Tool of Chinese Espionage and Cyber Crime Group.

In this blog, i will be uncovering backdoor deployed by Chinese APT group APT-C-41(aka StrongPity) backdoor recently targeting Europe countries. APT-C-41 is known for conducting cyber crime and espionage operations against financial, industrial and educational sectors. Recent activities of APT-C-41 are caught since Nov of last year.
Static and Dynamic Analysis
Static Analysis(Basic)
File Information
Its 32bit malware.
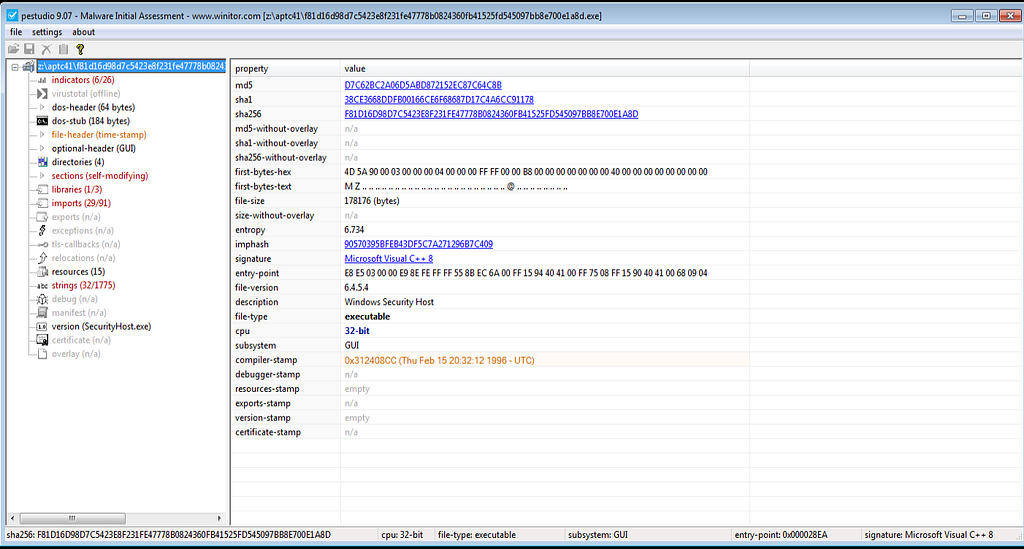
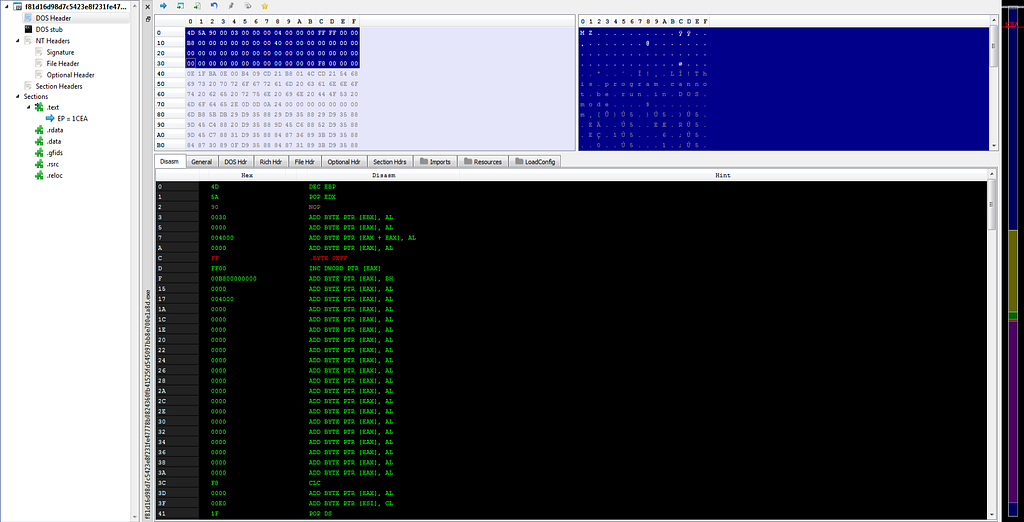 It’s the unpacked sample.
It’s the unpacked sample. Here’s the view of unpacked backdoor.
Here’s the view of unpacked backdoor.Static Analysis (Advanced)
For starting with the advanced static analysis lets see the exports. In exports there is only one function , which is start function.
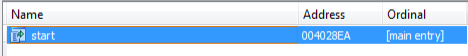 exports of APTC41 backdoor.
exports of APTC41 backdoor.start function:
Mainly in this function there are two functions, system_info_fetcher() and sort_of_main_function_for_access_scrambling_dll_loading(). Where the system_info_fetcher function is to fetch the system information for triage, whereas the sort_of_main_function_for_access_scrambling_dll_loading function is being deployed for the controlling access controls on systems, scramble up data and loading the dlls.
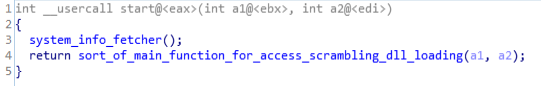
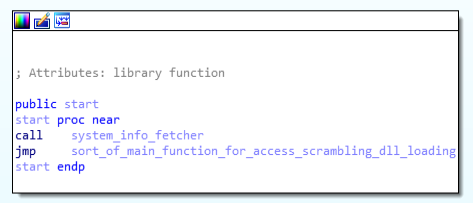 Code & Call Graph of start(entry) function.
Code & Call Graph of start(entry) function.system_info_fetcher function
This function is basically made for getting all information of information of system using GetSystemTimeAsFileTime, GetCurrentThreadId, GetCurrentProcessId, QueryPerformanceCounter function.
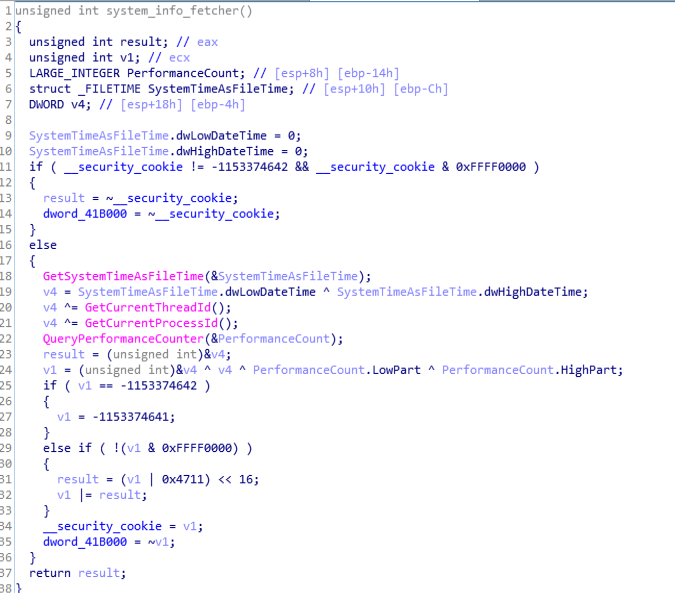
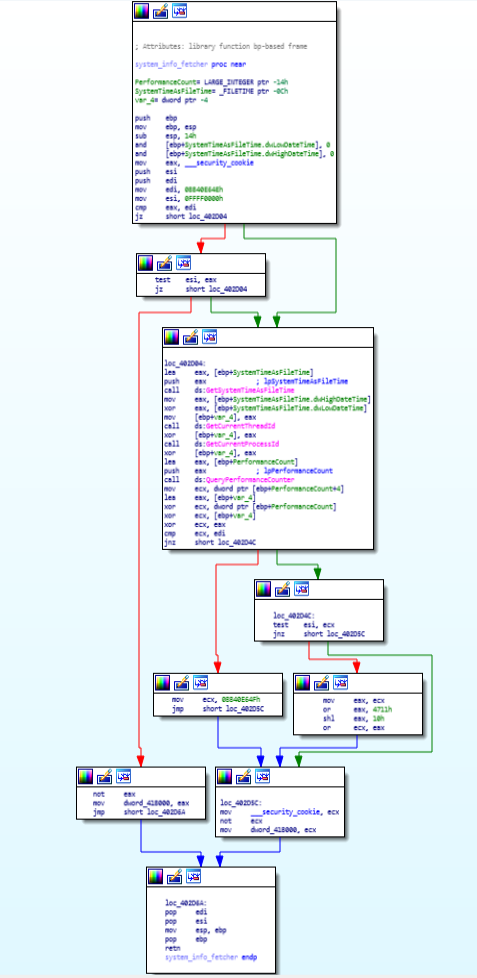 Code & Call Graph of system_info_fetcher function.
