Today, as we do every week, Talos is giving you a glimpse into the most prevalent threats we’ve observed this week — covering the dates between July 20 and 27. As with previous roundups, this post isn’t meant to be an in-depth analysis. Instead, we will summarize the threats we’ve observed by highlighting key behavioral characteristics and indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post isn't exhaustive, and is current as of the date of publication. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
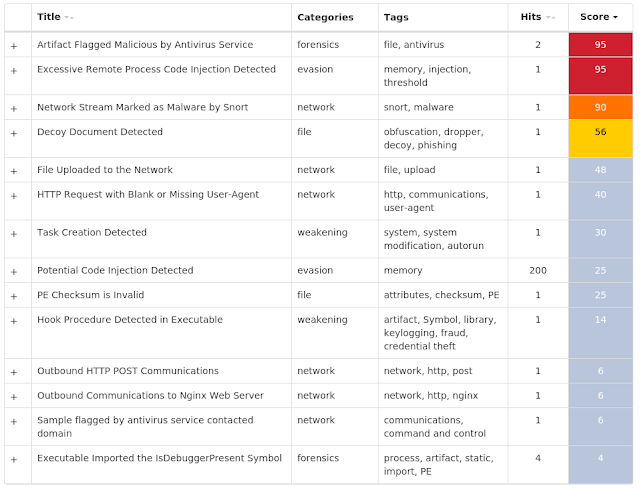
The most prevalent threats highlighted in this roundup are:
-
Win.Malware.Emotet-6622751-0
Malware
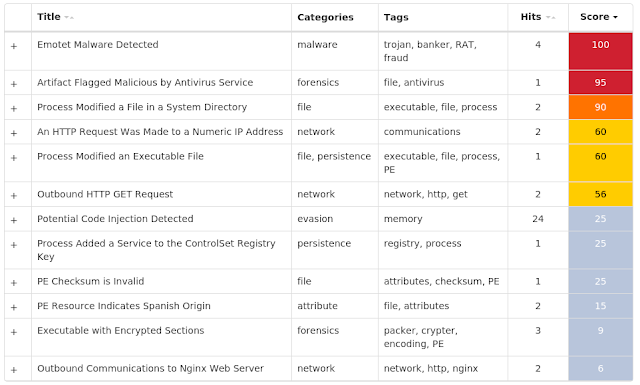
This cluster provides generic detection for the Emotet trojan downloaded onto a target machine. Emotet has been able to remain relevant because it has evolved over the years to avoid detection.
-
Win.Malware.Tinba-6622749-0
Malware
Tinba, aka Tiny Banker, is a well-known malware dedicated to stealing banking credentials from victims. It usually uses a domain-generation algorithm to connect to a command and control (C2) server and get further instructions. It injects itself into processes such as explorer.exe, ctfmon or winver. Then, it usually acts as a man-in-the-middle to collect banking information.
-
Win.Malware.Zusy-6622958-0
Malware
Zusy is a trojan that injects itself in other Windows processes and a web browser to steal valuable information. The malware also has anti-debugging and anti-VM capabilities, and it contacts a hardcoded C2 server.
-
PUA.Win.Downloader.Downloadguide-6622941-0
Downloader
This malware is a trojan downloader written in C++ that presents itself as an application installer. Downloadguide leverages techniques to hinder dynamic analysis and set up a proxy. Additional components are download and executed.
-
Win.Malware.Fareit-6622130-0
Malware
Fareit is a malware designed to steal sensitive information such as stored login information. You can read more about it on our blog: https://blog.talosintelligence.com/2015/09/down-rabbit-hole-botnet-analysis-for.html.
-
Win.Malware.Autoit-6622832-0
Malware
The initial binary contains an AutoIt script. The script is obfuscated. It creates several in-memory DLL structures with AutoIt's DllStructCreate and DllStructSetData. The script then executes the shellcode injected into these DLL structures.
