The digital world is an ever-evolving landscape, and with it comes the evolution of cyber threats. One such emerging threat is the Rhysida Ransomware Group, a new player in the cybercrime arena that has been making waves since its first sighting in May 2023. This group, which positions itself as a “cybersecurity team,” has been targeting systems and highlighting potential security issues, all while threatening victims with public distribution of exfiltrated data. This blog post aims to shed light on the Rhysida Ransomware Group, their attack methods, tools, targets, and how organizations can protect themselves against such threats.
Who is Rhysida?
 Fig.1. Rhysida threat actor card
Fig.1. Rhysida threat actor card
Rhysida is a Ransomware-as-a-Service (RaaS) group that emerged at the end of May 2023. Despite being a newcomer, the group has quickly established itself as a significant ransomware operation. Their first high-profile attack was against the Chilean Army, marking a trend of ransomware groups targeting Latin American government institutions.
On June 15, 2023, the group leaked files stolen from the Chilean Army, which turned the group’s claim as true.
 Fig. 2. Threat Actor/Malware Page of Rhysida Ransomware (Source: SOCRadar)
Fig. 2. Threat Actor/Malware Page of Rhysida Ransomware (Source: SOCRadar)
The group positions themselves as a “cybersecurity team” who are doing their victims a favor by targeting their systems and highlighting the supposed potential ramifications of the involved security issues.
How does Rhysida Attack?
Rhysida is deployed in multiple ways. Primary methods include deployment via Cobalt Strike – a penetration testing tool often misused by threat actors for its advanced exploitation and post-exploitation capabilities – or phishing campaigns. This suggests that Rhysida’s targets could potentially span a wide range of sectors and industries, as these attack methods are not specific to any particular type of organization.
Rhysida ransom notes are written as PDF documents to affected folders on targeted drives. This could potentially provide some insight into the types of systems or networks that Rhysida targets, as the presence of these ransom notes could indicate that the targeted systems have the capability to handle PDF documents. This indicates that the group is not targeting command-line operating systems used on network devices or servers.
The group threatens victims with public distribution of the exfiltrated data, bringing them in line with modern-day multi-extortion groups. Rysida can be appended to the list of the groups that follow the double-extortion strategy.
Rhysida’s ransomware is a 64-bit Portable Executable (PE) Windows cryptographic ransomware application compiled using MINGW/GCC. A sample analyzed by researchers suggests the tool is in the early stages of development because of the application’s program name is set to Rhysida-0.1.
When Rhysida runs, we observed a process of getting output from the command line, which apparently scans the files, runs the “file_to_crypt” function, and if successful, changes the file extension to “.rhysida”:
![Fig. 3. Script outputs that appear on cmd[.]exe when Rhysida runs](https://socradar.io/wp-content/uploads/2023/08/rhysida-cmd-output.png) Fig. 3. Script outputs that appear on cmd[.]exe when Rhysida runs
Fig. 3. Script outputs that appear on cmd[.]exe when Rhysida runs
For the encryption phase, Rhysida uses a 4096-bit RSA key with the ChaCha20 algorithm.
 Fig. 4. Some files in our test environment have changed to “.rhysida” extension
Fig. 4. Some files in our test environment have changed to “.rhysida” extension
Rhysida generates the ransom note as a PDF document, as mentioned above. The content of the document is embedded in the binary in clear text.
