In today’s digital age, the term “torrenting” often evokes images of pirated movies, music, or TV shows. However, the world of torrents is much broader than just illegal content. Torrenting, at its core, is a decentralized peer-to-peer file-sharing protocol known as BitTorrent. While a significant portion of BitTorrent traffic does involve copyright infringement, there are numerous legitimate uses for this technology. From reducing server costs for companies to distributing free or public content, the BitTorrent protocol offers a range of benefits. However, with these advantages come risks, especially when it comes to security and legal implications.
In this blog post, we will delve deep into the world of torrenting, exploring its mechanisms, benefits, potential dangers, and best practices for safe torrenting. Whether you’re a seasoned Torrent user or a newbie, this guide will provide a comprehensive understanding of the BitTorrent landscape.
What is a Torrent?
At its essence, torrenting is a method of downloading and sharing files using the BitTorrent protocol. But to truly grasp the concept, we need to break it down further:
- BitTorrent Protocol
The BitTorrent protocol is a decentralized peer-to-peer file-sharing system. Unlike traditional downloading methods where a user connects to a single server to obtain a file, BitTorrent allows users to download pieces of a file from multiple sources simultaneously. This decentralized approach not only speeds up the download process but also reduces the load on individual servers/users.
- Peer-to-Peer (P2P) File-Sharing
In a P2P network, every participant (or “peer”) acts both as a client (downloading files) and a server (uploading files). This interconnected web of peers ensures that tasks or data are distributed evenly across the network. Each peer contributes to the network by sharing a portion of the file they have, making the entire process collaborative.
- Torrent Files & Magnet Links
A Torrent file is a small file containing metadata about the files you want to download and information about the trackers, the computer that coordinates the file distribution. Instead of holding the actual content you wish to download, it provides a roadmap for your Torrent client to find peers who have the actual file pieces.
Magnet links, on the other hand, are a newer approach. They contain similar information as Torrent files but are presented as links. Clicking on a magnet link automatically opens your Torrent client and begins the downloading process, eliminating the need to download a separate torrent file.
- Trackers
Think of trackers as the phonebooks of the BitTorrent world. They help your Torrent client locate other peers who have the file you want to download. Once your client connects to a tracker, it receives a list of other peers and establishes a connection to download file pieces.
- Swarms, Seeders, and Leechers
When you’re downloading a file via a Torrent, you’re part of a “swarm” – a group of users who are either downloading (leeching) or uploading (seeding) a particular file. Seeders are users who have the complete file and are sharing it, while leechers are those who are still downloading the file. The health and speed of a Torrent often depend on the ratio of seeders to leechers: the more seeders, the faster and more reliable the download.
To illustrate it step by step let’s check this diagram:
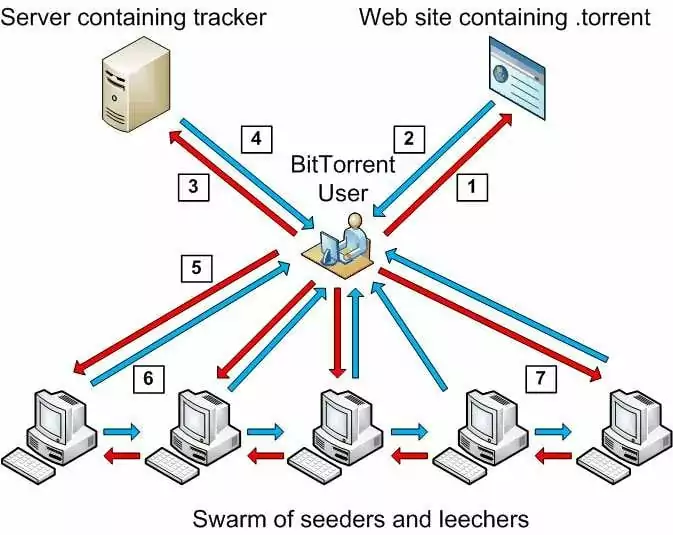 Figure 1. How BitTorrent works. (An FPGA-based system for tracking digital information transmitted via Peer-to-Peer protocols.)
Figure 1. How BitTorrent works. (An FPGA-based system for tracking digital information transmitted via Peer-to-Peer protocols.)
- The user searches online for the desired .torrent file.
- The user downloads the .torrent file and opens it with a BitTorrent client.
- The client contacts the tracker using the .torrent’s metadata and requests a peer list.
- The tracker provides a list of peers seeding the referenced file.
- The client handshakes with the listed peers; responsive peers indicate file availability.
