Author: Kay Kyoung-ju Kwak
Kay Kyoung-ju Kwak is the Head of Center for Threat Research and Intelligence, Talon at S2W. He is an advisory member of Cybersecurity Alliance operated by Ministry of Science and ICT, as well as the technical advisor of Personal Information Protection Commission in South Korea.
 Photo by Geran de Klerk on Unsplash
Photo by Geran de Klerk on UnsplashIntroduction
Cyber Threat Intelligence (CTI) has become an essential component of every organization’s cybersecurity program, enabling them to gather and analyze data to gain insights into cyber threats to their assets and operations. This article provides a comprehensive overview of CTI, including its current state, future trends, and the importance of quality analysts for CTI. This article also explores how Attack Surface Management (ASM), Vulnerability Intelligence (VINT), and Account Takeover Monitoring (ATOM) can be integrated with CTI to provide a more comprehensive and proactive approach to managing an organization’s cybersecurity risk.
The Current State of Cyber Threat Intelligence
CTI has come a long way from its traditional manual data analysis methods to more advanced technologies such as artificial intelligence (AI) and machine learning (ML). However, CTI still faces challenges and limitations, such as the lack of data standardization and difficulty determining sources' credibility. To address these challenges, CTI analysts should focus on developing a better understanding of the available data sources and adopting a consistent data collection and analysis methodology.
 The Mindmap of Cyber Threat Intelligence
The Mindmap of Cyber Threat IntelligenceThe Future of Cyber Threat Intelligence
The future of CTI is expected to involve more advanced technologies and tools, such as predictive analytics and automation. In addition, CTI is predicted to be more tightly integrated with other security tools, such as security information and event management (SIEM) systems, to provide a more comprehensive view of the threat landscape. The emergence of new technologies, such as blockchain and quantum computing, will also significantly impact CTI in the future.
The importance of high-quality analysts still remains
Furthermore, the importance of quality analysts for CTI cannot be overstated. While advanced technologies such as AI and ML have enabled data collection and analysis automation, the human element is still crucial in CTI. High-quality analysts bring a range of skills and experience to CTI, such as understanding and interpreting complex data, identifying patterns and anomalies, and developing actionable insights. In addition, analysts with diverse backgrounds and perspectives can provide a more comprehensive understanding of the threat landscape, including emerging threats and attack methods.
In addition, high-quality analysts can provide context and relevance to threat intelligence, tailoring it to an organization's specific needs. They can work closely with internal stakeholders to understand the unique risks and challenges faced by the organization and develop customized threat intelligence and recommendations for action.
Utilization of Cyber Threat Intelligence
CTI plays a crucial role in both corporate and national security. CTI can provide insights into the latest malware/threat actor trends, threat conditions, vulnerabilities, attack surfaces, and data breaches to help organizations prevent and respond to potential and ongoing threats. CTI can also play a critical role in helping organizations understand the broader social and environmental impact of cyber threats. For example, CTI can provide valuable intelligence on expanding the cybercrime enabler market, such as the darkweb and telegram, and help organizations better understand the risks associated with these threats.
1) Account Takeover Monitoring (ATOM)
Account take-over monitoring is the process of tracking whether the usernames and passwords belonging to a company or its employees have been leaked online. This monitoring is important because stolen or leaked credentials are frequently used by cybercriminals to gain unauthorized access to company resources and data. If an attacker has access to a valid set of credentials, it can be much easier for them to carry out a successful cyber attack, such as phishing attacks, data theft, or other malicious activities.
The recent LAPSU$ hacking incident is a perfect example of the importance of credential leakage monitoring. In this case, the hackers were able to gain access to sensitive data and confidential information of major corporations by leveraging a massive database of leaked credentials.
To monitor for credential leakage, organizations can leverage a variety of tools and techniques. For example, they can subscribe to threat intelligence feeds that provide information on recent data breaches and leaks and use this information to identify any affected accounts within their organization. Additionally, organizations can use automated tools to scan the internet and dark web for mentions of their brand or domain along with associated credentials, including email addresses and passwords.
Organizations should ensure that they have a comprehensive and up-to-date inventory of all their systems and applications, along with associated user accounts and credentials. They should also ensure that employees are regularly trained on the importance of password hygiene and the risks associated with credential leakage.
To integrate credential leakage monitoring into a corporate environment, there are several steps that organizations can take:
- Identify the domains and email addresses that the organization uses to create accounts and manage its online services.
- Use a credential monitoring service to regularly scan the internet for exposed credentials that match the organization’s email addresses and domains.
- Configure alerts to notify security teams when matches are found, enabling them to take swift action to prevent attacks.
- Implement two-factor authentication (2FA) across all accounts to provide an additional layer of security beyond passwords.
- Train employees on best practices for creating and managing strong, unique passwords.