Threats
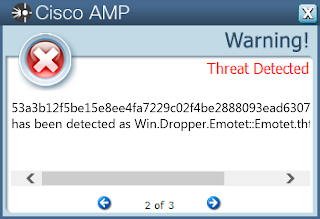
Win.Malware.Emotet-6622751-0
Indicators of Compromise
Registry Keys
- N/A
- N/A
- 67.68.235.25
- 187.192.180.144
- 190.154.42.106
- N/A
- %WinDir%\SysWOW64\267gKS2.exe
- 08f0261059671c8d2ce7744b72dafe36380fece3ccec98717a401b61cb09dd67
- 0a7d5ede4cfe02d2dd8ba3df255573d041e3d00ea68e3f1439d745f57e6e546b
- 0d37dc0cf1403e6bb4ea16426b690f3408c2b6ead2335f396898f785bca09fb1
- 1c21bbb0e989bbf1f6ab53092027d95f34b1affa1061ee02c073be3d977761de
- 2279b51d5a4a71931c1d1653afbcc504ee466c329d3175d4982093dc01e34e4d
- 2852b604c985a2b7b742c9758cff45e5475a734490af98ec2502f44a21956734
- 315d74779cf42d6ac4b598d860fa057be7c8c0d5807188553fd355ce607f47e3
- 3a6ccb939c57c7f449dbdde1dbe82e931c3683f1c41eae9909c5c6f53623e1ce
- 3f874d1b2adca571aed15ca41aafe083a21696e6079931768314a50e18934ca1
- 47d1b6bb68b5c8a8fc8abc861902a833850d001bcf69740a6f64f58199976908
- 51eff2a95e468661d25ad46e3ed576073661725e147b4c1357fea10000eeca39
- 53424273e648dd42c0939b5c861fa99f317563c4a0b952459cd3492c2a624aea
- 53a3b12f5be15e8ee4fa7229c02f4be2888093ead63077de2c45a34adbdd15a5
- 57231565cb69ca9e00e1fceec05df7ddc10594bb5aef6ccf661331a6b4227c27
- 5f90ec8324a3be0c7da857e54a613161296b3c083e8a668a44c3fd352571439e
- 65018e87d7d344da69df137669382d70ce04b097e4028b849423b5e06bc7d999
- 665119775d2b7e5155f855b13dd3e3d69f83de3fff7c24185f19ed7b79be2f1d
- 68ff0f52a62bc1d87c765fa6c25a3ea873a2e7c6d26e7f4694d614df0cac1d07
- 718e097a3a20f0e54c96e88e2f931de37291733299f281ff27062117c54c84ce
- 7232f0954e3a191a30d4dfd0e884f466d8ac15b427adc145f22ed04ee85d81b0
- 741754b54547cfc847cec859376c77160686853e4fd87ab428f3565359d22784
- 7be4f453ddc25c7cf6a40bc86886137647f039be4185e149696ecdf854a7e614
- 7d179994e7a227bd13733265cd4f3c043903c7c987b89dd5a26edbc71fc891fd
- 7d8796eeab377e45dabfaa365f79af5c86818b8e38c643a97974728b84eb5f8b
- 890906404fa629983743652be42645d2ee61dfc2f9dad8935cbbff03087567bd
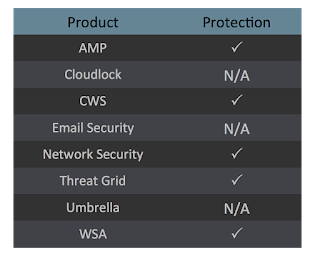
Coverage
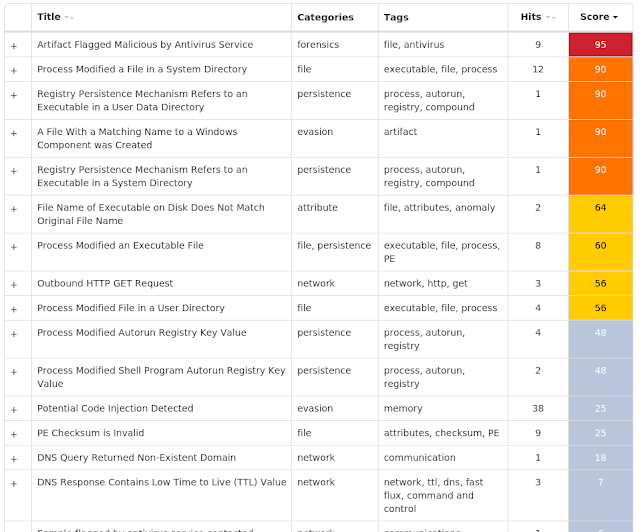
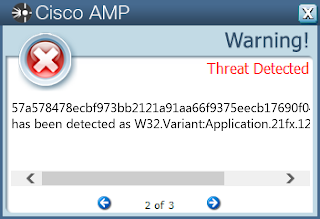
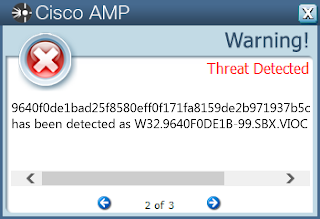
Screenshots of Detection
AMPThreatGrid
Win.Malware.Tinba-6622749-0
Indicators of Compromise
