Along with the many advantages and opportunities the digital age brings, cybersecurity is becoming an increasing priority. With each passing day, cyber threats are becoming more complex and sophisticated, and preparedness against these threats is becoming one of the top priorities of cybersecurity experts and organizations. In this context, cyber attack tools such as open-source botnets have gained particular attention in the cybersecurity world, as they are both easily accessible and can be updated faster against security measures.
In this research paper, we focus on the Supershell botnet. Supershell is a prominent example of open-source botnets and has recently attracted the attention of the cybersecurity community for its features. This paper aims to investigate and analyze the number of active botnet panels of the Supershell botnet in the last month to gain important insights about the attackers and potential victims.
The use of open-source botnets poses new issues and challenges in cybersecurity. This article will help us understand how such botnets work and what dangers they pose through the Supershell botnet. The findings on the Supershell botnet can be an essential reference for cybersecurity experts and those who develop organizations’ security strategies.
Introduction To Supershell Botnet
Supershell is a type of open-source botnet, a WEB management platform that integrates reverse SSH (Secure Socket Shell) service. It stands out as a botnet capable of one-click fast builds using Docker. Supershell supports team collaboration for C2 remote control and can achieve a fully interactive shell by establishing a reverse SSH tunnel on the target host. This platform offers client-side payloads for multi-platform architectures, and the client-side payload size is a few megabytes. This means quickly deploying an SSH server of a few megabytes to the target host and then obtaining an SSH shell. Supershell offers a range of capabilities such as client management, client payload creation, interactive shell, file management, file server, memory injection, service installation, GUID migration, native SFTP command for local file transfer, native SSH tunnel port forwarding and note taking.
Functional Features:
- Supports concurrent operation and allows access to all features through a single browser.
- Supports bouncing shell client payload, integrated compression, and kill protection for different system architectures.
- Supports automatic reconnection even if the client disconnects.
- Provides a fully interactive shell on all platforms and supports using this shell within the browser and shell sharing.
- Supports managing the list of connected clients.
- Built-in file server.
- Supports file management.
- Supports memory injection, i.e., files can be executed on local storage without trojan behavior tree.
- Supports bouncing shell service setup on Windows and uid and gid passing on Linux.
Supported Architectures:
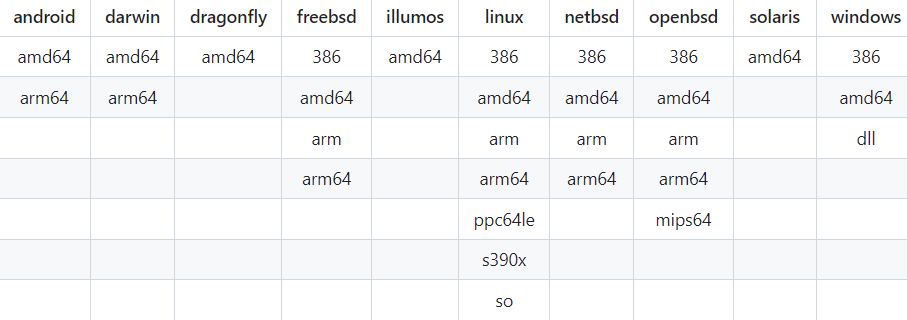 Supershell supported architectures
Supershell supported architectures
The image above shows that Supershell Botnet is compatible with different operating systems and architectures. However, since our primary focus is not to introduce the Botnet, we can briefly examine this information and move on to our main objectives.
Threat Hunting For Supershell Botnet Panels
In our research process, we meticulously examined the Supershell Botnet Panels detected in the last month. We tried to get to know the Supershell Botnet more closely by adopting an operational approach and infiltration of these panels.
We started the tracking process on Urlscan with a search query that enabled us to achieve successful results. With the search query we created, we were able to access the information of a large number of active panels. The results of our research with the query “task.tags:(c2 AND malware AND supershell)” in the search query section on Urlscan are shown below.
