During the end of the year 2019, a ransomware named ‘Snatch” was discovered. Snatch ransomware will force Windows to reboot in Safe Mode (where most of the software and system drivers will not be running) in order to perform the file encryption process.
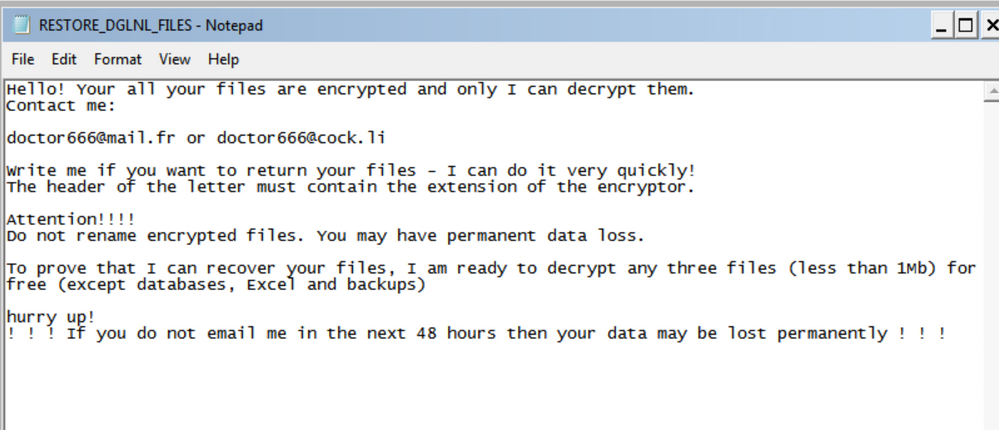
Similar to the other variants of ransomware, it will also perform the deletion of volume shadow copies to ensure all the data cannot be restored easily. After it performs file encryption, it will drop a ransom note named “RESTORE_[five_character_random_string]_FILES.txt” as shown in Figure 1 below.
Figure 1: Screenshot of the ransom note
This post serves to inform our customers about detection and protection capabilities within the Carbon Black suite of products against Snatch Ransomware.
Behavioral Summary
Upon execution of Snatch ransomware, it will install itself as a Windows service named “SuperBackupMan” and create the following registry key to ensure it will start up during bootup into Safe Mode.
HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\SuperBackupMan
Figure 2: Registry key created by Snatch
Next it will run the following commands to force the operating system reboot in Safe Mode:
- bcdedit.exe /set {current} safeboot minimal
- shutdown /r /f /t 00
Figure 3: Screenshot of process chart by Snatch Ransomware
After the infected machine reboots into Safe Mode, it will execute the following commands to stop the ‘SuperBackupMan’ service, delete the volume shadow copies to ensure all the data cannot be restored easily, and then begin the encryption process.
- net stop SuperBackupMan
- vssadmin delete shadows /all /quiet
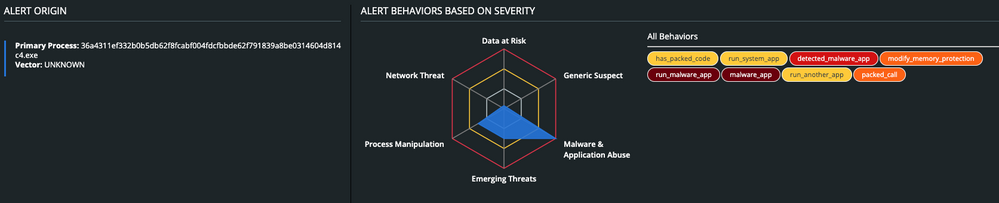
In addition, CB Defense will display the malware’s overall triggered TTPs.
To learn more about how to defend against this attack, click here.
Remediation:
MITRE ATT&CK TIDs
| TID | Tactics | Technique |
|---|---|---|
| T1158 | Defense Evasion, Persistence | Hidden Files and Directories |
| T1060 | Persistence | Registry Run Keys/ Startup Folder |
| T1050 | Persistence | New Service |
| T1045 | Defense Evasion | Software Packing |
| T1143 | Defense Evasion | Hidden Window |
| T1083 | Discovery | File and Directory Discovery |
| T1497 | Defense Evasion, Discovery | Virtualization/Sandbox Evasion |
| T1119 | Collection | Automated Collection |
| T1081 | Credential Access | Credentials in Files |
| T1005 | Collection | Data from Local System |
| T1486 | Impact | Data Encrypted for Impact |
| T1490 | Impact | Inhibit System Recovery |
The post Threat Analysis Unit (TAU) Threat Intelligence Notification: Snatch Ransomware appeared first on VMware Carbon Black.
Article Link: https://www.carbonblack.com/2020/01/21/threat-analysis-unit-tau-threat-intelligence-notification-snatch-ransomware/