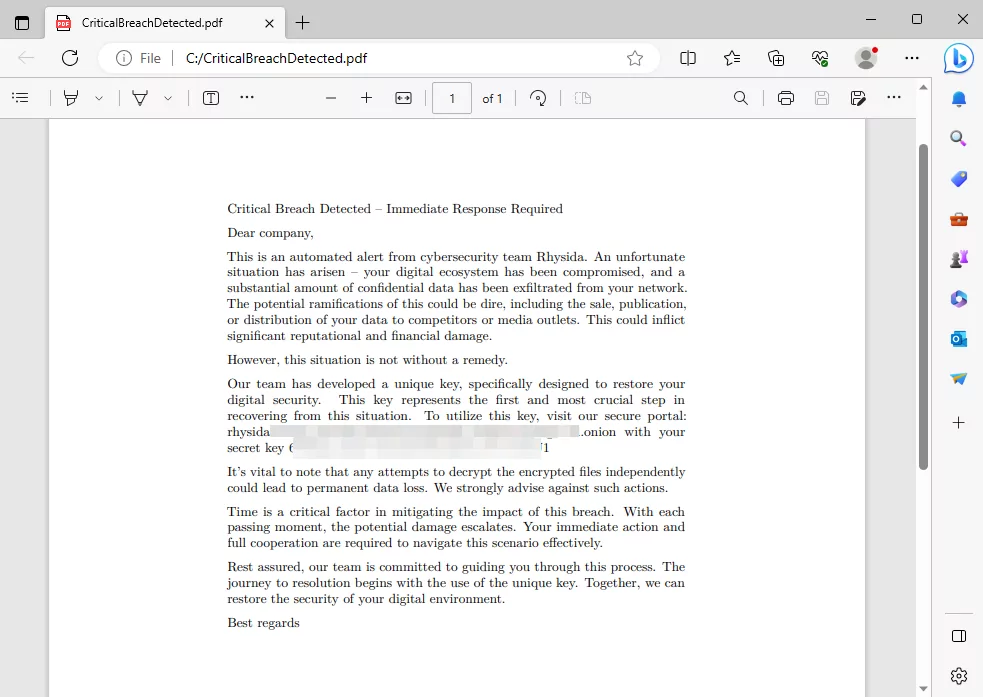 Fig. 5. Rhysida Ransomware’s ransom note ‘CriticalBreachDetected.pdf’
Fig. 5. Rhysida Ransomware’s ransom note ‘CriticalBreachDetected.pdf’
A quick look at Rhysida Ransomware’s TOR page
When the TOR page of the group is opened, their own logo Rhysida Centipede and the current auctions and total number of victims can be seen.
 Fig. 6. Heading section of Rhysida Ransomware’s TOR page
Fig. 6. Heading section of Rhysida Ransomware’s TOR page
When we scroll down to the middle of the homepage, we see an area where the token in the ransom note can be entered for victims to communicate with Rhysida, also on the left side of the page shows new victims and data shares on the right side where they have started the data leak phase.
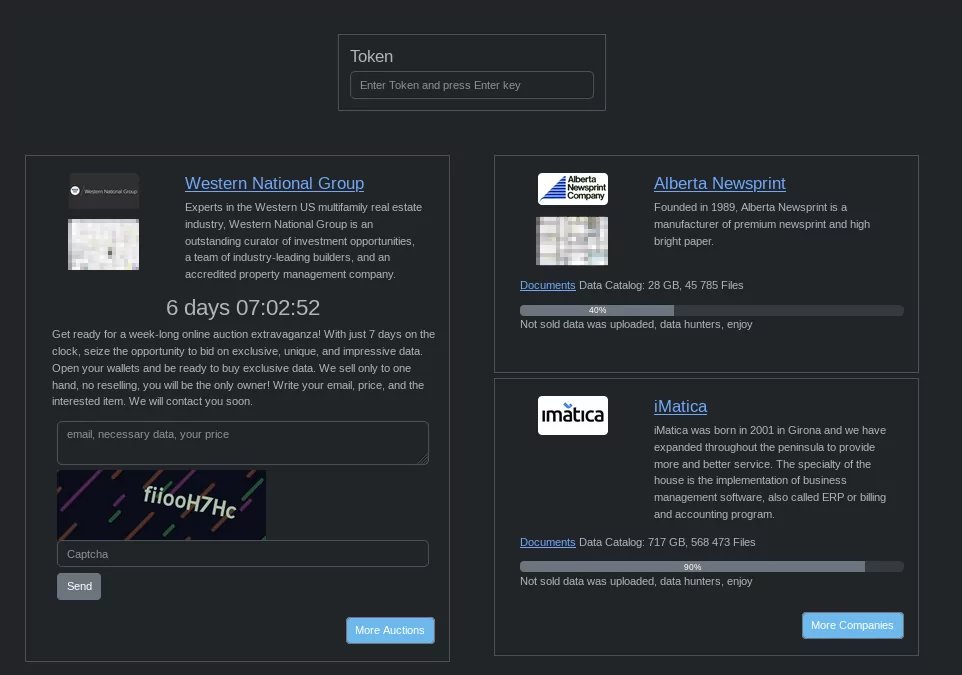 Fig. 7. The token field and the current listings of Rhysida
Fig. 7. The token field and the current listings of Rhysida