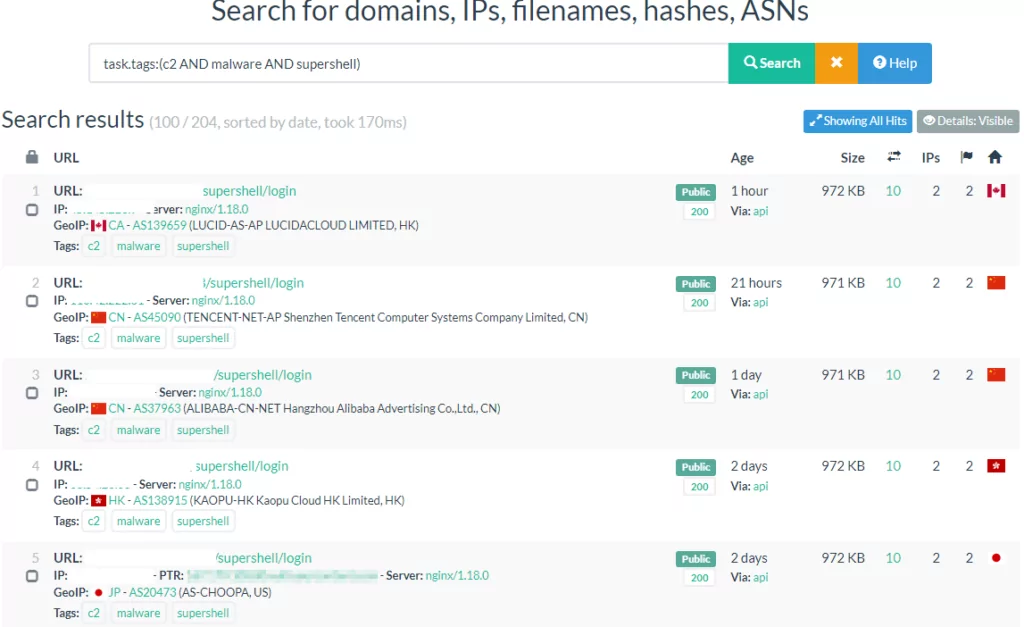 Urlscan search: “task.tags:(c2 AND malware AND supershell)”
Urlscan search: “task.tags:(c2 AND malware AND supershell)”
Since we set a date range for the last month, the total number of Supershell Botnets in this date range is 85.
As can be seen from the results, the last detections were made one hour before the relevant query was run. We can observe that the number of active Supershell Botnet panels is constantly increasing. During the operation, we obtained login credentials to some of the dynamic addresses to learn more about the panel and the attacker’s attack strategy.
The panel login page usually requests only username or username with password information. The Supershell Botnet similarly requires a username and password.
 Supershell panel login page
Supershell panel login page
We detected many Supershell panels and immediately started our operational efforts. We took one of the panels we successfully logged into and examined the panel interface. As you can see from the image below, we can view infected systems and access options that can enable the creation of malicious files. There are also pages in the panel where we can view logs.
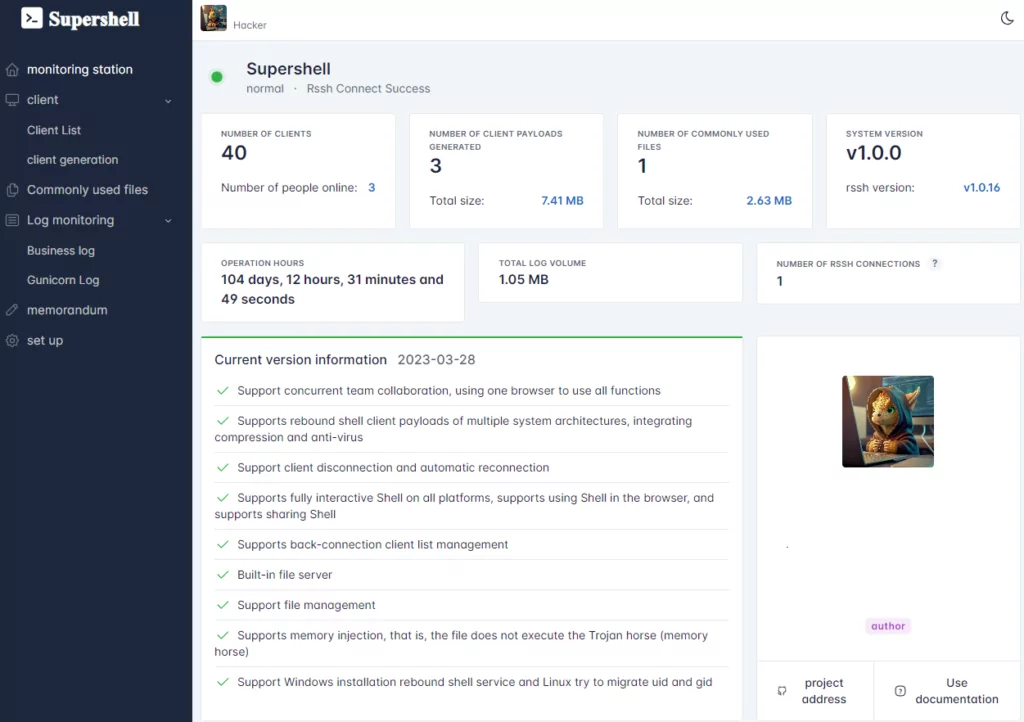 Supershell botnet panel interface
Supershell botnet panel interface
When we entered the page with infected systems, we encountered systems from different countries with different operating systems included in the Botnet network.
