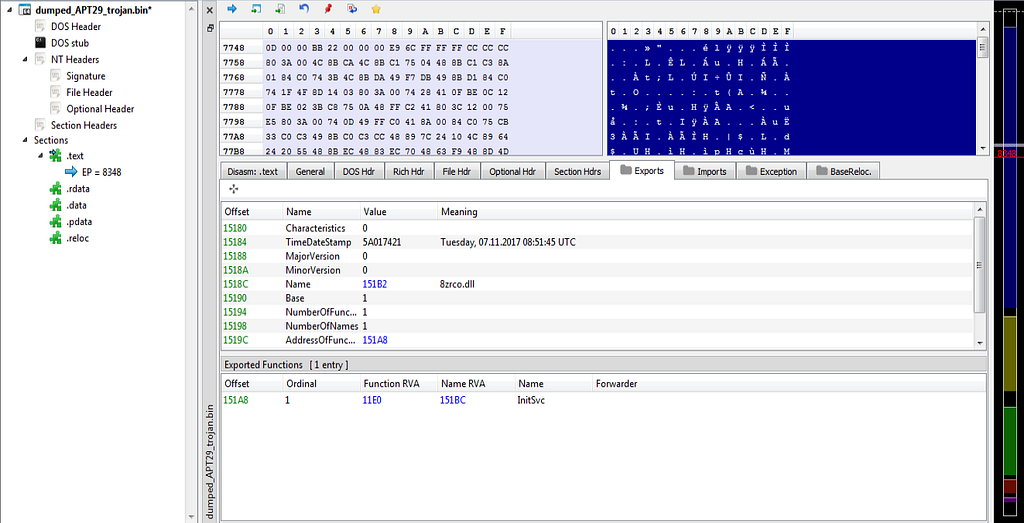 PE Bear with fixed file information.
PE Bear with fixed file information.Sample from Report:
From Abuse[.]ch:
Packed Sample:
MalwareBazaar | Browse malware samples
Unpacked Sample:
MalwareBazaar | Browse malware samples