Story of the H2 2023: Statistical Insights into Ransomware Trends and Impact on Victims (English ver.)
Author: Kyunghee Kim, Jiho Kim, and Huiseong Yang | S2W TALON
Last Modified: Feb 21, 2024
 Photo by Sasun Bughdaryan on Unsplash
Photo by Sasun Bughdaryan on UnsplashExecutive Summary
- This report analyzes the activities of ransomware groups that occurred in the second half of 2023 (July 1, 2023, to December 31, 2023).
- The analysis targets ransomware groups with ransomware Leak sites and the victim companies and organizations uploaded to these ransomware Leak sites.
- In the second half of 2023, ransomware infections of 2,344 companies were posted on the Leak sites.
— The total number of affected companies increased by 1,036 compared to the second half of 2022 (July 1, 2022, to December 31, 2022). - A total of 53 ransomware groups were active, with an average of approximately 44 companies attacked per group.
- There were 25 new or modified Leak sites. The new ransomware groups with Leak sites attacked an average of about 21 companies each.
- In H2 2023, large enterprises accounted for 8.4% of the companies targeted by ransomware groups, which is higher than the 7.7% in the previous year’s second half.
- The top 10 countries affected by ransomware attacks during H2 2023 were selected, with the United States experiencing the greatest damage.
— Compared to the second half of 2022, many countries within the European continent experienced an increase in damage in 2023, with the United States being the country where the damage increased the most.
— Compared to 2022, the countries where damage decreased in 2023 were located in Europe, Asia, and the Americas, with Taiwan and Vietnam experiencing the greatest decrease in damage. - The top 10 industries affected by ransomware damage were identified, with the manufacturing sector experiencing the greatest damage throughout the year 2023.
- Additionally, unique characteristics of ransomware groups in 2023 were identified based on job postings and activity platforms.
— In 2023, ransomware groups increasingly recruited members with diverse and specific skill sets, operating their groups systematically. - An understanding of ransomware groups and detailed issues can be found in the Ransomware Trends Report Part 2.
1. Overall ransomware group activity in H2 2023
During the second half of 2023, a total of 2,344 companies were observed to have suffered damages due to ransomware group attacks. This represents an increase of 1,036 companies compared to the 1,308 companies affected by ransomware attacks in the second half of the previous year. According to Figure 1, ransomware activity frequency was higher in every monthly segment from July to December compared to the second half of 2022, with an average increase of approximately 173 affected companies per month.
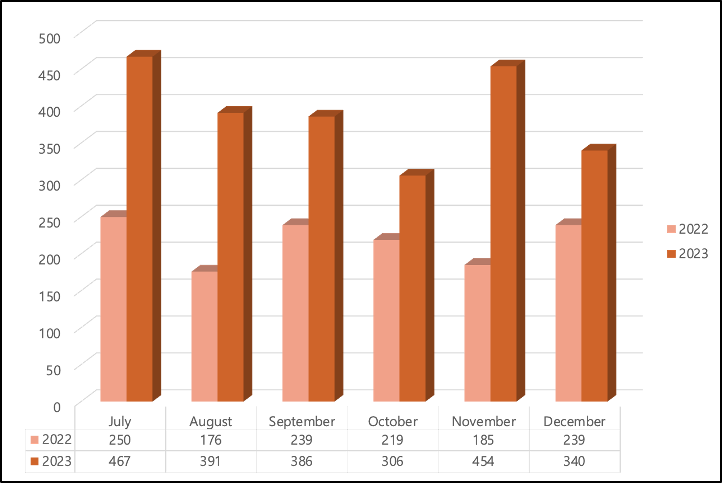 Figure 1. Monthly Attack Volume Comparison between the Second Half of 2022 and 2023
Figure 1. Monthly Attack Volume Comparison between the Second Half of 2022 and 2023Analysis targeting ransomware groups operating Leak sites revealed that a total of 53 groups were active in the second half of 2023, attacking an average of about 44 companies each. The top 10 ransomware groups, which were the most active, accounted for 70.9% of all ransomware attacks in the second half of 2023. Detailed figures can be found in Table 1 and Figure 2.
- The top 10 ransomware groups in terms of attack volume averaged attacks on 166 companies each.
- Excluding the top 10 ransomware groups in terms of attack volume, the remaining 43 ransomware groups performed attacks on an average of approximately 16 companies each.
- The top 10 ransomware groups in terms of attack volume had a significantly higher attack volume, approximately 10.4 times higher than the average attack volume of groups not in the top 10. This indicates a substantial gap in attack volume.
