Containers have revolutionized development in the cloud, allowing dev teams to work with unprecedented speed, efficiency, and scale. But securing containers at that speed and scale can be a thorny problem.
The infrastructure of containers is complex and contains multiple attack vectors, and most enterprises don’t have the time or resources to secure all attack vectors for all containers. This is exacerbated by how short-lived most containers are — Sysdig’s latest research has found that 70% of containers exist for less than five minutes.
Essentially, containers are a growing risk for the organizations that use them, and companies need new security measures in place to account for that risk. To that end, analyst firm GigaOm has released a report assessing key container security vendors, so organizations can make an informed decision on which solution is right for them.
“Here’s a small bit of advice: we know most organizations are not currently doing comprehensive container security,” GigaOm writes. “We advise that a solution be chosen and implemented, the sooner the better.”
Want to learn more on how to choose a container security solution — and why Sysdig’s rate of innovation and breadth of features earned us an Outperformer designation and a place in the Leaders circle? Check out the full report from GigaOm, or read on for a summary of the most important points.
<div>
</div>
<div>
<a href="https://go.sysdig.com/GigaOm-Container-Report.html" rel="noreferrer" target="_blank">Read the Report</a> </div>
The many approaches to container security
To select a container security vendor, you’ll first want to have a clear picture of what your organization needs, and what features may be a higher or lower priority. This will look different for each organization, but there are some broad generalizations that can be made depending on a company’s size. Small-to-medium businesses may want to prioritize ease of use and deployment in container security solutions. By contrast, large enterprises need solutions that focus on flexibility, performance, data services, and scalability.