Registry Keys
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Run
- F5DBF765
- F5DBF765
- 216.218.185.162
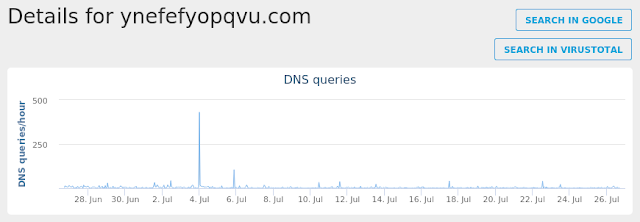
- ynefefyopqvu.com
- %LocalAppData%Low\F5DBF765
- %AppData%\F5DBF765
- %AppData%\F5DBF765\bin.exe
- %AppData%\F5DBF765\bin.exe
- 00a5a2e2ef5a08795cdb16aaef4c7ad728e5b1a9869b25aeb88f0f6e11d63e60
- 02c3fea907d36cb1631293539a2d4187028c9468eb2249d156168b7e42c20a6c
- 02e0bb96c57a60d86c2dcce7e7426dae2087acf3dcedc87156d38a22d37f2b0f
- 033b94cf05f6f95bc4f42d429e843d9df6062c862fc465730953ec7df02afa02
- 052d59e7c7d28212d9bd7b820b34f75cd66e6556a1b1cfe5adfa47b8e6389de2
- 05d7e5f0a473cd973e41fb2f5f879059b4b7619bf426928dd6c13a127b4303b4
- 063e1824bef20580bd14e18b168f7fd467a517496fae2f5935aa0dc71e55edf2
- 0693deca032c55dcd733af7bc330c223955587a17aa6a2d185c9a498696cb597
- 07cdc73fae7b6ed105625e7eff67817f878a30ee7e00ad1ecd85dd785dd4d97c
- 09cf9fc6d7ac1d2dce60924230949fff9cc41080add8b62b6f2224982c3b9e39
- 0bdf6536625358ace9e486633b22cadf967ff1bca6347d28af5fd43dca721228
- 0be0389fbb962fe5dcc2bb380830cd9b0da0ca1dea6570f51cfde5168b0df349
- 0bff836a0a08f0704e1604b7578efa930cb7e6074f5b03cadf9a423d40907fc8
- 0c507186da9fb8c3d79274f76c2cb58e585855ec541db5f4be740a292ff3c85f
- 0dfb17781828f71873bf11277d3f813a47e6408ce1c36f6a5e1e25f359cf5965
- 10b99c7f4f0d43fc9bcd97d842396afecc4d7ecd5569ffa2e5f1b8b4e4a3f4a1
- 11eb227dc0783ca787ab12f1cb2f75bde39fd0ced8c7c6174f39e6a579208ad2
- 12176eaed8e2f480a9ea16b6753ef9d7df7097787e837a940c01df7c586d5907
- 1503a43aaedaac8b7024a01e8213ddfac39ab02011f1052e0a6b14327670f11e
- 186a21eff7c970bcd1230225565d4906d354b65ddd9b79f5e7c6239b40600e16
- 18daccd80418eacab7ec33bc08a1b57d5dc91c98931a8046852be4bfad44956a
- 1a026c7e2de968f31cf6626b125a6220c80531692a0d6a6387b04a5f2af77a53
- 1cbf8e44c2096e24951445632090497be01ce2c8169bd11d48d0266279dbaf15
- 1ea06f5162de7055d581c03af3877a009394fc793d36fa2895ee4e614b68205d
- 1fb94c74154fcf4c9eabde27e01fd5718833a7e32fbac96839f6b6dbd94dbc8e
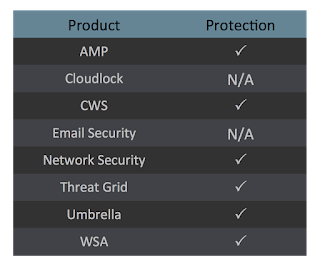
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Win.Malware.Zusy-6622958-0
Indicators of Compromise
Registry Keys
- N/A
- N/A
- N/A