Once the token is entered, a contact form specially designed for victims appears:
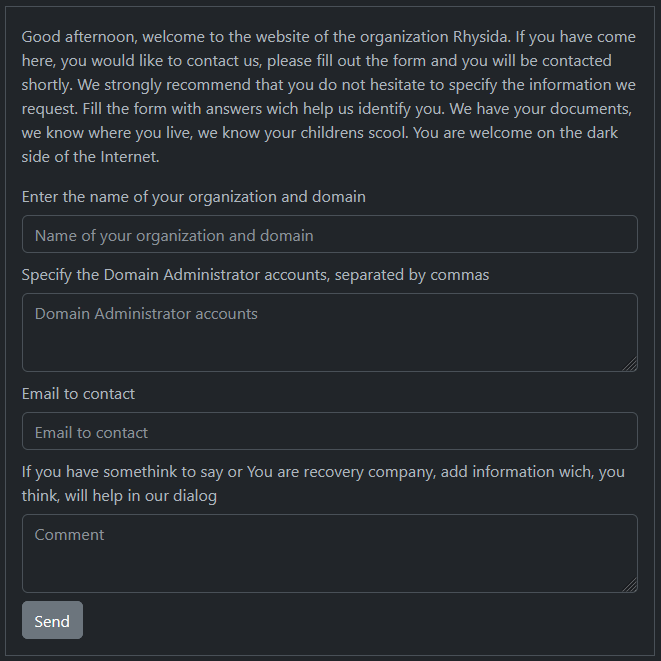 Fig. 8. Custom Contact form designed for victims of Rhysida (Source: Secplicity)
Fig. 8. Custom Contact form designed for victims of Rhysida (Source: Secplicity)
The footer of the group’s TOR page has 3 sections:
- News: The section where they add news posts that appear under the group’s own name
- Contact Us Form: The section where Journalist, Recoveries and fans who want to get in touch can leave their contact details
- How you can buy BTC: The section where the Bitcoin’s dollar equivalent can be seen and various sites where Bitcoin can be purchased are shared
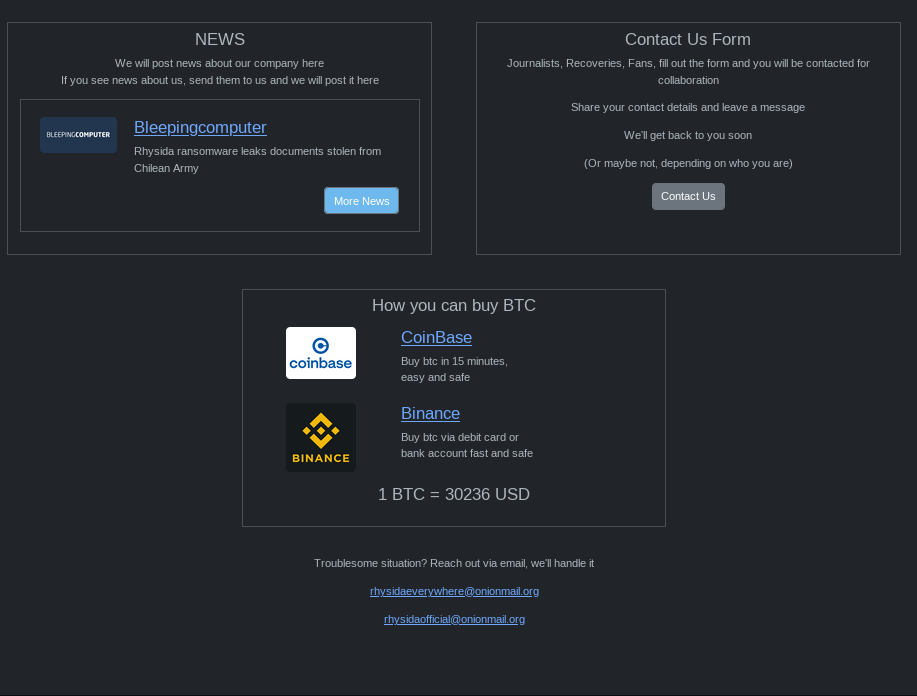 Fig. 9. TOR page footer
Fig. 9. TOR page footer
When we click on the Auctions button in the header section of the page, there are victim announcements where data leaks have not yet been initiated by the group.
