A compromise (CVE-2025-30066) was discovered in the popular GitHub Action tj-actions/changed-files on March 14, 2025. It impacted tens of thousands of repositories that use this action to track file changes. This blog will explain how Falco Actions can easily be integrated into your workflows to help detect this CI/CD attack and provide in-depth visibility.
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
Falco Actions is an open-source project that monitors your CI/CD workflows for potential threats in real time, leveraging the OSS tool Falco. It can detect suspicious activities such as unauthorized network connections, secret access, and source code modifications.
Detecting the tj-actions/changed-file payload
The payload was introduced in the repository through a compromised GitHub Personal Access Token, as reported here. Having gained access to the repository, the attacker used an off-the-shelf payload (memdump.py) to steal the secrets contained in the memory of the Runner.Worker process. It does so by leveraging the proc filesystem to:
- Identify the PID of Runner.Worker, which is the process of the application that runs a job from a GitHub Actions workflow. This process is relevant because any secret the workflow needs is passed to it.
- Check
/proc/{pid}/mapsto understand which virtual memory addresses have read permissions. - Open
/proc/{pid}/memand iterate through each readable memory region of each readable memory region. Then the script uses regex to dump the content to standard output. The output is later piped to a grep command to look for specific secrets, such as theGITHUB_TOKENor any other user-defined secret.
These operations leave a lot of space to write meaningful detection rules. The falco-actions project was created to address threats like this, so it already contains a rule to detect access to the memory of another process using /proc/{pid}/mem.
- rule: Process Dumping Memory of Others
desc: >
Detect a process dumping memory of other processes. Sensitive information can be stored in memory, and this could be a step prior to exfiltration.
condition: >
open_read and fd.name startswith "/proc/" and fd.name endswith "/mem" and not fd.name contains "/self/"
output: A process %proc.name with pid %proc.pid is dumping memory of other processes (file=%fd.name process=%proc.name proc_exepath=%proc.exepath gparent=%proc.aname[2] ggparent=%proc.aname[3] gggparent=%proc.aname[4] command=%proc.cmdline terminal=%proc.tty container_image=%container.image.repository)
priority: WARNING
tags: [CI/CD]Falco Actions to the rescue
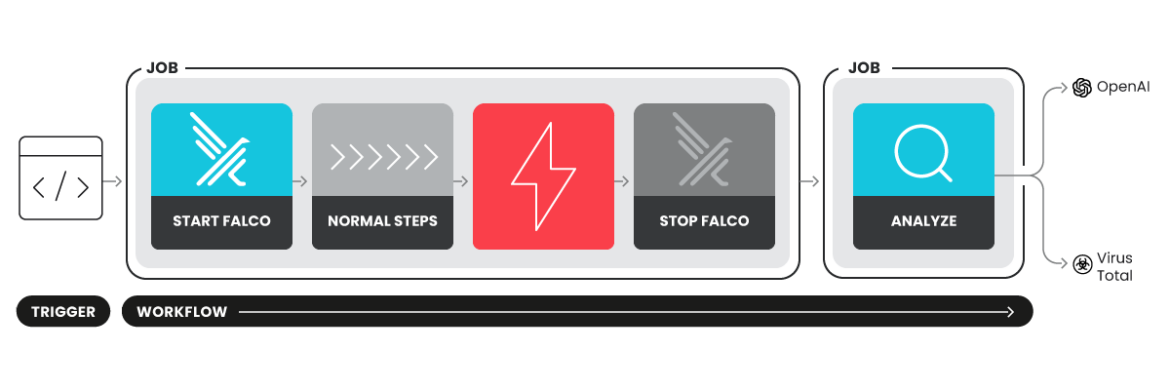
Falco Actions can be plugged into any GitHub workflow to track what happens at runtime during each workflow execution.
The action can be plugged into your workflows by simply defining start and stop actions. The example below shows how the Falco Action can be used in a workflow using the vulnerable version of tj-actions/changed-files.