Code & Call Graph of system_info_fetcher function.sort_of_main_function_for_access_scrambling_dll_loading function:
This function is responsible for the controlling access controls , setting up exceptions , applying anti analysis techniques and calling WinMain function.
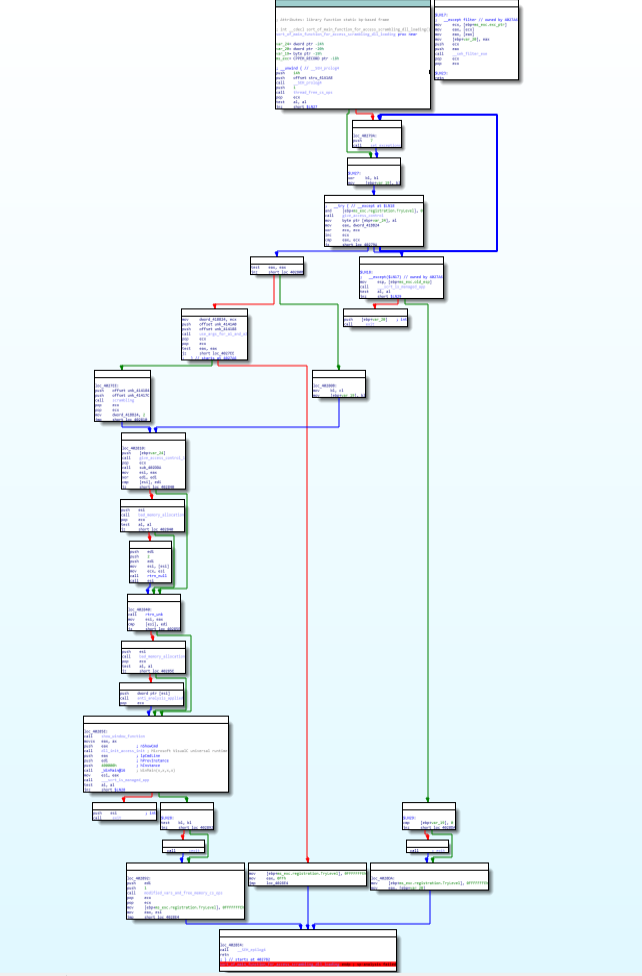
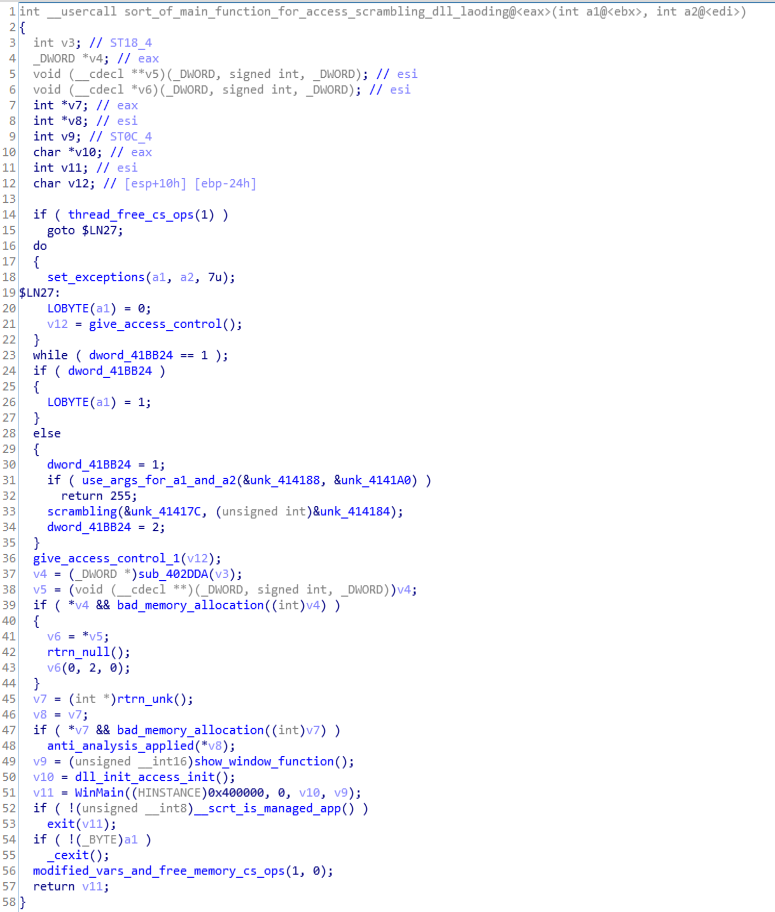 Call graph & Code of sort_of_main_function_for_access_scrambling_dll_loading function.
Call graph & Code of sort_of_main_function_for_access_scrambling_dll_loading function.WinMain function
Moving on to backdoor WinMain function, which is used to have calling seven functions.
GetModuleHandleA, GetProcAddress, GetLastError, callr_of_system_info_fetcher_for_win_main, Sleep, downld_plugin_from_C2.
firstly using the module of kernel32 is being loaded then after that the go_for_callr_of_dll_main() function is being executed which is main function for loading dlls for exploitation.
Then after that, callr_of_system_info_fetcher_for_win_main function is called which is used for fetching system information for the WinMain function. Then for sometime Sleep function is called for hiding the activities from user. Then for downloading plugin from C&C (command and control server) it uses downld_plugin_from_C2 function.
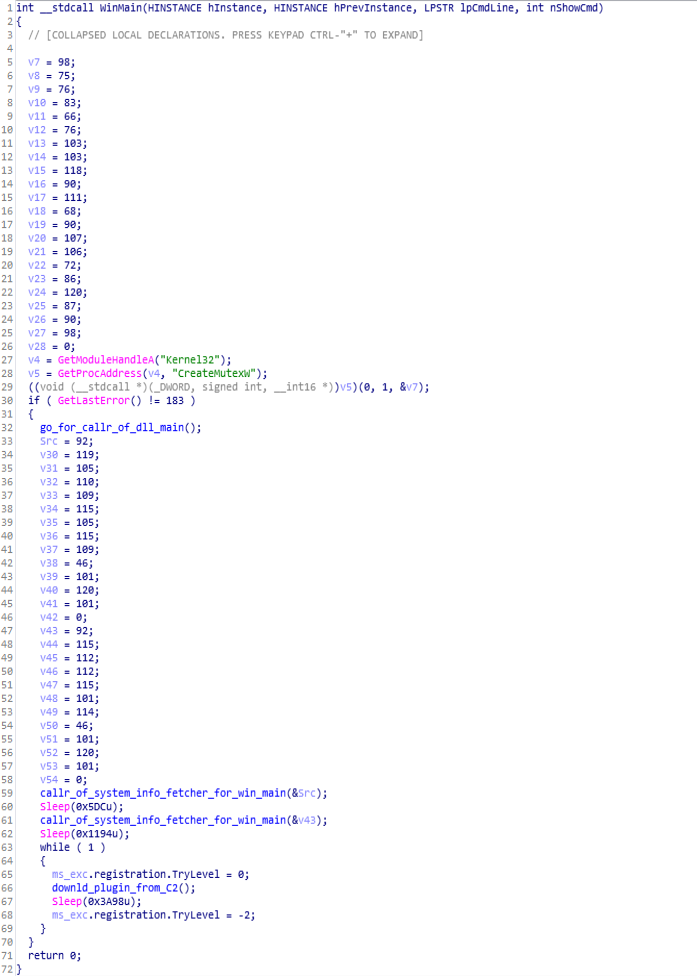
 Code & Call Graph of WinMain function.
