A stealthy predator lurks in the vast, unforgiving digital desert, known as AridViper. Like a snake silently slithering through the sands, this state-sponsored cyber threat actor moves with quiet and deadly precision. Emerging from the shadows of the Middle East, AridViper, also recognized as Desert Falcons and APT-C-23, has etched its name in the annals of cyber espionage. With a venomous blend of sophisticated tactics and targeted attacks, this group has struck at the heart of various sectors and nations, leaving a trail of digital intrigue in its wake.
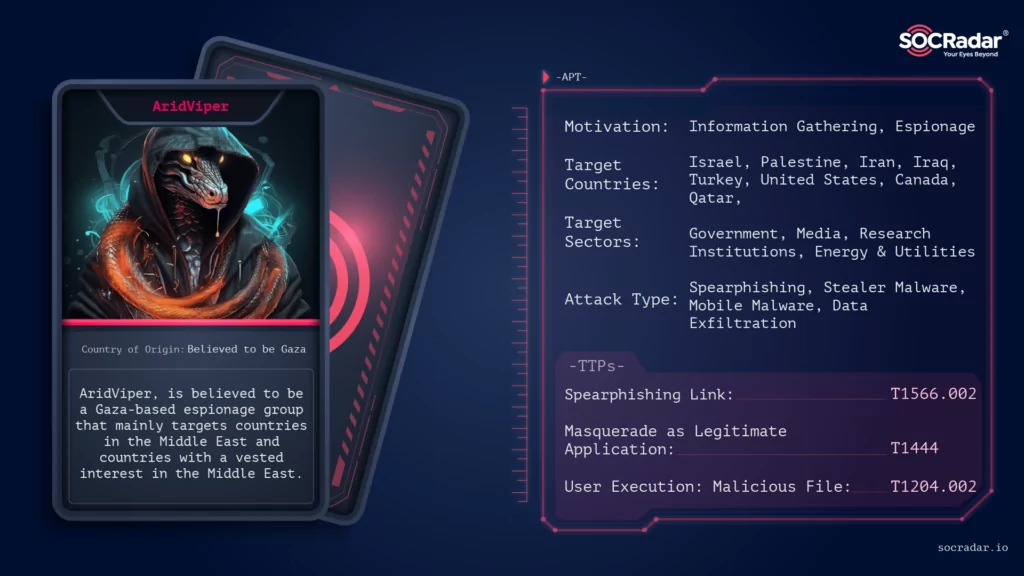 Threat actor card of AridViper
Threat actor card of AridViper
This blog post ventures into the arid realm of AridViper, unraveling the mysteries of who they are, their modus operandi, their prey, and their most cunning operations. As we traverse this digital dunescape, we gain insights into modern cyber threats’ intricate and dangerous world, highlighting the ever-growing need for vigilant and robust cybersecurity defenses.
Who is AridViper?
AridViper, also known as Desert Falcons, Two-tailed Scorpion, and APT-C-23, is a prominent cyber threat actor believed to be state-sponsored and primarily operating in the Middle East. The group is believed to have a connection to Hamas and mainly targets Arabic-speaking countries. Emerging around 2015, but some sources said it is believed to have first seen around mid-2013, this group has engraved a place in cyber espionage, focusing on political and strategic intelligence. Its activities predominantly target entities in Israel and Palestine, but its reach extends beyond these borders, hinting at a broader geopolitical agenda.
 Illustration of AridViper generated using DALL-E 3
Illustration of AridViper generated using DALL-E 3
The group’s modus operandi is characterized by custom-developed malware and sophisticated social engineering tactics. AridViper specializes in creating and deploying various malware tools, including backdoors, spyware, and advanced mobile malware. These tools are designed to infiltrate systems discreetly and exfiltrate sensitive data. The group often employs spear-phishing emails and malicious websites, meticulously crafted to appear legitimate and appealing, exploiting current events or personal interests to lure their targets.