- name: Start Falco
uses: falcosecurity/falco-actions/start@f67ddcc4b202aae0ab3d7194159c9c947ae77791
with:
mode: live
falco-version: '0.39.0'
verbose: true
- name: List all changed files
env:
ALL_CHANGED_FILES: ${{ steps.changed-files.outputs.all_changed_files }}
run: |
for file in ${ALL_CHANGED_FILES}; do
echo "$file was changed"
done
- name: Get changed files
id: changed-files
uses: trmlabs/changed-files@eb3c72d826fc4f9a9af40679c867cfdcf2e88012 # vulnerable version
- name: Read Sensitive File
run: |
sleep 3
docker run --rm --privileged ubuntu cat /etc/shadow
- name: Stop Falco
uses: falcosecurity/falco-actions/stop@f67ddcc4b202aae0ab3d7194159c9c947ae77791
with:
mode: live
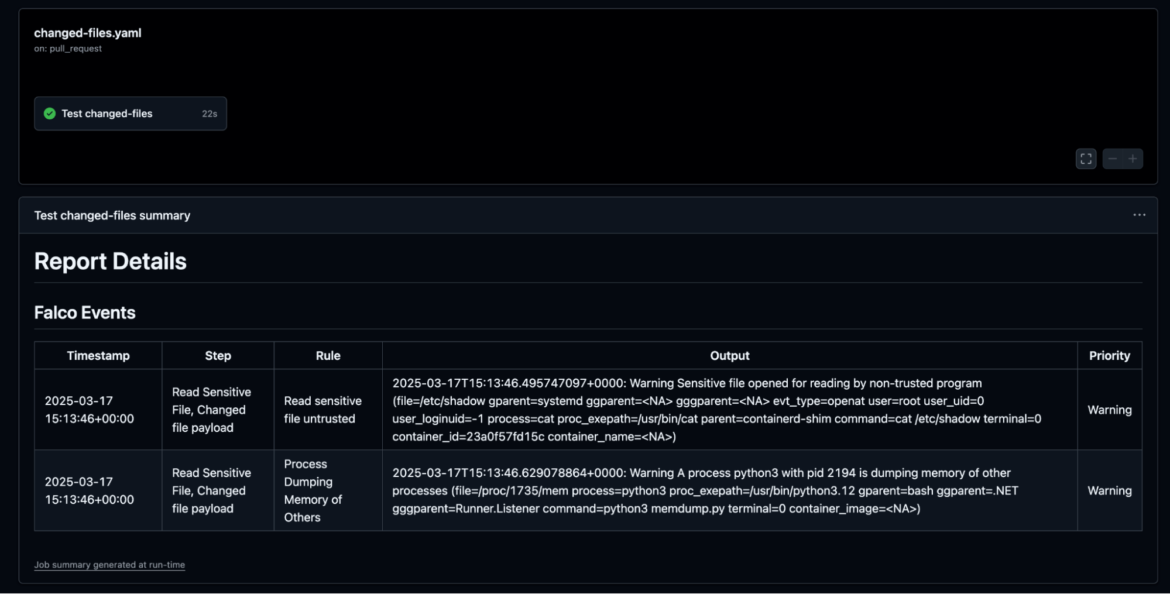
verbose: trueAt the end of the workflow run, a report is generated that includes the Falco events triggered during the run. As seen in the screenshot below, Falco detected the exploit execution, which tried to dump credentials using the memdump.py script.
The Falco Action can also identify which workflow step the rule triggered. This will simplify the investigation activities and remediation actions.
Analyze Mode
Falco Actions also support analyze mode to get even more information on what happened during the workflow run.
With the Analyze job, we can also extract information on connections that happened during the run, file changes, containers run, and more. To achieve this, a scap file is generated via a Sysdig OS container, which is started and stopped using the start and stop actions seen before. The capture file is then uploaded as an artifact and passed to a subsequent analyze job that uses the analyze action.
Falco Actions also integrate with the following external services:
- VirusTotal for IP reputations and highlighting if the run contacted a malicious IP.
