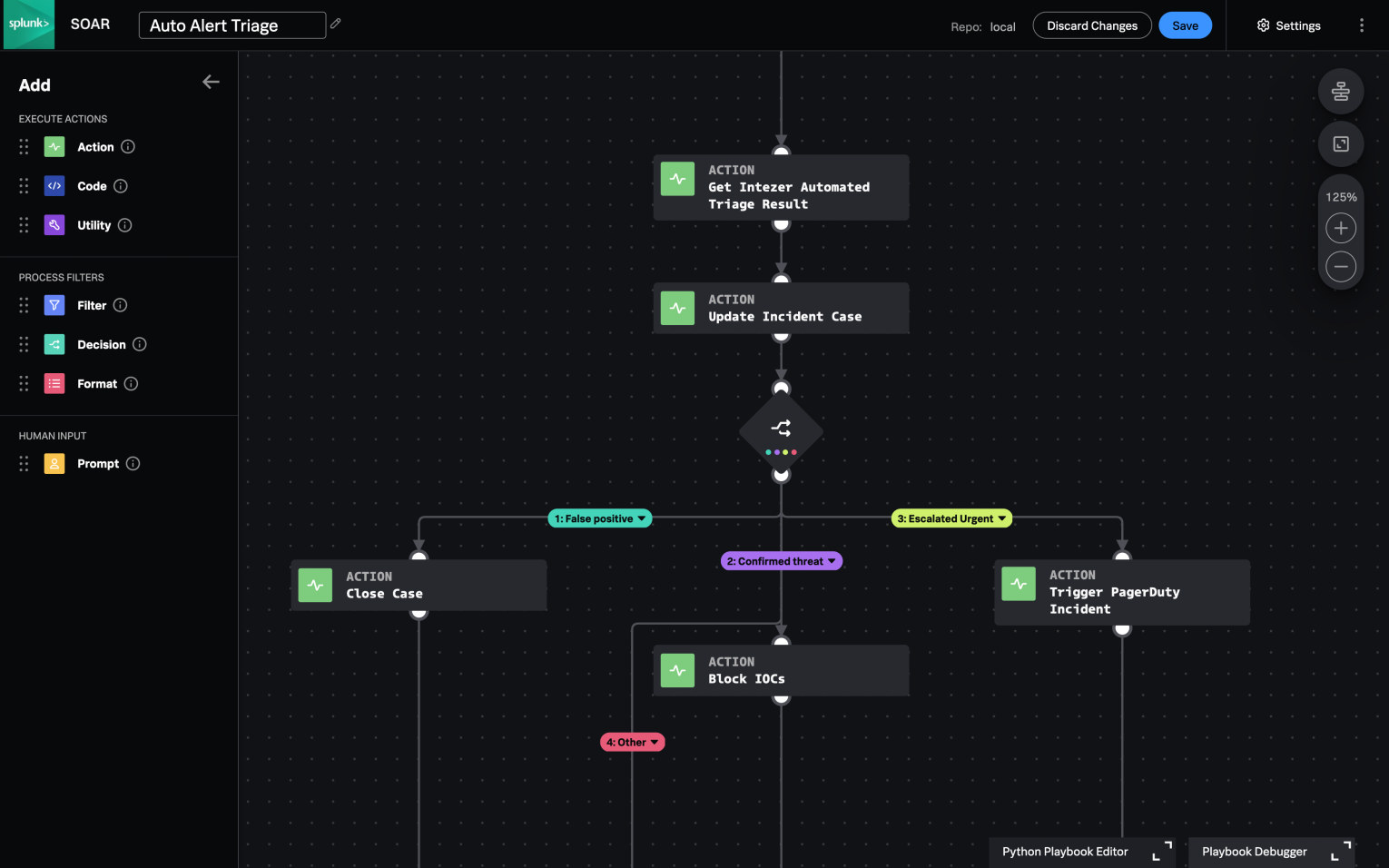
Organizations are constantly seeking ways to streamline and automate their security operations. The integration of Intezer and Splunk SOAR brings forth a powerful combination that enables security professionals to automate the alert triage and response of threats. In this blog post we will delve into the enhanced version of Intezer and Splunk SOAR integration, highlighting its key features and benefits.