AridViper’s technical prowess is evident in its evolving arsenal of cyber tools. Developing mobile malware variants like GnatSpy and VAMP notably underscores the group’s commitment to expanding its capabilities, particularly in compromising mobile devices. This adaptability and focus on high-value targets underscore AridViper’s position as a formidable actor in the cyber espionage landscape.
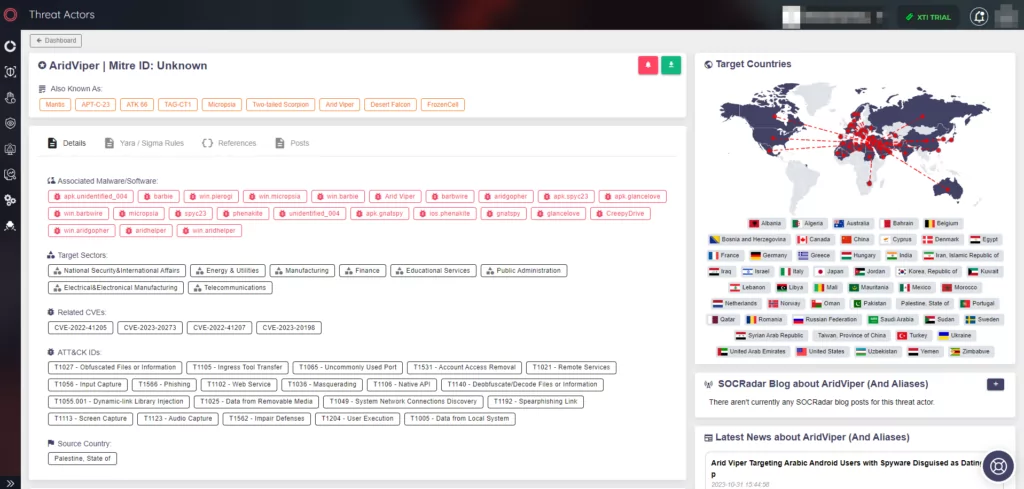 Threat Actor information page of AridViper (Source: SOCRadar)
Threat Actor information page of AridViper (Source: SOCRadar)
How Does AridViper attack?
AridViper employs a multifaceted approach to cyber-attacks, characterized by a blend of technical sophistication and psychological manipulation. The group’s tactics are designed to infiltrate systems, remain undetected, and extract valuable information. Below are the methods used by AridViper in their cyber attacks, each illustrating the group’s tactical diversity and technical expertise.
Spear-Phishing Emails: AridViper frequently initiates attacks with spear-phishing emails. These emails are carefully crafted to appear legitimate and often contain malicious attachments or links. Once opened or clicked, they deploy malware or direct the victim to compromised websites.
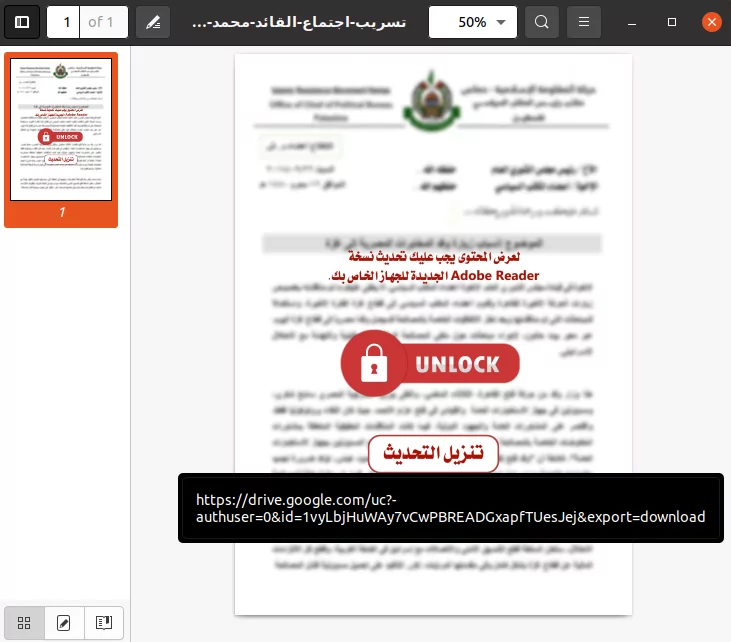 Lure document used in the delivery of AridViper’s Remote Access Trojan (Source: Qihoo 360)
Lure document used in the delivery of AridViper’s Remote Access Trojan (Source: Qihoo 360)
Custom Malware Deployment: The group is known for developing and using custom malware, including backdoors and spyware. This malware is tailored to stealthily infiltrate target systems, avoid detection, and transmit sensitive data back to the attackers.
