As enterprises march deeper into incorporating 5G for their digitization initiatives, the impact on security could turn out to be profound. Are you an enterprise getting ready to adopt 5G? Here, you’ll learn the top five security considerations to keep in mind when deploying 5G for enterprises.
A widespread perception is that only service providers and telcos are investing in 5G. The reality is that enterprises around the world are leveraging private 5G networks. In fact, 5G is now the catalyst of change for many enterprises, driving the future of Industry 4.0 digitization initiatives. Private 5G networks enable new enterprise use cases not previously possible, allowing for industrial-scale IoT networks with ultra-low latency, mission-critical reliability and a high degree of mobility. Due to its compelling value proposition as a major driver of business transformation, 5G adoption is growing rapidly across numerous industry verticals worldwide.
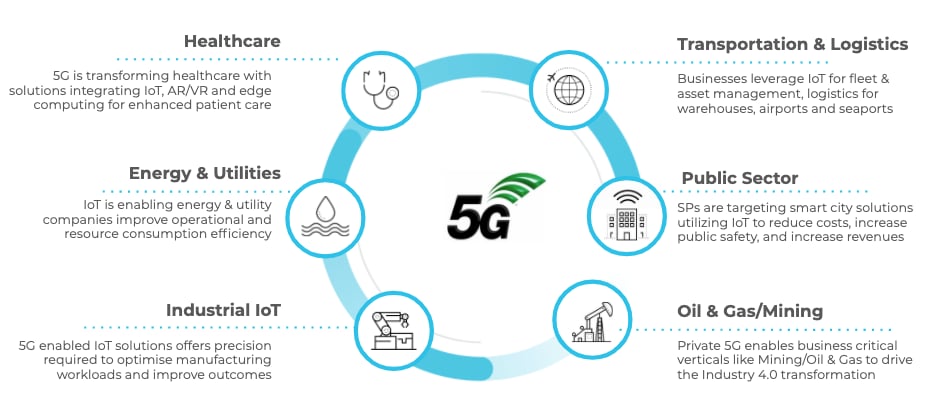
As enterprises continue to rethink connectivity and accelerate their digital transformation journey, we see them invest in 5G networks with a specific focus on driving digitization, accelerating IoT adoption and harnessing innovative techniques to deliver enterprise connectivity, improve productivity and increase operational efficiencies. Owing to IoT growth and development of smart cities initiatives, smart homes and smart industries, we see 5G has a key role to play with the potential to offer reliable, high performance solutions. Business and mission-critical applications for enterprise 5G will include use cases such as energy, utilities, critical infrastructure, manufacturing, logistics and fleet management. These are the beginnings of the 5G digital economy, a hyper-connected world full of possibilities – as well as cybersecurity challenges that should be addressed now.
Taking the Pulse of Enterprise 5G
There are plenty of great reasons for enterprises to adopt 5G. According to an ABIResearch report, “Private cellular networks for industrial use have the potential to boost gross margin by 5% to 13% for factory and warehouse operations that fully embrace Industry 4.0.” The graphic below shows more information about how 5G can transform various industries.
Enterprise 5G applications are served either through public service provider 5G networks or private cellular networks, such as Private LTE/Enterprise 5G. They can be deployed either standalone or in conjunction with public networks. Regardless of whether enterprises lease 5G networks or build their own, they have the opportunity to use them to build robust offerings with innovative applications and services.
Are Enterprise 5G Networks Secure Enough?
New enterprise 5G trends demand a new approach to security. The modern mobile IoT environment poses greater IoT security risks, with business-critical operations at stake. More devices and data mean more targets for cyberattacks. Cyberattacks grow innovative, automated and “defense-aware.” While the attack targets and techniques are constantly evolving, the most common threats faced by enterprises offering business-critical services are cyberespionage to gain access to control systems, spear phishing campaigns run by nation-states to gain key business intelligence, cryptomining and ransomware.
