Top 5 IoC Search & Enrichment Platforms
Indicators of Compromise (IoCs) are critical pieces of digital forensics that identify potential breaches in an endpoint or network. These digital assets assist information security professionals in detecting malicious activity or security threats, such as data breaches, insider threats, or malware attacks. However, as cybercriminals become more advanced, IoCs constantly change, making detection more difficult.
To help with this effort, several IoC search and enrichment platforms have emerged, each with a unique set of features to improve threat detection and response. These platforms offer real-time, actionable threat intelligence, automated IoC enrichment, and direct integration capabilities, making them valuable resources for organizations looking to improve their cybersecurity posture.
This article will look at the top five IoC search and enrichment platforms that stand out due to their large and active communities, extensive threat data, and integration capabilities.
RST Cloud
RST Cloud is a well-known provider of scalable and flexible threat intelligence and data enrichment solutions that help businesses with their cybersecurity efforts. The platform distinguishes itself through its comprehensive approach to collecting, analyzing, and contextualizing threat data, which is critical for understanding and mitigating cyber threats.
RST Cloud’s key features include a comprehensive threat intelligence engine that aggregates data from multiple sources, including sandboxes and its own honeypot network, to provide contextualized threat intelligence.
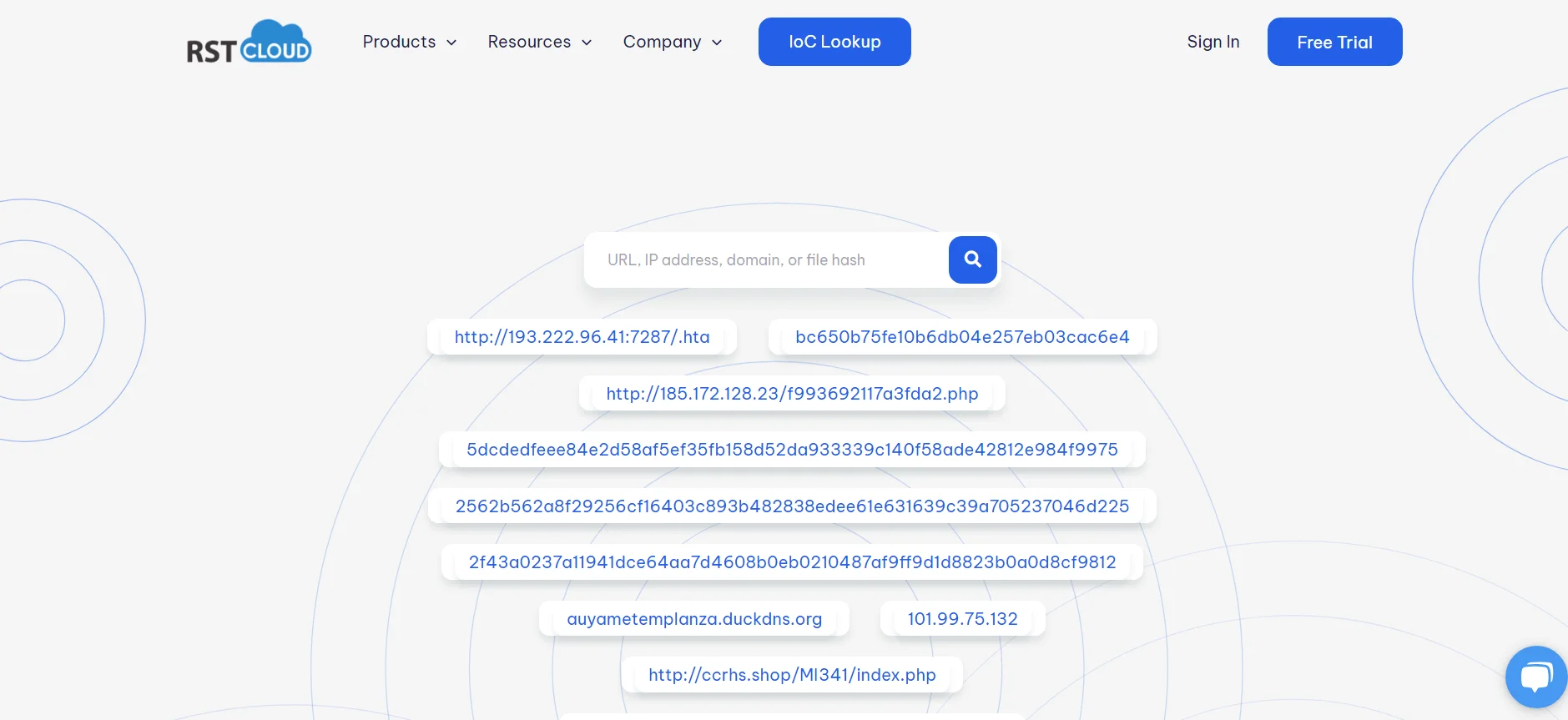
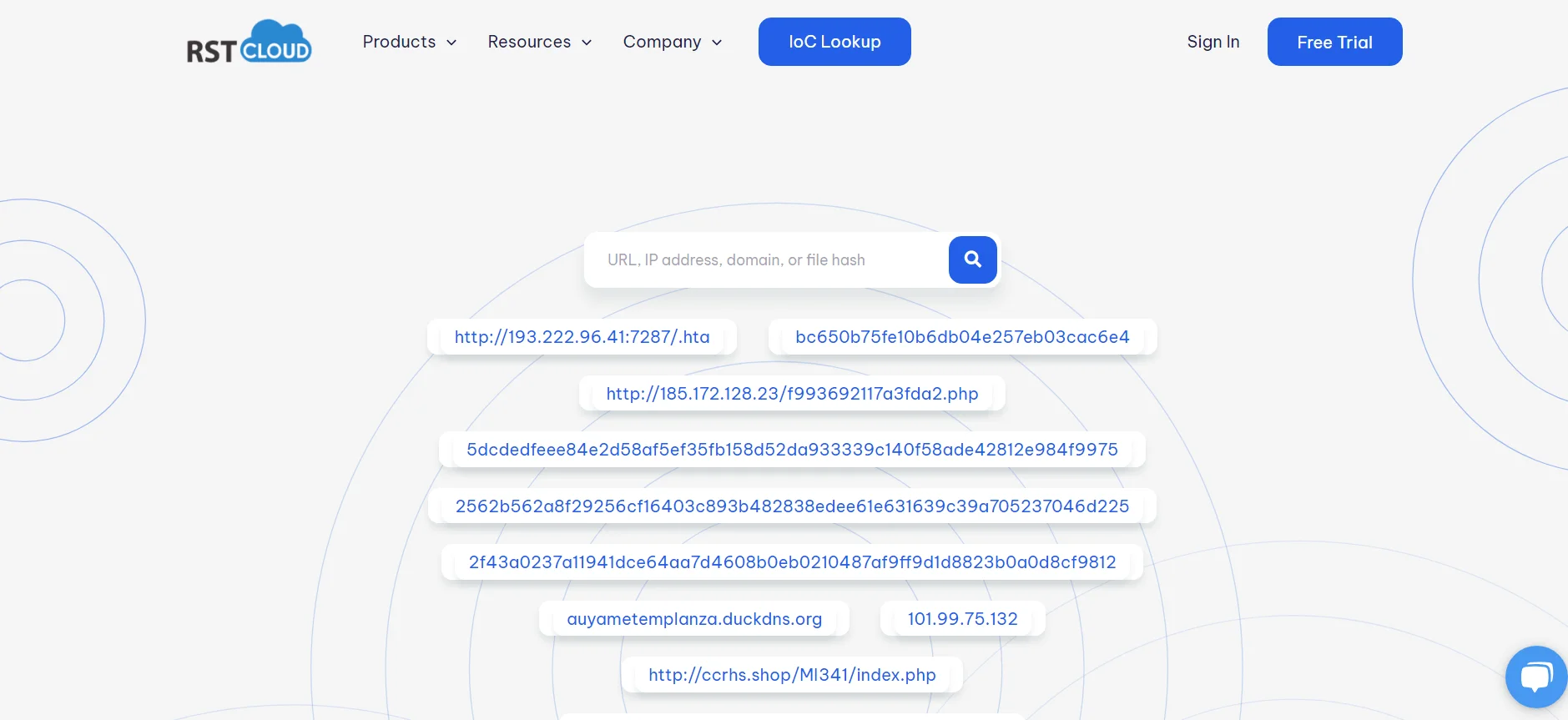
RST Cloud IoC Lookup
The platform provides detailed information about threat categories, malware families, threat actors, and vulnerabilities, which is critical for accurate threat detection and response. RST Cloud integrates seamlessly with popular security tools such as SIEM, SOAR, NGFW, and TIP, thereby improving existing security workflows.