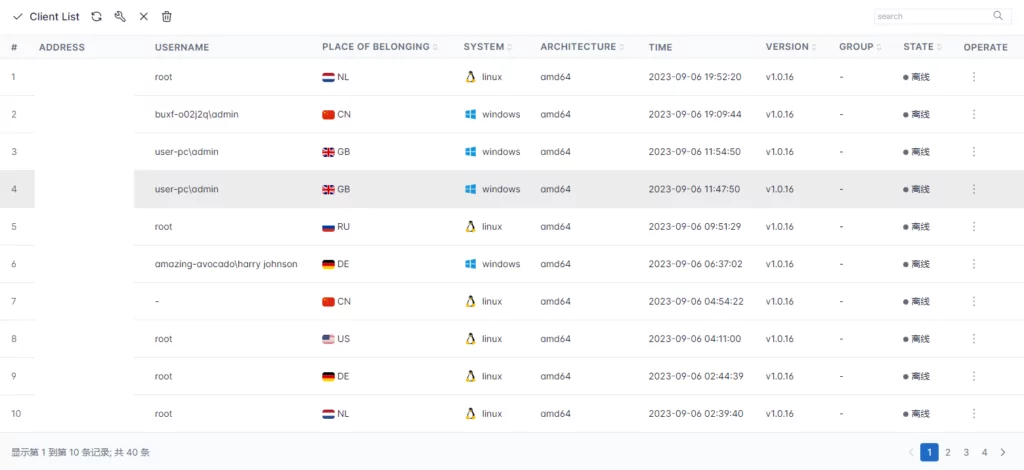 Infected systems
Infected systems
We were able to successfully log in to a few panels during this process. Some of these panels contained malware that had been created, although no infected systems were detected.
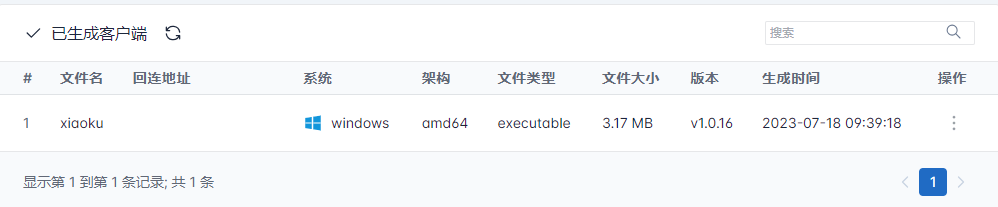 There is an executable named “xiaoku”
There is an executable named “xiaoku”
Based on our previous statement, there is no infected system yet, but an executable file is targeting the Windows operating system created under the name ‘xiaoku’. As the SOCRadar Threat Research team, we started to closely monitor these panels by cooperating with our other teams to monitor and connect them to the SOCRadar platform.
When we search for one of the botnet addresses in the SOCRadar Threat Hunting module, we can see from a single screen where we can catch it as a source of IOCs as below.