The sharp increase in the total number of victim companies attributed to ransomware group activities in the second half of 2023 can be attributed to the significant increase in activity by new ransomware groups such as 8Base, Akira, Cactus, and others. Detailed introductions to these new ransomware groups can be found in the report below.
New ransomware groups in the first half of 2023: Story of H1 2023: In-depth Examination of Notable Ransomware Groups and Key Issues
New ransomware groups in the second half of 2023: Story of H2 2023: In-depth Examination of Notable Ransomware Groups and Key Issues
Especially, Medusa, AKIRA, and 8Base, which emerged in the first half of 2023, continued to perform ransomware attacks steadily in the second half of 2023, securing their positions in the top 10 alongside established ransomware groups in terms of attack volume.
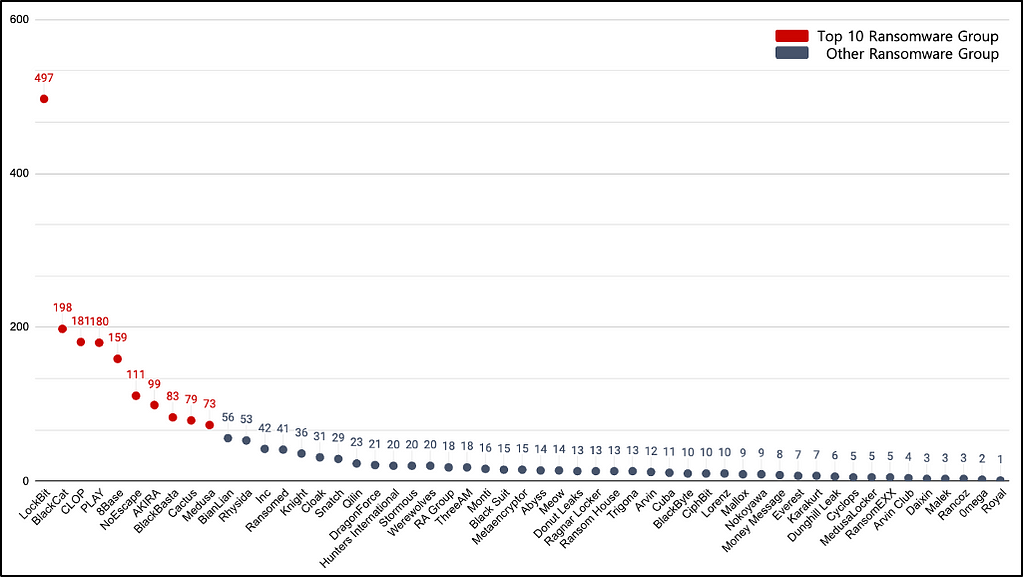 Figure 2. Graph of Attack Volume by Ransomware Group in the Second Half of 2023
Figure 2. Graph of Attack Volume by Ransomware Group in the Second Half of 2023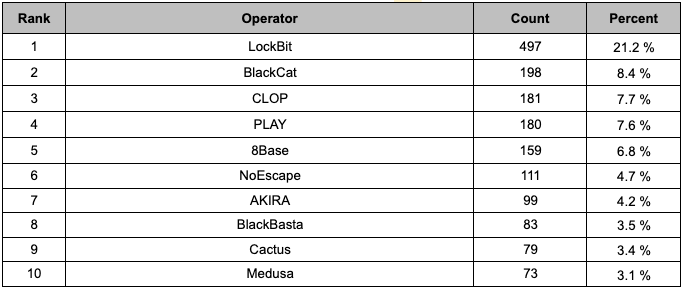 Table 1. Attack Volume Table of Top 10 Ransomware Groups
Table 1. Attack Volume Table of Top 10 Ransomware Groups2. Activity of new ransomware groups in 2023 H2
In the second half of 2023, a total of 18 newly discovered Leak sites were confirmed, with 5 sites having their addresses changed: Trigona, Ransomed, 8Base, BlackCat, and Stormous. Two Leak sites, Trigona and Ragnar Locker, were confirmed to have ceased operations.
The activity of the 18 ransomware groups associated with newly discovered Leak sites in the second half of 2023 amounted to a total of 332 incidents, averaging approximately 21 incidents per group. Thus, compared to the overall average activity of ransomware groups, as discussed in Section 1, which was 41 incidents, the activity of new ransomware groups was half of that average.