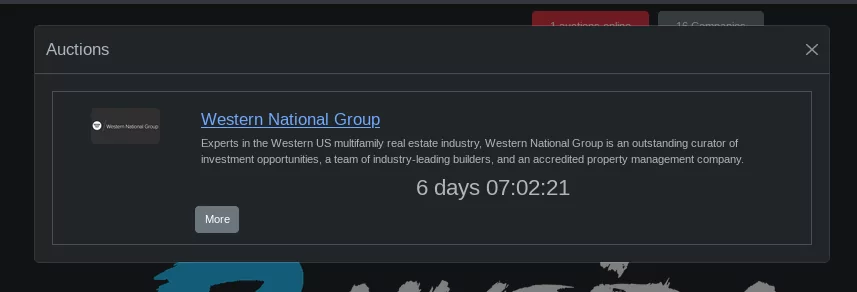 Fig.10. A victim announcement by Rhysida
Fig.10. A victim announcement by Rhysida
When the Companies button in the header section of the page is clicked, there is a list of victims whose data leak process has started or completed, and URLs belonging to the each leaked data.
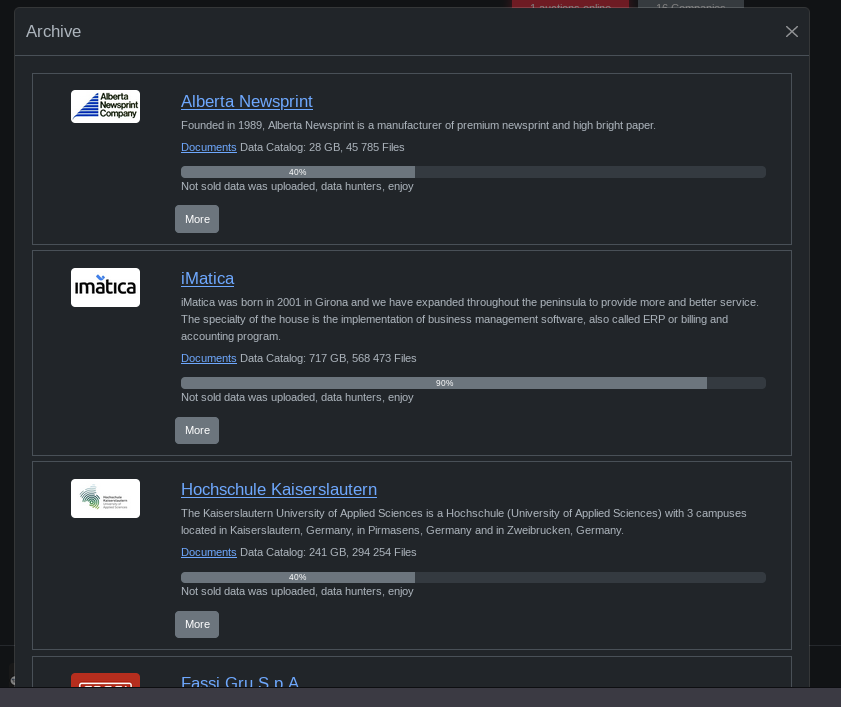 Fig. 11. The victims whose data have been leaked
Fig. 11. The victims whose data have been leaked
What are the targets of Rhysida?
Target Sectors:
When observing the group’s attacks, it can be inferred that it mostly targets the organizations operating in the Education and Manufacturing fields.