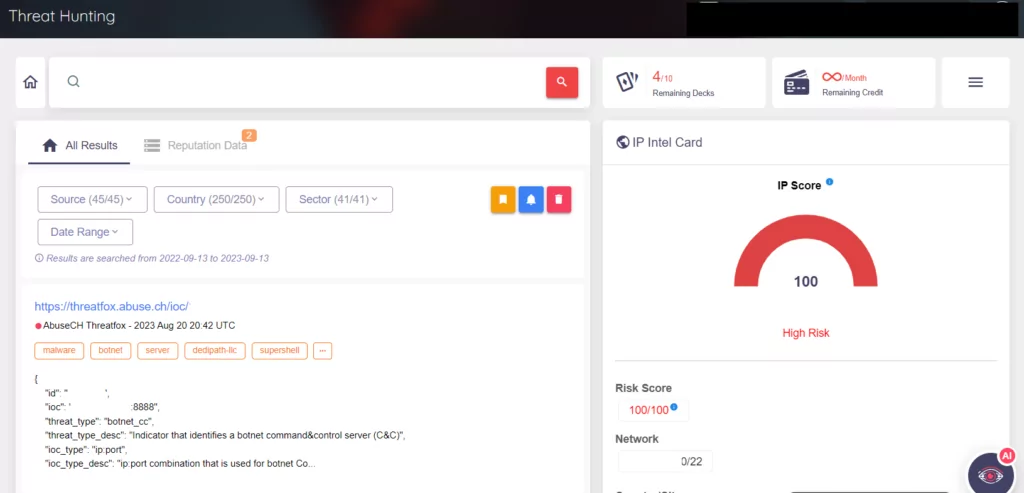 SOCRadar Threat Hunting
SOCRadar Threat Hunting
While investigating the Supershell botnet panels, we obtained login authorization to one more panel containing many infected devices running Linux operating systems.
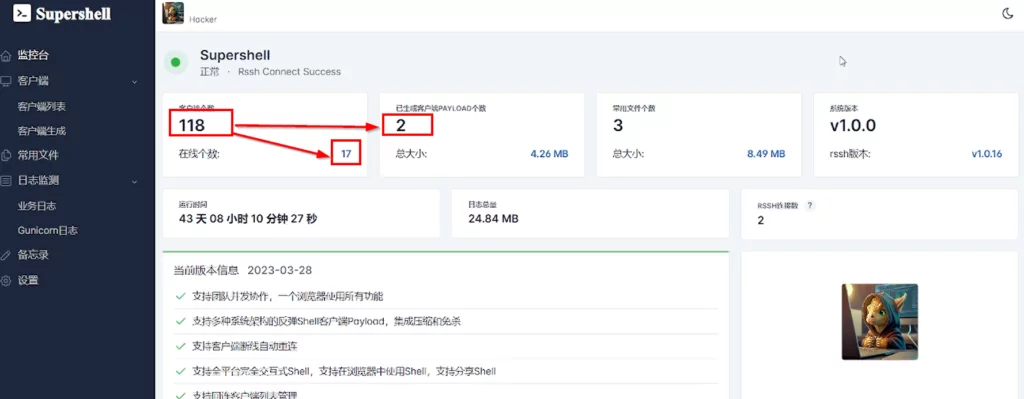 Supershell botnet panel shows 118 infected systems
Supershell botnet panel shows 118 infected systems
We detected 118 infected systems in this panel, 17 of which were running online. We also observed that two different malware were being used among these infected systems. When we dynamically analyzed these two malware, we observed that both were configured to connect to the Supershell botnet panel.
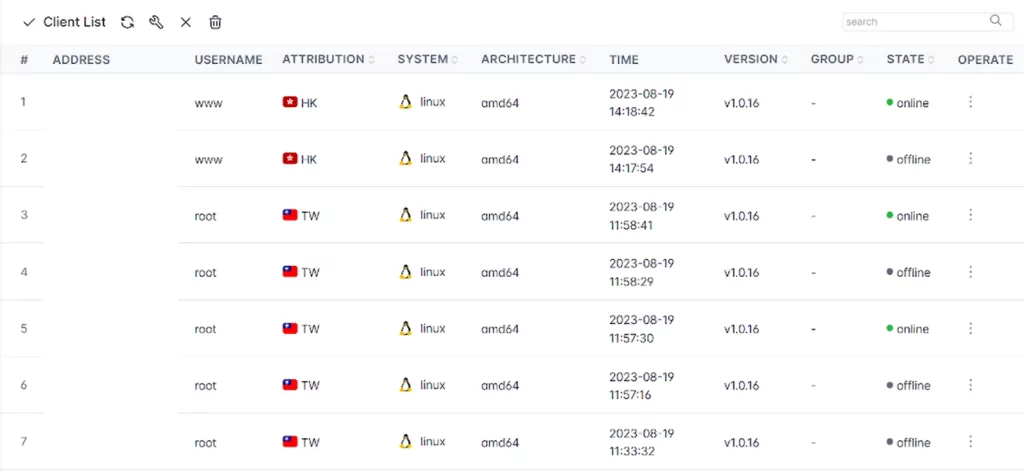 Online infected systems
Online infected systems
Our attempts to establish an SSH connection to infected systems online have been successful.