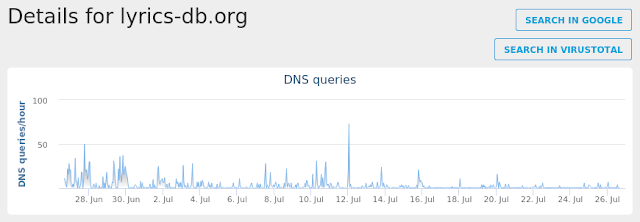
- lyrics-db.org
- %LocalAppData%\Temp\~NwcTemp
- %AppData%\MICROS~1\mstsc.exe
- %AppData%\MICROS~1\smss.exe
- %AppData%\mqtgsvc.exe
- %WinDir%\RCX190A.tmp
- %System16%\RCX1DA0.tmp
- %System16%\wininit.exe
- %WinDir%\winlogon.exe
- 33bc057301d62c8c717c735da5de219f7ed0ddb3730232a377d4d471ded6770f
- 36e59586a1befb28a44ddceaed8b60b849680ae54c0623254fa6edc4298a062f
- 386c738af602aae637c612ecdb7df491588d8b69d6ebbb97ded359f13e35919b
- 573a8bed6140ff1206b37e9f18113ed33de17a143da67014192e7cdfc2276d9d
- 658a26c8e110f33a1062b9392187c42e1654ea10479c716e92639ea322552b2c
- 7a3e884b95e2ac172ee2e12452f400c73e894213b2f600d9941ca13cc75f9945
- 971e4fa0ad4ecd6218f9105616ab0ae6fcfb9e71d829be6c977a83570b535be8
- 9c90a36e7e93cd38e09f373a48c626f2415bec009eaeb080bd9bca7573ea3518
- b171b8152d85e074b27dba98a7af2fa6fbed2a0dad389ee117cf9dc163b9d3c6
- cd9b6c1820b5cf352806abdec78b7ba13fed27033e7c4ab3aadac4cf700f6f7d
- e9d6a93a090c2ec2c5f80bb03dce130d28cdaca2cb3dde5051c44ef47dd78f3a
- f3a350151059a6b1fa123c6c0911d816602c85566f254e960d17a8dc63ee8f4d
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
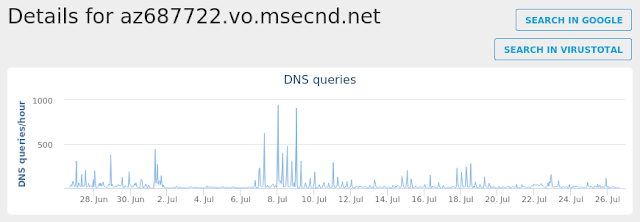
PUA.Win.Downloader.Downloadguide-6622941-0
Indicators of Compromise
Registry Keys
- <HKCR>\LOCAL SETTINGS\MUICACHE\3E\52C64B7E
- Value Name: LanguageList
- N/A
- 104.45.146.238
- 72.21.81.200
- 104.40.156.71
- dlg-messages.buzzrin.de
- dlg-configs.buzzrin.de
- az687722.vo.msecnd.net
- %LocalAppData%\Temp\DLG\requirements
- %LocalAppData%\Temp\DLG\ui\common\last\css
- %LocalAppData%\Temp\DLG\ui\common\last\img
- %LocalAppData%\Temp\DLG\ui\common\last\img\img1.png
- %LocalAppData%\Temp\DLG\ui\common\last\index.html
- %LocalAppData%\Temp\DLG\ui\common\last\js\jquery-1.10.2.min.js
- %LocalAppData%\Temp\DLG\ui\common\last\last.zip.part
- %LocalAppData%\Temp\DLG\ui\common\progress
- %LocalAppData%\Temp\DLG\ui\common\progress\img
- %LocalAppData%\Temp\DLG\ui\common\progress\img\bar-rb.png
- %LocalAppData%\Temp\DLG\ui\common\progress\img\br-b.png
- %LocalAppData%\Temp\DLG\ui\common\progress\img\br-rb.png
- %LocalAppData%\Temp\DLG\ui\common\progress\img\icon.png
