In the ever-evolving cybersecurity landscape, breaches have become all too common, sending shockwaves through industries and leaving organizations scrambling to recover. One such significant breach that has recently dominated headlines is the MOVEit breach. MOVEit, a widely used file transfer platform, became the target of a sophisticated cyberattack that compromised the data of millions. This breach exposed the vulnerabilities inherent in some of the world’s most trusted platforms and highlighted the audacity and capabilities of modern cybercriminals. Furthermore, becoming the primary attack vector for the Cl0p ransomware group, it has led to many other attacks.
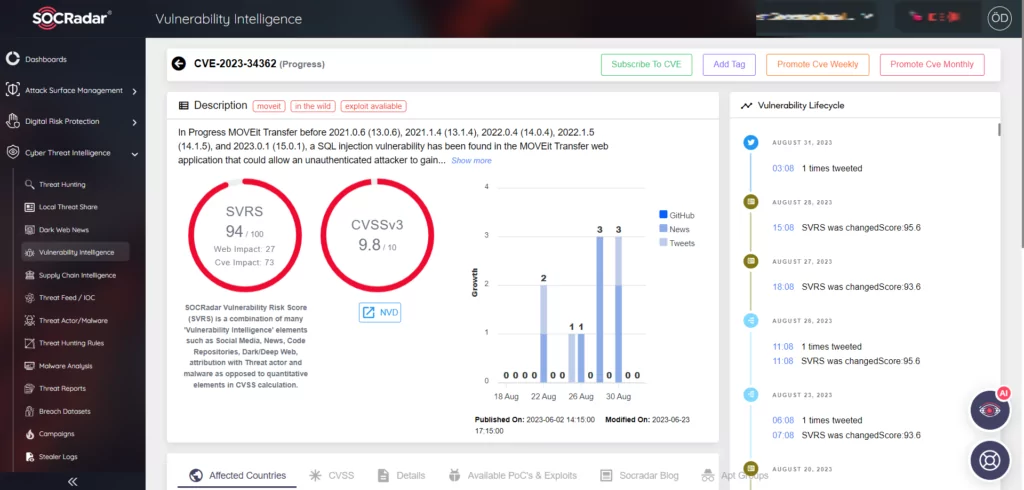 Figure 1. The abused zero-day in MOVEit breach. (SOCRadar Vulnerability Intelligence)
Figure 1. The abused zero-day in MOVEit breach. (SOCRadar Vulnerability Intelligence)
In this article, we delve into the top 10 facts about the MOVEit breach, shedding light on its magnitude, the perpetrators behind it, and the lessons we must take away to fortify our digital defenses. Join us as we unpack the statistics, analysis, and far-reaching implications of one of 2023’s most significant cyber incidents.
What is MOVEit and Who Uses It?
MOVEit, created by Progress Software Corporation, serves as a widely utilized file transfer solution embraced by numerous entities globally, ranging from government agencies and financial institutions to various public and private sector organizations. Its primary purpose revolves around securely facilitating the exchange of information. MoveIT was also an app recommended by the Department of Defense and used by many US-based companies.
When Did the MOVEit Breach Occur and Who Was Behind It?
During late May 2023, MOVEit users encountered unusual data transfers. Instead of the typical file exchanges initiated by authorized users, data was being illicitly extracted by a ransomware group called Cl0p. This incident was not inadvertent; MOVEit had been intentionally singled out and compromised by these threat actors. On June 1, MOVEit released patches to the vulnerability, which cybersecurity researchers flagged. In the same week, huge companies such as Zellis, BBC, and British Airways experienced data breaches over MOVEit. Furthermore, as per findings from Kroll researchers, Cl0p has retained access to the MOVEit vulnerability since 2021, indicating that this persistently exploited weakness will continue to pose significant challenges for an extended period.
How Many Organizations and Individuals Were Affected by the MOVEit Breach?
According to Emsisoft, by the end of August, 2023, the breach had affected 1,062 organizations and approximately 65,435,641 individuals. This information has been gathered from multiple channels, encompassing state breach notifications, SEC filings, public disclosures, and even Cl0p’s website.
Which Organizations Suffered the Most Due to the MOVEit Breach?
