This is a concerning time for our industry and the public at large. We are in the midst of a global health crisis. In such times, we all need to be working together and ensuring that everyone has the most accurate and reliable data. We all want assurance that we can trust the resources available to us. Anything counter to that is destructive and potentially harmful to society. However, we all know that cybercriminals and sophisticated adversaries seize opportunities like this to further their own cause. This not only leads to the usual barrage of complications inherent to any cyber attack or event, but in this case it can translate to real harm to those we love and protect.
Summary
At Sentinel Labs, we have been closely tracking adversarial behavior as it pertains to COVID-19/Coronavirus. To date, we have observed a significant number of malware campaigns, spam campaigns, and outright scams that are preying on the fears and uncertainties of the global population.
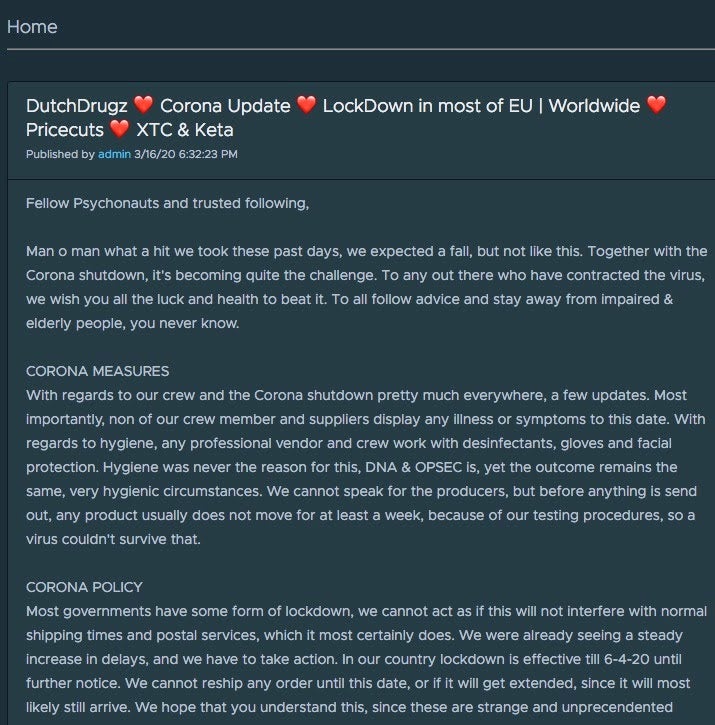
Over the last few months we have seen aggressive use of COVID-19/Coronavirus as a lure all over the spectrum of sophistication. Campaigns range from run-of-the mill scams (selling supplies for BTC via .onion sites) to non-targeted spam campaigns (primarily for credential harvesting). We have even observed enterprising criminals selling COVID-19-specific malware/phishing ‘kits’ which can be customized and leveraged in downline attacks for a very small investment (less than $1000 USD). Nothing is sacred, either: not even the tragic death of NBA star Kobe Bryant, whose image was used to lure fans into downloading malicious desktop backgrounds.
Indeed a picture (in this case an interactive map) is worth a thousand words, with attackers offering up the ability to load payloads to victims that visit this nefarious coronavirus spread map:
At the higher end of the range we have seen nation-state actors embrace this opportunity to deploy their implants to high-value targets.
Domain Registration and Squatting
From the onset of the SARS-CoV-2 virus’s spread, opportunistic cyber-criminals have taken to proactively registering relevant domain names for malicious use. According to data from Recorded Future, “Beginning on January 12, the number of domain registrations started to increase, with an additional large spike on February 12”.
While domain registration alone is not proof of ill-intent, it is a reminder that we need to be extra cautious when interacting with “COVID” and “Coronavirus” related domains.