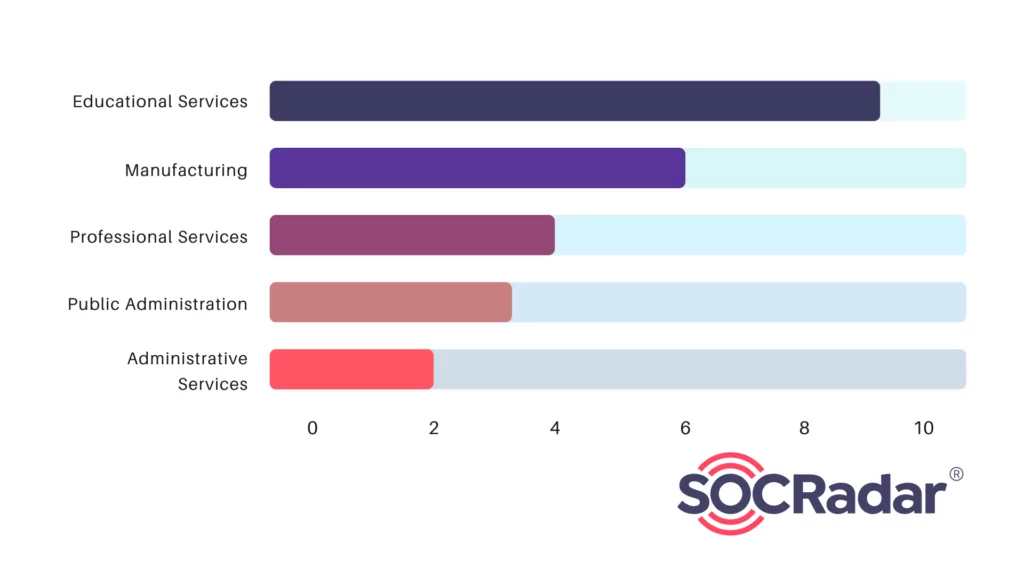 Fig. 12. Distribution of affected sectors by Rhysida Ransomware (Source: SOCRadar)
Fig. 12. Distribution of affected sectors by Rhysida Ransomware (Source: SOCRadar)
Target Countries:
Looking at the countries where the organizations affected by Rhysida Ransomware are located, it can be inferred that it is mostly active in North America, Europe and Australia.
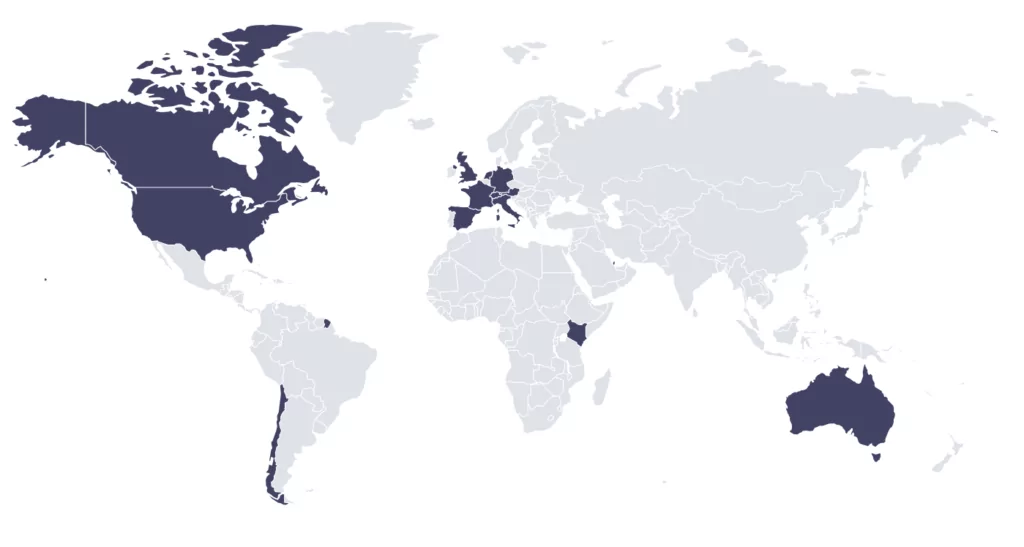 Fig.13. Countries affected by Rhysida Ransomware (Source: SOCRadar)
Fig.13. Countries affected by Rhysida Ransomware (Source: SOCRadar)
When the country distributions are analyzed, we conclude that the United States, Italy, Spain and the United Kingdom are targeted more than other countries, respectively.