On the other hand, the ransomware activity of the Cactus ransomware group, which emerged in July 2023, amounted to 79 incidents, showing approximately four times the activity compared to the average activity of new ransomware groups, which was 21 incidents. Thus, the Cactus ransomware group exhibited the highest activity among the new ransomware groups in the second half of 2023. The activity of the new ransomware groups, including Cactus, in the second half of 2023 can be seen in Figure 3.
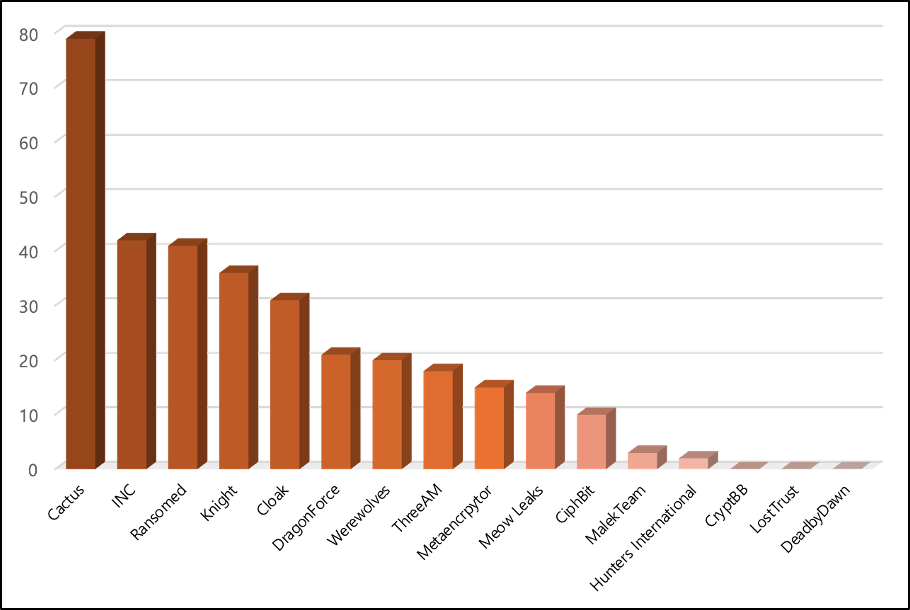 Figure 3. Graph of Activity Volume of New Ransomware Groups in the Second Half of 2023
Figure 3. Graph of Activity Volume of New Ransomware Groups in the Second Half of 20233. Targeted Victim Enterprises Size
In Section 3, we investigated and analyzed the scale of companies affected by ransomware attacks. The size of the companies was classified based on their revenue, following the criteria defined by Gartner, as in the Ransomware Trends Report for the first half of 2023.
In the second half of 2023, the number of companies affected by ransomware groups was highest among small enterprises with 1,497 incidents, followed by midsize enterprises with 535 incidents, and large enterprises with 186 incidents. Additionally, there were 126 incidents reported for companies that did not publicly disclose their revenue scale. Therefore, among the disclosed scale of affected companies in the second half of 2023, small and midsize enterprises accounted for 91.6%, while large enterprises accounted for 8.4%.
In the second half of 2022, the scale of affected companies was also highest among small enterprises, with 508 incidents, followed by midsize enterprises with 264 incidents, and large enterprises with 64 incidents. Additionally, there were 472 incidents reported for companies that did not publicly disclose their revenue scale. Therefore, among the disclosed scale of affected companies in the second half of 2022, small and midsize enterprises accounted for 92.3%, while large enterprises accounted for 7.7%.