- The client downloads file pieces from responsive seeders and shares completed pieces with the swarm.
- After downloading, the client seeds the file until it is disconnected from the swarm.
In essence, torrenting is a collaborative effort. It’s a system where everyone benefits from sharing, ensuring files are downloaded faster and more efficiently. However, it is essential to understand that while the technology itself is legal, the content being shared might not always be.
The Risks of Torrenting
While torrenting offers a unique and efficient method of file sharing, it’s not without its dangers. Here are some of the primary risks associated with torrenting:
Legal Consequences
Copyright Infringement: The most significant risk associated with torrenting is downloading or distributing copyrighted material without authorization. Engaging in such activities can lead to legal consequences, ranging from fines to potential jail time, depending on the jurisdiction.
ISP Monitoring: Many Internet Service Providers (ISPs) monitor Torrent traffic. If they detect that you’re downloading copyrighted content, they might send warning emails, throttle your internet speed, or even report your activities to copyright holders.
Direct Legal Action: In some jurisdictions, especially in the U.S., copyright holders might take direct legal action against individuals they believe are infringing on their copyrights. While rare, there have been instances where individuals have faced lawsuits for torrenting copyrighted content.
Malware and Exposure
Fraudulent Files: Not all torrents are what they claim to be. Some might be disguised malware or contain malicious files that can harm your device or steal your data. This scenario is quite prevalent, particularly in pirated software and cracked products. Even when the downloaded application appears to function as desired, it could potentially serve as a Trojan horse, opening a backdoor to your computer.
Vulnerable Software: Outdated Torrent clients can have vulnerabilities that hackers can exploit. It is essential to keep your Torrent client updated to the latest version to avoid potential security breaches.
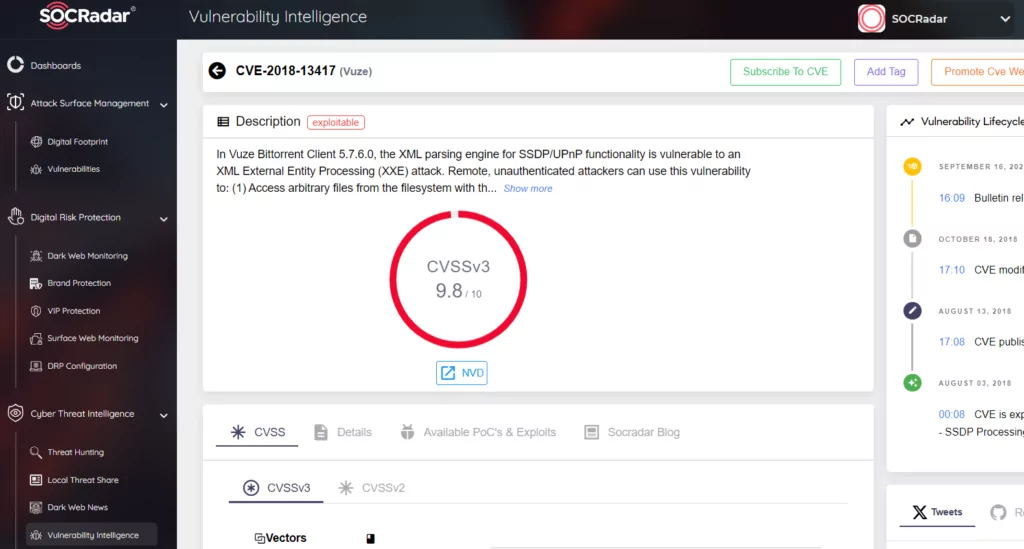 Figure 2. SOCRadar Vulnerability Intelligence, Many Torrent software may have critical vulnerabilities.
Figure 2. SOCRadar Vulnerability Intelligence, Many Torrent software may have critical vulnerabilities.
Privacy Concerns: When you’re part of a Torrent swarm, your IP address is visible to all other peers. This exposure can lead to potential privacy risks, as malicious actors might target your connection or even attempt to identify you. This can expose you to potential threats and make you vulnerable to attacks. In this regard, SOCRadar can identify if your institution’s IP is part of such networks.
For this situation’s dangers and solution methods, see “How to detect if your IP addresses are being used in DHT Networks?” blog post.
Protecting Yourself While Torrenting
Engaging in torrenting without proper precautions can expose you to various risks. However, by following these protective measures, you can significantly enhance your security and privacy:
- Use a VPN (Virtual Private Network)
A VPN masks your IP address, making it difficult for anyone (including your ISP) to track your online activities and VPNs encrypt your data, ensuring that even if someone intercepts your traffic, they won’t be able to decipher its contents.