Several organizations experienced a significant impact due to the breach. Some of the most affected with high numbers of individuals include:
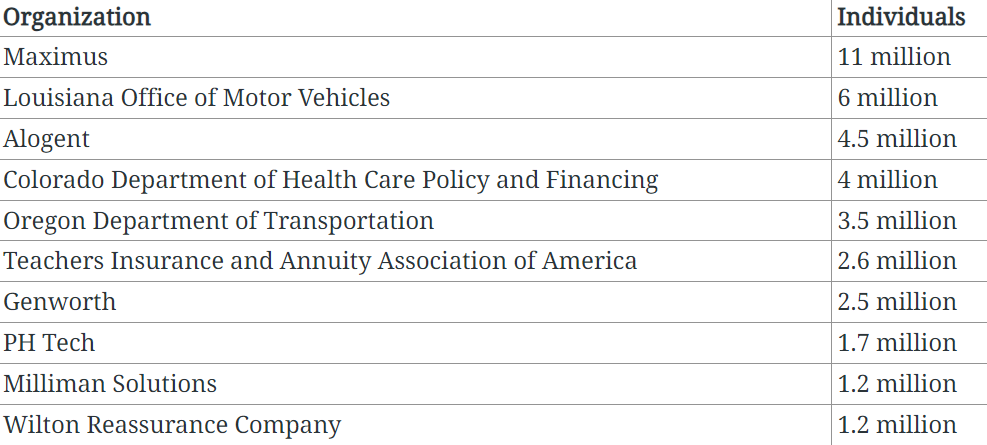 Figure 2. Highest numbers of individuals affected (Emsisoft)
Figure 2. Highest numbers of individuals affected (Emsisoft)
And some of the most famous victims include:
- The US Department of Energy,
- Shell Oil company,
- First National Bankers Bank,
- BBC,
- British Airways,
- Medibank,
- Siemens Energy,
- American Airlines,
- Warner Bros,
- ING Bank,
- Deutsche Bank
Which Countries and Sectors Were Most Heavily Impacted?
U.S.-based organizations bore the brunt of the breach, accounting for 84.7% of known victims. Following the U.S., Germany-based organizations made up 3.4%, Canada-based ones 2.6%, and U.K.-based organizations 1.9%. In terms of sectors, finance and professional services were the hardest hit, accounting for 23.8% of incidents, closely followed by the education sector at 19.7%. As previously noted, including MOVEit as a recommended application by the DoD may have played a significant role in the heightened targeting of US-based companies.
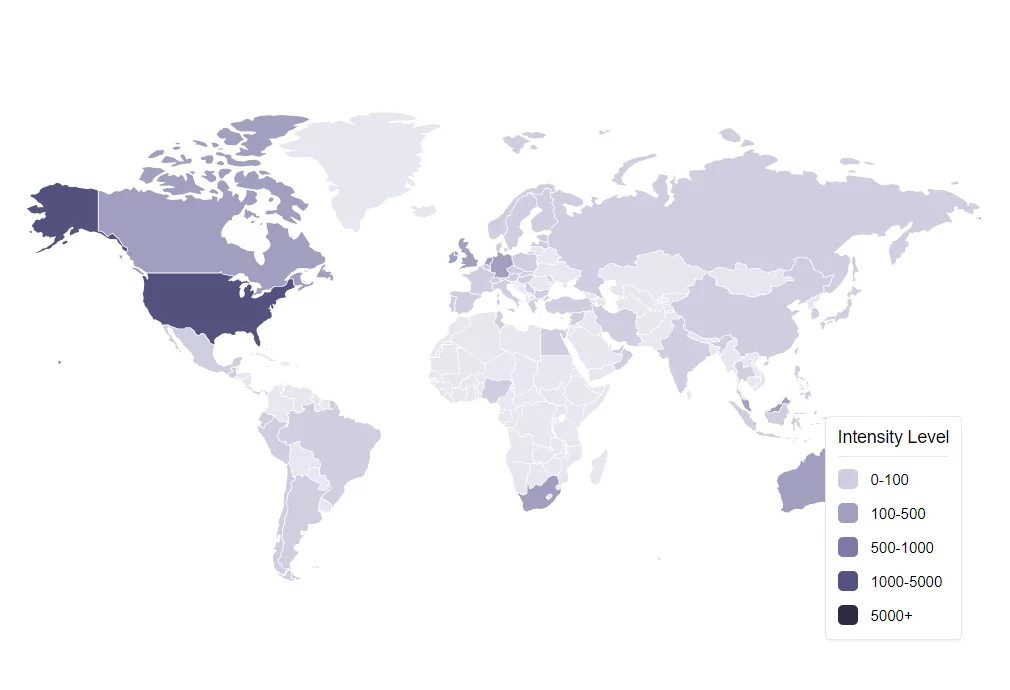 Figure 3. The intensity map of the affected countries.
Figure 3. The intensity map of the affected countries.
What is the Estimated Financial Impact of the MOVEit Breach?
According to TechCrunch, while it’s challenging to pinpoint the exact cost of the MOVEit incident, using IBM’s data breach cost average of $165 USD per record provides some insight. Based on the number of confirmed individuals affected, the cost of the MOVEit incident stands at approximately$9,923,771,385. However, considering not all victims have reported the number of individuals impacted, the potential cost could escalate to around $65,440,204,950.
How Did the MOVEit Breach Happen?
The breach’s origins can be traced back to May 31st when Progress Software identified and issued an advisory for a vulnerability labeled as CVE-2023-34362, which had a severity rating of 9.8 out of 10. This vulnerability could lead to escalated privileges and potential unauthorized access. Subsequent patches were released for other critical vulnerabilities in June. These vulnerabilities could have further allowed the MOVEit platform to be exploited.