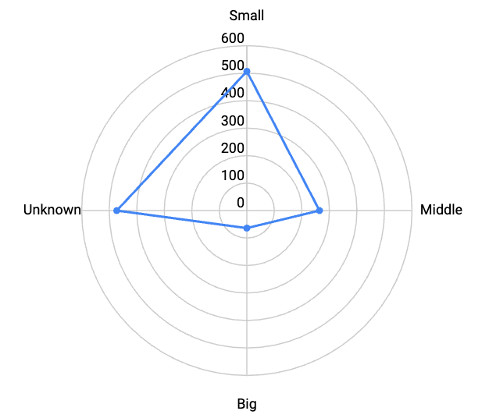
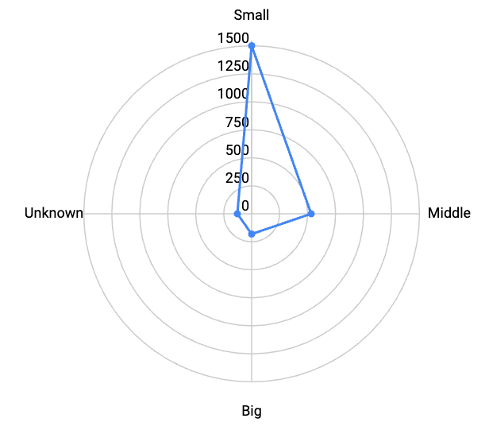 Figure 4. Radar Chart of Company Classification by Revenue (Left-H2 2022, Right-H2 2023)
Figure 4. Radar Chart of Company Classification by Revenue (Left-H2 2022, Right-H2 2023)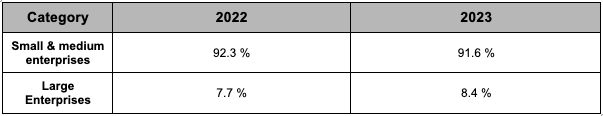 Table 2. Frequency Table of Targeted Company Classification for the Second Half of 2022 and 2023
Table 2. Frequency Table of Targeted Company Classification for the Second Half of 2022 and 2023The comparison of the target recipients of ransomware groups in the second half of 2022 and 2023 revealed that, relatively, there was a higher proportion of small and midsize enterprise targets in the second half of 2022. Conversely, in the second half of 2023, there was a slight increase in the proportion of large enterprise targets.
- However, among the 53 ransomware groups, it was noted that there were over 20 groups, including Cyclops and Werewolves, for which no history of attacking large enterprises was identified.
- Among the top 10 groups in terms of attack volume, LockBit targeted 26 incidents out of a total of 497 attacks on large enterprises, while PLAY targeted 4 incidents out of a total of 180 attacks on large enterprises, indicating a relatively low frequency of targeting large enterprises. However, CLOP targeted approximately 40% of its total attacks, amounting to 72 incidents, on large enterprises out of a total of 181 attacks, while Dunghill Leak also targeted approximately 33% of its total attacks, accounting for 2 incidents, on large enterprises out of a total of 6 attacks.
- Through this, it was observed that there are differences in the sizes of companies targeted by ransomware groups. Particularly, some ransomware groups, including CLOP, tend to target large enterprises more frequently.
However, it is worth noting that there may be variations in the aforementioned figures due to the possibility that large enterprises with sufficient ransom payment capabilities and a significant amount of critical information may have paid the ransom before uploading to the leak site.
4. Targeted Victim Country
4.1. Top 10 Targeted Victim Countries
The top 10 ransomware-affected countries account for 77% of all affected businesses. Among the top 10 affected countries, there are 6 countries from Europe, 3 from the Americas, and 1 from Oceania, indicating a high frequency of ransomware-related damages in countries across Europe and the Americas. These 10 countries all rank within the top 18 in terms of GDP, indicating that a significant number of ransomware attacks were targeted at countries with strong economic standings in the second half of 2023. This suggests a trend where ransomware attacks are commonly targeted at countries with higher GDPs. The CCB also mentioned a strong correlation between a country’s GDP and the number of affected businesses, indicating that ransomware groups target wealthier countries to acquire ransom payments.
Blue: Countries in Oceania
Green: Countries in Europe
Yellow: Countries in America
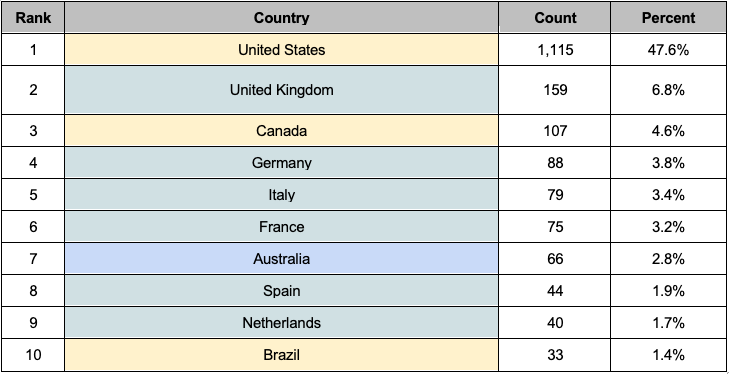 Table 3. Top 10 Countries Affected by Ransomware.