- Choose a Reputable Torrent Client
Ensure that your Torrent client is regularly updated to protect against vulnerabilities. Some torrent clients come with bundled adware or are prone to security issues.
- Download from Trusted Sources
Before downloading a Torrent, read the comments and reviews. Other users might mention if the file contains malware or if it is a fake. Some torrent sites have verified badges for trusted uploaders. Look for these badges to ensure the authenticity of the torrent.
- Enable a Kill Switch
A kill switch is a feature in many VPNs that will cut off your internet connection if the VPN connection drops, ensuring that your real IP address is never exposed.
- Peer Blockers
Software like PeerBlock can block connections to known malicious IP addresses, adding an extra layer of protection.
But remember, while these measures can significantly enhance your security and privacy, no method is 100% foolproof. Always stay informed about the latest security practices and be cautious about the torrents you choose to download.
Torrents and Ransomware: The Case of Clop
Ransomware groups are continuously seeking innovative methods to maximize their impact and evade authorities. One such tactic that has recently come to light involves the use of torrents by the Clop ransomware gang.
The Clop ransomware group has shifted its extortion tactics to use torrents for leaking data, especially data stolen in MOVEit attacks. This move is strategic, as torrents are decentralized, making it challenging for authorities to take down the leaked data.
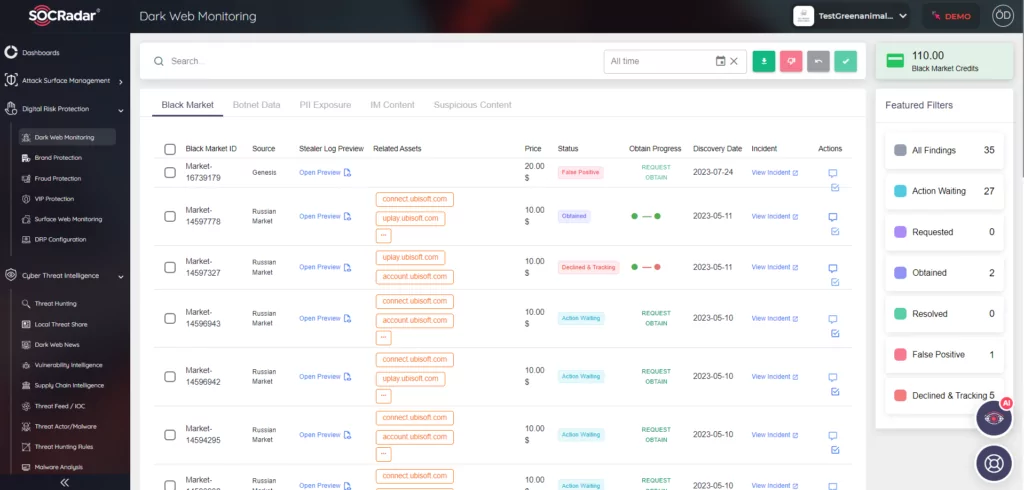 Figure 3. SOCRadar, Digital Risk Protection Module
Figure 3. SOCRadar, Digital Risk Protection Module
SOCRadar Digital Risk Protection may help you stay ahead of potential data breaches by receiving alerts if your data appears in unauthorized places, including torrent sites.
Furthermore, traditional data leak sites, especially those on the TOR network, offer slower download speeds, reducing the impact of the leak. By using torrents, which employ peer-to-peer (P2P) file transfers, the Clop gang ensures faster data distribution, making the leaked information more accessible and increasing the potential damage.
Conclusion
Torrenting, a revolutionary method of file sharing, has undeniably transformed the way we access and distribute content. Its decentralized nature offers speed and efficiency, making it a preferred choice for many. However, as with any technology, it comes with its set of challenges and risks. From legal implications to cybersecurity threats, the landscape of torrenting is fraught with potential pitfalls.
Recent developments, such as the innovative tactics of ransomware groups like Clop, further emphasize the need for vigilance and proactive measures. It is a stark reminder that in the digital age, staying informed and adopting robust security practices is not just beneficial—it is imperative.
While tools and platforms like SOCRadar offer advanced solutions to navigate these challenges, individual responsibility remains paramount. Whether you’re an individual user or a large organization, understanding the intricacies of torrenting, its benefits, and its dangers, is the first step towards safer online practices.
The post The Torrent Landscape: Understanding Security, Risks, and the Future appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: The Torrent Landscape: Understanding Security, Risks, and the Future
