In the realm of cybersecurity, the tools and techniques used to analyze and combat malware have undergone significant transformations. One of the most notable advancements in this field has been the evolution of sandboxing and malware analysis tools. This article delves into the journey of sandboxing, from its rudimentary beginnings to the sophisticated solutions available today. We will offer insights that will keep you informed and ahead in the field of malware analysis, detailing what you need to know to stay aligned with the forefront of innovations and best practices.
Sandboxing: A Transformative Journey
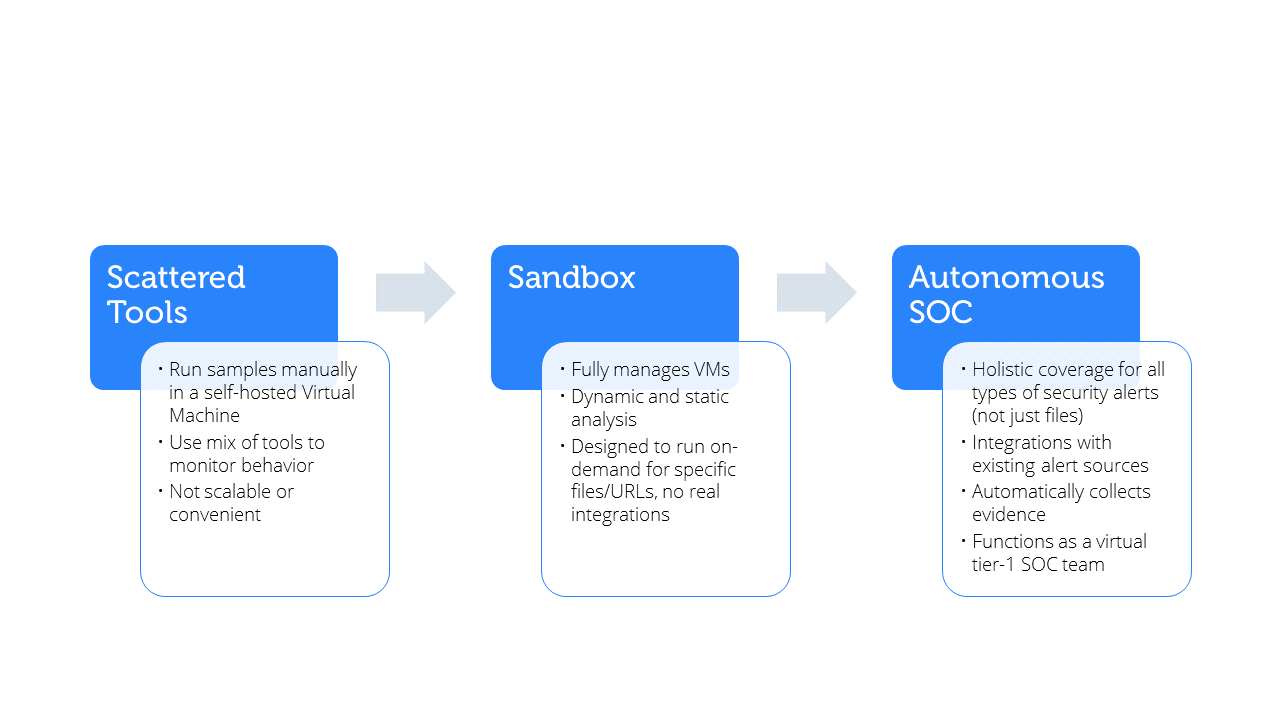
Before we delve deeper into the intricacies of each phase, let’s take a moment to overview the three pivotal stages that have shaped the trajectory of sandboxing and malware analysis:
- Scattered Tools Era: The initial phase where analysts manually operated within VMs, utilizing a mix of tools to monitor suspicious activities. It was a foundational step but lacked the efficiency and scalability required for comprehensive threat analysis.
- Sandboxes: A transformative period that introduced dedicated sandboxes, automating many processes and offering both dynamic and static analysis. While it revolutionized malware analysis, it also brought to light certain limitations, especially in terms of integration and handling diverse security alerts.
- The Dawn of the Autonomous SOC: The most advanced stage, where the focus shifted from mere analysis to holistic threat management. The Autonomous SOC integrates with existing security tools, triages a broader range of alerts, and truly functions as an extension of the security team, automating many previously manual tasks.
