In a recent update, a well-known and notorious threat actor declared their targeting of Telegram. This group initiated the attack after Telegram’s decision to ban their primary account on the messaging platform.
The actor in question is Anonymous Sudan, renowned for their distributed denial-of-service (DDoS) attacks, primarily motivated by political and religious causes. While this attack on Telegram does not appear to stem from a political or religious dispute, it seems to be a retaliatory action following the banning of their main channel, or to simply get Telegram’s attention.
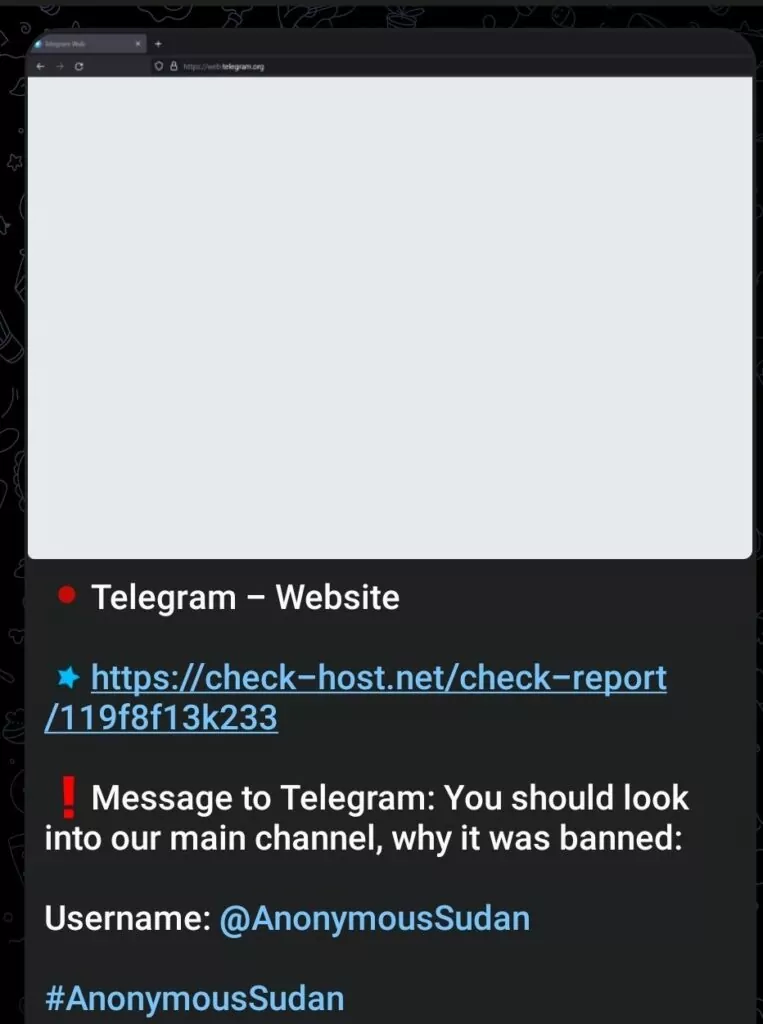 Telegram was downed. (Source)
Telegram was downed. (Source)
Why Did Telegram Ban the Threat Actor?
The threat actor moved their main Telegram channel for the time being. Telegram has long been a favored platform for threat actors due to its robust privacy features. Even after being banned, it appears no threat actor can resist using Telegram for their operations and communication.
Telegram had not provided a specific reason for banning their channel; however, an examination of the channel’s activities prior to the ban suggests that the ban was likely a response to the use of bot accounts.
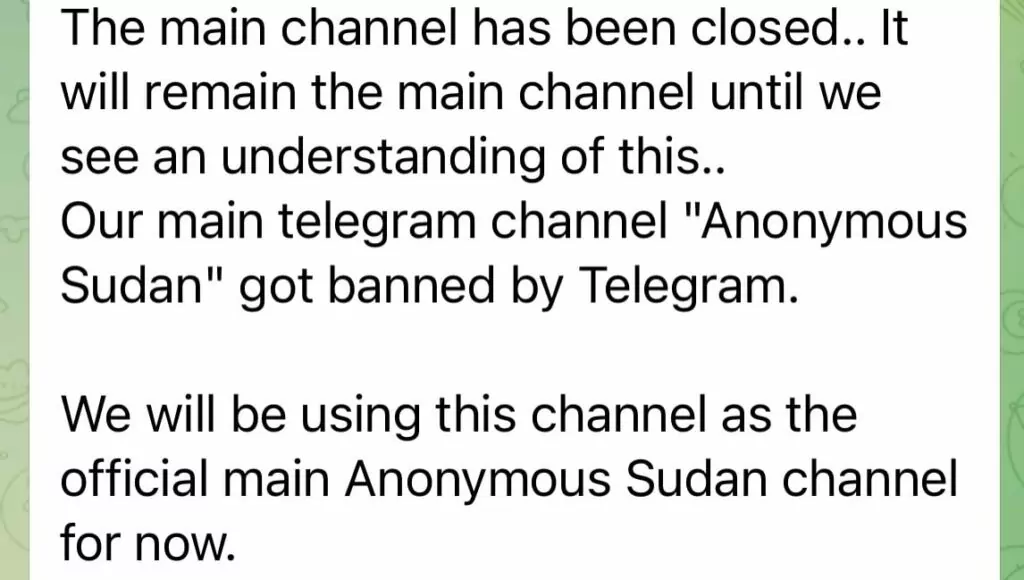 Statement by the threat actor (Source)
Statement by the threat actor (Source)
The bot accounts were used to inflate the channel’s user count. Anonymous Sudan’s Telegram channel had approximately 120,000 users, and the ban may have been enacted due to spam.