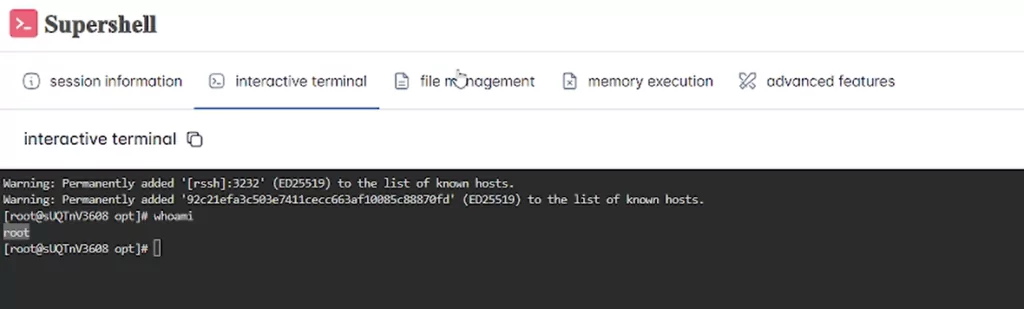 Supershell botnet interactive terminal
Supershell botnet interactive terminal
The high number of infected systems in this panel was the first thing that stood out. However, a closer look at the malware revealed a file named “xmrig”. From this, the threat actor seems to be using the infected Linux operating systems for crypto mining. In other words, these infected systems are being exploited to mine cryptocurrencies.
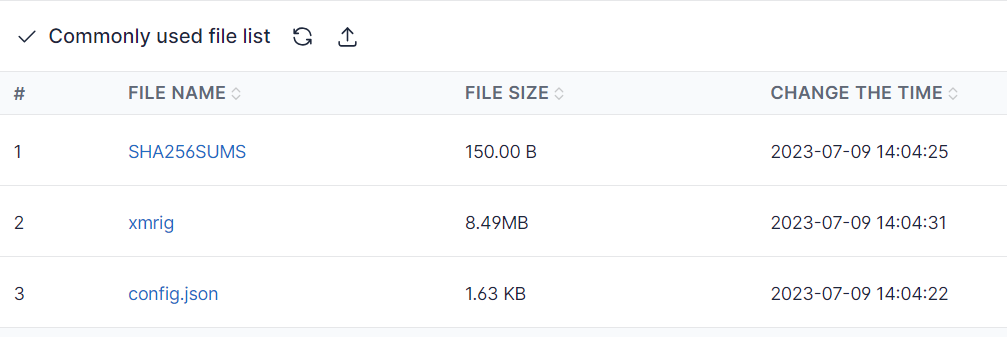 Xmrig miner is seen among files
Xmrig miner is seen among files
When we examined the infected systems and panel logs in detail, we identified accounts, log-in and logout records, and total addresses to confirm the activities we suspected.
 Panel logs
Panel logs
In total, 45 different crypto account addresses are hosted, and the results for the account where we observed the most activity are as follows.
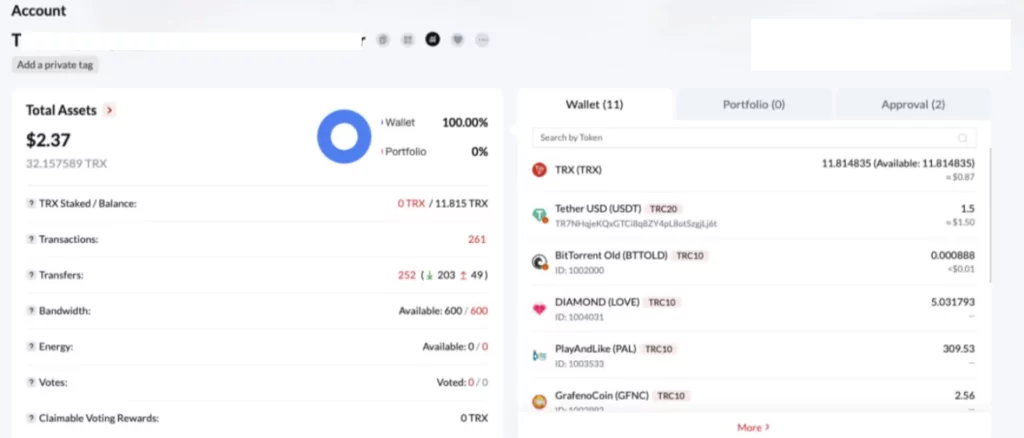 The most active crypto account
The most active crypto account
A total of 261 transactions with the Tron (TRX) wallet were observed in the account indicated in the screenshot. We also tried to observe past activity using the “history” command on infected systems that we could connect to different panels.