- %LocalAppData%\Temp\DLG\ui\common\progress\img\img1.png
- %LocalAppData%\Temp\DLG\ui\common\progress\progress.zip.part
- %LocalAppData%\Temp\DLG\ui\offers
- %LocalAppData%\Temp\DLG\ui\offers\7fe97ec50ca64604e0220718c8f8697a\img
- %LocalAppData%\Temp\DLG\ui\offers\7fe97ec50ca64604e0220718c8f8697a\img\img1.png
- %LocalAppData%\Temp\DLG\ui\offers\7fe97ec50ca64604e0220718c8f8697a\img\progress-bar.png
- %LocalAppData%\Temp\DLG\ui\offers\7fe97ec50ca64604e0220718c8f8697a\index.html
- %LocalAppData%\Temp\DLG\ui\offers\7fe97ec50ca64604e0220718c8f8697a\js\jquery-1.10.2.min.js
- %LocalAppData%\Temp\DLG\ui\offers\d9d3f9c93703d0824c9ab2b3c9c7f923
- %LocalAppData%\Temp\DLG\ui\offers\d9d3f9c93703d0824c9ab2b3c9c7f923\css\style.css
- %LocalAppData%\Temp\DLG\ui\offers\d9d3f9c93703d0824c9ab2b3c9c7f923\img
- %LocalAppData%\Temp\DLG\ui\offers\d9d3f9c93703d0824c9ab2b3c9c7f923\img\img1.png
- %LocalAppData%\Temp\DLG\ui\offers\d9d3f9c93703d0824c9ab2b3c9c7f923\index.html
- %LocalAppData%\Temp\DLG\ui\offers\d9d3f9c93703d0824c9ab2b3c9c7f923\js
- %LocalAppData%\Temp\DLG\ui\offers\d9d3f9c93703d0824c9ab2b3c9c7f923\js\jquery-1.10.2.min.js
- %LocalAppData%\Temp\DLG\ui\offers\d9d3f9c93703d0824c9ab2b3c9c7f923\uifile.zip
- %LocalAppData%\Temp\DLG\ui\common\last\js\jquery-1.10.2.min.js
- %LocalAppData%\Temp\DLG\ui\common\last\last.zip.part
- %LocalAppData%\Temp\DLG\ui\common\progress\css\style.css
- %LocalAppData%\Temp\DLG\ui\common\progress\img\bar-rb.png
- %LocalAppData%\Temp\DLG\ui\common\progress\img\br-b.png
- %LocalAppData%\Temp\DLG\ui\common\progress\img\br-bg.png
- 01254b31bae6080f2c8174aab93cceb34f73371c812b15d8a81d65e606450b06
- 01457388b9ae551df608961fd80d5e5e3cb10984f075edb934dee4d01808b8d5
- 024cf1be349c299cceff37b541636017577c34d6611731202a040bbeba715842
- 028c26f9b89ef8dccf5bdf1f6038b2218453c80077369110a486161315eb0be1
- 02c5260e5bcb6ee08850372cfbd8e3bb079f1ba8d3a0f5eadb416acd9f311dd3
- 032156742c5cfbce4fe4a1833edde2c2cdcf705153a0d8632bebfe73436b722b
- 03a72a7638c4fa08a90162344b17d84fce7f855baed1ed29b7cdec35fb8e916b
- 041c33c6e89158e7c2235192d3bf1cc63512aa560da39ce414133f296359d8e1
- 047bdf35fdd28cdc684ddda552a47e1a40b797447236aebc2a42320cbf5f94ce