By proactively monitoring for credential leakage and implementing security measures such as MFA (Multifactor Authentication), organizations can significantly reduce the risk of credential-based attacks. It’s important to note that credential leakage monitoring is just one aspect of a comprehensive cybersecurity program and should be combined with other security measures such as regular vulnerability scans, employee training, and incident response planning to ensure that the organization is well-protected against cyber threats.
2) Vulnerability Intelligence (VINT)
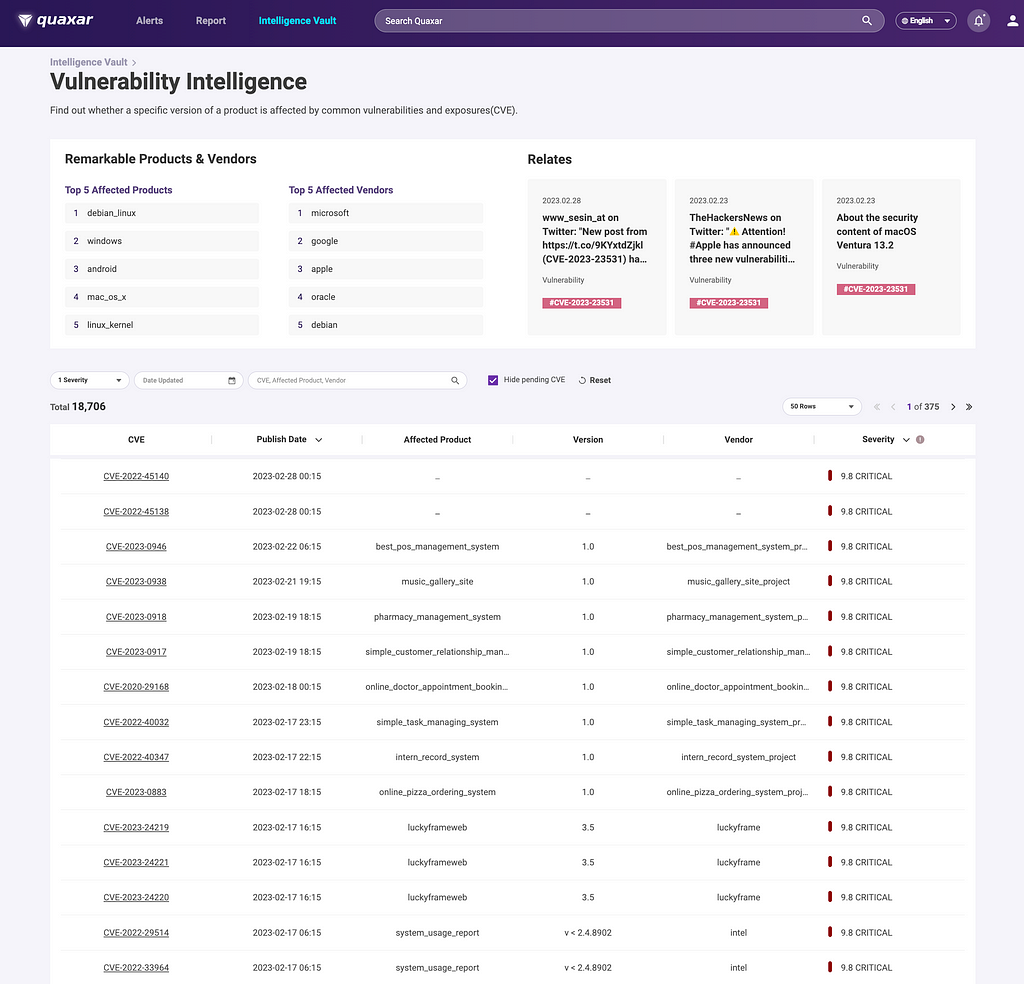 Vulnerability Intelligence of QuaXar
Vulnerability Intelligence of QuaXarCTI services are used for vulnerability intelligence because they can provide comprehensive and up-to-date information on the latest vulnerabilities and threats. CTI analysts leverage a wide range of data sources, including the dark web, deep web, social media, and other surface websites, to collect and analyze data about cyber threats.
When it comes to vulnerabilities, CTI services can provide a range of information, such as the Common Vulnerabilities and Exposures (CVE) identification numbers, which are unique identifiers for publicly known vulnerabilities. CTI services can also provide information on in-the-wild vulnerabilities, which are vulnerabilities that are being actively exploited by attackers.
In addition to identifying vulnerabilities, CTI services can also provide information on the severity of a vulnerability, typically expressed using the Common Vulnerability Scoring System (CVSS) or the Exploit Prediction Scoring System (EPSS). These scoring systems help organizations understand the potential impact of a vulnerability on their systems and prioritize remediation efforts.
Overall, the use of CTI services for vulnerability intelligence provides organizations with a more comprehensive and accurate view of the threat landscape. By leveraging the latest intelligence on vulnerabilities and threats, organizations can more effectively manage their cybersecurity risk and prioritize their security efforts to protect their assets and operations.