Code & Call Graph of WinMain function.make_requests_to_C2 function:
This module of APT-C-41 backdoor is responsible for making requests to the Command and Control Server (aka C&C/C2) using functions like WinHttpOpenRequest, WinHttpAddRequestHeaders, WinHttpSendRequest, WinHttpReceiveResponse.
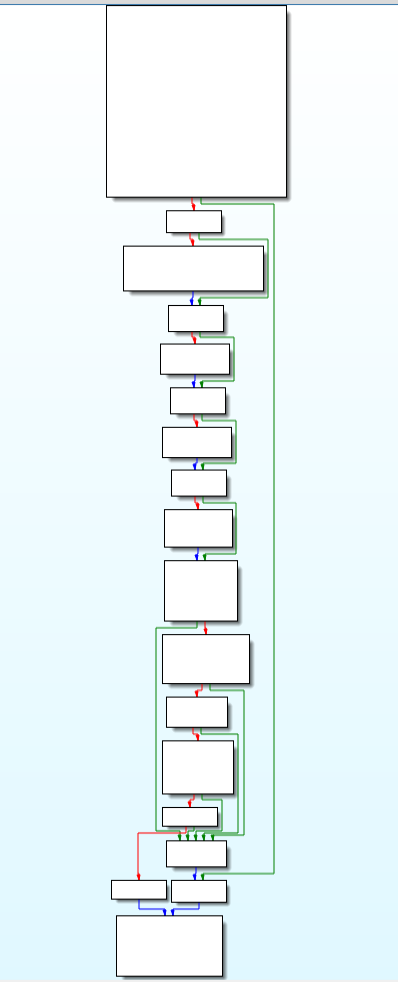
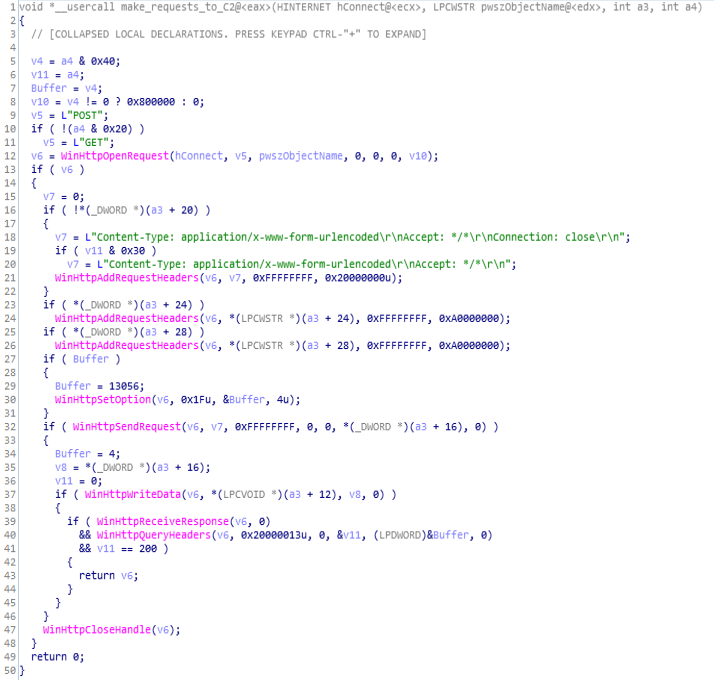 Call Graph & Code of make_requests_to_C2 function.
Call Graph & Code of make_requests_to_C2 function.downld_plugin_from_C2 function:
This function is deployed for downloading plugins from C2 using the functions like get_files_loaded_from_C2.
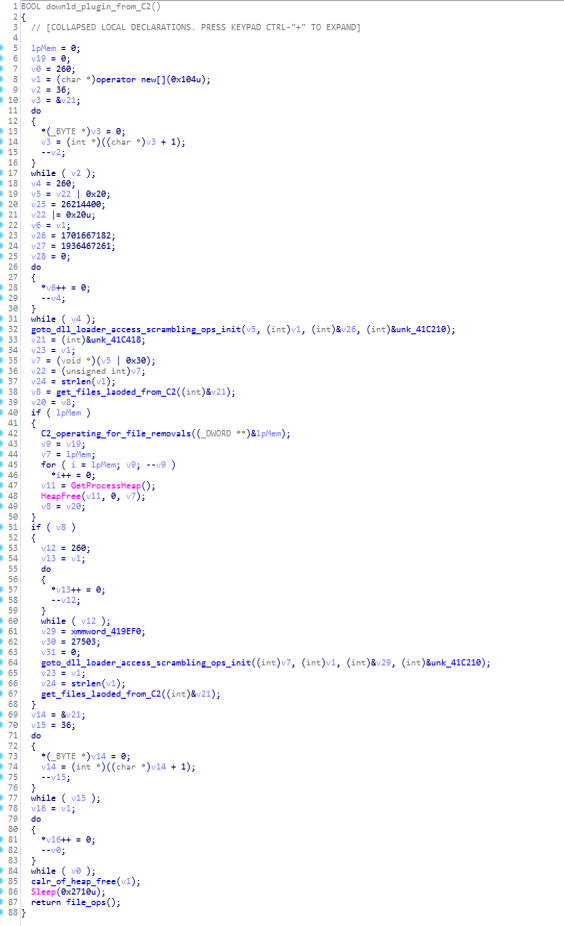
 Code & Call Graph of downld_plugin_from_C2 function.
Code & Call Graph of downld_plugin_from_C2 function.get_files_loaded_from_C2 function:
This function is mainly used for loading the files from command and control server.
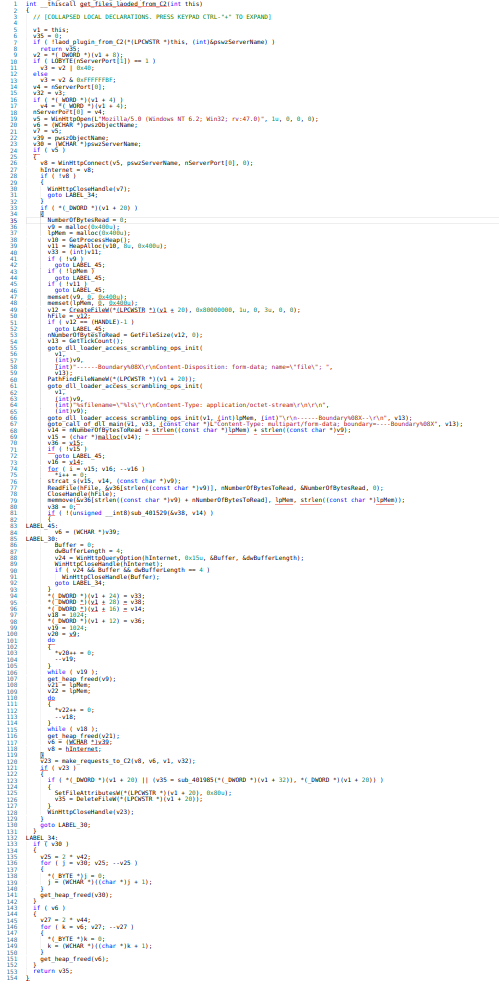 Call Graph & code of get_files_loaded_from_C2 function.
