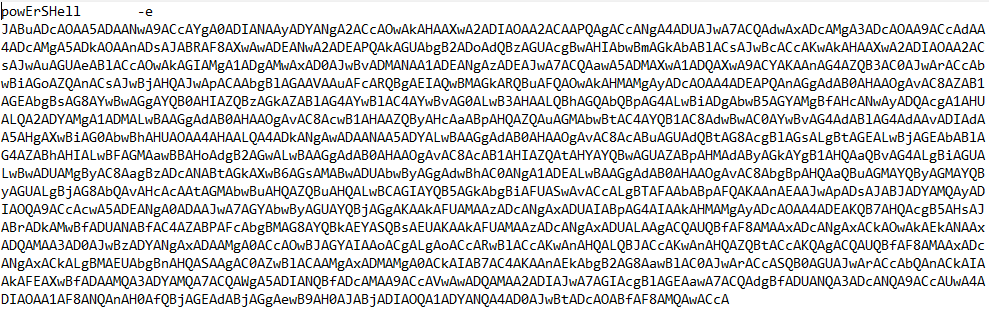SHA256 – 4221a9922d97fa329b3dbb27e37522448958cbfa186a6ef722e48d63f9753808
Download link – VirusTotal
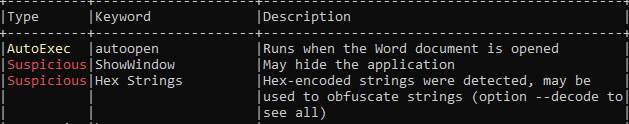
I downloaded this word document and checked whether macro present and it auto executes on opening document.
Yes, it does and it has obfuscated strings too.
I opened document and navigated to > Views > Macros > View Macros > Selected “autoopen” > Edit
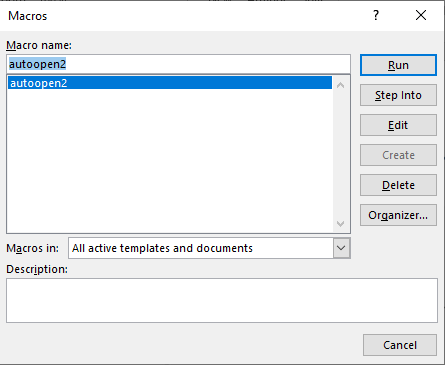
I renamed autoopen() to autoopen2. (Which you can see in above screenshot)
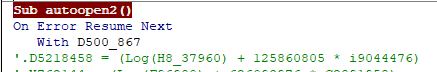
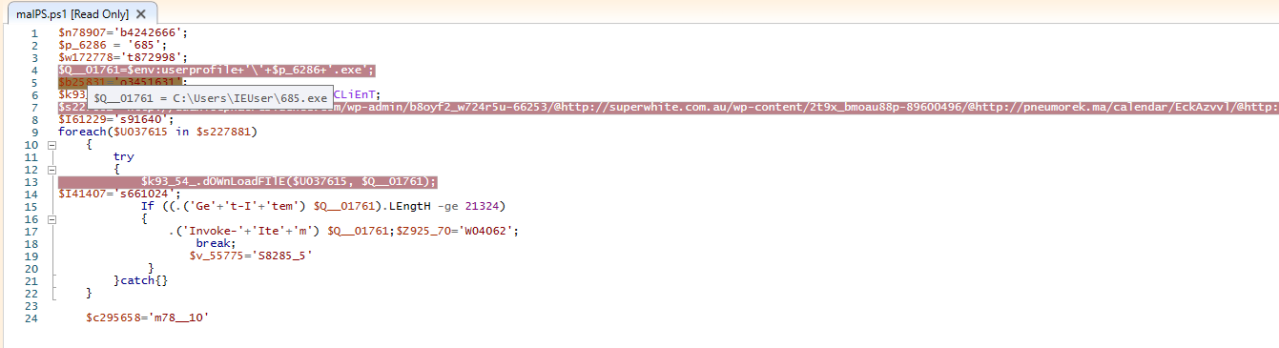
while debugging macro, found it executed PowerShell script in obfuscated form.
After deobfuscate, below is the PowerShell script.
On debugging PowerShell script, it tries to download 685.exe from one of below URL’s
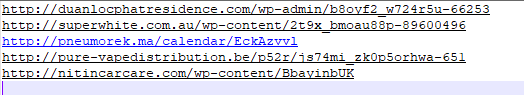
hxxp://duanlocphatresidence%5B.%5Dcom/wp-admin/b8oyf2_w724r5u-66253
hxxp://superwhite%5B.%5Dcom%5B.%5Dau/wp-content/2t9x_bmoau88p-89600496
hxxp://pneumorek%5B.%5Dma/calendar/EckAzvvl
hxxp://pure-vapedistribution%5B.%5Dbe/p52r/js74mi_zk0p5orhwa-651
hxxp://nitincarcare%5B.%5Dcom/wp-content/BbayinbUK
and drops PE file at location C:\Users\<user>\685.exe
While debugging PowerShell script, I tried to hit the download script but found none of above URL’s has PE file.
The file is removed from all URL’s.
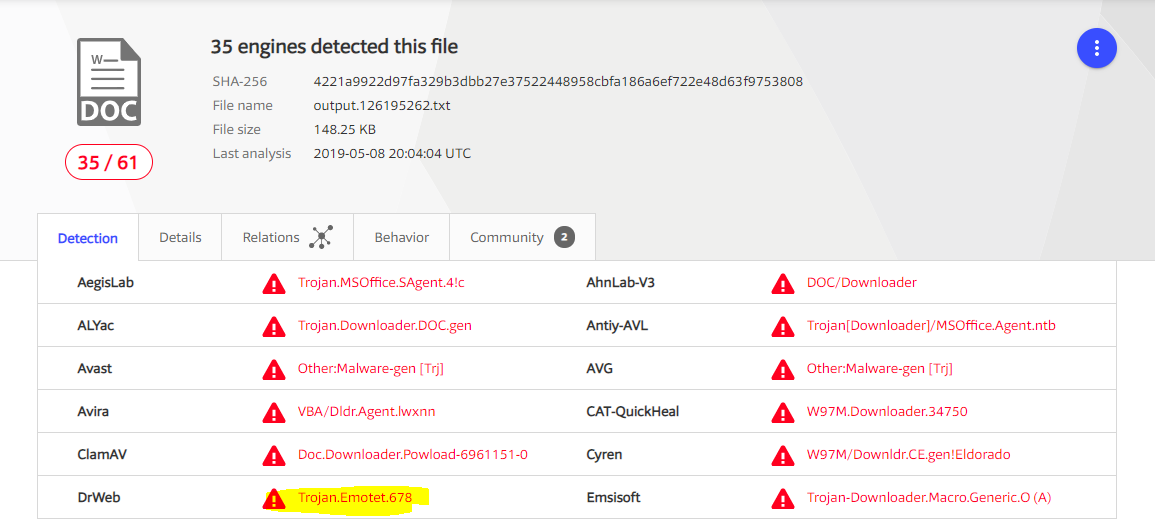
Below is VirusTotal score.
Article Link: https://malwr-analysis.com/2019/05/14/trojan-downloader-word-macro/