SSH connections were broken for those online in many panels. However, we could run the “history” command without connection problems on online infected systems in a panel where we could open session authorization.
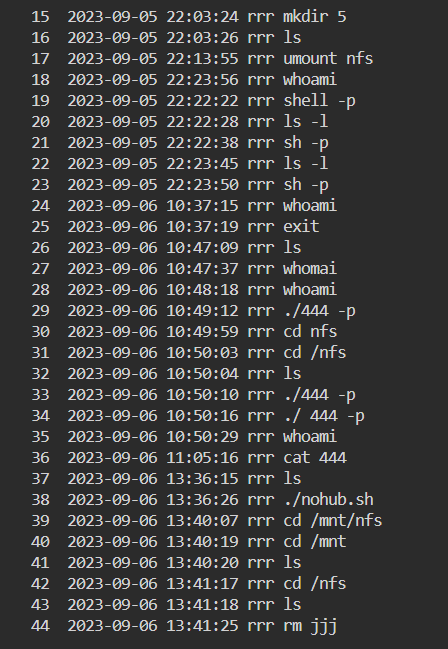 History (1)
History (1)
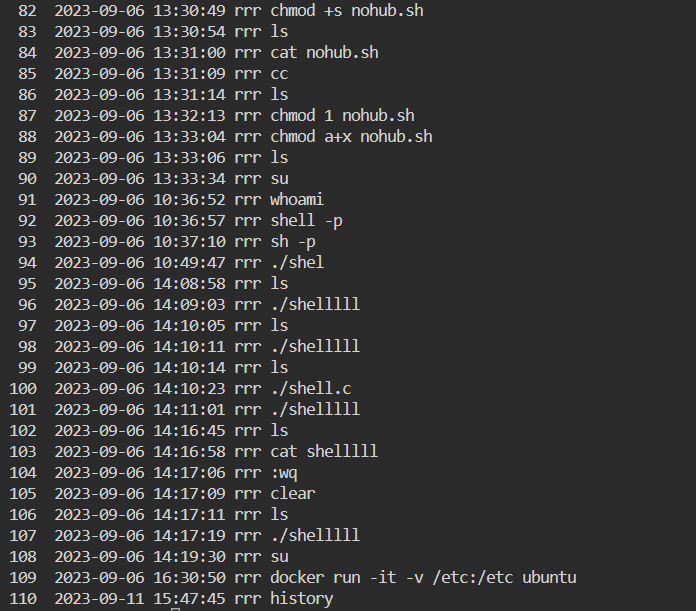 History (2)
History (2)
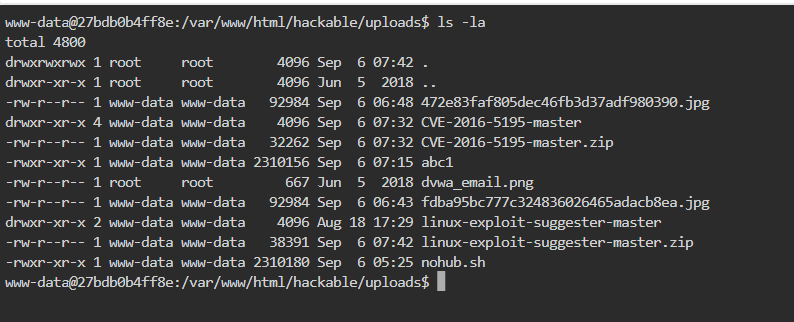
As can be seen from the screenshots, authorization escalation operations were performed to the “nohub.sh” file, and the bash file named “shelllll” was run. We changed the file directory path and detected the “nohub.sh” file in the folder named “hackable” in the “/var/www/html” folder.