3) Attack Surface Management (ASM)
Attack Surface Management (ASM) is another critical area that CTI can play a role in. ASM involves identifying and monitoring an organization’s digital attack surface, including all systems, applications, and data that can be targeted by attackers. CTI can provide valuable insights into potential vulnerabilities in an organization’s attack surface, such as credential leakage, recent 1-day or 0-day vulnerabilities, and in-the-wild vulnerabilities revealed from recent incidents. By incorporating ASM into CTI, organizations can better understand their potential weaknesses and threats proactively.
In the upcoming article, we plan to provide further information and details about Attack Surface Management.
4) Attack Surface Management (ASM) with VINT + ATOM
By using ASM and Vulnerability Intelligence together, organizations can identify potential weaknesses in their digital attack surface and prioritize their remediation efforts based on the risk level of each vulnerability. This can help organizations manage their cybersecurity risk more effectively and ensure that their most critical assets are adequately protected.
Incorporating Account Takeover Monitoring (ATOM) services with ASM and Vulnerability Intelligence can further enhance an organization’s security posture. ATOM services can identify and alert organizations to compromised credentials, which can be used to gain unauthorized access to critical systems and data. By integrating ATOM services with ASM and Vulnerability Intelligence, organizations can proactively monitor their digital attack surface for signs of account takeover and quickly remediate any identified vulnerabilities or compromised accounts.
In terms of traditional ASM services, it depends on the specific service and its capabilities. Some traditional ASM services may provide similar capabilities to ASM and Vulnerability Intelligence, while others may be more limited in their scope or less effective in identifying potential vulnerabilities. Ultimately, the best approach will depend on each organization's specific needs and risk profile. However, integrating ASM, Vulnerability Intelligence, and ATOM services can provide a more comprehensive and proactive approach to managing an organization’s cybersecurity risk.
Integrating Attack Surface Management and Account Takeover Monitoring is a critical component of a comprehensive cybersecurity program. However, to ensure that these are effective, it is essential to have complete visibility into potential attack vectors, including covert channels such as the dark web, Telegram, Discord, and others.
These channels are often used by threat actors to communicate and exchange information about potential targets, vulnerabilities, and exploits. By monitoring these channels, organizations can gain valuable insights into emerging threats, as well as potential vulnerabilities in their own attack surface.
However, monitoring these channels can be challenging, as they are often highly encrypted and difficult to access. This is where the importance of data visibility comes into play.
Data visibility refers to the ability to see and understand all the data flowing through an organization’s networks and systems. This includes both internal and external data sources, such as social media, the dark web, and other covert channels. By having complete visibility into these sources, organizations can identify potential threats and vulnerabilities before they can be exploited by attackers.
For example, in the case of an account takeover, an attacker may use a covert channel to communicate with other threat actors and share information about compromised credentials. By monitoring these channels, organizations can detect the compromise and take proactive measures to prevent further damage.
Without having complete visibility into all potential attack vectors, this can include data breaches, financial losses, and reputational damage.
Additionally, there are tools and services available that can help organizations achieve complete data visibility. These tools can include threat intelligence services that provide access to a wide range of data sources, as well as advanced analytics and machine learning to identify potential threats and vulnerabilities.
Conclusion
Cyber Threat Intelligence (CTI) is vital to any organization’s cybersecurity program. CTI provides insights into the latest cyber threats and vulnerabilities and enables organizations to take proactive measures to prevent and respond to attacks. CTI has evolved significantly over the years, moving from traditional manual data analysis to more advanced technologies such as artificial intelligence (AI) and machine learning.
However, despite the progress made in CTI, it still faces challenges and limitations, such as the lack of data standardization and the difficulty in determining the credibility of sources. To overcome these challenges, organizations must invest in quality analysts with a diverse range of skills and experience who can provide comprehensive, relevant, and actionable threat intelligence.
In the future, CTI is expected to become more tightly integrated with other security tools, such as security information and event management (SIEM) systems, to provide a more comprehensive view of the threat landscape.
Incorporating Attack Surface Management (ASM) into CTI is another important area that can help organizations proactively understand their potential weaknesses and threats. Furthermore, ATOM services can identify and alert organizations to compromised credentials, which can be used to gain unauthorized access to critical systems and data. By integrating ATOM services with ASM and Vulnerability Intelligence, organizations can proactively monitor their digital attack surface for signs of account takeover and quickly remediate any identified vulnerabilities or compromised accounts. Additionally, Threat Intelligence can provide access to a wide range of data sources and advanced analytics and machine learning to identify potential threats and vulnerabilities.
To stay ahead of the ever-changing threat landscape, organizations must adapt to the latest technologies and tools. By leveraging actionable and insightful CTI, organizations can better protect themselves from cyber threats and ensure their continued success.

Homepage: https://s2w.inc
Facebook: https://www.facebook.com/S2WLAB
Twitter: https://twitter.com/S2W_Official
The Future of Cyber Threat Intelligence was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: The Future of Cyber Threat Intelligence | by S2W | S2W BLOG | Medium