The platform collects IoCs from various open and community-supported sources, enriching and ranking them to help cybersecurity professionals consolidate their knowledge of publicly available threat intelligence sources. A script is available that downloads IoCs from RST Cloud and imports them into MISP (Malware Information Sharing Platform & Threat Sharing) for analysis, which is useful for organizations that use MISP for threat intelligence.
The platform’s emphasis on high-fidelity information, as well as its comprehensive threat intelligence approach, position it at the forefront of effective cyber threat management solutions.
CrowdStrike
CrowdStrike, a cybersecurity platform, provides advanced cyber threat protection solutions. Its Falcon® platform is central for IoC search & enrichment, using real-time attack indicators, threat intelligence, and improved monitoring to provide enhanced security.

CrowdStrike logo
The Falcon platform enables real-time threat detection and integration capabilities. The platform’s incorporation with Cybersixgill’s real-time contextual threat data enabled proactive malware analysis and automated IoC enrichment.
The incorporation also provides early warning and investigation capabilities, machine-to-machine automation, advanced threat hunting for malicious IoCs, and contextual understanding of IoCs.
AlienVault Open Threat Exchange
AlienVault Open Threat Exchange (OTX) is a top threat intelligence platform that offers practical, community-powered threat data. It provides community-generated threat data, offering collaborative research, and automating the update of security infrastructure with threat data from multiple sources.
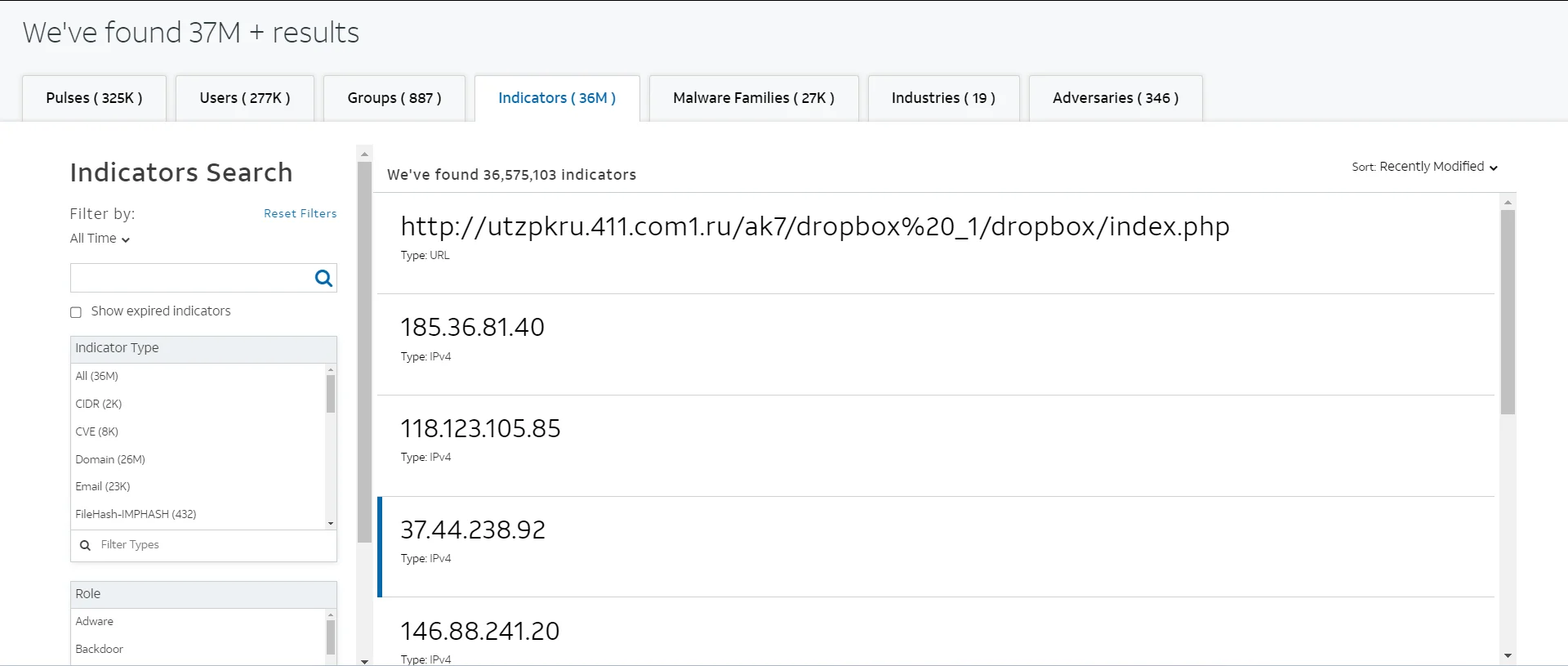
AlienVault Open Threat Exchange Indicators Search
AlienVault OTX’s key features include Pulses, which are the primary means by which the community shares threat information, as well as support for a wide range of Indicators of Compromise (IoCs). The platform promotes active discussion, research, validation, and sharing of the most recent data and trends among the security community. It also provides several methods for security tools to ingest pulse data, allowing for faster and more efficient threat response.