Table 3. Top 10 Countries Affected by Ransomware.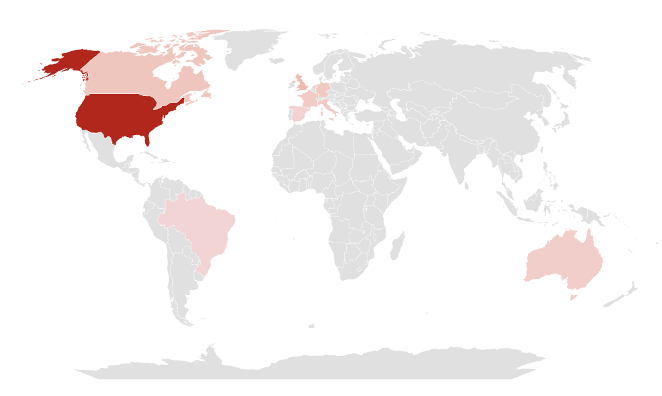 Figure 5. Graph of Top 10 Countries Affected by Ransomware
Figure 5. Graph of Top 10 Countries Affected by Ransomware4.2. Top 10 Countries with increased target count compared to H2 2022
The country with the highest increase in ransomware incidents from the second half of 2022 to the second half of 2023 was the United States. Additionally, you can find the top 10 countries with increased ransomware incidents in Table 4. Among the top 10 countries with increased incidents, 6 countries belong to the European continent, making it the continent with the highest increase in ransomware incidents.
- The top 3 countries with the highest ransomware incidents in the second half of 2023 according to Table 3, namely the United States, Canada, and the United Kingdom, also correspond to the top 3 countries with the highest increase in ransomware incidents according to Table 4. This aligns with the results observed in the first half of 2023.
Red: Countries in Asia
Blue: Countries in Oceania
Green: Countries in Europe
Yellow: Countries in America
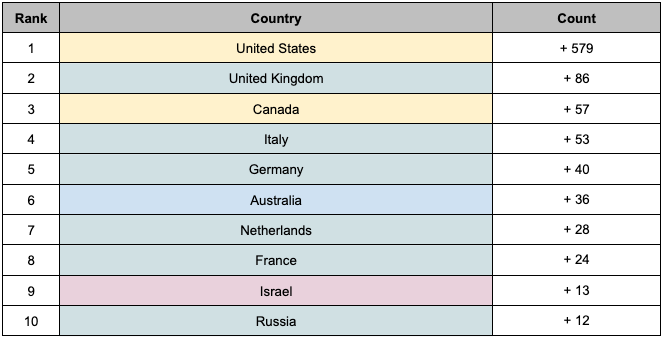 Table 4. Top 10 Countries with Increased Ransomware Incidents
Table 4. Top 10 Countries with Increased Ransomware Incidents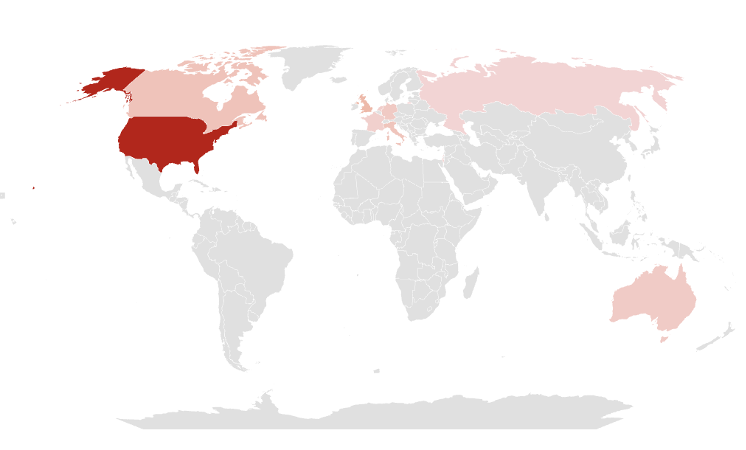 Figure 6. Graph of Top 10 Countries with Increased Ransomware Incidents
Figure 6. Graph of Top 10 Countries with Increased Ransomware IncidentsAnother notable characteristic observed in the ransomware activity during the second half of 2023 is the significant increase in ransomware incidents in Israel and Russia, which were not among the top-ranking countries in the second half of 2022. Investigation into ransomware groups targeting these two countries revealed that, as shown in Figure 7, the majority of the attacks were carried out by specific groups.
- Israel saw a surge from 1 incident to 14 incidents, while Russia climbed from 2 incidents to 14 incidents, landing them in the 9th and 10th positions, respectively, according to Table 4.
- Out of Israel’s 14 incidents in the second half of 2023, 7 were attributed to LockBit.