Call Graph & code of get_files_loaded_from_C2 function.load_plugin_from_C2 function:
This function is available for loading the plugins from the C2.
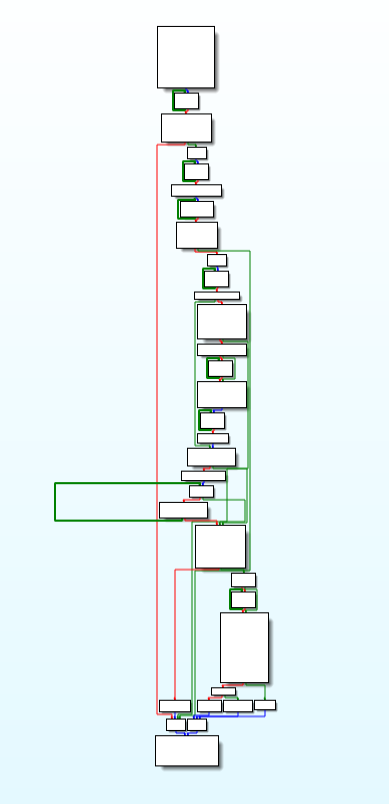
 Call Graph & code of load_plugin_from_C2 function.
Call Graph & code of load_plugin_from_C2 function.C2_operating_for_file_removals function:
In this function, the C2 operations are being crafted for file removals.
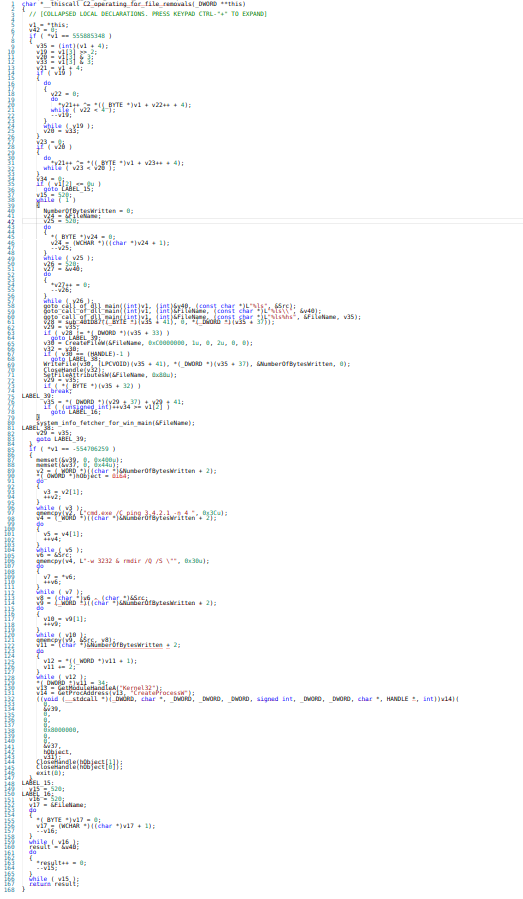 Call graph & code of C2_operating_for_file_removals function.
Call graph & code of C2_operating_for_file_removals function.Dynamic Analysis:(Advanced)
For dynamic analysis , i had set the few breakpoints in the start function:
..:- system_info_fetcher
..:- sort_of_main_function_for_access_scrambling_dll_loading
Luckily the breakpoints gets hits for this sample.
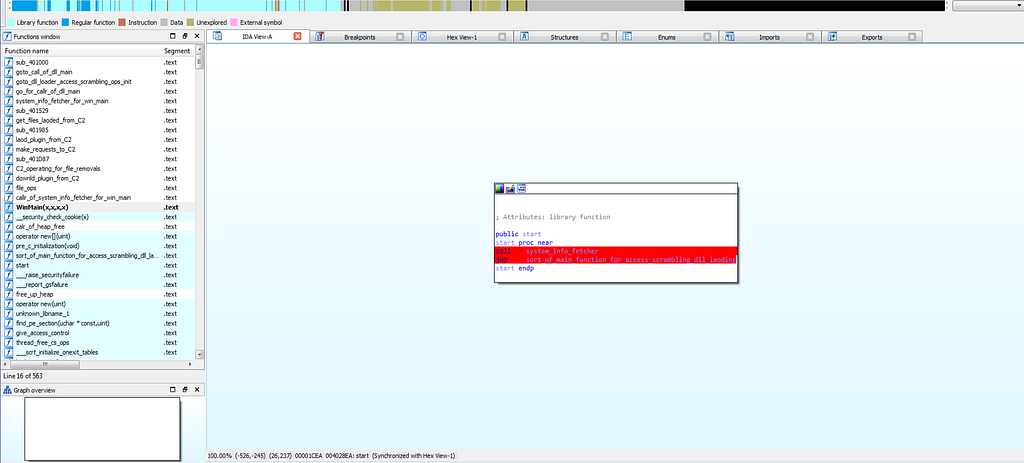 In IDA Setting up breakpoints in start function.
In IDA Setting up breakpoints in start function.As the debugger hits at first breakpoint in start function following dlls are being loaded .
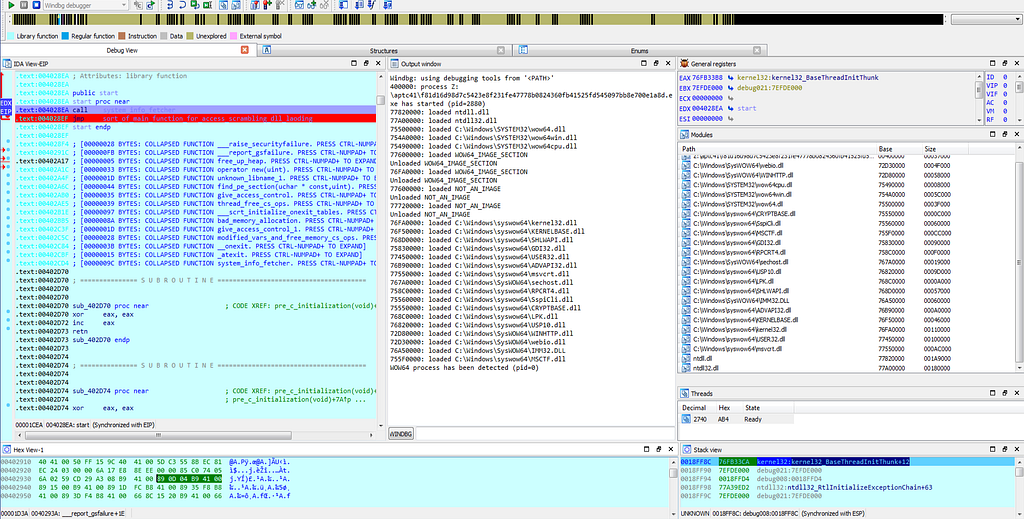 Text view of IDA hitting at system_info_fetcher function in start function.