AlienVault OTX provides its participants with real-time, actionable information, allowing them to respond immediately to emerging threats. It processes over 19 million new IoC records per day, providing users with valuable threat intelligence. The platform is known for its user-friendly interface, as well as its large and active community, which shares millions of potential threats on a daily basis.
Malware Domain List
The Malware Domain List is a community-driven project that catalogs domains associated with malware, such as ransomware and trojans. It provides detailed information about each domain, including the URL, IP addresses, the type of threat it represents, and other information such as the registrant, reverse lookup, and ASN.
PrecisionSec’s Malware Domain List
PrecisionSec’s Malware Domain List is a high-fidelity feed of domains currently being used by malware. Experts around the world use this feed to identify and block malicious domains that are known to be associated with malware. It is essential for Data resellers, and MSSPs, or Security Managers to protect their assets and customers from ransomware attacks.
The Malware Domain List improves cybersecurity through real-time updates and expert support. Malicious domains are assigned to specific types of malware or malware families, which improves understanding and response to threats.
Domains are considered strong Indicators of Compromise (IoCs) and can indicate when a network has been breached. Domains used in phishing or social engineering scams can be identified and investigated for threat hunting purposes. Analyzing DNS logs can reveal unusual traffic patterns and the use of Domain-Generating Algorithms (DGAs), which are frequently used by attackers to create new domains for malware.
SOCRadar’s Threat Feed / IOC
SOCRadar’s Threat Feed & IOC module is a comprehensive cybersecurity solution that delivers enriched data and actionable intelligence to help organizations stay ahead of cyber threats. This module is intended to provide cybersecurity teams with comprehensive and enriched data, serving as a critical resource for researching and combating cyber threats.
The module includes user-friendly dashboards that enable professionals to customize feeds based on their specific requirements. It allows users to stay up to date on recent threats, easily search for Indicators of Compromise (IoCs), and benefit from seamless integration with their systems via the TAXII protocol.