Intezer Connector for Splunk SOAR
The Intezer Connector for Splunk SOAR simplifies the incorporation of Intezer’s automated alert triage and decision making technology into your Splunk playbooks.
It allows Splunk SOAR users to do the following:
- Submit files or file hashes to Intezer for analysis
- Submit URLs to Intezer for analysis
- Submit suspicious emails (raw .eml or .msg) to Intezer for analysis
- Submit various security alerts to Intezer in order to automatically investigate them
- Automatically push or pull on-demand Intezer’s alert investigation results into Splunk SOAR which could be then used in playbooks, such as smart verdicts, IOCs, TTPs, and more
Smart Decision Making
The integration of Intezer and Splunk SOAR provides an easy way for security teams to incorporate smart decision-making and advanced threat analysis into their new or existing playbooks. With Intezer’s ability to mimic the skills of a human analyst, you can now incorporate a human-like decision-making component into your Splunk SOAR playbooks, enabling your team to truly automate Tier-1 and Tier-2 tasks.
For example, instead of engineering a custom playbook that collects multiple evidence for a Crowdstrike alert, analyze each piece of evidence and then build complex logic to come up with an incident-wide conclusion, Intezer already does that for you, providing a clear triage assessment that has been abstracted into a simple block in your SOAR playbook. That way, you can reduce the need for human involvement as well as complicated and hard-to-maintain custom engineering.
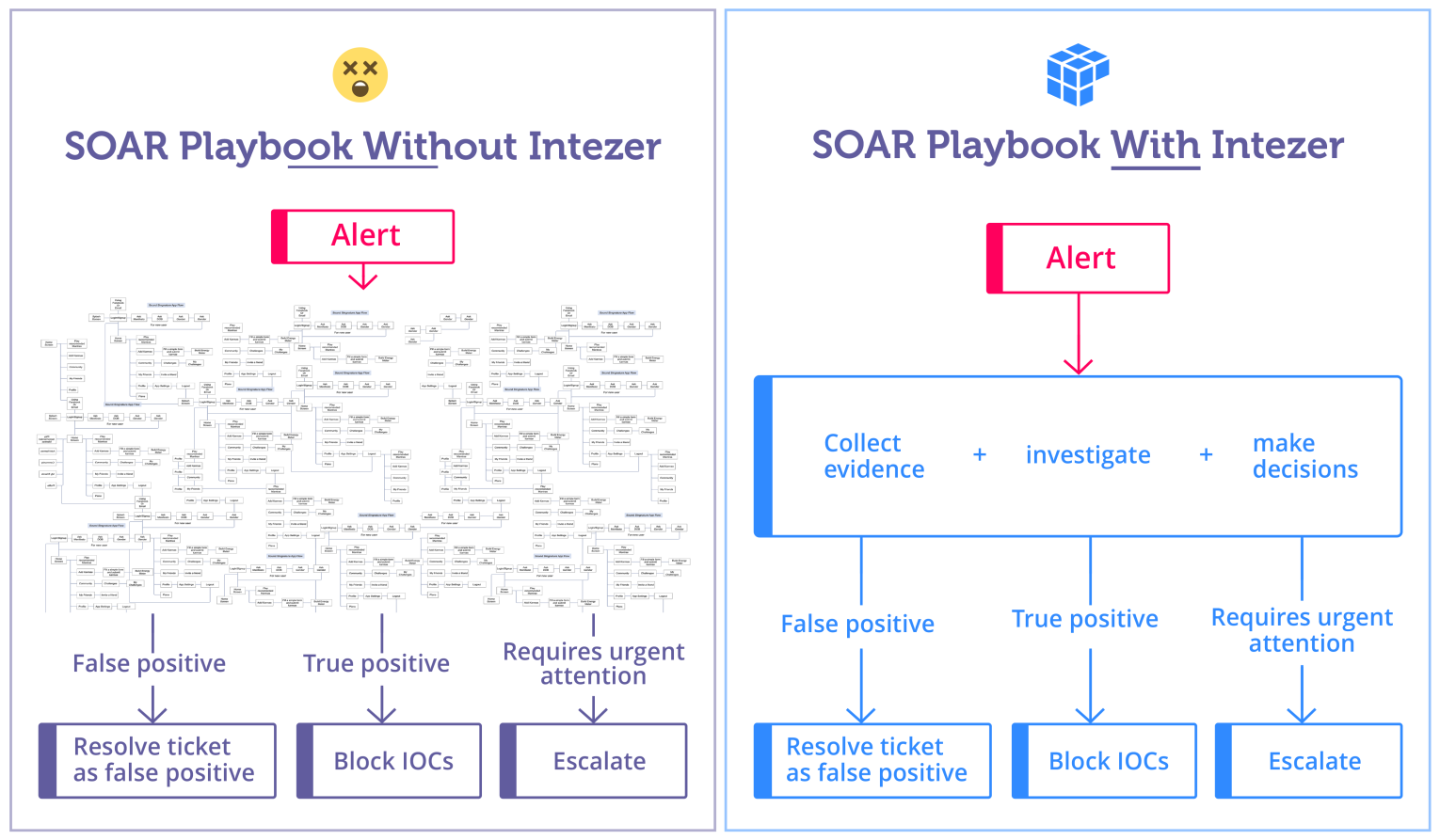
Streamlining Incident Response with Contextual Automation
The seamless integration of Intezer and Splunk SOAR brings a new level of simplicity and efficiency to case management.
The integration is instrumental in taking action to prioritize tickets and automatically resolving false positive alerts. Removing the need for manual intervention, it considerably reduces the time it takes to triage alerts and decide which ones should be focused on. The ability to automatically reduce the noise, as well as create tickets only for alerts that actually require an attention from a human analyst, is crucial in maintaining a robust security posture for your organization.