Text view of IDA hitting at system_info_fetcher function in start function.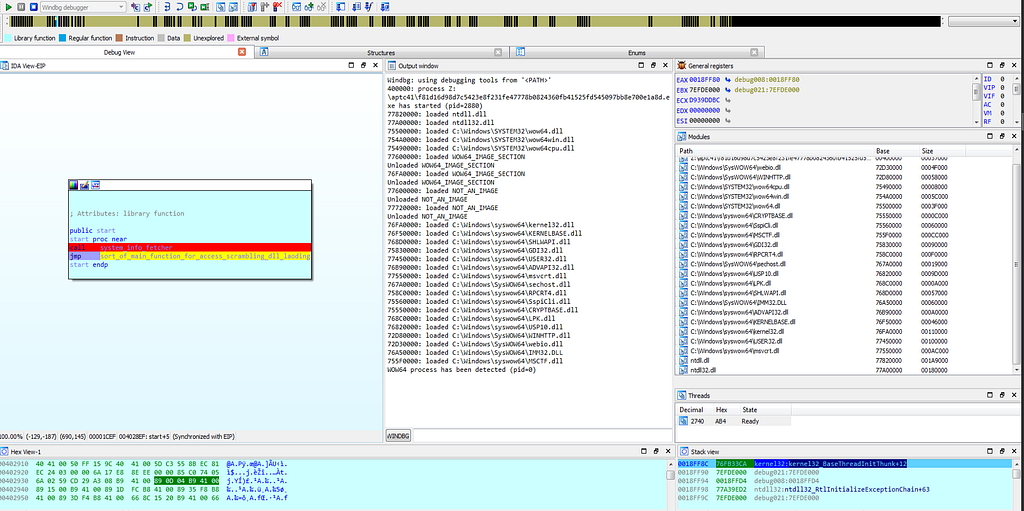 Graph view of IDA hitting at system_info_fetcher function in start function.
Graph view of IDA hitting at system_info_fetcher function in start function.Soon after first breakpoint the debugger gets hits at the “004024FE” in WinMain function.
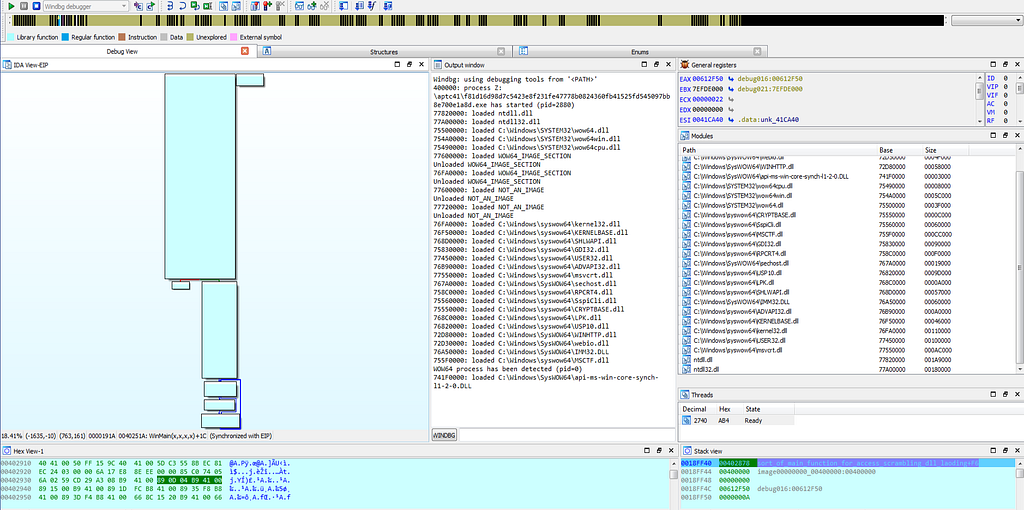
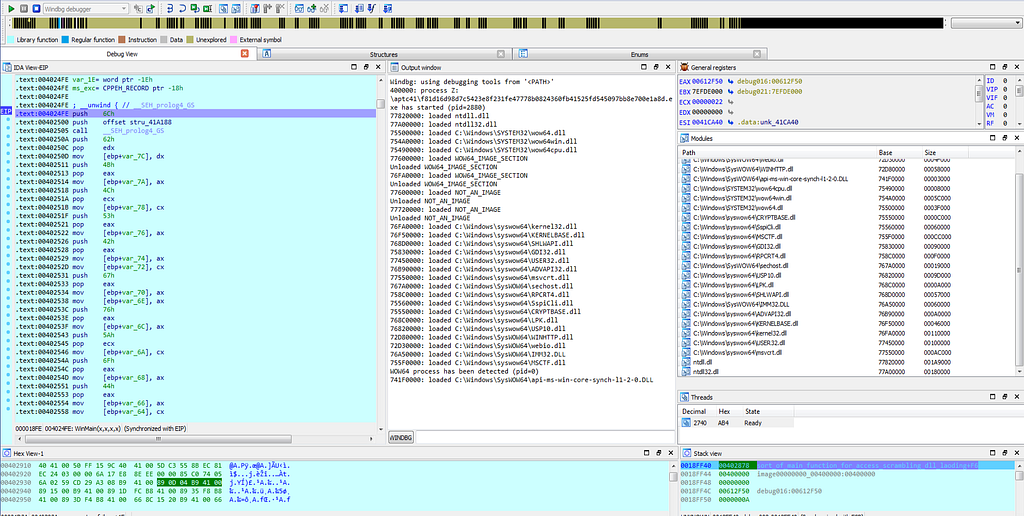 Graph view & Text View of IDA hitting at 004024FE location in WinMain function.
Graph view & Text View of IDA hitting at 004024FE location in WinMain function.Then after that , the breakpoint is being hit at “75492E09”.
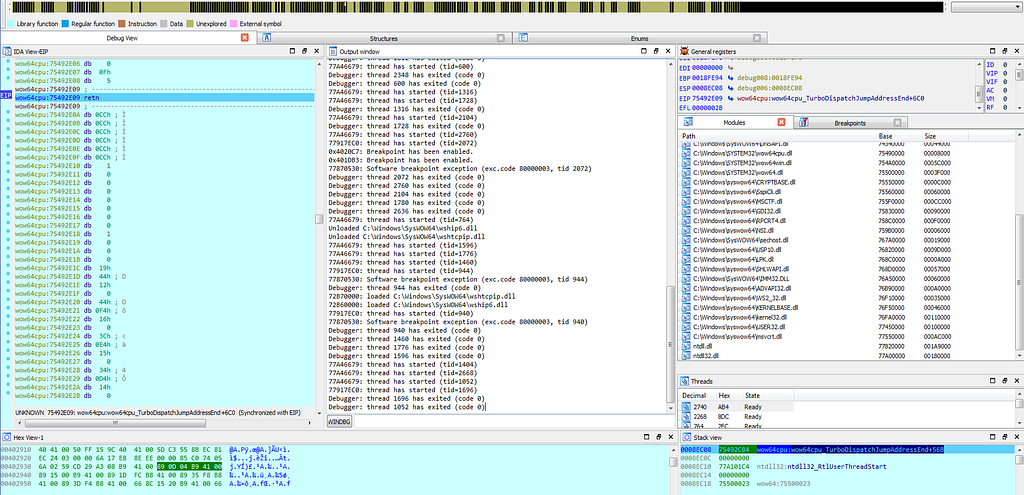 Text View of IDA hitting at 75492E09 location.
Text View of IDA hitting at 75492E09 location.As the execution of debugger continues, the debug gets hit at the debugbreak in sub-routine “sub_77870530" which is just having the debugbreak function in it.