Exploitation of Social Media: AridViper also leverages social media platforms to target individuals. They create fake profiles, engage in social engineering to build trust, and eventually deliver malware through shared links or files. Besides, AridViper commonly uses legitimate-looking social media applications to spread its malware.
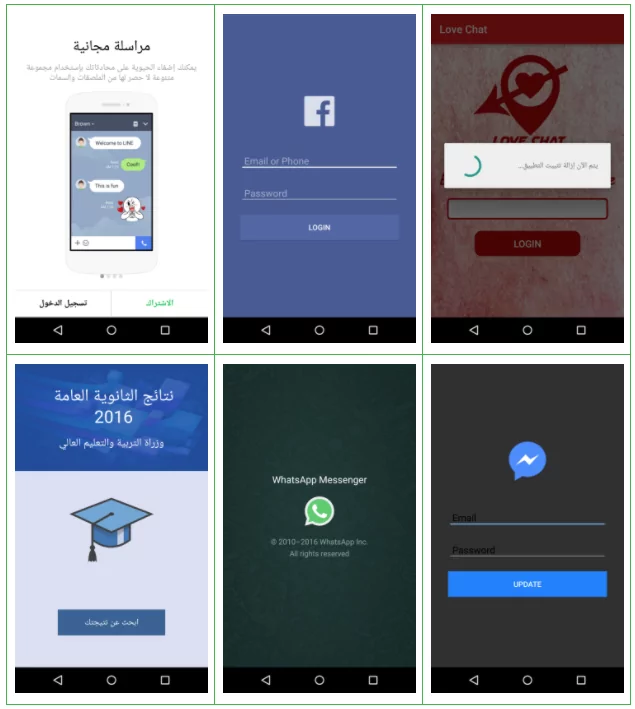 Fake social media and examination apps used by AridViper to spread its malware (Source: Lookout)
Fake social media and examination apps used by AridViper to spread its malware (Source: Lookout)
Mobile Malware: A significant aspect of AridViper’s arsenal includes mobile malware like FrozenCell, GnatSpy, and VAMP. These tools are designed to compromise mobile devices, enabling the group to access various personal and organizational data.
Exfiltrate data from USB drives: Besides the previous tactics, AridViper has been known to use scripts to exfiltrate data from local hard drives and USB devices.
 The infographic shows the numbers of data AridViper exfiltrated during its Desert Falcons campaign (Source: Kaspersky)
The infographic shows the numbers of data AridViper exfiltrated during its Desert Falcons campaign (Source: Kaspersky)
What Are the Targets of AridViper?
AridViper’s operations are not random; they are meticulously planned and executed with specific targets in mind. These targets are chosen based on their strategic value for intelligence gathering or exerting influence in the geopolitical landscape. The group focuses primarily on the Middle East, but its activities have global implications. This section is divided into Targeted Countries and Targeted Sectors, each highlighting the specific focus areas of AridViper’s operations.
Targeted Countries
AridViper’s primary focus has been on countries in the Middle East, with a significant emphasis on Israel and Palestine. These countries are particularly interesting due to their central role in regional politics and conflicts. However, the group’s activities are not confined to these nations alone. There have been instances of AridViper targeting entities in other countries, particularly those with a vested interest in the Middle East or those involved in international diplomacy and defense sectors. This global reach indicates a strategic intent to gather intelligence that could influence regional and international policies.
