I tested the level of account security of 10 different IP security cameras I found on Amazon’s “hot new releases” and “best sellers” categories
Introduction
When the COVID-19 pandemic spread across Europe, I, like many others, was forced to work from home. While at home, I tried to find things I could easily research from home. I wanted to focus on something that doesn’t require physical ownership of a device. An idea came to my mind: the security of IP cameras with cloud connection. I narrowed my focus on the account security of these IP cameras.
In December of 2019, an article was published on Vice about how a journalist’s colleague hacked an Amazon Ring security camera, the journalist described the camera’s poor account security at the time. Fast forward a few months later – I was curious how other smart camera vendors reacted to the news and if they introduced some best practices that would protect their users’ accounts from a brute force attack.
So, in May and June 2020, I decided to check if the apps that accompany smart cameras include a two-factor authentication option, send the owner a notification that someone has attempted to log in or has successfully logged in from a new device, especially if the login attempts came from a device appearing to be on the opposite side of the world?
Methodology
I chose 10 different IP security cameras (each from a different vendor and using a different accompanying app to connect to it) with cloud functionality that I found on Amazon’s “hot new releases” and “best sellers” categories.
I didn’t actually purchase the cameras, but instead, I downloaded the apps used to connect and control them. I came up with a fictional person I named “Walter Duchesne” and created a Google Account for Walter. I installed the apps for the 10 cameras on my phone and created accounts for Walter. After successfully logging in, I checked for an option to change the accounts’ password and set up two-factor authentication for the accounts.
I then used a second phone with a VPN app to connect to a server in China, so that the communication from the second device would go through that server and thus anything being sent from the device would appear to be coming from a device located in China.
I purposely attempted to log in to Walter’s account using the second device connected to the VPN. I used wrong passwords more than 10 times to see if any kind of brute force attempts would be detected by the apps. After that, I used the correct login credentials to log in to Walter’s account to see if he received a notification about a new login from a different device and location. Following this, I checked if the traffic between the app and the manufacturer’s server was encrypted. You can find the results of this small research in the table:
| Name of IP Camera App | # of app downloads (Google Play) | One time password (OTP) | Brute force Protection | New device notification | Password restrictions |
| Blink | 1M+ | Via email (only to add new device) | Yes | Yes (OTP required, sent per email) | None |
| Wyze | 1M+ | Text message/authentication app (user has to enter code to activate) | Yes (user not notified of attempts) | No | None |
| YI IOT | 100K+ | No | No | Yes (user receives notification with every new login) | Max length of 16 characters |
| YI Home | 1M+ | No | No | Yes (user receives notification with every new login) | Max length of 16 characters |
| Wansview Cloud | 100K+ | No | No | No | Max length of 16 characters |
| MIPC | 500K+ | No | No | No | None |
| Jawa | 50K+ | No | No | No | None |
| CloudEdge | 100K | No | No | No | Max length of 20 characters |
| Amcrest Cloud | 50K+ | No | No | No | None |
| iCSee | 1M+ | No | No | No | Max length of 32 characters |
Results
When I started with my research, I thought the level of account security would be different for all of the apps, but the reality is a little bit different. I observed only two levels. One where a one time password would be required to sign in from a new device and the other, where there are no protective measures whatsoever. Of course I’m exaggerating a little, luckily all of the apps use encryption when communicating with the cloud and all of them require the user to set up login credentials to gain access to their accounts, but not all of them require strong, complex passwords, nor do they provide any kind of notification or brute force protection. You may ask, why are the notifications so important. They are crucial in cases such a password leakage or brute-forcing of credentials. I was able to try to log in more than 10 times on almost all of the apps, details below.
The Good, the bad and the ugly
Of the ten apps I looked at, only two had what I would consider an acceptable level of account security measures. What I was hoping all of the apps would have was some kind of two-factor authentication (preferably via an authenticator app), no set minimum for password length (some of the apps restricted the password length to 16 characters), and notifications notifying the user of logins from new devices or from unknown locations.
The two applications that provided the best basic account security out of the ten I looked at were Blink and Wyze. Blink requires users to enter a one time password to add a new device, a one time password to change the account password, notifies users of brute force attempts, and notifies users when a login was made using a new device. Wyze fared well thanks to offering two-factor authentication, while not set by default, but at least allowing the user to chose to have the authentication code sent via text message or authenticator app, which eliminates the risk of anyone gaining access should the email account used for the account be compromised. Wyze also notifies the user if too many login attempts were made, not the user of the account, but the user attempting to login.