Moreover, for those tickets that do get in the hands of your team, Intezer’s analytical context is instantly transferred into your case management system, which saves significant time and resources to complete an investigation. This direct deployment of Intezer’s alert investigation results into Splunk SOAR effortlessly provides essential context, allowing analysts to make quick, informed decisions. Added context can include:
- Risk level (is it a critical threat or just unwanted software?)
- Associated threat actor or malware family
- IOCs from all the pieces of evidence that are associated with the alert
- Analysis results of every piece of collected evidence
Taking actions based on Intezer’s recommended actions for investigated alerts are another critical feature of this integration. Splunk SOAR users can quickly create playbooks to respond to threats by blocking processes, isolating a machine, applying Indicators of Compromise (IOCs), and implementing other necessary steps to prevent any potential breaches. The complicated part of deciding how to respond and what action to take, is suddenly simplified by simply relying on Intezer’s clear recommendations on what should be done next.
Simplified Licensing
Managing licenses and credentials for multiple third-party tools can be a logistical challenge for security teams. However, the integration of Intezer and Splunk SOAR simplifies this process by reducing the need for maintaining licenses for numerous tools. With a consolidated solution, you can streamline your security operations, enhance efficiency, and reduce the administrative burden associated with license management.
Getting Started
Intezer Connector for Splunk SOAR allows you to incorporate smart decision making and automated threat analysis capabilities within your new or existing playbooks. This allows security teams to achieve unprecedented efficiency and accuracy for alert triage and response.
For more details about the Intezer and Splunk SOAR integration and how to install it, please refer to the official documentation.
If you are eager to explore the capabilities of Intezer and Splunk SOAR integration and witness its potential firsthand, contact us to get a demo.
The post Streamlining Security Operations with Intezer and Splunk SOAR Integration appeared first on Intezer.
Article Link: Intezer and Splunk SOAR Integration