- Out of Russia’s 14 incidents in the second half of 2023, 12 were attributed to Werewolves.
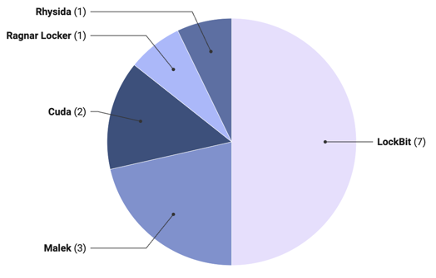
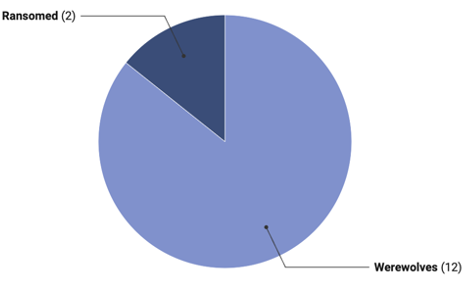 Figure 7. Pie Plot of Ransomware Groups Targeting Companies in Israel and Russia (Left-Israel, Right-Russia)
Figure 7. Pie Plot of Ransomware Groups Targeting Companies in Israel and Russia (Left-Israel, Right-Russia)4.3. Top 10 Countries with reduced target count compared to H2 2022
The country with the largest decrease in ransomware incidents from the second half of 2022 to the second half of 2023 was Taiwan and Vietnam. Additionally, you can refer to Table 5 to see other countries where ransomware incidents have decreased. Within the top 10 countries with decreased incidents, there are three countries each from Asia, Europe, and the Americas, indicating a reduction in ransomware incidents compared to the previous year.
Red: Countries in Asia
Blue: Countries in Oceania
Green: Countries in Europe
Yellow: Countries in America
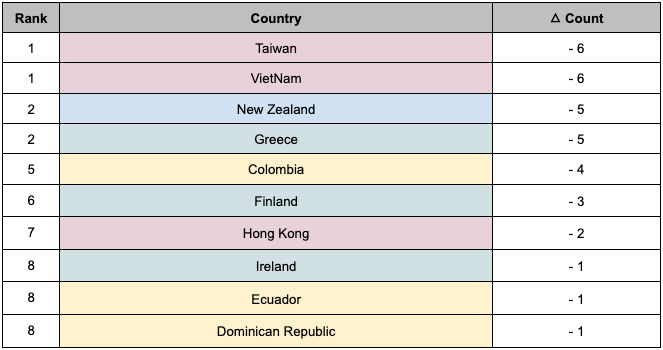 Table 5. Top 10 Countries with Decreased Ransomware Incidents
Table 5. Top 10 Countries with Decreased Ransomware Incidents Figure 8. Ransomware Damage Reduction Country TOP 10 Graph
Figure 8. Ransomware Damage Reduction Country TOP 10 GraphWhen comparing Sections 4.2 and 4.3, it was observed that both the country with the highest increase and the country with the highest decrease in ransomware attacks were located on the European continent. Upon examining the differences between European countries where the attack volume increased and those where it decreased, it was found that the countries with increased attack volumes had larger GDPs and populations compared to those with decreased attack volumes.
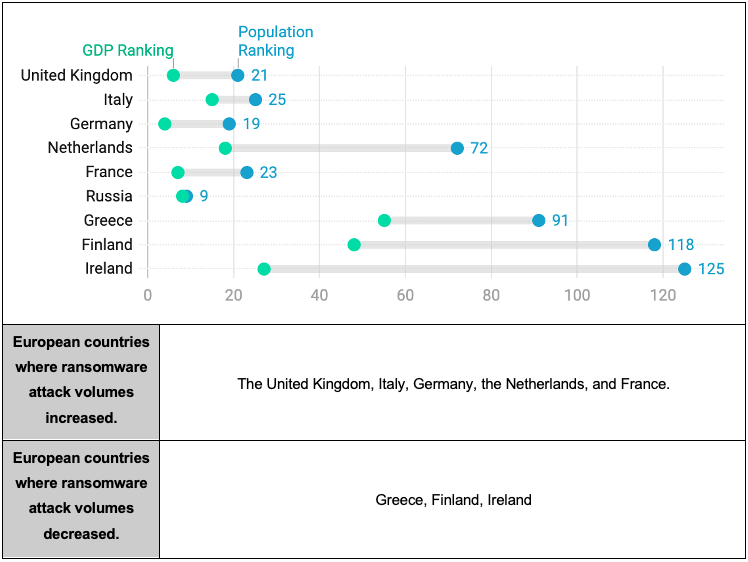 Figure 9. Comparison of GDP and population between European countries where the attack volume increased and those where it decreased.