To provide some context, consider the following data:
Registered domains including “coronavirus” in the last 7 days = 5762
Registered domains including “covid” in the last 7 days = 6155
Registered domains including “covid-19” in the last 7 days = 934
Registered domains including “covid19” in the last 7 days = 3098
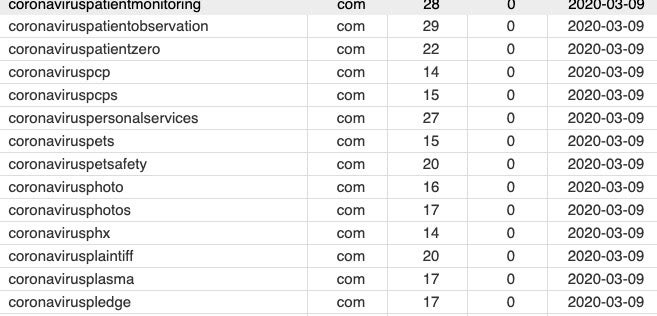
Src: DN Pedia
In the more scam-centric realm, registered domains including “coronacure” in the last 7 days = 934.
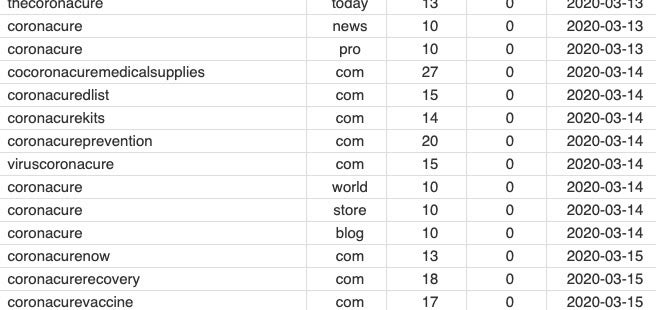
Src: DN Pedia
Some of these domains claim to offer medical supplies at exorbitant prices; would-be buyers pay up-front and take their chances as to whether they will ever see a delivery.
It is important to note that these numbers do not account for typo-squatting or subtly-varied names (homographic attacks), or numerical-replacement variants (aka ‘hackerese).
Malware, Phishing & Scams
A specific rundown of recent campaigns and events is as follows:
January 2020
In late January 2020, we observed Coronavirus-themed Emotet spam campaigns, primarily targeting Japanese entities. Message templates for the spam runs were updated frequently (as is normal with Emotet). That being said, most messages masquerade as “urgent notifications which urge the victims to open malicious email attachments. The malicious attachments are disguised as updated information briefings on COVID-19 patients in their particular region.
February 2020
In early February 2020, multiple COVID-19/Coronavirus-themed phishing campaigns were tracked, targeting primarily the shipping and logistics industry. The phishing campaigns were used to spread the AZORult trojan to high-value targets in the shipping sector. Some message samples contained malicious Microsoft Office documents designed to exploit CVE-2017-11882. CVE-2017-11882 is a memory corruption vulnerability in Equation Editor. Successful exploitation allows for the execution of arbitrary code across affected versions of Microsoft Office.
In early February 2020, a massive COVID-19/Coronavirus-themed phishing campaign targeted large swaths of Office 365 users. The motive behind these campaigns was basic credential harvesting. Victims were urged to open malicious attachments which were disguised as updates on COVID-19 patterns in their local areas. Most observed samples masquerading as updates from the “Centers for Disease Control and Prevention”. Attackers took advantage of ‘look-a-like’ domains for added authenticity (ex: cdc-gov[.]org)
In early February 2020, we tracked COVID-19/Coronavirus-themed spam campaigns spreading LokiBot, specifically targeting Chinese entities. Spam messages were seen masquerading as updates from the ‘Ministry of Health in the People’s Republic of China’. Messages were written in English but appear to have been written by a non-native English speaker. The LokiBot malware was distributed in these messages in the form of RAR archives (with .arj extensions).
In mid-February 2020, multiple malicious websites were constructed to deliver the Grandoreio banking trojan. Multiple weaponized sites were utilized, primarily targeting users in Mexico, Spain, and Brazil. The sites utilized a ‘video player’ download-style lure to entice victims into executing the Grandoreio payloads.