Targeted Sectors
Government and Military: One of the primary targets of AridViper is government and military institutions. These targets are of high value due to the sensitive and classified information they hold, which can provide strategic advantages in terms of intelligence and national security.
Media and Communications: AridViper also targets media outlets and communication companies. Infiltrating these sectors allows the group to potentially manipulate public opinion and access a wealth of information circulating in journalistic and communication networks.
Academic and Research Institutions: Universities and research institutions are targeted for their cutting-edge research and development information, particularly in fields related to technology, defense, and international relations.
Technology Companies: Tech companies, especially those involved in software development and cybersecurity, are targeted to gain access to proprietary technologies and exploit vulnerabilities within digital infrastructures.
Notable Operations of AridViper
AridViper has been involved in several high-profile operations, showcasing its sophisticated cyber espionage approach. Below is a list of some of their most notable operations, highlighting the group’s evolving tactics and targets.
Operation Desert Falcons: One of the earliest and most comprehensive campaigns attributed to AridViper. Targeting government officials, activists, and media organizations, this operation involved using custom malware to infiltrate systems and exfiltrate sensitive data. It was notable for its broad reach and the diversity of its targets across the Middle East.
 Timeline of Desert Falcons Campaign (Source: Kaspersky)
Timeline of Desert Falcons Campaign (Source: Kaspersky)
Operation Bearded Barbie: This campaign by AridViper targeted Israeli officials, utilizing sophisticated malware delivered through deceptive social media tactics. Named for its unique blend of social engineering and technical skills, the operation was focused on data exfiltration and surveillance.
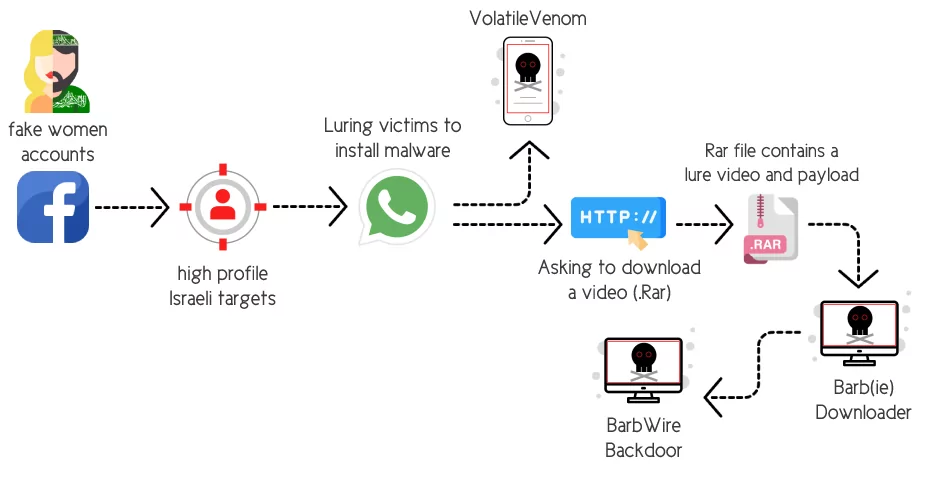 Infection chain of Operation Bearded Barbie (Source: Cybereason)
Infection chain of Operation Bearded Barbie (Source: Cybereason)
VIPERRAT Mobile Campaign: AridViper executed a significant mobile espionage campaign using malware known as VIPERRAT. This operation specifically targeted high-profile individuals in the Middle East, leveraging mobile devices to gain access to a wealth of personal and professional information.
Micropsia Malware Deployment: In this operation, AridViper used a malware called Micropsia, which is known for its capabilities to record audio, take screenshots, and gather system information. This malware was used mainly against organizations in the Middle East, focusing on extracting as much data as possible from compromised systems.
GnatSpy Mobile Malware: This operation involved using GnatSpy, a variant of mobile malware developed by AridViper. It targeted Android devices, particularly those used by individuals in the Middle East, to collect call logs, text messages, and other sensitive data.
Use of Fake Dating Apps: AridViper was found to camouflage its malware in knockoff dating apps in a more unconventional approach. Once downloaded and installed, these apps served as a conduit for the group to infiltrate mobile devices and extract data.