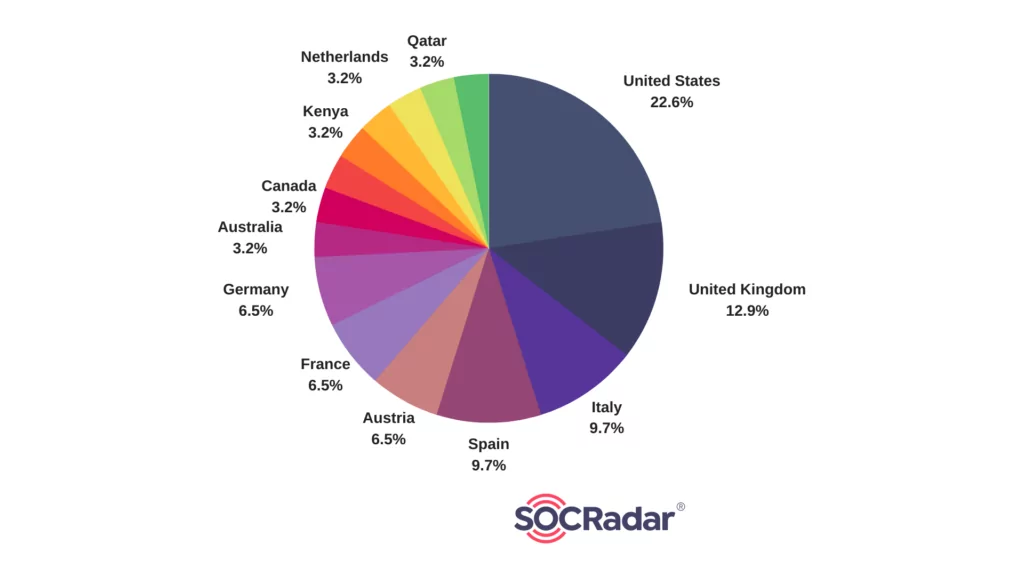 Fig. 14. Distribution of affected countries by Rhysida Ransomware (Source: SOCRadar)
Fig. 14. Distribution of affected countries by Rhysida Ransomware (Source: SOCRadar)
What are the latest activities of Rhysida Ransomware?
The group’s recent attacks show that the education sector has been targeted most recently.
One of the recent victim of Rhysida is the University of West Scotland:
 Fig. 15. University of West Scotland has been announced as a victim.
Fig. 15. University of West Scotland has been announced as a victim.
 Fig. 16. Dark web news page of SOCRadar Platform’s CTI Panel (Source: SOCRadar)
Fig. 16. Dark web news page of SOCRadar Platform’s CTI Panel (Source: SOCRadar)
Rhysida’s Relation with Vice Society
Recently, security researchers have alleged that there is a relationship between Rhysida and Vice Society. In terms of commonalities, both groups mainly target the education sector. 38.4% of Vice Society’s attacks targeted the education sector, compared to 30% of Rhysida’s.
Conclusion
Rhysida Ransomware Group has emerged as a significant threat in the cyber landscape. With its strong encryption techniques and double extortion tactics, Rhysida posed a serious risk to organizations worldwide in a short time. The group’s focus on military and government institutions, as evidenced by their attack on the Chilean Army, further underscores the potential severity of their activities.
By understanding the group’s tactics, techniques, and procedures (TTPs), organizations can take proactive measures to protect their systems and data. This includes patching known vulnerabilities, implementing robust security measures, and training staff to recognize and avoid phishing attempts.
Security Recommendations against Rhysida
Given the severity of Rhysida’s attacks, it’s crucial for organizations to take proactive measures to protect their systems and data. Here are some security recommendations to defend against Rhysida Ransomware:
Virtual Patching: Rhysida is known to exploit known vulnerabilities in software to gain access to systems. Virtual patching can help by providing an immediate layer of protection against known vulnerabilities that the ransomware might exploit. This is especially important when a vendor-supplied patch is not immediately available or cannot be applied right away due to testing requirements.
Phishing Awareness Training: Since Rhysida often uses phishing campaigns to deliver its ransomware, it’s important to provide regular phishing awareness training to all employees. This can help them recognize and avoid phishing attempts.
Use of Endpoint Security Solutions: Endpoint security tools can help fight against ransomware by continuously checking all points of entry in a network, spotting and stopping malicious software, reviewing all incoming data, and giving the option to separate or delete data from afar, which helps prevent the spread of ransomware throughout the network.