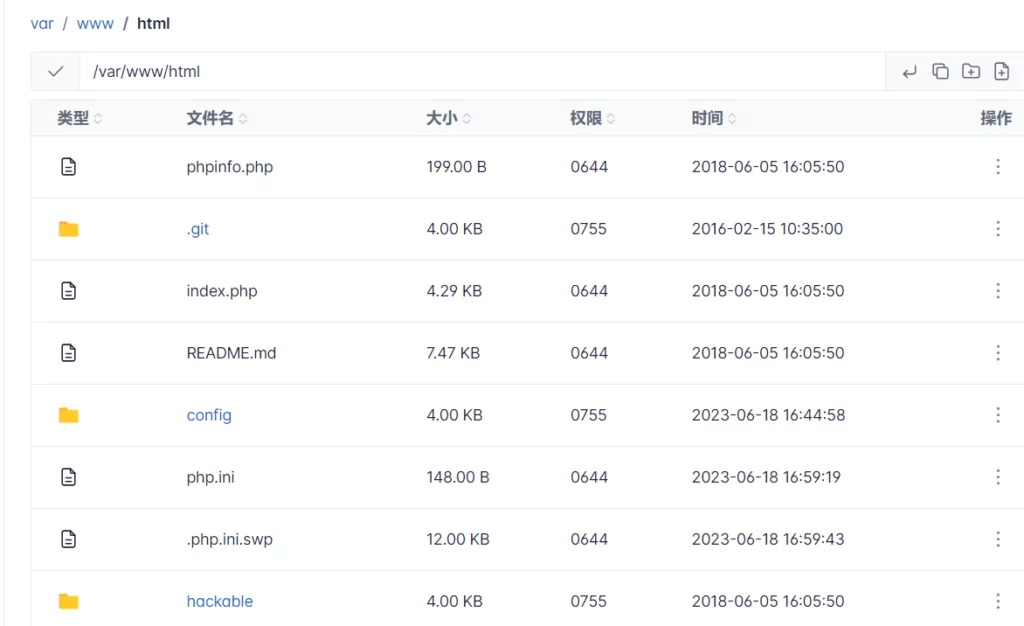 /var/www/html folder
/var/www/html folder
When we downloaded the “Index.php” file and examined the source codes, we came across the source codes of the “Damn Vulnerable Web Application” project, where you can study vulnerabilities and attack techniques.
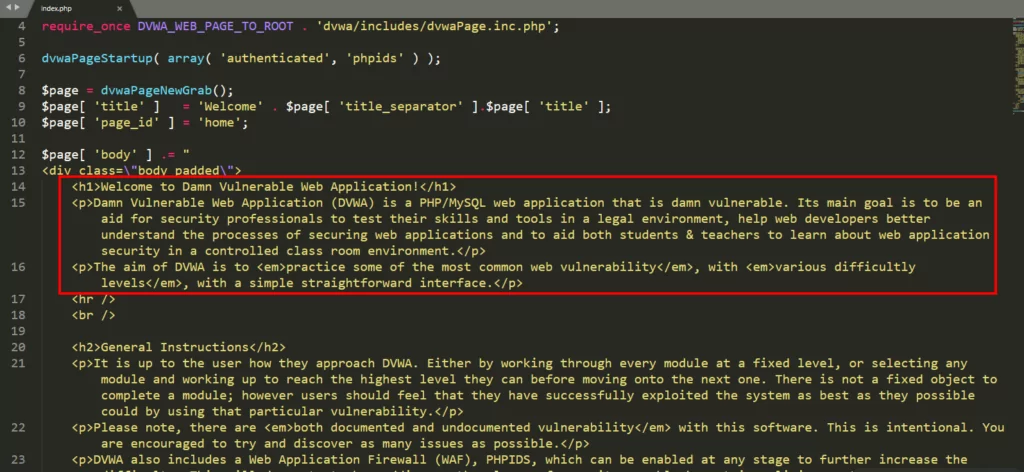 “Damn Vulnerable Web Application”
“Damn Vulnerable Web Application”
As a result of this result, we concluded that this infected system could be a honeypot. In the rest of our research, we tried to draw more statistical conclusions about threat actors and infected systems.