For further explanation of the matter check out the blog post about MOVEit.
Who Exactly is Cl0p and What Was Their Role in the Breach?
Cl0p is a ransomware variant that has been active in cyberattacks since 2019. The data stolen in their attacks is often published on a dark web site they refer to as “CL0P^_- LEAKS.” This ransomware and its associated website have ties to FIN11, a financially-driven cybercrime operation linked to both Russia and Ukraine. Cl0p has shifted its strategy over time, now focusing on quickly extracting data and threatening its release to extort payment.
 Figure 4. Cl0p Ransomware
Figure 4. Cl0p Ransomware
Instead of directly reaching out to the organizations it had compromised to demand a ransom, the Cl0p ransomware group took an unorthodox approach by instructing the victims to initiate contact with them.
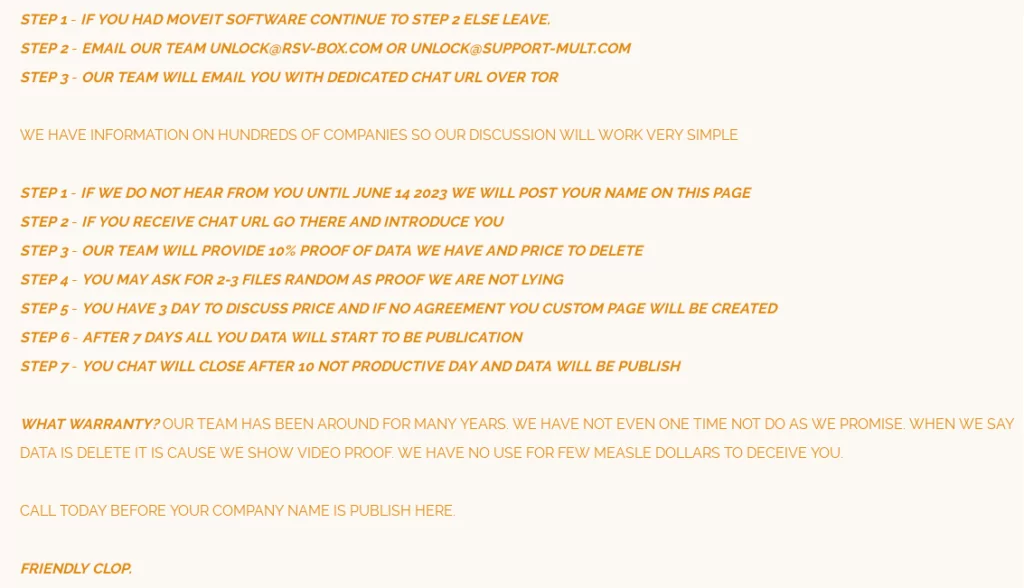 Figure 5. Cl0p’s contact instructions.
Figure 5. Cl0p’s contact instructions.
What Other Platforms Have Cl0p Targeted in the Past?
Cl0p’s malicious activities are not limited to MOVEit. They have previously launched attacks on various file transfer platforms, including:
- Accellion File Transfer Appliances (FTA) in 2020/2021.
- SolarWinds Serv-U in 2021.
- Fortra/Linoma GoAnywhere MFT servers in 2023.
This history underscores the group’s focus on exploiting vulnerabilities in file transfer systems to further their malicious objectives.
 Figure 6. Cl0p’s Leak Website
Figure 6. Cl0p’s Leak Website
How Can Organizations Prevent Similar Breaches in the Future?
The MOVEit incident underscores the challenges organizations face in safeguarding their data. It is not just their own security they need to be concerned about but also the security of their supply chains. Attacks leveraging zero-day vulnerabilities, like this one, are particularly challenging to defend against. To prevent such incidents, “Secure by Design” and “Secure by Default” initiatives could play a pivotal role. The onus is on improving software security, as organizations cannot be solely responsible for defending against attacks targeting vulnerable software.
In this context, an assistant can also be SOCRadar. By using SOCRadar Vulnerability Intelligence, you can receive alarms about vulnerabilities affecting your assets, conduct research, and even be aware of vulnerabilities in an organization that is in your Supply Chain. In this way, organizations may obtain intelligence about their vulnerabilities and have a chance to intervene beforehand. You can even receive alerts about indirect breaches through the supply chain, even if your weakness does not directly cause it. This proactive approach will strengthen your security posture and enable you to achieve full coverage.
Conclusion
The MOVEit breach, with its profound impact and vast repercussions, stands as a cautionary tale for organizations and entities across the globe. While the breach’s facts and figures are staggering, they offer invaluable lessons about the cybersecurity landscape’s evolving threats and the need for more robust defenses. With malicious actors like Cl0p continually innovating their methods and searching for vulnerable platforms, the onus rests on organizations to reinforce their digital fortresses.
The post Top 10 Facts About MOVEit Breach appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: Top 10 Facts About MOVEit Breach