In mid-February, the “Corona Virus Map Phishing Kit” was advertised for sale in various underground forums. The kit ranged in price from $200 USD to $700 USD. Buyers are able to customize the kit to embed their own payloads or force a redirection (upon execution of the trojanized map EXE) to remote payloads. The malicious map executable masquerades as legitimate map data from Johns Hopkins University.
In late February 2020, we observed COVID-19/Coronavirus-themed spam campaigns targeting users in the Ukraine. Spam messages are disguised as updates from the ‘Center for Public Health of the Ministry of Health of Ukraine’. The messages claim to contain updated information for the public pertaining to COVID-19/Coronavirus. Initial waves of the campaign were used to distribute various dropper and downloader trojans.
In late February 2020, COVID-19/Coronavirus-themed spam emails were used to distribute the Tesla Keylogger. Spam messages were constructed via a customized phishing kit. Observed samples are disguised as updates from ‘The Centers for Disease Control’. Victims are enticed into following malicious links in order to access informational “updates for their area”.
In late February 2020, we observed a spam campaign targeting South Korean entities. The spam campaigns were used to distribute BabyShark implants, often associated with the cyber operations of North Korea. Malicious attachments were disguised as official updates on South Korea’s response to COVID-19.
In late February 2020, multiple spam campaigns were observed distributing the FormBook. malware. Messages were disguised as updates from FedEx on their current plans for dealing with issues and delays around COVID-19.
In late February 2020, Trickbot campaigns were tracked, primarily targeting Italian entities. Spam messages were constructed with a customized phishing kit, and redirected victims to Trickbot payloads.
March 2020
In early March 2020, the APT group Mustang Panda (China) utilized multiple spam campaigns to deliver implants. Spam messages made use of multiple COVID-19-themed lures. Malicious documents were used to execute additional scripts, and leverage subsequent LOTL tactics to retrieve and launch payloads.
In mid-March 2020, we observed multiple websites hosting fake versions of WiseCleaner utilities. These sites were used to distribute the Kpot Infostealer trojan, along with a new ransomware family dubbed “CoronaVirus”. From the fake WiseCleaner-themed sites, a malicious version of “WSHSetup.exe” was used to download both the CoronaVirus ransomware along with Kpot Infostealer. Once-infected, a customized ransom message is displayed at boot, prior to the loading of Windows. Victims are instructed to email attackers, as opposed to interacting with them via a payment portal site.
The Kpot Infostealer trojan is coupled with the ransomware in order to harvest cryptocurrency wallets, browser data and credential sets. The requested ransom is typically ~$50.00 USD.
In mid-March 2020, a new family of Android ransomware, CovidLock, began targeting users via malicious app (APK) downloads. The malicious apps were hosted on sites masquerading as hosts for valid real-time information tracking apps. Upon infection, the ransomware tricks users into providing full device control via misleading permissions request dialogs. The malware sets itself to load upon device startup and leads to a lock-screen style ransom request. This specific family utilizes Pastebin to aid in the construction of the displayed ransom notes.