 Some of the fake dating apps used by AridViper to hide its malware (Source: Meta)
Some of the fake dating apps used by AridViper to hide its malware (Source: Meta)
Social Media-Based Attacks: AridViper has also been involved in operations that leverage social media platforms to target individuals. By creating fake profiles and engaging in social engineering, they could deliver malware to unsuspecting victims.
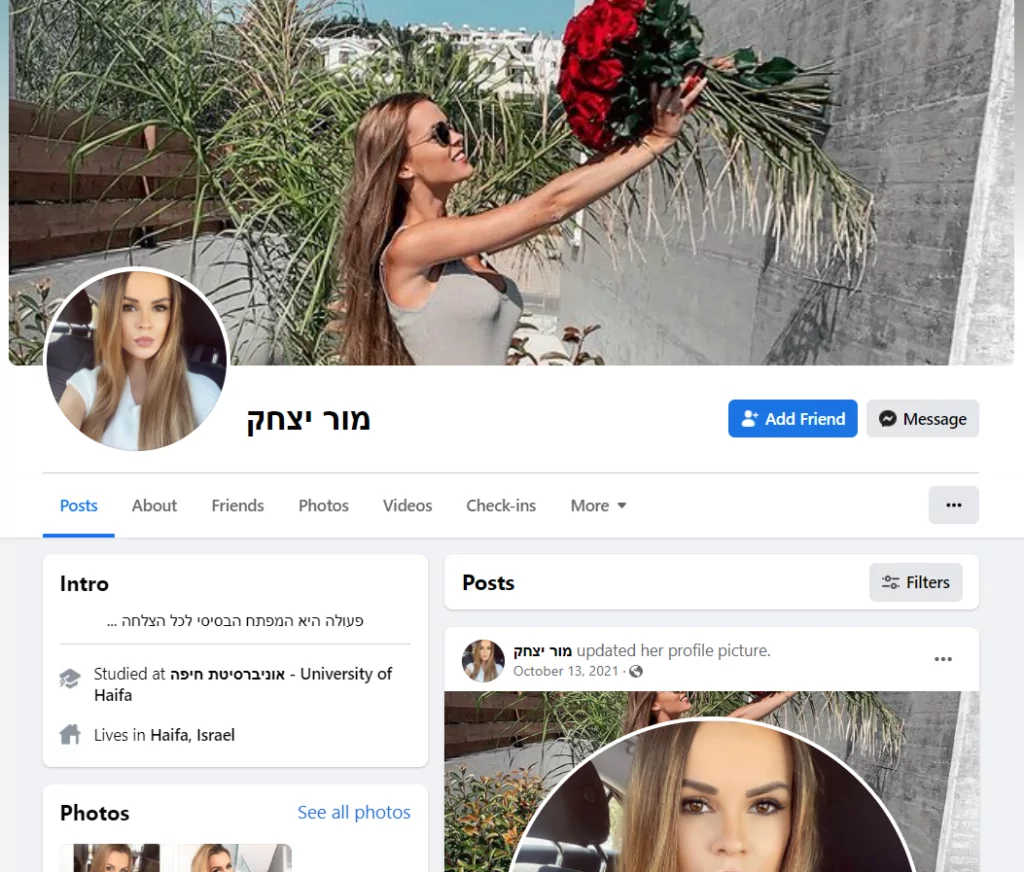 One of the fake profiles used by AridViper (Source: cybereason)
One of the fake profiles used by AridViper (Source: cybereason)
Conclusion
In summary, AridViper stands as a formidable force in the landscape of cyber espionage. Originating from the Middle East, this state-sponsored group has demonstrated a profound capability for sophisticated cyber attacks targeting diverse sectors and countries. Through their use of custom malware, spear-phishing, mobile espionage, and fake social media profiles, AridViper has shown remarkable adaptability and technical prowess. Their operations, from Operation Desert Falcons to deploying GnatSpy and Micropsia malware, highlight their strategic intent and expertise in digital espionage.