Taking a closer look at the 10 apps
Blink
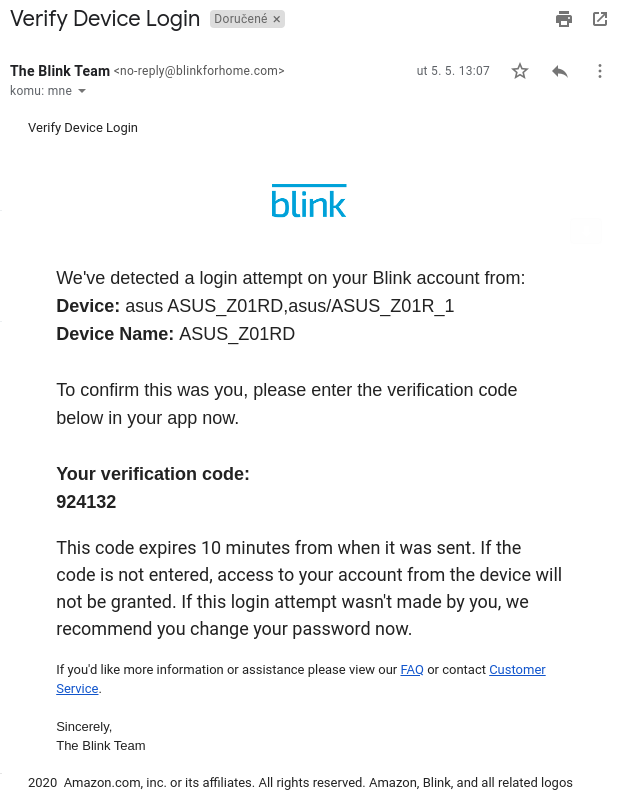
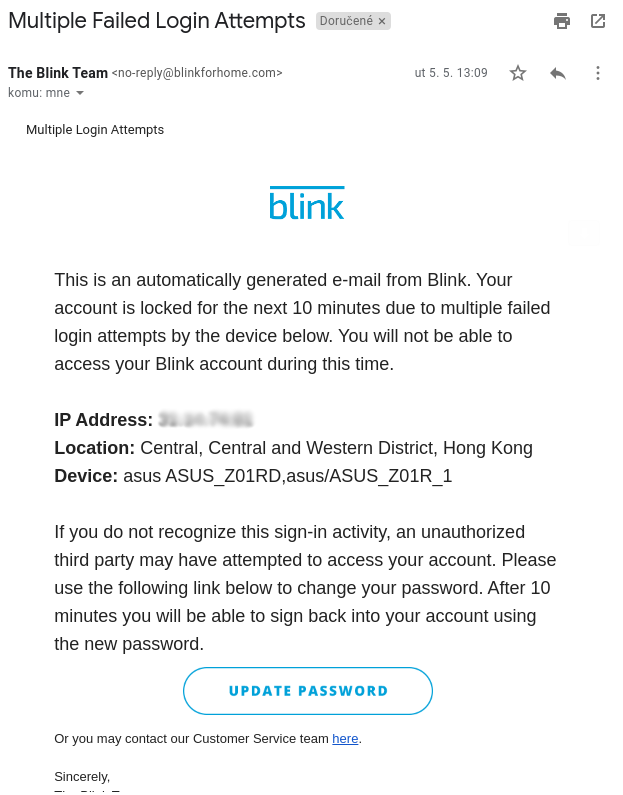
Blink is owned by Amazon and we can definitely see that the Ring incident had an impact in terms of how they handle account security. To log in on a new device, users have to authorize the new login with a one time password sent to their email address. After too many unsuccessful login attempts, new attempts are denied and the user is notified via email.
- Verification code for new device
- Brute force notification
This is almost what I was looking for, the only thing I would like to see is another way of getting the one time password, not just via email. If a password was included in a data breach including login details, there is a chance that the user used the same password for their email account and their Blink account and thus the one-time password could be intercepted by an attacker. On top of that, a one time password sent to the user’s email is needed in order to change the account’s password.
Wyze
The second app that did fairly well in terms of account security was Wyze. The app protects accounts from brute force attacks, but it does not notify the user that too many login attempts were made, but instead notifies the person attempting to login that there were too many failed attempts to login.