- 05983a7aa34da9e2505751b1cea98ce462e230df4d1279be07c9f036b91e15f3
- 0659ad0c66aeb677e381b89edf442c04821bffed6ec96bcd2a9f774495ccc145
- 06845c54e04d0828a68a3328320a904165687ae9f93289d79cf75769101093eb
- 076a87b35cec9825ba9b99ae890ec911582d1ddbfdd56eea37969ab5a01c91ce
- 083ec0dae285080d95ce30fca8ace09cbdbf8259d1b2787a45a077b5a868f923
- 08be2a75ed5a08f531a32b229e4a8e77e4ec44ab19136a91fea8f0e1085ddcfb
- 09c03c9c2e10c08c920b121842163c11655b4e5c4b59f056b33490ee12adb944
- 0a60a6c39e11cc7da2bb710ed63dca71b8b11c0be810351a63fb2308725974a2
- 0ab269d61e2fb0a1fb4d48f8a5acff5c96372698543e233da6bc1a0f91a0e71a
- 0b45096e8b22da648cc9f86c6c0191644de9baaad3b8869c2186717120edbe93
- 0bded347d6be964d38425d9ac84f533d5ec76720f9691c5a83da2f150e2f809b
- 0bf53bfabc494b390907d8b91eecef5630ca54631bc9d7ab7df33f1968103bf9
- 0d18e95860c43ade1616b1de9257f128f0e8c2b44a17be1279a8fd95e87e8361
- 0e167e32dd2eabb36b9450cb47f41226df2d79aa7159b1df969e1e5691e20ceb
- 0e6a9843c76fdf516443b8eabf671a9515924898bd5d21940ee8a823f8cff18f
- 109c7a6a4160095ccf491c5732750b42eaf9e0a57cdd5751977ee8717fa9be39
Coverage
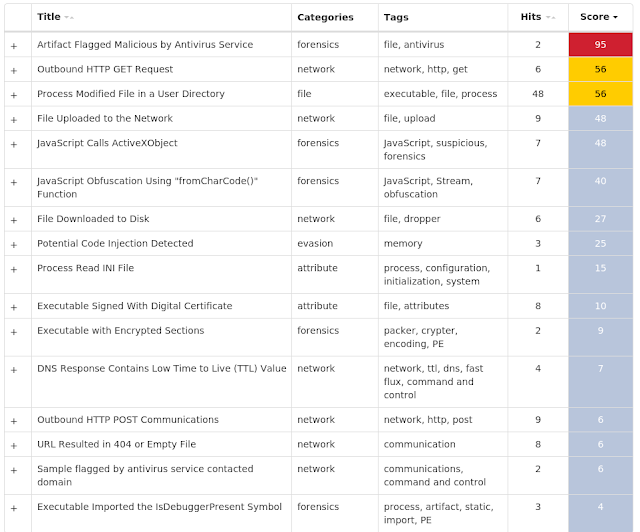
Screenshots of Detection
AMPThreatGrid
Umbrella
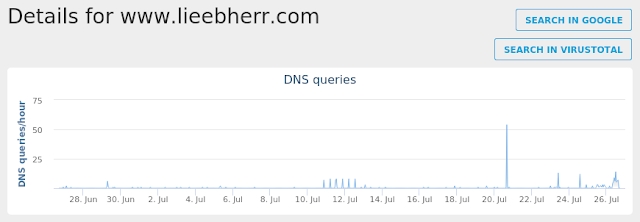
Win.Malware.Fareit-6622130-0
Indicators of Compromise
Registry Keys
- N/A
- N/A
- N/A
- www.lieebherr.com
- ssleee99.gq
- checkip.dyndns.org
- %LocalAppData%\Temp\XGY.exe
- %AppData%\The May Department Stores Company
- %AppData%\The May Department Stores Company\The May Department Stores Company.exe
- %LocalAppData%\Temp\XGY.exe
- %AppData%\The May Department Stores Company\The May Department Stores Company.exe
- 1a62d9fa23236eebfab27275fcad63e77a35c9d8e9e08e8e54ae1c453a3cd151
- 3de29be46399420eabcfd88a5c4074972a107a83aae006401d251543089b4d18
- 416e4ec779d7bdc6369b72c3519131cf3edddd5807897641bb8dd779ebb82861
- 75f2a610862b4755addcded64a8917ebdd58bef5eeb1cd7384c650ff86782435
- b3621e28c5f4c4d30eb2cbd4bff9fe9a0c42005610ec18392dce8f60227a24c8
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Win.Malware.Autoit-6622832-0
Indicators of Compromise
Registry Keys
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TREE\WINMGR72