Figure 9. Comparison of GDP and population between European countries where the attack volume increased and those where it decreased.Furthermore, in Section 4.2, the trends of the TOP 10 countries that increased compared to last year appeared to be similar to the results of the first half of 2023. However, in Section 4.3, countries such as Taiwan and Vietnam, which were not included in the statistics for the first half of the year, appeared among the TOP 10 countries where attack volumes decreased. When estimating the reasons for these results in the second half of 2023, it is noted that according to CompaniesMarketCap, the number of companies classified as large companies based on market capitalization was 3,640 in the United States, 257 in the United Kingdom, and 394 in Canada. In contrast, Taiwan had 99, Vietnam had 1, and New Zealand had 29 companies, indicating that the number of major global companies in each country is relatively low. Consequently, there is a possibility that the number of companies exposed to attacks was proportionally lower accordingly.
5. Targeted Victim Industry
5.1. Top 10 Targeted Industries
The Top 10 affected industries accounted for 66.0% of the total damage, and among them, five industries with high revenues in 2023, as surveyed by Global Edge, were targeted by ransomware groups, indicating a tendency to target industries with significant revenue. The manufacturing sector, which accounted for 16.7% of all affected companies, remained the most affected industry, similar to the first half of 2023. According to Table 6, the manufacturing sector also saw the highest increase in damage compared to last year among the Top 10 affected industries, followed by increases in the business services and distribution industries.
- The manufacturing sector can suffer significant downtime in production processes due to ransomware attacks, leading to production delays and substantial financial losses due to supply chain disruptions. According to HEFFERNAN’s research, particularly in the food manufacturing industry, delays in processing can result in food ingredients spoiling, leading to significant resource and financial losses that cannot be avoided. The food manufacturing industry tends to rely on computerized systems, making it highly vulnerable to ransomware attacks, with a high likelihood of paying ransom to mitigate damages. Additionally, it is speculated that the food distribution industry is also vulnerable to ransomware attacks, as delays in transportation can lead to significant impacts on food quality.
- Furthermore, according to Construction Business Owner, the construction industry often operates on tight project schedules, with contractual obligations for the timely supply of important documents and materials. Ransomware groups have exploited situations where operational disruptions occur, leading to cascading impacts on schedules and costs, resulting in substantial losses.
- In the case of the education sector, according to Futureio, schools may not be cash-rich, yet they can have an immediate and extensive impact on the local community. This makes them noticeable targets for ransomware groups.
As mentioned above, ransomware groups not only target industries with significant revenue but also take into account factors such as time constraints and societal impact.
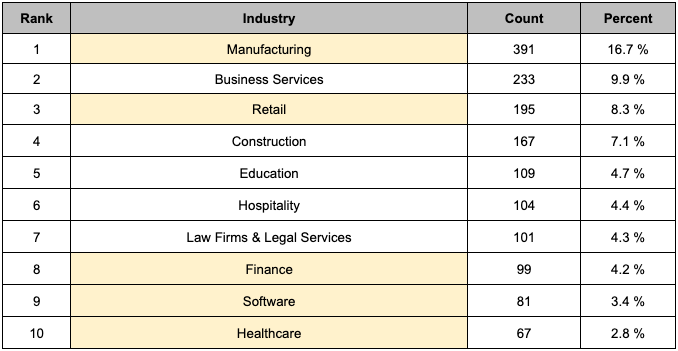 Table 6. Top 10 Industries Affected by Ransomware (Yellow: Top 10 Industries by Revenue
Table 6. Top 10 Industries Affected by Ransomware (Yellow: Top 10 Industries by RevenueCompared to the second half of 2022, industries affected by ransomware saw increases in damages during the second half of 2023, with most of them being included in Table 6. The major target industries and their frequencies were similar to those of the previous year. However, the Government was not included in Table 6, but Table 7 showed an increase in the frequency of ransomware damage. Analysis regarding the increasing trend of ransomware infections in Government will be detailed in Section 5.2.