Immutable Backups: Utilizing the inherent stability of immutable backups, which are distinguished by their resistance to modification and deletion, organizations can construct a robust protective barrier against potential ransomware incursions. These backups guarantee that, despite the presence of such cyber risks, the restoration of data remains a feasible and efficient approach, thereby negating the necessity to comply with ransom requisitions
Network Segmentation: By segmenting your network, you can limit the spread of ransomware if one part of your network is compromised.
Use of Firewalls and Intrusion Detection Systems: Firewalls and intrusion detection systems can help detect and block suspicious activity, potentially stopping an attack before it can do significant damage.
Incident Response Plan: Having a well-defined incident response plan can help your organization respond quickly and effectively to a ransomware attack, minimizing downtime and damage.
Least Privilege Principle: Limit the access rights of users and applications as much as possible. This can help prevent ransomware from gaining the access it needs to encrypt files or spread throughout your network.
MITRE ATT&CK TTPs of Rhysida Ransomware
|
Technique |
ID |
|
Reconnaissance |
|
|
Active Scanning |
T1595 |
|
Phishing for Information |
T1598 |
|
Resource Development |
|
|
Acquire Infrastructure |
T1583 |
|
Develop Capabilities |
T1587 |
|
Initial Access |
|
|
Phishing |
T1566 |
|
Abuse Elevation Control Mechanism: Bypass User Account Control |
T1548.002 |
|
Execution |
|
|
Command and Scripting Interpreter |
T1059 |
|
Shared Modules |
T1129 |
|
Persistence |
|
|
Registry Run Keys / Startup Folder |
T1547.001 |
|
Privilege Escalation |
|
|
Process Injection |
T1055 |
|
Thread Execution Hijacking |
T1055.003 |
|
Registry Run Keys / Startup Folder |
T1547.001 |
|
Defense Evasion |
|
|
Obfuscated Files or Information |
T1027 |
|
Indicator Removal from Tools |
T1027.005 |
|
Masquerading |
T1036 |
|
Process Injection |
T1055 |
|
Thread Execution Hijacking |
T1055.003 |
|
Virtualization/Sandbox Evasion |
T1497 |
|
Hide Artifacts |
T1564 |
|
NTFS File Attributes |
T1564.004 |
|
Reflective Code Loading |
T1620 |
|
Discovery |
|
|
Application Window Discovery |
T1010 |
|
Process Discovery |
T1057 |
|
System Information Discovery |
T1082 |
|
File and Directory Discovery |
T1083 |
|
Virtualization/Sandbox Evasion |
T1497 |
|
Security Software Discovery |
T1518.001 |
|
Collection |
|
|
Data from Local System |
T1005 |
|
Automated Collection |
T1119 |
|
Command and Control |
|
|
Application Layer Protocol |
T1071 |
|
Web Protocols |
T1071.001 |
|
Exfiltration |
|
|
Exfiltration Over C2 Channel |
T1041 |
|
Impact |
|
|
Data Encrypted for Impact |
T1486 |
Appendix
IoCs of Rhysida Ransomware:
|
IOC Type |
IOC |
|
URL |
https://ipapi.com/json/ |
|
Hash (SHA-256) |
a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6 |
|
Hash (SHA-256) |
6903b00a15eff9b494947896f222bd5b093a63aa1f340815823645fd57bd61de |
|
Hash (SHA-1) |
7abc07e7f56fc27130f84d1c7935a0961bd58cb9 |
|
Hash (SHA-256) |
3bc0340007f3a9831cb35766f2eb42de81d13aeb99b3a8c07dee0bb8b000cb96 |
|
Hash (SHA-256) |
2a3942d213548573af8cb07c13547c0d52d1c3d72365276d6623b3951bd6d1b2 |
|
Hash (MD-5) |
59a9ca795b59161f767b94fc2dece71a |
|
Hash (SHA-256) |
250e81eeb4df4649ccb13e271ae3f80d44995b2f8ffca7a2c5e1c738546c2ab1 |
|
Hash (SHA-256) |
2a3942d213548573af8cb07c13547c0d52d1c3d72365276d6623b3951bd6d1b2 |
For more IoCs, you can visit the Threat Actor/Malware page under the CTI module of SOCRadar XTI Platform.
The post Threat Profile: Rhysida Ransomware appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: Threat Profile: Rhysida Ransomware
