In recent cyber news, a critical security flaw has been unearthed in JetBrains TeamCity. With the trend of growing software vulnerabilities, it is essential for organizations to stay ahead of potential threats. This vulnerability, identified as CVE-2023-42793, has caught the attention of the cybersecurity community due to its severity and potential impact.
This flaw was initially discovered and reported by the adept team at Sonar. For those unfamiliar with TeamCity, it is a product from JetBrains and serves as a robust solution for continuous integration and deployment (CI/CD). Yet, like all software, it’s not immune to vulnerabilities.
Details of the Vulnerability
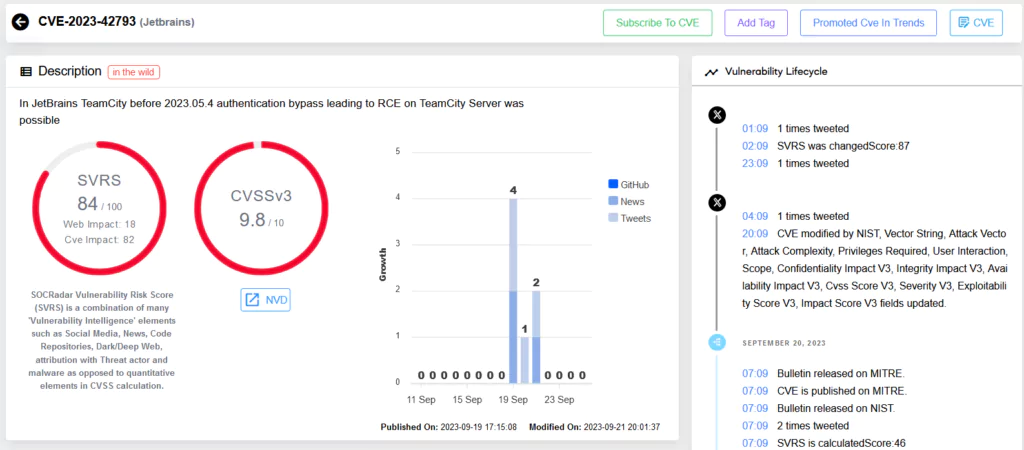
Vulnerability Intelligence page for CVE-2023-42793 in SOCRadar Platform.
The criticality of this flaw lies in its potential. It allows an unauthenticated attacker with HTTP(S) access to a TeamCity server to bypass authentication. This bypass paves the way for a remote code execution (RCE) attack, allowing attackers to gain administrative control of the TeamCity server. The gravity of this vulnerability is reflected in its CVSS score of 9.8, indicating its high-risk nature.
Affected Versions and Mitigations
All on-premises versions of TeamCity are susceptible to this vulnerability. Thankfully, JetBrains acted promptly, releasing a fix in version 2023.05.4. It’s crucial for organizations using TeamCity On-Premises to upgrade their servers to this version, ensuring the security of their systems.
However, JetBrains has provided a security patch plugin in scenarios where an immediate upgrade isn’t feasible. This plugin, compatible with TeamCity 8.0 and above, specifically targets and patches the RCE vulnerability. But it’s worth noting that this is a temporary fix. Upgrading the server to the latest version is recommended for a holistic security solution.
Safety First: Precautionary Measures
For servers that are publicly accessible, if upgrading or applying the patch isn’t immediately feasible, a best practice would be to temporarily restrict its accessibility. This would be prudent to prevent potential exploitation until mitigation measures are in place.
No Known Exploits in the Wild
It’s essential for TeamCity users and administrators to understand the nature of this discovered vulnerability. While the security flaw is significant, as of the information provided, there’s no evidence suggesting an active exploit in the wild targeting this specific vulnerability. In other words, while the potential impact of the flaw is profound, no malicious actors have been reported to be actively exploiting it.
However, it’s worth noting that the absence of a known exploit does not diminish the urgency to apply the recommended security measures. History has shown that once a vulnerability becomes public knowledge, it’s only a matter of time before potential threats emerge. It remains a best practice to ensure that software, especially those critical to operations, is updated to the latest secure versions. Proactive steps today can save a lot of reactive efforts in the future.
Impact of the Vulnerability
TeamCity servers running version 2023.05.3 and earlier are vulnerable to a severe authentication bypass flaw. If taken advantage of, this vulnerability allows an unauthenticated attacker to execute code remotely (RCE) on the vulnerable server. The potential repercussions of such an intrusion are extensive:
Theft of Proprietary Code: Threat actors could access and exfiltrate the source code stored on the server.
Exposure of Sensitive Data: Critical data, such as service secrets and private keys, are at risk of unauthorized access and potential misuse.
Tampering with Software Integrity: With the capability to manipulate the build process, attackers can introduce malicious alterations. This jeopardizes the authenticity of software releases and introduces risks to all users reliant on the software.
What heightens the severity of this flaw is the absence of a need for any user interaction for its exploitation. Even though full technical details are not publicly available now, the significance of taking immediate action to address this vulnerability cannot be emphasized enough. The ease with which this vulnerability can be exploited without requiring a valid account on the target server heightens concerns about potential misuse in the wild.