Could the Twitter Attack Also Be a Factor?
The threat group disrupted X, formerly known as Twitter on August 29, aiming to pressure Elon Musk into launching the Starlink service in their country.
X remained inaccessible for over two hours as the hackers posted on Telegram, urging Elon Musk to “Open Starlink in Sudan.”
 X (Twitter) was downed (Source)
X (Twitter) was downed (Source)
While bot accounts remain the prime suspect for their channel’s ban, the exact reason remains officially undisclosed. Could their attack on X also have played a role in their banishment?
The Rise of Modified Telegram Versions and the Impending Threat
Another recent concern associated with Telegram is the proliferation of seemingly legitimate yet counterfeit versions of the app, hiding among other modified versions.
Users often develop modified versions of Telegram, including additional features and customizations to enhance their messaging experience. Modified Telegram versions are readily available in official app stores and receive support from Telegram itself. However, they carry a significant risk.
Another popular messaging app, WhatsApp, actively combats such modified versions to uphold a secure environment for its users. In the case of Telegram, the encouragement of mod development introduces the risk of various forms of malware.
Recently, Kaspersky researchers uncovered multiple infected apps on Google Play, masquerading as Uyghur, Simplified Chinese, and Traditional Chinese versions of Telegram.
These trojanized versions closely mimic the official Telegram’s descriptions and endeavor. Furthermore, they claim superior speed to persuade users, attributing it to a distributed network of global data centers.
These apps conceal an additional module which continuously monitors Telegram activities, operating as a spyware. It sends gathered data to the threat actor’s command and control (C2) server, including contacts, sent and received messages with attached files, chat names, and the account owner’s name and phone number.
For a detailed analysis of these infected Telegram apps and associated indicators of compromise (IoCs), refer to Kaspersky.
Proactive Threat Mitigation with SOCRadar
SOCRadar actively monitors the latest activities of threat actors and malware to profile their Tactics, Techniques, and Procedures (TTPs), Indicators of Compromise (IoCs), targets, and other crucial information.
Empowered by the Threat Actor Tracking module, the platform equips you to proactively thwart malicious intentions by staying ahead of the curve with timely intelligence. Additionally, through the Dark Web Monitoring feature, SOCRadar provides notifications for critical discussions occurring in deep and dark web forums, and communication channels like Telegram.
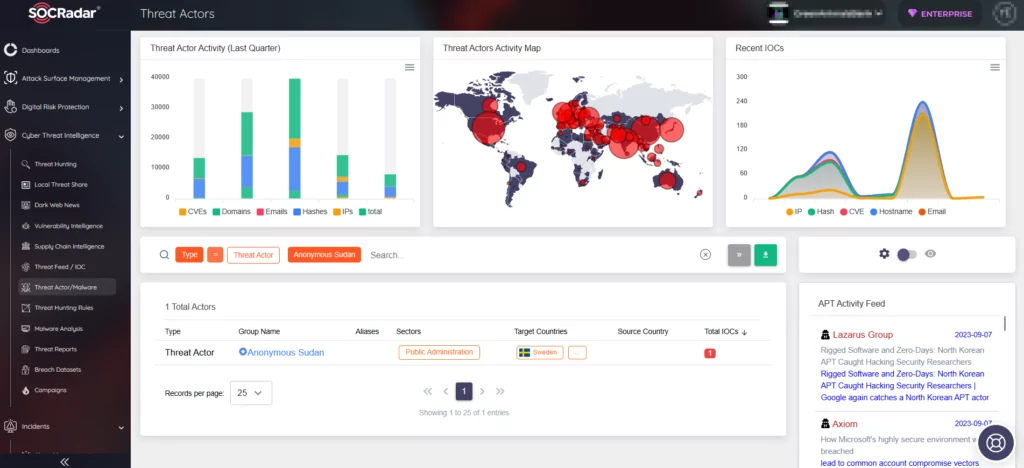 SOCRadar Cyber Threat Intelligence/Threat Actors
SOCRadar Cyber Threat Intelligence/Threat Actors
Sign up for the Free Edition to unlock the complete potential of SOCRadar in safeguarding your online presence.
The post Telegram Hit by a DDoS Attack: What Is the Cause Behind It? appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: Telegram Hit by a DDoS Attack: What Is the Cause Behind It?