Your organization’s industry may also determine some of your container security needs. Public sector organizations should look for solutions that excel in compliance and security, as they likely have strict security requirements they must meet. Service providers will want solutions that can support multiple clients, with an emphasis on flexibility, performance, data segregation, and features to improve security and data protection.
Finally, you’ll want to determine what deployment model best fits your organization. There are four primary models used for container security solutions: virtual machine or container image, public cloud image, software as a service, and software. Each has its own pros and cons, as detailed in GigaOm’s report, so make sure you’ve familiarized yourself with your options.
How to compare container security vendors
In their report, GigaOm assessed each container security solution based on key capabilities (including runtime drift detection and response, registry scanning or monitoring, and network isolation), business evaluation metrics, and ability to integrate emerging technologies.
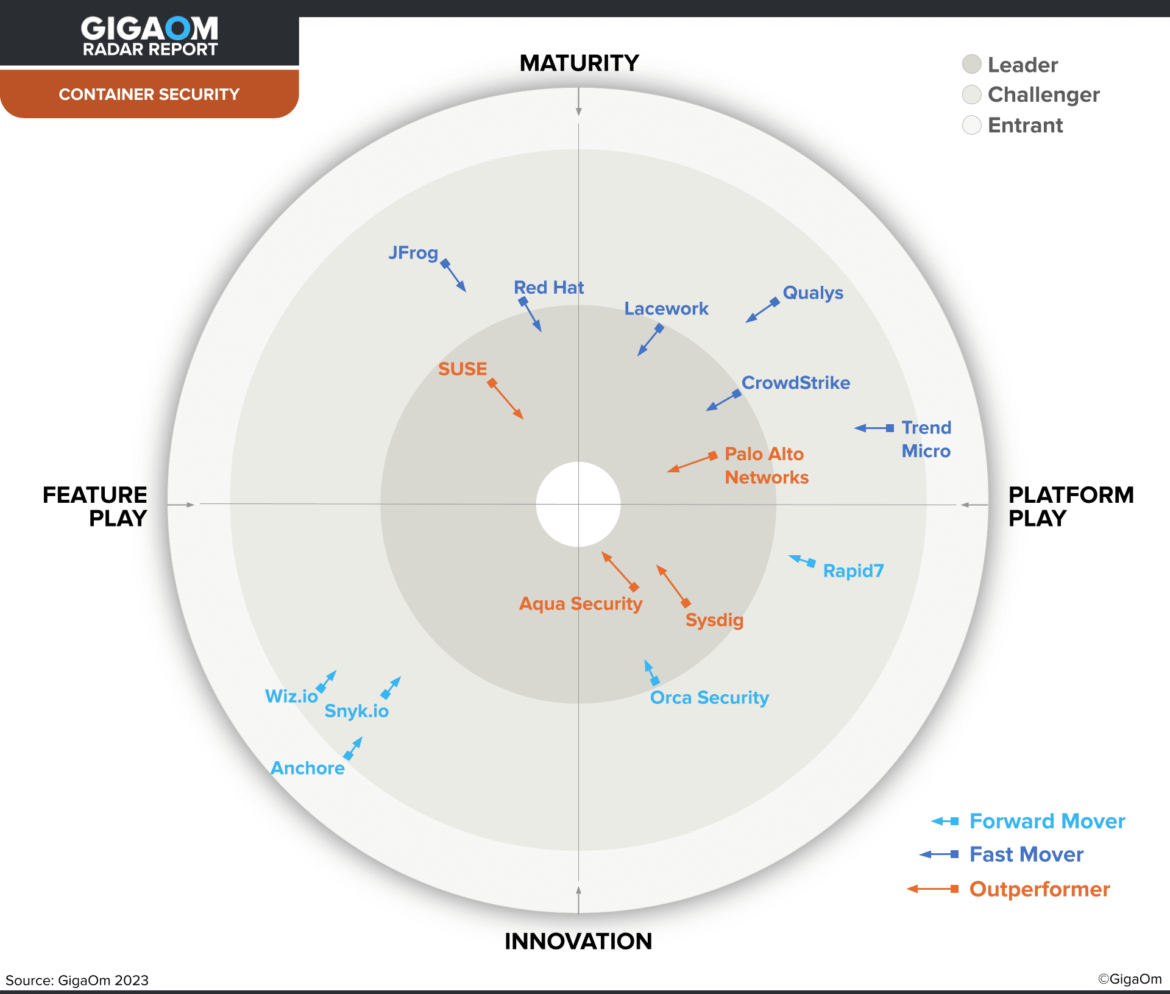
Based on these criteria, GigaOm created a Radar chart to give an overall picture of how the different solutions compare.
The GigaOm Radar plots vendors on two axes: Maturity versus Innovation and Feature Play versus Platform Play. The solutions judged to be the highest performers are those that appear closest to the center of the circle.
As you may notice, Sysdig placed exceptionally well, being named an Outperformer and earning a place in the Leaders circle. We’re proud that our continued leadership in container security has been recognized, and our designation as an Outperformer indicates that we’re truly on the cutting edge of the market.