It is imperative for all TeamCity users to urgently apply the patch provided by JetBrains. The release that addresses this vulnerability is TeamCity version 2023.05.4. Additionally, it’s worth noting that TeamCity Cloud is not impacted by this particular security issue.No Known Exploits in the Wild
Reproduction of the Vulnerability by PT Swarm
The cybersecurity team at PT Swarm (Positive Technologies Offensive Team) demonstrated the severity of the TeamCity vulnerability through a proof-of-concept (PoC) video shared on Twitter. Although the entire process was not disclosed in detail, the video effectively highlighted the potential damage of the flaw.
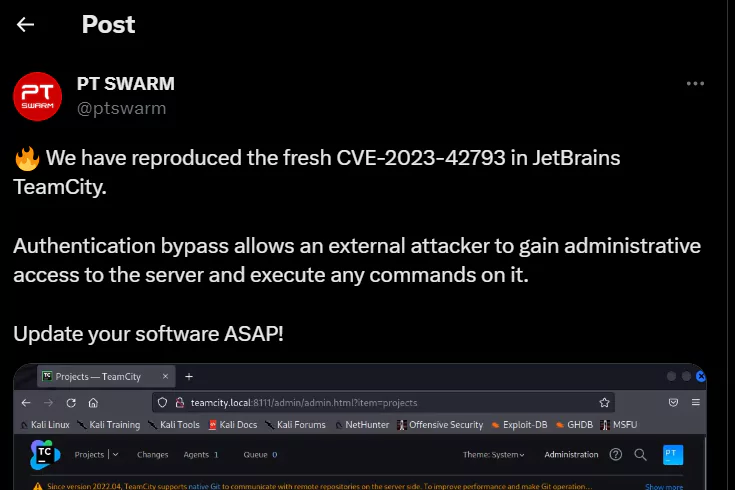 PT Swarm`s reproduction of the vulnerability.
PT Swarm`s reproduction of the vulnerability.
In their demonstration, PT Swarm was able to:
Add a New User: The vulnerability allowed them to effortlessly add a new user to the TeamCity environment. Given that the system is primarily designed to manage and control software development tasks, adding unauthorized users poses a significant risk.
Define New Jobs: Once the unauthorized user was created, the team showcased the capability of this user to create and define new tasks or “jobs” within TeamCity.
Execute Shell Commands through Building Steps: The gravest revelation was the ability of the created jobs to execute shell commands. This opens the door for a remote code execution (RCE) attack. Such an attack can have devastating consequences, especially when considering the pivotal role TeamCity plays in software development pipelines.
It’s worth noting that JetBrains’ blog post indirectly supports this theory. They have highlighted a severe authentication problem in TeamCity, which aligns with PT Swarm’s findings.
It’s essential to understand that PT Swarm’s reproduction underscores the vulnerability’s critical nature. All TeamCity users should take heed and ensure their systems are updated to the latest secure version or apply necessary patches to mitigate this risk.
The Larger Picture: SOCRadar Vulnerability Intelligence
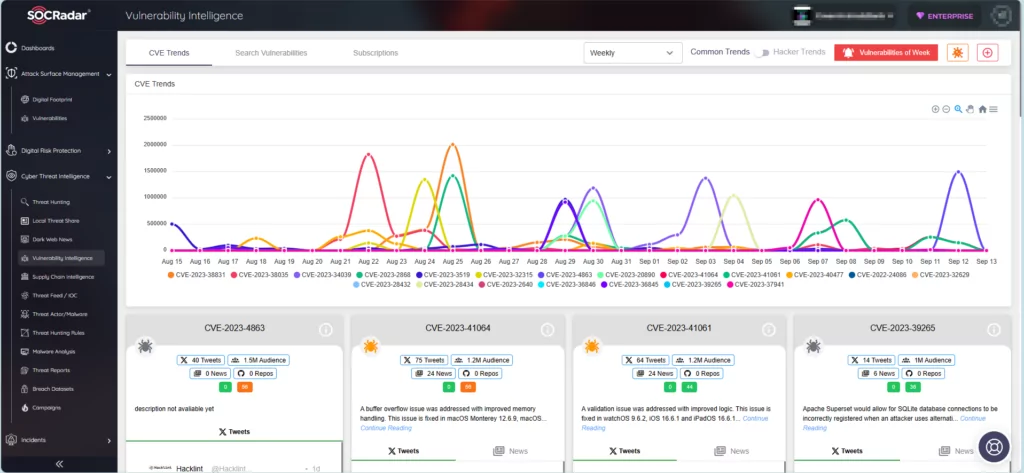 Vulnerability Intelligence module of SOCRadar Platform.
Vulnerability Intelligence module of SOCRadar Platform.
The discovery of such vulnerabilities underscores the importance of proactive cybersecurity measures. Tools like SOCRadar’s Vulnerability Intelligence can serve as the first line of defense, providing real-time insights into emerging threats. By staying informed, organizations can take timely action, ensuring their infrastructure remains secure.
Conclusion
The digital landscape is ever-evolving, with new vulnerabilities emerging daily. Staying ahead requires diligence, swift action, and the right tools. With platforms like SOCRadar’s Vulnerability Intelligence, organizations are better equipped to face these challenges head-on, ensuring a safer digital future for all.
The post TeamCity Authentication Bypass Flaw: CVE-2023-42793 appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: TeamCity Authentication Bypass Flaw: CVE-2023-42793