Emergence of Blatant Scams
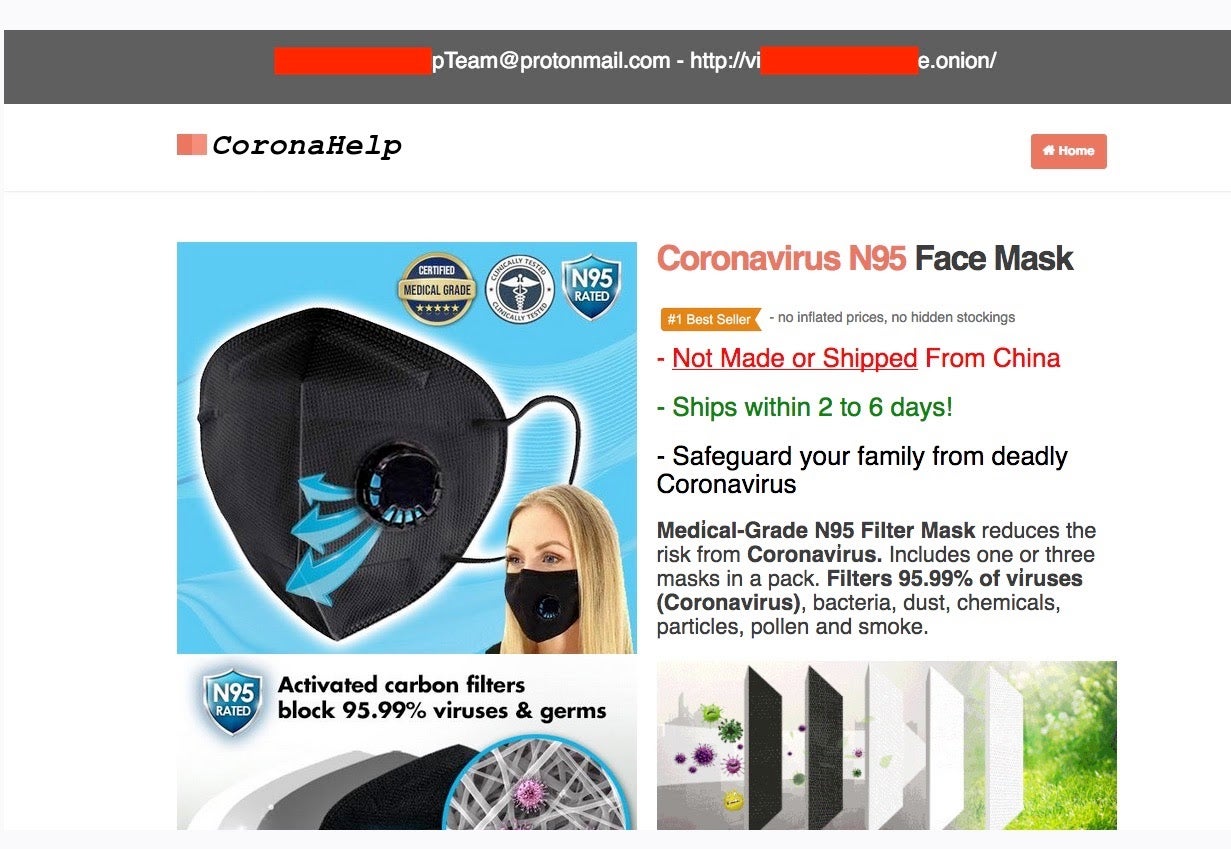
Multiple dark web (.onion) sites claim to sell COVID-19/Coronavirus supplies (masks, sanitization and cleaning supplies) directly for BTC (bitcoin). These are outright scams, which just collect BTC and deliver nothing to their victims. To add insult to injury, we have also seen sites reporting to sell non-existent vaccines, charging $5000.
Scammy COVID-19 supply sellers
Infrastructure & Misinformation Attacks
On Monday, March 16 an attempted DDoS attack was carried out against the US Health and Human Services Department. While the HHS infrastructure remained “fully operational” there was a perceived strain on the targeted systems given the increased activity. The attack comes at a critical time given the current influx of requests to their site (and services) seeking information and updates around protection against COVID-19. In this situation, the HHS was prepared. According to an HHS spokesman, “while preparing and responding to COVID-19, HHS put extra protections in place”.

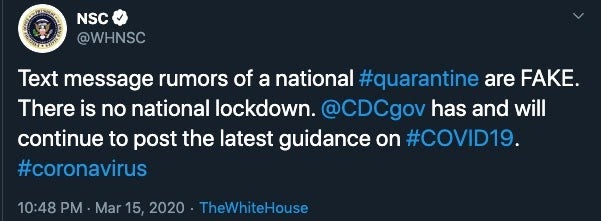
In addition to the DDoS attempt on HHS, we have seen a flurry of social media campaigns specifically crafted to spread misinformation, and increase paranoia around the Coronavirus pandemic. There appear to be multiple, ongoing misinformation campaigns across all social media platforms (ex: Twitter, Facebook, Telegram).