Sysdig’s runtime insights and data collection sets it apart
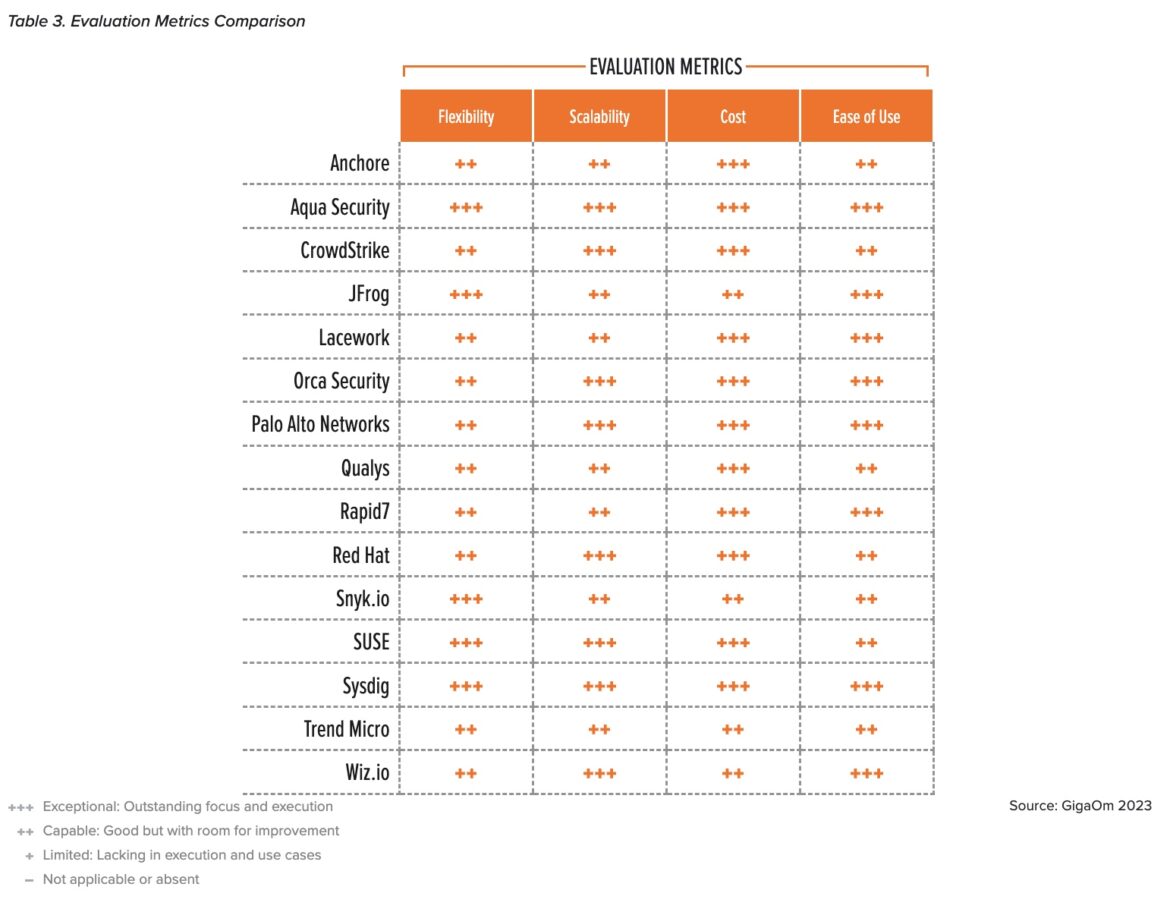
How did Sysdig achieve such high results? GigaOm highlights our rate of innovation and wide range of core features, including our ability to help IT prioritize risk more efficiently. Sysdig was one of only two vendors rated as exceptional in all of the evaluation metrics, including flexibility, scalability, cost, and ease of use.
In their in-depth analysis of our container security offering, GigaOm singled out our powerful runtime protection, commenting that “The depth and breadth of runtime information available to help assess risk and protect running workloads is a primary strength of the Sysdig solution. While some monitoring solutions in this analysis simply use the information in log files, Sysdig pulls information from everywhere, including Linux, Windows, and Kubernetes deep within the system in real time.” GigaOm also points out that this same data collection enables our solution to prioritize risks and manage overall system health more effectively than many other vendors.
The benefits of Sysdig’s unique approach to container security can be seen in our work with our customers. For instance, we’ve helped Airline Tariff Publishing Company (ATPCO) simplify their container security; capture detailed health, risk, and performance data; and save on time and efficiency.
But don’t just take our word for it. Check out the full report to learn more about why Sysdig was one of only a handful of vendors named a Leader and Outperformer for container security.
<div>
</div>
<div>
<a href="https://go.sysdig.com/GigaOm-Container-Report.html" rel="noreferrer" target="_blank">Read the Report</a> </div>
The post Sysdig Named Leader and Outperformer in GigaOm Radar for Container Security appeared first on Sysdig.
Article Link: https://sysdig.com/blog/sysdig-leader-outperformer-gigaom-radar-container-security/