- OpenAI to produce a report summarizing what happened during the run and options for remediation.
When the analysis job finishes, it produces a customizable and ready-to-use report with all the information extracted from the capture, including:
- Falco rules triggered during steps’ execution
- Contacted IPs
- Contacted DNS domains
- SHA256 hash of spawned executables
- Spawned container images
- Written files
- A summary of the report generated with OpenAI
- Reputation of contacted IPs
- Reputation of SHA256 hashes
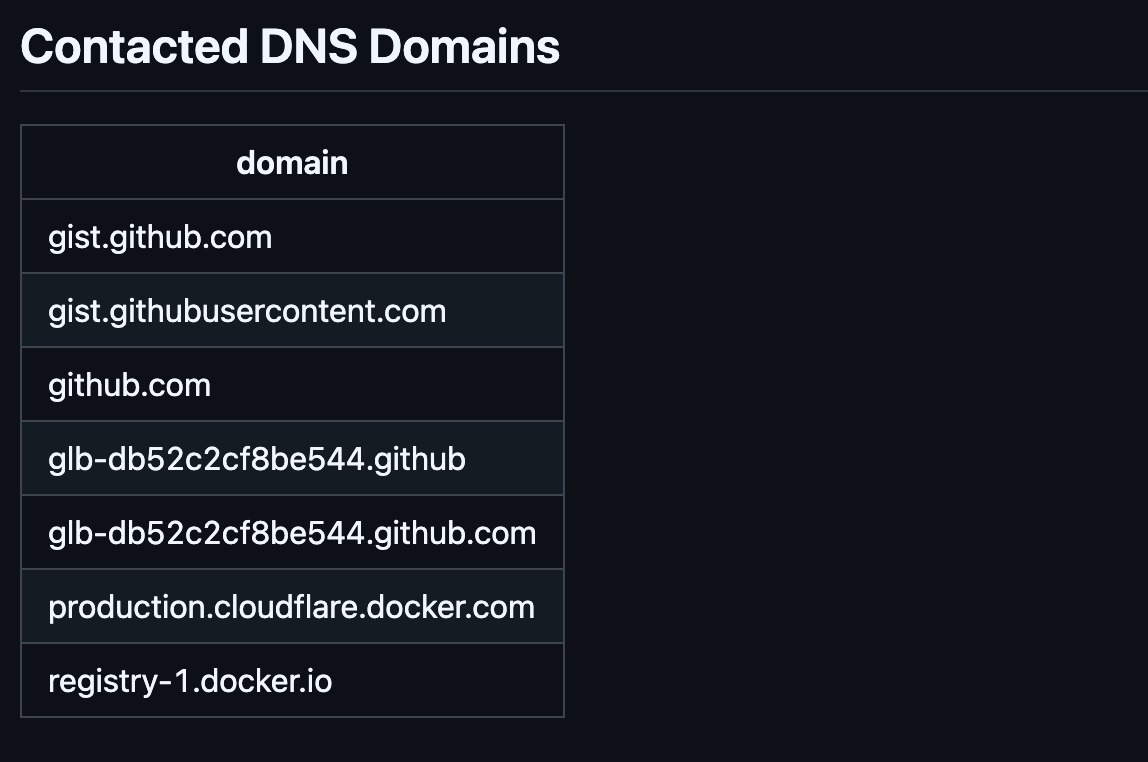
Among the information extracted, we extract domains contacted during the workflow run. In this tj-actions/changed-file use case where the malware has been downloaded and executed, we can see in the screenshot below that gist.githubusercontent.com appears in the contacted DNS connection.
Conclusion
The tj-actions/changed-files GitHub Action vulnerability is only the most recent example of the growing risk of supply chain attacks in CI/CD environments. Organizations can mitigate potential damage and safeguard their sensitive data by understanding the mechanics of the attack, using runtime security controls like Falco Actions to secure workflows, and swiftly remediating.
The post tj-actions/changed-files with Falco Actions appeared first on Sysdig.
Article Link: tj-actions/changed-files with Falco Actions | Sysdig