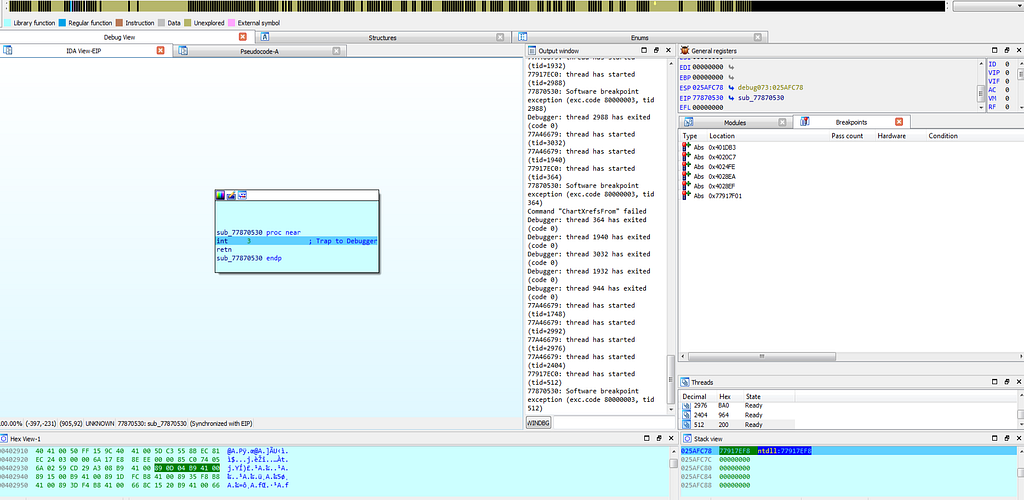 Graph view & Text View of IDA hitting at “sub_77870530” sub-routine.
Graph view & Text View of IDA hitting at “sub_77870530” sub-routine.Since, execution on that debugbreak stops due to “debug trap” that is hardware interrupt and what that means is that debugger gets hits at the hardware breakpoint and after such interrupt no execution of debugging instruction will take place in memory and execution will only loop around the debug trap only.
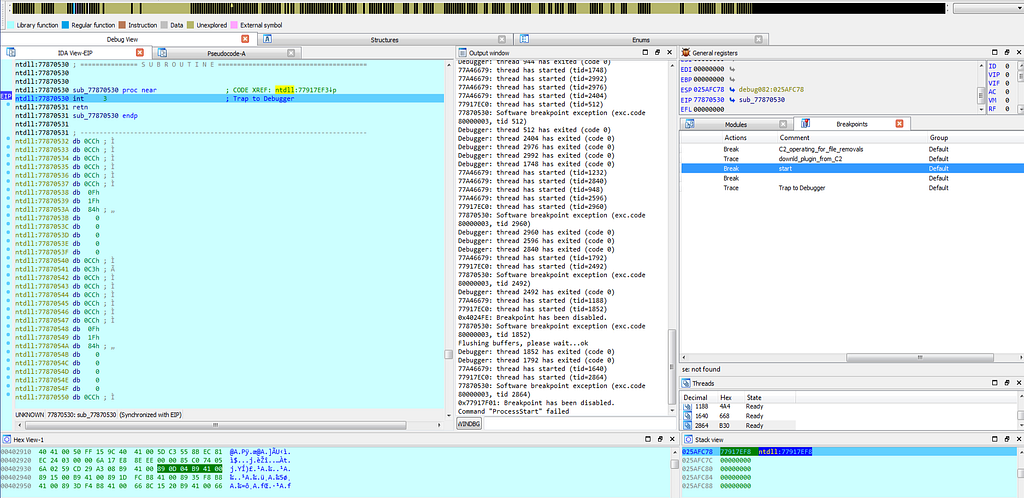 Graph view & Text View of IDA hitting at debug trap (Hardware Interrupt aka Hardware Breakpoint).
Graph view & Text View of IDA hitting at debug trap (Hardware Interrupt aka Hardware Breakpoint).So by stopping the debugging and setting again two breakpoints :
..:- load_plugin_from_C2
..:- make_requests_to_C2 .
When the first debugger breakpoints gets hit results are as shown below.
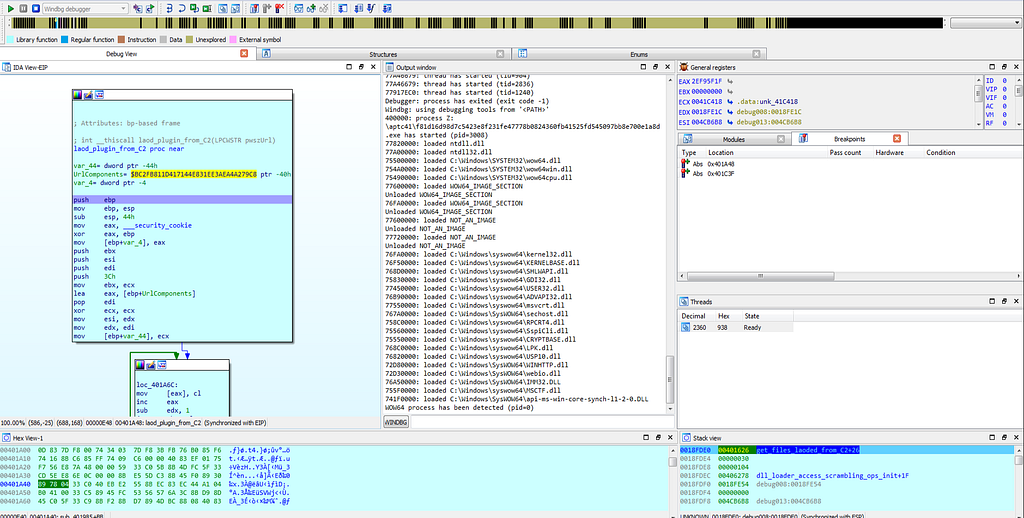
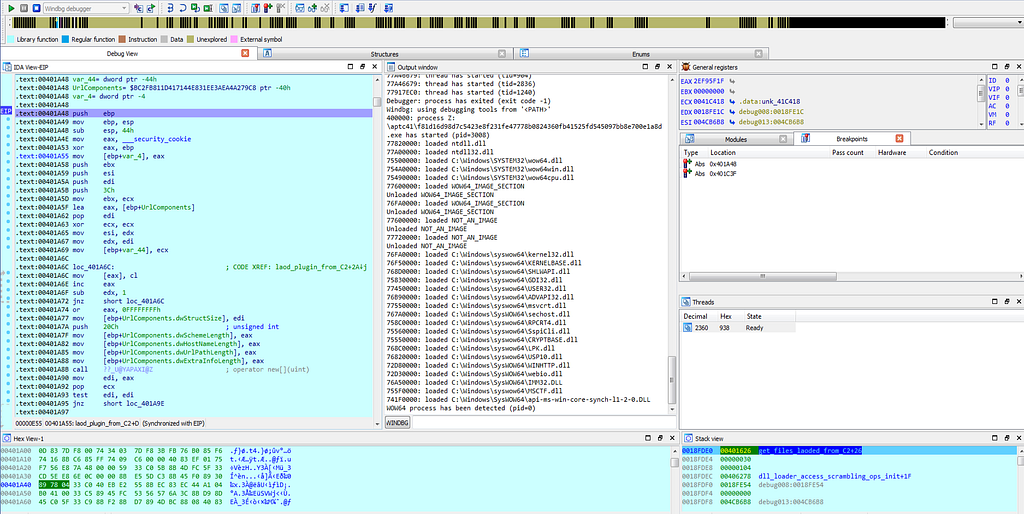
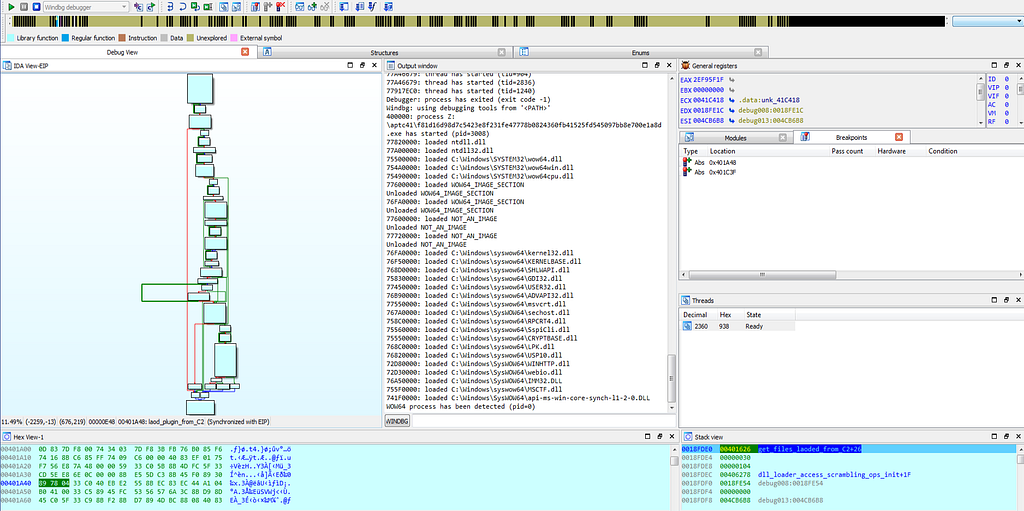 Graph view & Text View of IDA hitting at get_files_loaded_from_C2 sub-routine.