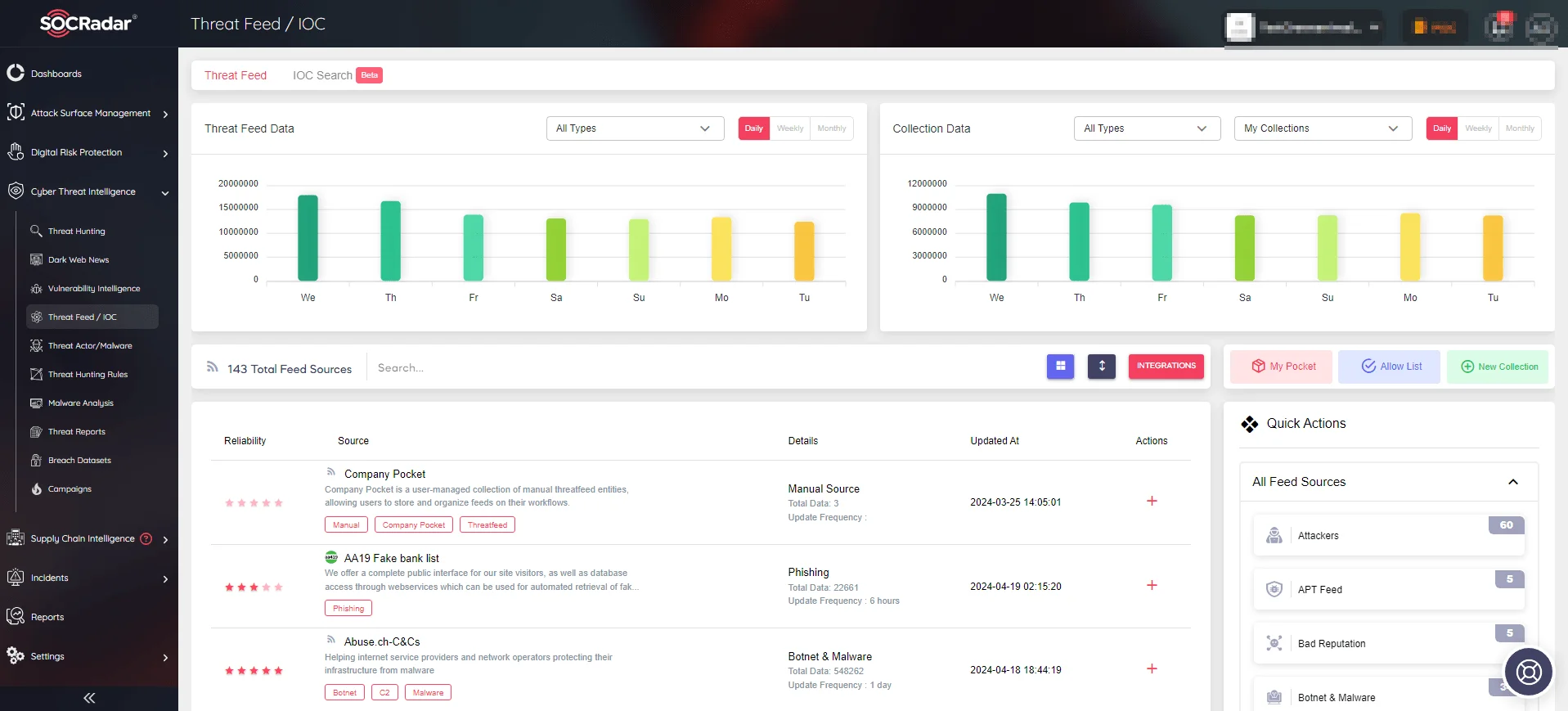
SOCRadar’s Threat Feed & IoC Management module
Furthermore, the module supports bulk searches, which enable users to query multiple IoCs or IPs from a single screen. This functionality is extremely useful, especially when defenders are dealing with newly emerging threats and time is critical.
SOCRadar combines a variety of threat feeds, transforming massive amounts of data into actionable intelligence. This enables rapid detection, thorough analysis, and effective response to emerging threats, thereby strengthening an organization’s resilience in the ever-changing cyber landscape.
Test the module’s IoC search capabilities using SOCRadar Labs’ IoC Radar, which is a supplementary version.
SOCRadar Labs’ IoC Radar
Article Link: Top 5 IoC Search & Enrichment Platforms - SOCRadar® Cyber Intelligence Inc.