With this bird’s-eye view in mind, let’s dive deeper into each stage, exploring their contributions, challenges, and the innovations they spurred in the world of security operations.
Scattered Tools Era
In the early days, the process of malware analysis was largely manual and fragmented. Analysts would run suspicious files or URLs in a virtual machine (VM) and monitor their behavior using an assortment of tools, such as Sysinternals. While these tools provided valuable insights, the approach was far from ideal. It was cumbersome, lacked scalability, and was heavily reliant on the expertise of the analyst. The need for a more streamlined and automated solution was evident.
The Rise of Automated Analysis
Recognizing the limitations of scattered tools, the cybersecurity industry witnessed the emergence of dedicated sandboxes. These platforms, available both online and on-premise, automated the creation and reset of VMs, monitored malware behavior, and presented results in a user-friendly manner. Sandboxes brought with them the power of automated file detonation, dynamic and static analysis, making them indispensable tools for threat analysts.
However, as powerful as they were, sandboxes had their set of challenges. For one, they required skills that were often unavailable, especially among junior-level analysts. The results they provided, while detailed, were often vague and required interpretation. Moreover, they struggled with certain types of security alerts, such as fileless threats. Perhaps most critically, they weren’t inherently designed to integrate with existing security tools, making it challenging to fully automate the security alert triage process.
The Dawn of the Autonomous SOC
The limitations of traditional sandboxes paved the way for the next evolutionary step: the Autonomous Security Operations Center (SOC). This advanced solution integrated seamlessly with existing security tools, offering a holistic approach to threat analysis. Unlike its predecessors, the Autonomous SOC was equipped to triage alerts, not just files. It automated evidence collection, could analyze fileless alerts, and functioned as a decision-maker, truly serving as an extension of the security team. By automating many of the tasks that were previously manual, the Autonomous SOC allowed organizations to “automate-out” Tier 1, streamlining operations and enhancing efficiency.
However, it’s essential to note that while sandboxes have always played a role as decision-making assistants for security analysts, they never truly achieved the status of a standalone decision-maker capable of automating alert triage. This limitation meant that many organizations still found themselves reliant on outsourcing their Tier-1 operations to Managed Detection and Response (MDR) services or other external providers. The Autonomous SOC, with its enhanced capabilities, aims to bridge this gap, offering a more integrated and autonomous approach to threat management.
Intezer’s Role in the Evolution
From its inception, Intezer emerged as an innovator in the realm of malware analysis. The introduction of its Genetic Analysis technology marked a significant leap, not only enhancing the classification of threats but also lowering the bar-to-entry for organizations and individuals to conduct in-depth threat analysis. This innovation empowered a broader spectrum of users to delve into meaningful threat investigations without the need for extensive expertise.
In the recent year, Intezer has further expanded its horizons by positioning itself at the forefront of the Autonomous SOC revolution. Recognizing the industry’s challenges, especially the resource and talent shortages faced by many companies, Intezer has been instrumental in offering solutions that address these gaps. By integrating advanced automation and intelligence into their platform, Intezer aids organizations in optimizing their security operations, ensuring they can effectively respond to threats even with limited resources and expertise. Read more about the difference today between Intezer and traditional sandboxes.
 A Crowdstrike alert triaged by Intezer that includes several pieces of evidence that were collected, both a file and a memory scan, in order to complete the triage assessment
A Crowdstrike alert triaged by Intezer that includes several pieces of evidence that were collected, both a file and a memory scan, in order to complete the triage assessment
—
Join the Revolution
In the ever-evolving domain of cybersecurity, staying ahead of the curve is essential. At Intezer, we’ve dedicated ourselves to ensuring that transitioning to an Autonomous SOC is as seamless as possible. Our focus has been on refining the product experience and offering flexible commercial terms to facilitate easy onboarding.
For organizations currently utilizing a Sandbox or contemplating its acquisition, we strongly advocate considering an upgrade to an Autonomous SOC. Doing so not only positions you at the forefront of security operations but also addresses a prevalent challenge in the industry: the shortage of resources. Talk to our team to hear more about how you can leverage the power of Autonomous SOC for your team.
The post The Evolution of Sandboxing appeared first on Intezer.
Article Link: The Evolution of Sandboxing