Cybersecurity is more important than ever when securing 5G. Businesses need to establish a strong security posture that can stop cyberattackers from infiltrating their networks, disrupting critical services, destroying industrial assets or threatening the safety of the environment. In mission-critical industries, security breaches cost more than just downtime, lost revenue and tarnished brands – they can put human lives in jeopardy. A high level of cybersecurity readiness will ultimately reduce the risk for private network investments.
But wait, don’t take our word for it – yet. Let’s decode.
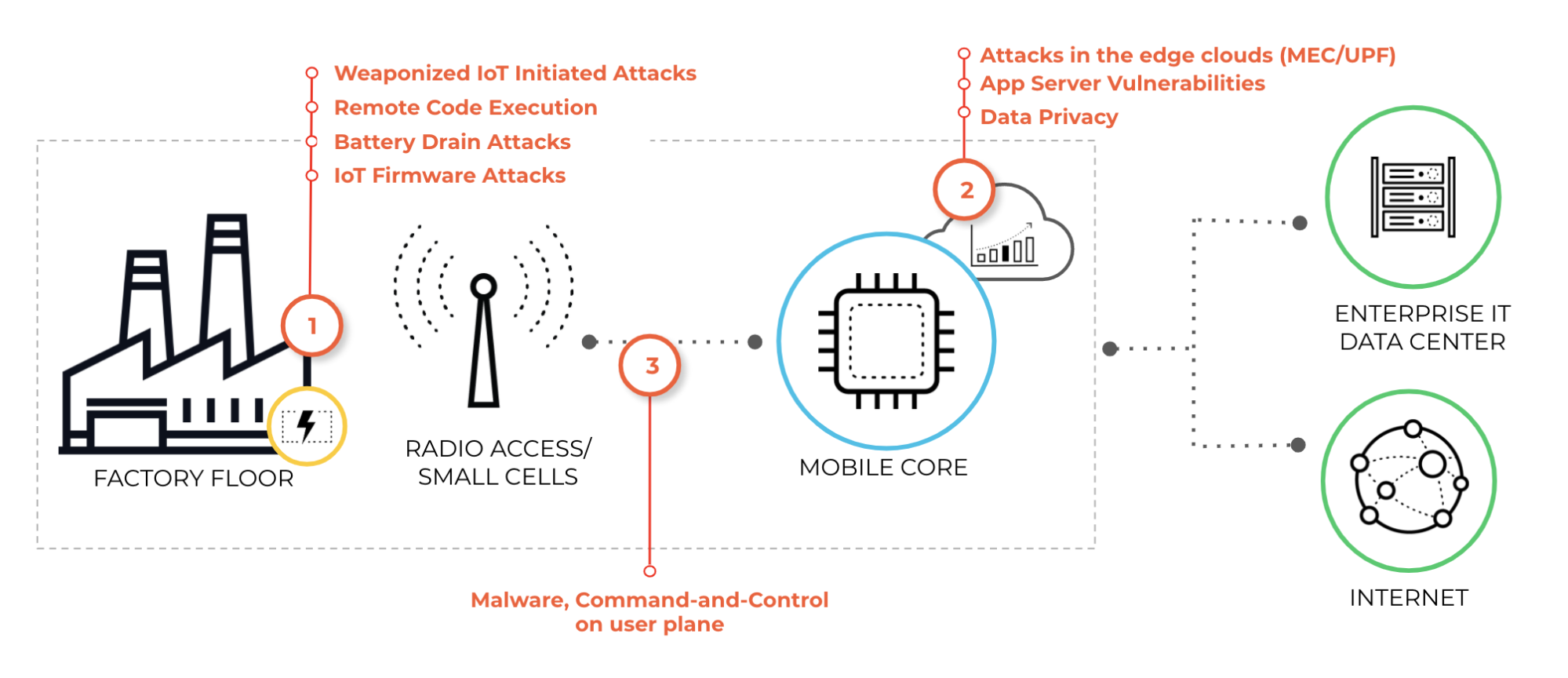
Cyberattacks take advantage of the speed and volume of traffic associated with 5G and challenge security teams to create novel methods for tackling threats. Three critical areas need to be secured in any enterprise 5G deployment:
- IoT/Machine to Machine (M2M) devices across industry verticals are an integral part of enterprise 5G/IoT strategy. These include sensors, actuators and other M2M/IoT devices. Some of them may communicate only occasionally – perhaps just once a month – while others communicate frequently at regular time intervals. According to the 2020 Unit 42 IoT Threat Report, 98% of all IoT traffic is unencrypted, exposing personal and confidential data on the network. The report also found that 57% of IoT devices are vulnerable to medium- or high-severity attacks. Organizations keen on adopting IoT must understand the cybersecurity risks that the technology may bring. Hackers are now capable of launching cellular connectivity-based attacks to disrupt IoT devices to transmit and stream their data for “data harvesting” attacks. ML-driven visibility, security enforcement and automation fulfill the need of the hour.