- Value Name: Id
- Z1GvCDZ7WjjivTLFlroDIYtChirzywit8riAimZvtJFVwnAGqouOmu1RD2aOhzQjKkCzfBDA
- N/A
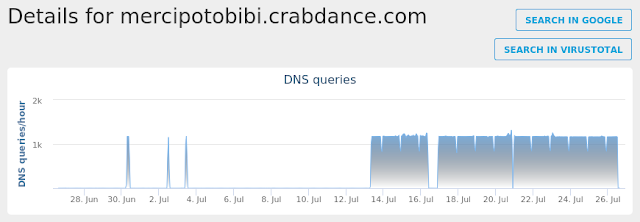
- mercipotobibi.crabdance.com
- %AllUsersProfile%\winmgr72.exe
- %System32%\Tasks\winmgr72
- \TEMP\16d13c468b4aee0cef0ed6ad496c1f784d0463a008668bb65433b5971f906bcd.exe
- 00f3401fec2374a115607ca2d5b5686574c93ebda489a045ed44dba9d967597b
- 083bc23bb6c52c796193de26b738bec11fb8737192cfea6964d6ff30adc11488
- 0ebe5e0e5ef6b37a5e7026ffa3c5cf7405b5208d73590c7c6486f686106d8660
- 0fda7143f2dba50c9d04a415208358d5521a83a2935237504bc31f64d18e5578
- 106417e1fab3a9dbae898aaef07d230e0b401e12e4f4871afef1d224fdb25e43
- 12d98356631b5bfee4e6f830fea039344dcc152e5c0df790db1be96359082ed6
- 13035cc21c31465cd585f4cd724d529179578694738cc4f4e6c67284aac595c4
- 13a16250e80410751d384599db1fec9a5652bc4d618c63d05c936ba73b09f9c4
- 14df6a49a8300f25a9248bc7b9e9fa9741219f97f9de38efc6fb3175184c6dff
- 15245e08d5840225b231a0274122f468f1282fdf4711c028448afcdc4fb491df
- 16236f9899441a6ba6a5d717c946d32ff92d91374d1495637df09564e31e28e5
- 167e5ded14ddd124ca9fa5ab7320cdd938127353729fe13566028a41a28d61bd
- 16d13c468b4aee0cef0ed6ad496c1f784d0463a008668bb65433b5971f906bcd
- 1f6d039036579f5f6c882e83a5955f121b2f029d13eb024d1804e3d60bae70b1
- 206c768f9bc537a301c60386f5c0691986dfda13415d72d1764f4698b7fcdcd0
- 222be8b44373f6742bec3f40a1d54346948c1785bb58e753046e6f8117b2b73f
- 2236b9e9d0de66212e5992c09f95d8b5087242a83e6508147075d6018145af9d
- 236ed18e2291c2ba7e81e27a5cb1760b29fd7e660c10c581010563c0dd38e4a7
- 25ae823e0d090494370968f8d8a6ccd7009ba020bdadd621568ed42942d87d62
- 2682e453c3eacf478a027077d9adad6216152c87e33800c086e0c1a9e7d209d1
- 2cde45358f868a7aa9ec5509ea99b77c8f19ec113105adebd8dfbc95adb688ca
- 2e8bfa92d09fa3c6ce6131debfc15f7c12532911dabf9517f68d9f10f23f444e
- 2ea6a3e9f57626e2f2390dc8e77ca92e610e35cd2ab669b3c4b0ff3042e2f4d8
- 31c67214842b961675ab240ec05bea05e9d2599030c151c261aaa99cf9e6c23c
- 33649d53e676469ce642e3bfd5e0c4fb6c8e0a5c3791459de8dc9f3d3982b84d
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Article Link: http://feedproxy.google.com/~r/feedburner/Talos/~3/SJ7gZUk_gyk/threat-roundup-0720-0727.html