Wyze supports two-factor authentication either via text message or an authenticator app, but it is not enabled by default. If a login attempt is made on an account without two-factor authentication enabled, the user isn’t notified. I strongly recommend turning on two-factor authentication to anyone who owns a Wyze camera and hasn’t done so yet. The downside to the app is that it does not notify the user of a new device login, only doing so indirectly, if the user has two-factor authentication enabled.
Wyze 2FA setup process
YI IoT
This app is most controversial for me. On one hand, there are notifications about login from different devices, on the other hand it was not very easy to spot where I could change the account password (I had to click on the profile picture to get to the settings), and the password length was limited to a length to max. 16 characters, which is very unfortunate.
YI Home
YI Home is from the same developer as YI IoT. The only difference is in design. I noticed that notifications around new device logins sometimes arrived with delay or were not shown at all, which may have been caused by network issues.
- YI IoT
- YI Home
Wansview Cloud
This app doesn’t have any kind of protection when it comes to account security. Similarly to YI Home and YI IoT, Wansview Cloud puts a limit on the maximum length of passwords, allowing passwords to only be up to 16 characters long. The only way a user may detect that someone else is connected to the app is when they are kicked out of their login due to the new login on a different device, because the app doesn’t allow concurrent connections. A better option in my opinion, would be to notify account users of new account logins, but allow concurrent connections for multiple users to control the camera.
- UI
- Max 16 characters for password
MIPC
MIPC provides no brute force protection or notifications. The password reset procedure is transmitted over HTTP, meaning it is unencrypted and can be intercepted.
Jawa
Jawa is a perfect example of an app whose account security falls in the middle, I would say. It doesn’t offer two-factor authentication, notifications around new logins nor brute force protection, but at least it doesn’t imply restrictive rules on password length and the password reset procedure is reasonable – it’s done over HTTPS, and a one-time code sent via email is required.
- UI
- Max 40 characters password
CloudEdge
A nice feature of this app is that if users change or reset their password they need to use a one time password sent to their email in order to do so. Passwords are restricted to 20 characters, which is not as bad as 16, but nevertheless unlimited characters would be better. The app does not provide any protection against brute-force attack attempts, does not notify users of new device logins, nor does it offer two factor authentication for logins.
Amcrest Cloud
Similar to the Jawa app, this app doesn’t provide users the option to use two-factor authentication or notifications around new logins. On a positive note, the app allows passwords to be more than 60 characters long and requires users to enter a one time password sent to their email if they want to reset their password.
- More than 60 character password
- Password reset procedure
iCSee
Like the Amcrest Cloud app, iCSee’s only notable account security measures are a restricting password lengths to 32 characters, which isn’t as good as the 60 character restriction in the Amcrest app or the unlimited number of characters Jawa users can set their password to, but better than most of the apps we looked at.
- Change password procedure, no OTP needed
- Password reset procedure
Recommendations
When considering purchasing a cloud-connected IP camera to use in a home or office space, it’s important to not only look into how often the device receives software updates, for example, but the level of account security the accompanying app provides. Ideally, an app should offer two-factor authentication (preferably via an authenticator app), no set maximum for password length (some of the apps restricted the password length to 16 or 20 characters), and notifications letting users know of logins from new devices or from new locations.
DIY
If while looking for a camera, you want to check the accompanying app’s account security you can do what we did too!
You’ll need two phones, one with a VPN (we recommend Avast SecureLine VPN  ) that allows you to choose a server to connect to, that is in a different city than where you are and you’ll need to take the following steps:
) that allows you to choose a server to connect to, that is in a different city than where you are and you’ll need to take the following steps:
- Download and install the app you want to test
- Create account for that app
- On the second phone, turn on the VPN and connect to a server located in a different city or ideally country than your own location
- Install the same app from step one on second phone
- Try to log in to the app on the second phone using a wrong password, repeat this step as fast as possible using different incorrect passwords each time (> 10x).
- Check the notifications shown by the app installed on the original phone and emails to the address associated with the account. Were you notified of the attempts? Were you blocked from further attempts by the app on the second phone?
- Log in to the app on the second phone with the correct password.
- Check if you get a notification about login from another device and location on the original phone.
- On either phone, check the app’s settings, to see how you can change the account password, if there are any options for notifications and to enable two-factor authentication. At this stage, I would suggest also checking how intuitive the app is and the app’s features to see if they include everything you’re looking for.
The post Testing IP Camera Account Security appeared first on Avast Threat Labs.