Graph view & Text View of IDA hitting at get_files_loaded_from_C2 sub-routine.while executing further the execution gets to second breakpoint “make_requests_to_C2"
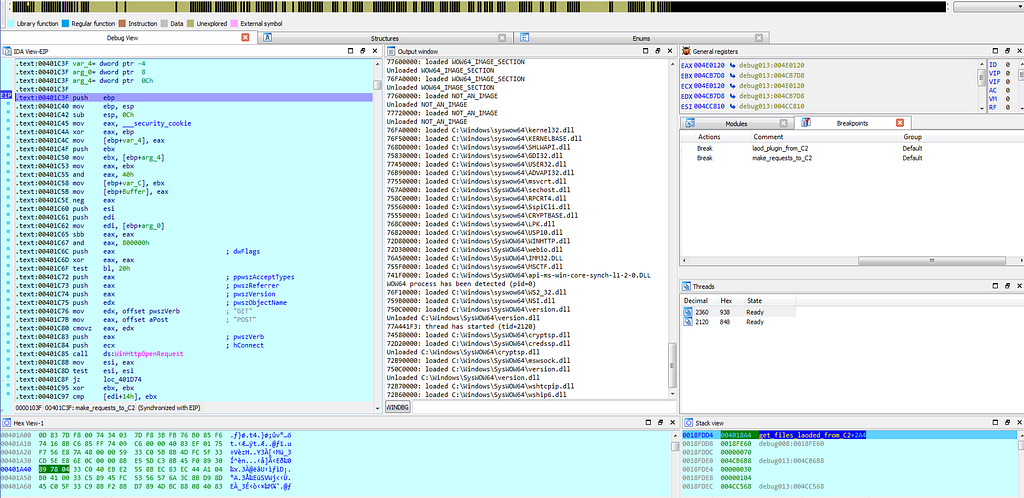
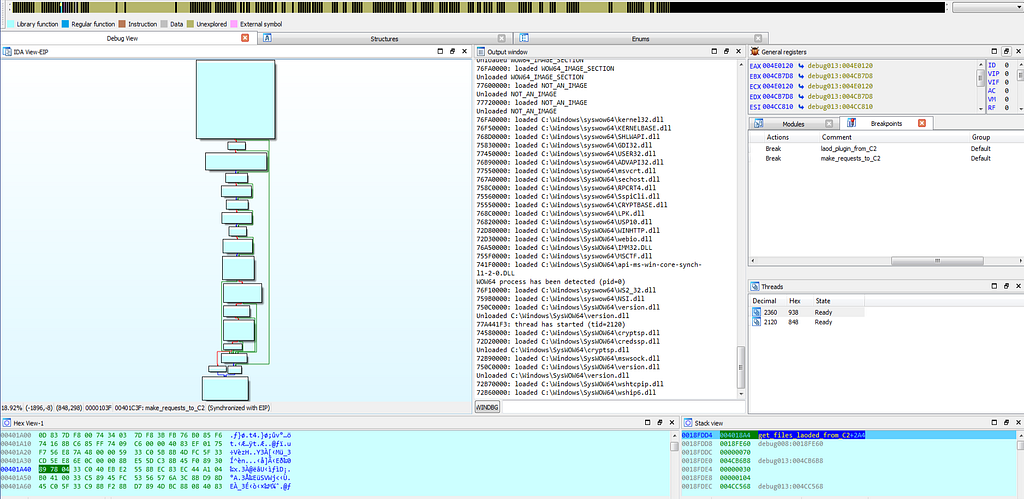
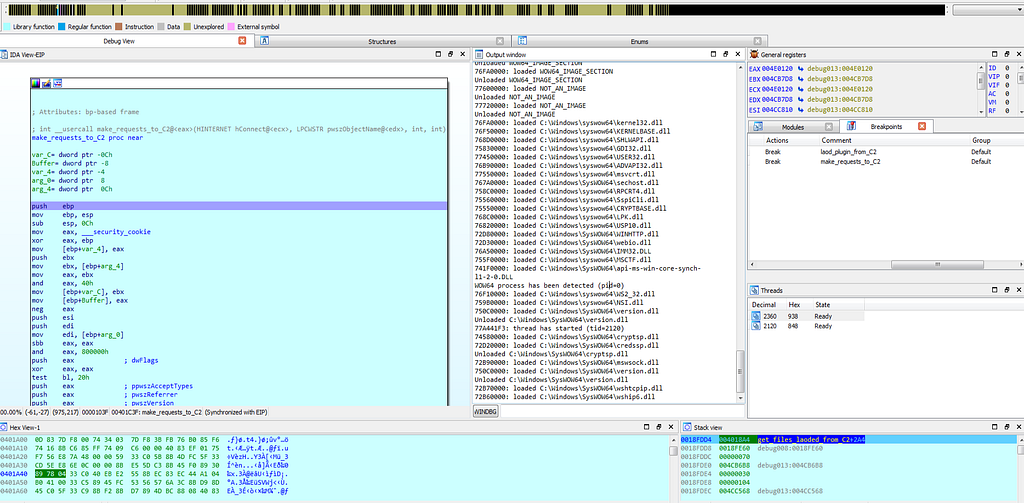 Text View & Graph view of IDA hitting at make_requests_to_C2 sub-routine.
Text View & Graph view of IDA hitting at make_requests_to_C2 sub-routine.Since, execution on that debugbreak stops again due to “debug trap” and after such interrupt no execution of debugging instruction will take place in memory and execution will only loop around the debug trap only.