- We see a vast increase in intelligence at the network edge to support latency-critical applications, likely in the form of a gateway. According to Gartner, 75% of enterprise-generated data will be created and processed at the edge by 2025. Here, all the enterprise IoT traffic, such as from M2M devices/sensors, will be aggregated into different groups and sessions. The network edge also provides edge intelligence, analytics and telemetry to support latency-critical applications. Cloud deployments are moving faster than their security solutions. A Zero Trust ecosystem is the best way to ensure consistent enforcement of security policies across an enterprise 5G network.
- The network core, where all the traffic is aggregated, and where analytics and signaling control resides, provides critical functionality, such as mobile session authentication and management, quality of service and packet inspection and more. The network core components can be attacked by in-network IoT devices infiltrated and weaponized with malware to launch a DDoS attack on the network.
To sum up, the proliferation of devices, vast increase in intelligence at the network edge and the aggregation of critical functionality at the network core bring out three main challenges that together contribute to a perfect storm of security risk in enterprise 5G deployments.
1. Limited Visibility
- Challenge: Lack of ability to identify compromised assets/users in an enterprise 5G network.
- Potential Impact: Network congestion and service outages.
2. No Prevention
- Challenge: No real-time threat prevention mechanisms for safe enablement of applications.
-
Potential Impact: Risk to your enterprise operations and downtime.
3. Unknown Threats
- Challenge: Increased attack surface with new vulnerabilities and exploits that are not yet understood.
- Potential Impact: Difficulty in keeping up with unknown threats infiltrating the network.
New Enterprise 5G Trends Demand a New Approach to Security: The Top Five Security Considerations
Enterprises should use the following key security practices to help navigate risks and secure their 5G networks, while enabling a seamless experience and advancing the digitization of the business:
- Visibility: Implement visibility and control to uniquely scan the enterprise 5G network. Secure integrated supply chain to support myriad suppliers and business partners with customizable security permissions and access privileges.
- Control: Use cloud-delivered advanced threat protection to detect and stop malware, command and control traffic, and other vulnerabilities. Implement ML-Based Inline Threat Prevention to stop zero-day threats to both OT and IT, to secure your valuable assets and maintain uninterrupted operations.
- Enforcement: Adopt a Zero Trust security model for edge clouds and private networks for consistent security visibility, enforcement and analytics across your 5G network.
- Dynamic Threat Correlation: Implement Subscriber- and Equipment ID-based security enforcement to correlate, isolate and quarantine infected devices.
- Lifecycle: Improve threat and overall network visibility by illuminating usage patterns and potential security gaps through automated analysis of the evolving threat landscape.
A strong security posture portends successful digital transformation. Enterprises need to have constant real-time visibility and granular control of traffic passing through their networks. Only then can they detect and stop malicious activities and threats in 5G and build an effective and efficient scalable defense against IoT-based botnets.
Learn more about securing private 4G/5G mobile networks.
The post Top 5 5G Security Considerations for Enterprises appeared first on Palo Alto Networks Blog.
Article Link: http://feedproxy.google.com/~r/PaloAltoNetworks/~3/9P_TxkLnl7U/