For this reason, we all need to be extra careful and ultra-discerning. The NSC has been quick to alert on and clarify most of these attempts, but again they are ongoing. It is recommended that the public continually monitor the NSC (and other official outlets) for accurate data and updates, as well as alerts on misinformation campaigns.
Supply & Lockdown Effects on the Criminal Element
Cyber criminals can be affected by the societal impacts of COVID-19 as well. Perhaps as a ‘positive’ side-effect, some underground vendors are having to cease operations due to increased risk or limited supplies.
Conclusion
The psychology of fear, uncertainty, and doubt is a powerful weapon. Criminals have become more advanced in their understanding of manipulating human emotion to achieve a targeted action. Social engineering is based on the premise that I can get a victim to take action the victim believes to be trusted, but which is actually malicious, using manipulation, influence, and deceit. It can also be based on downright intimidation, authority, and extortion. The net result is a victim taking actions they otherwise never would have in the absence of social engineering.
Nation-state actors have long relied upon social engineering to achieve targeted goals for espionage, system compromise, election influence, and social media manipulation.
While this is still very much a ‘living’ situation, Sentinel Labs has already observed the ability for enterprising cybercriminals to capitalize on the fear and uncertainty of the general public. As is the case with any large and newsworthy event, our adversaries have no scruples when it comes to social engineering and malware distribution. Nothing is out of bounds, and the main difference with the current climate is that the stakes are much higher. It is enough of a challenge to get accurate data and information from known-and-reputable sources. The criminal element further muddies the water and makes our attempts to protect our loved ones (and selves) that much more of a challenge.
Resources
Sentinel Labs will be posting updates and details as they become available at https://labs.sentinelone.com/
This post draws out critical lessons we can learn from both cyber and biological threats:
In addition, the US-CERT/CISA has posted a list of additional resources which can assist in avoiding COVID-19-related scams and attacks. They cover cyber-hygiene recommendations and link additional helpful resources as well:
US-CERT: Defending Against COVID-19 Cyber Scams
CISA Insights: Risk Management for Novel Coronavirus (COVID-19) (Note: PDF)
Indicators of Compromise
Emotet 4c9e35f3d5f555dda5f4373cf23fbb289c6067c70841be7022ba6da62e49cccbEmotet
b49c9eba58537f8d856daded80bc9493a83c508d73423b98686d4e8b232d61c3Emotet
7cbcad4d6e9ad8438e5febd3830bff9aef4729b98d23935ad7f9e6d290272732Emotet
acec0bb9d9bd199d3e6a77b763cebee8f67275996d3c55af8c617fef76f2e87fEmotet
109[.]236[.]109[.]159Emotet
85[.]96[.]49[.]152Emotet
186[.]10[.]98[.]177Emotet
erasmus-plius[.]tomasjs[.]com/Emotet
easytogets[.]com/Emotet
drhuzaifa[.]comEmotet
dewarejeki[.]infoEmotet
dewakartu[.]infoAZORult
d2b231eb83de043acfcdf1c938c6b49e465d585fe4ce79f42add43a17aba1300AZORult
2b35aa9c70ef66197abfb9bc409952897f9f70818633ab43da85b3825b256307LokiBot
198[.]23[.]200[.]241LokiBot
198[.]23[.]200[.]241LokiBot
906EFF4AC2F5244A59CC5E318469F2894F8CED406F1E0E48E964F90D1FF9FD88Grandoreiro
08710023c219f26237a9c8de5454a1de17117a2da651b4391afce8e331f31dfaGrandoreio
3bbd2beaa7953543e3cfb09d064db83b11034ff81255429b82e2de40d661ee29Grandoreio
13[.]72[.]105[.]98Generic Downloader/Dropper
9aea43b22f214228caf4fc714f426c0a140b7dd70b010bf3778cd1c0ec440851
The post Threat Intel Update | Cyber Attacks Leveraging the COVID-19/CoronaVirus Pandemic appeared first on SentinelLabs.
Article Link: https://labs.sentinelone.com/threat-intel-update-cyber-attacks-leveraging-the-covid-19-coronavirus-pandemic/