Security Recommendations Against AridViper
To defend against AridViper and other sophisticated threat actors, organizations should take the following steps:
Enhanced Email Security: Given AridViper’s reliance on spear-phishing, it is crucial to implement advanced email filtering solutions. These should include phishing detection and sandboxing capabilities to scrutinize email attachments and links for malicious content.
Regular Security Awareness Training: Educate staff and users about the risks of spear-phishing and social engineering attacks. Regular training sessions can significantly reduce the likelihood of successful phishing attempts.
Robust Endpoint Protection: Deploy comprehensive endpoint security solutions that offer real-time monitoring and protection against malware, including custom and zero-day threats. Ensure that all endpoints are regularly updated and patched.
Mobile Device Management (MDM): With AridViper’s focus on mobile malware, implementing an MDM solution is vital. This should include monitoring, managing, and securing employees’ mobile devices that access corporate networks and data.
Network Segmentation and Access Control: Segment your network to limit the spread of an intrusion. Implement strict access controls and use the principle of least privilege to minimize the access rights of users and applications to only what is necessary.
Incident Response Plan: Have a well-defined incident response plan in place. This plan should include procedures for identifying, containing, eradicating, and recovering from a cyber attack and notifying relevant stakeholders.
Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration tests to identify and remediate vulnerabilities in your IT infrastructure.
Monitoring and Logging: Implement comprehensive logging and monitoring solutions. Regularly review logs for suspicious activities, especially those relating to sensitive data and systems access.
USB Security Policies: Given the use of USB malware, enforce strict policies regarding the use of removable media. This includes disabling autorun features and scanning all USB devices for malware before use.
Stay Informed and Collaborative: Keep abreast of the latest cyber threat intelligence and collaborate with industry peers and government bodies to share information about threats and best practices.
MITRE ATT&CK TTPs of AridViper
|
Technique |
ID |
|
Initial Access |
|
|
Exploit Public-Facing Application |
|
|
Phishing |
|
|
Phishing: Spearphishing Attachment |
|
|
Phishing: Spearphishing Link |
|
|
Deliver Malicious App via Other Means |
|
|
Masquerade as Legitimate Application |
|
|
Execution |
|
|
Command and Scripting Interpreter |
|
|
User Execution |
|
|
User Execution: Malicious File |
|
|
Windows Management Instrumentation |
|
|
Native Code |
|
|
Persistence |
|
|
Scheduled Task/Job |
|
|
Create or Modify System Process |
|
|
Hijack Execution Flow |
|
|
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
|
|
Broadcast Receivers |
|
|
Privilege Escalation |
|
|
Abuse Elevation Control Mechanism |
|
|
Defense Evasion |
|
|
Process Injection |
|
|
Hide Artifacts |
|
|
Impair Defenses |
|
|
Indicator Removal |
|
|
Masquerading |
|
|
Virtualization/Sandbox Evasion: System Checks |
|
|
Subvert Trust Controls: Code Signing |
|
|
Suppress Application Icon |
|
|
Credential Access |
|
|
Exploitation for Credential Access |
|
|
Discovery |
|
|
File and Directory Discovery |
|
|
Network Service Discovery |
|
|
Process Discovery |
|
|
System Information Discovery |
|
|
Collection |
|
|
Input Capture |
|
|
Archive Collected Data |
|
|
Screen Capture |
|
|
Data from Local System |
|
|
Capture Camera |
|
|
Capture Audio |
|
|
Access Notifications |
|
|
Access Call Log |
|
|
Protected User Data: Contact List |
|
|
Protected User Data: SMS Messages |
|
|
Command and Control |
|
|
Application Layer Protocol |
|
|
Application Layer Protocol: Web Protocols |
|
|
Data Obfuscation |
|
|
Ingress Tool Transfer |
|
|
Non-Standard Port |
|
|
Impact |
|
|
Delete Device Data |
The post Threat Actor Profile: AridViper appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: https://socradar.io/threat-actor-profile-aridviper/