Implications For Threat Actors And Infected Systems
About the control panels we detected for the Supershell Botnet, we mentioned that we found 85 active panels in the last month, and we continue to examine these findings more closely. Let’s examine from which countries the control panels are managed.
|
Country Info |
|
|
10 COUNTRIES |
34 CITIES |
|
Worldwide |
85 IPs |
|
China |
36 IPs |
|
United States |
21 IPs |
|
Hong Kong |
11 IPs |
|
Japan |
6 IPs |
|
Singapore |
3 IPs |
|
Netherlands |
3 IPs |
|
France |
2 IPs |
|
India |
1 IP |
|
Thailand |
1 IP |
|
Taiwan |
1 IP |
We used the IPinfo service to examine the distribution of IP addresses belonging to the Supershell Botnet by country. In total, 10 different countries and 34 different cities were detected. The most detected country was China, and 36 IP addresses were seen from this country. The highest number of detections in China may be due to the fact that Supershell’s Github page is in Chinese.
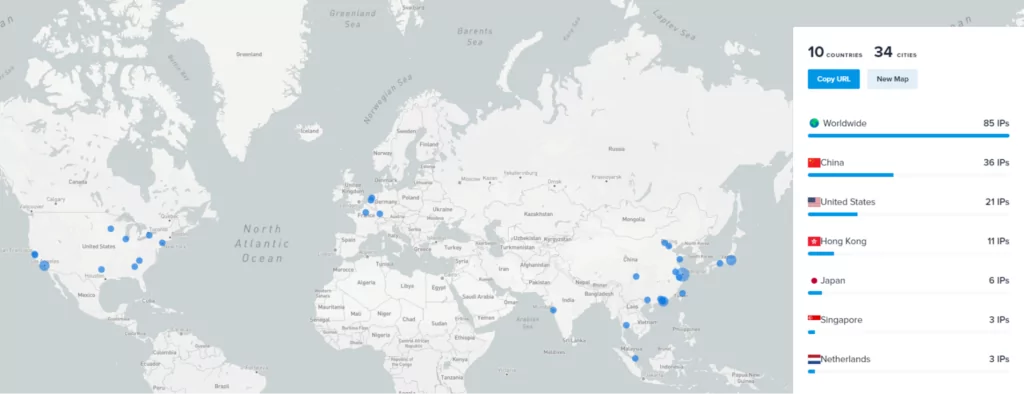 Distribution of IP addresses belonging to the Supershell Botnet
Distribution of IP addresses belonging to the Supershell Botnet
In our research for infected systems, we encounter a table in our IPinfo-based results for IP address information in Supershell Botnet panels.
|
Country Info |
|
|
12 COUNTRIES |
26 CITIES |
|
Worldwide |
41 IPs |
|
China |
10 IPs |
|
United States |
8 IPs |
|
Russia |
6 IPs |
|
Germany |
6 IPs |
|
Canada |
3 IPs |
|
Netherlands |
2 IPs |
|
Vietnam |
1 IP |
|
Czech Republic |
1 IP |
|
Sweden |
1 IP |
|
Italy |
1 IP |
|
Austria |
1 IP |
|
France |
1 IP |
From 85 active Supershell Botnet panels, the total number of infected systems in some panels we could log in to is 52, according to IP address information. When we examine the table above for the 52 infected systems we detected, we see 12 different countries and 26 different cities in total. The most infected system was detected in China, with 41 IP addresses.
Conclusion
Alongside the many advantages the digital age offers, cybersecurity is increasingly critical. Day by day, cyber threats are becoming more complex and sophisticated, and preparedness against these threats is becoming a priority for cybersecurity professionals and organizations. In this context, cyber attack tools, such as open-source botnets, are attracting particular attention in the cybersecurity world, and more importantly, cyber intelligence is also crucial for cybersecurity.
The use of open-source botnets raises new issues and challenges in cybersecurity. This paper aims to help us understand how such botnets work and what dangers they pose through the Supershell botnet. It also provides recommendations on how organizations can be prepared for such threats.
 SOCRadar Dark Web News
SOCRadar Dark Web News
As the SOCRadar XTI team, we constantly monitor the dark web for underground forums, Telegram channels, and addresses where open-source codes are shared to keep our customers at the highest level of cyber security and threat intelligence. In this way, we aim to identify potential dangers in advance and provide the necessary information to our customers.
The post The Future of Open-Source Botnets and Preparedness Against Threats: Supershell Botnet appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: https://socradar.io/the-future-of-open-source-botnets-and-preparedness-against-threats-supershell-botnet/