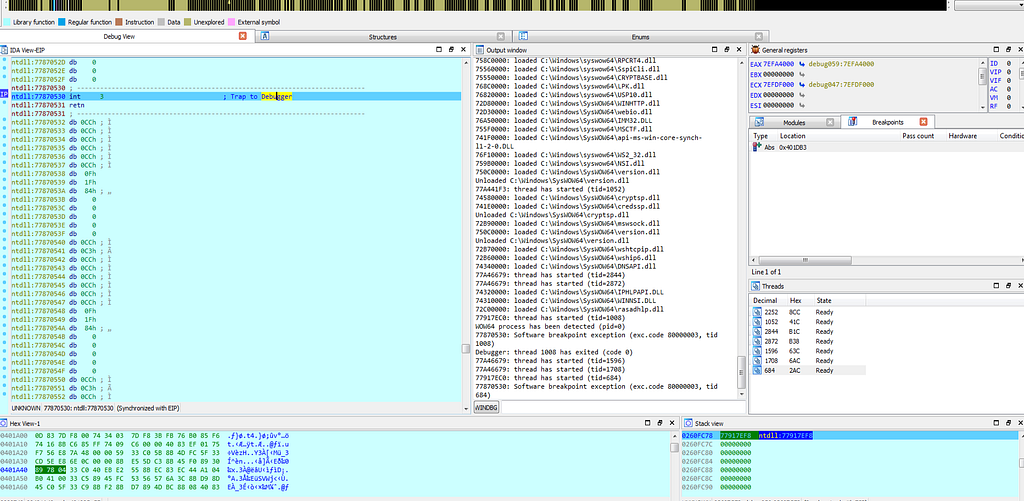
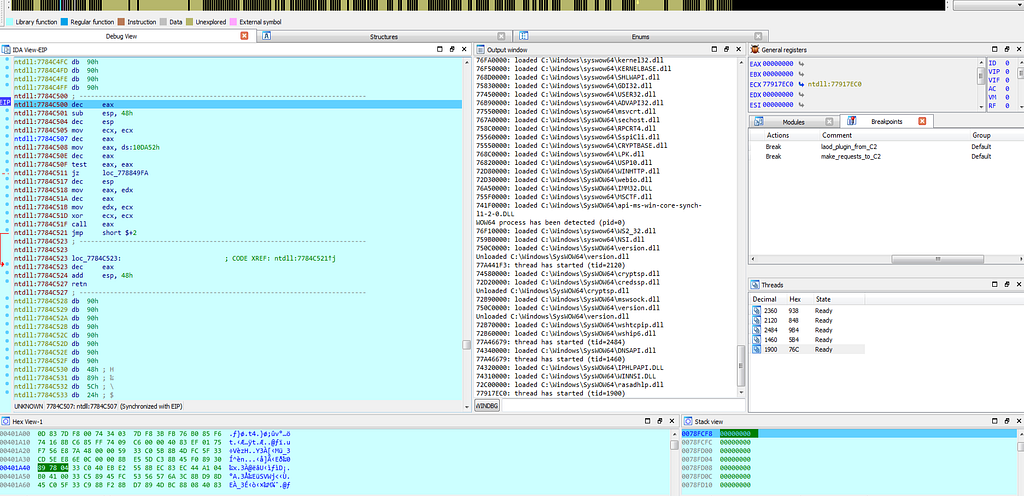 Graph view & Text View of IDA hitting at again at debug trap (Hardware Interrupt aka Hardware Breakpoint).
Graph view & Text View of IDA hitting at again at debug trap (Hardware Interrupt aka Hardware Breakpoint).Indicators of Compromise(IOCs) and Detections
Network [ C2 Communications]
91[.]219[.]238[.]31
Att&ck IDs
T1059, T1055, T1497, T1027, T1027.002, T1124, T1518.001, T1057, T1010, T1018, T1083, T1082, T1056, T1560, T1573, T1095, T1071.
Att&ck Mitre Techniques
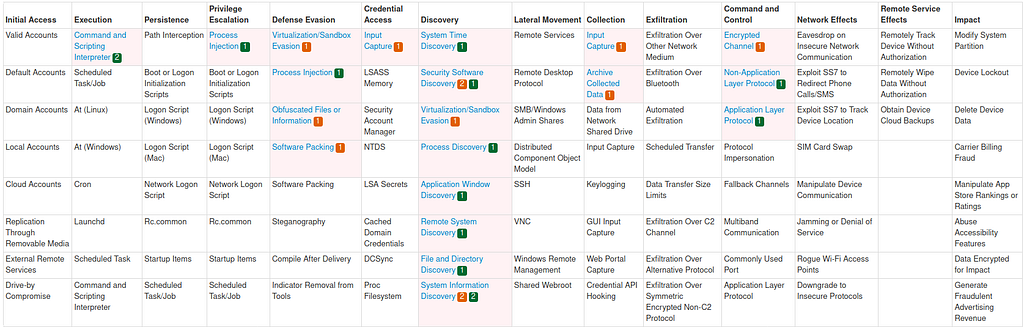
Sample from Report
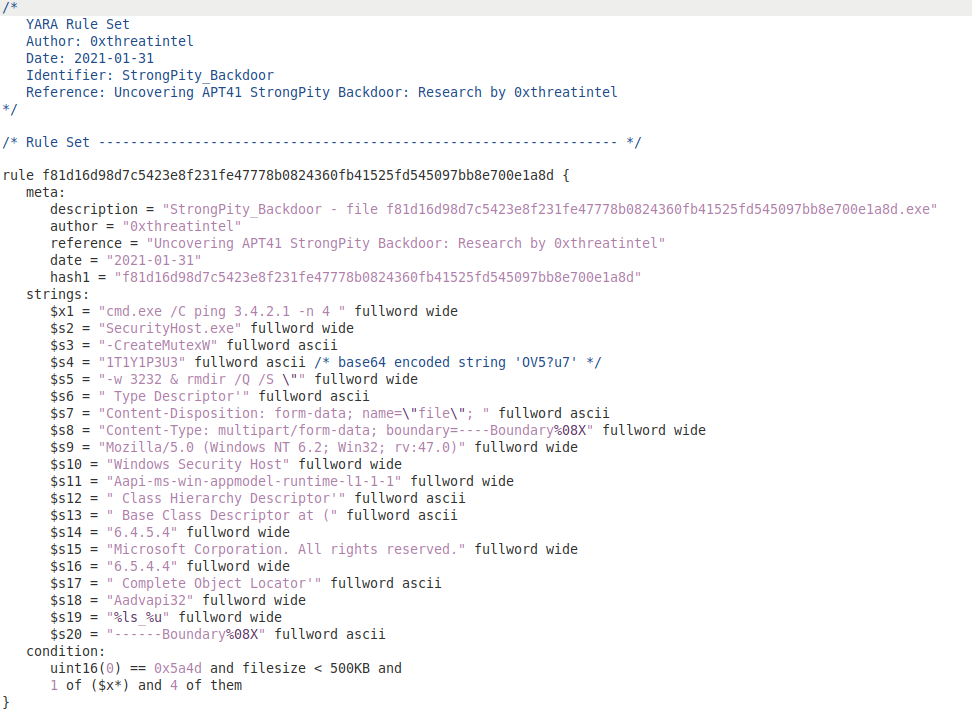
StrongPity Backdoor:
MD5: d7c62bc2a06d5abd872152ec87c64c8b
SHA1: 38ce3668ddfb00166ce6f68687d17c4a6cc91178
SHA256: f81d16d98d7c5423e8f231fe47778b0824360fb41525fd545097bb8e700e1a8d
YARA Signature:
Thank you for reading.
Article Link: https://medium.com/@0xthreatintel/uncovering-apt-c-41-strongpity-backdoor-e7f9a7a076f4?source=rss-a15183055fd6------2