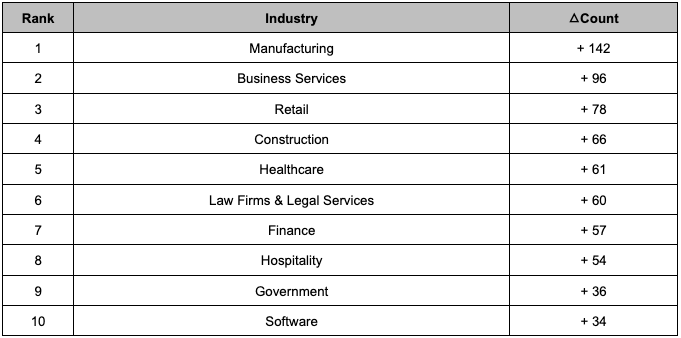 Table 7. Top 10 Industries with Increased Ransomware Damage from 2022 to 2023
Table 7. Top 10 Industries with Increased Ransomware Damage from 2022 to 20235.2. Targeted governments in H2 2023
When government agencies fall victim to ransomware attacks, it can lead to prolonged disruptions in municipal councils and critical social infrastructure services, resulting in significant impacts from ransomware attacks. In the second half of 2022, there were relatively few ransomware attacks on government agencies, with 21 incidents reported. However, in the second half of 2023, the number of attacks increased by 36, totaling 57 attacks on government agencies. Among the 57 government agencies targeted in the second half of 2023, 20 were targeted by ransomware groups, with LockBit ransomware being the most prevalent, accounting for 16 incidents of attacks on government targets.
In 2023, government agency damage was observed in eight countries that were among the Top 10 affected nations: the United States, Australia, Italy, the United Kingdom, Spain, the Netherlands, Brazil, and France. The United States, which was the most affected country in the second half of 2023, experienced 23 incidents of government agency damage. However, it is worth noting that an additional 19 countries were observed to have government agency damage despite not being included in the Top 10 affected countries of 2023.
- Among the countries where government agencies suffered damage, the eight countries included in the Top 10 affected countries of 2023 rank from 1st to 18th in terms of world GDP, indicating that they have higher GDP rankings. On the other hand, the remaining 20 countries range from 13th to 128th in terms of GDP, indicating that they belong to countries with relatively lower GDP rankings.
- Referring to Section 4.1, ransomware attacks typically target countries with high GDP. However, there have been cases where ransomware attacks targeted government agencies in countries with lower GDP. Apart from GDP considerations, Cybereason pointed out that government agencies are targeted because many of them lack well-established security policies and recovery plans. This vulnerability makes government agencies susceptible targets for ransomware attacks.
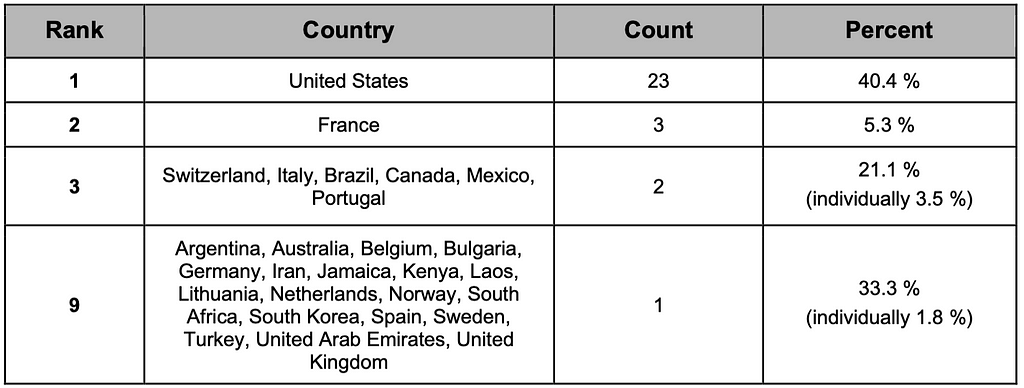 Table 8. Top 10 Countries Where Government Agencies Have Suffered Ransomware Damage
Table 8. Top 10 Countries Where Government Agencies Have Suffered Ransomware Damage6. New Trends in Ransomware Operation and Law-based Defense
6.1. Affiliate Recruitment and Communication Post
The RAMP forum, where ransomware groups primarily operate, includes separate sections for recruitment (Freelance) and RaaS (Ransomware-as-a-Service) bulletin boards. The combined total of posts and comments uploaded to these bulletin boards during 2023 is depicted in Figure 10. Recruitment notices have been observed seeking Pentesters, attackers who infiltrate the internal infrastructure of targets to disseminate ransomware, among other cases aimed at recruiting RaaS members.
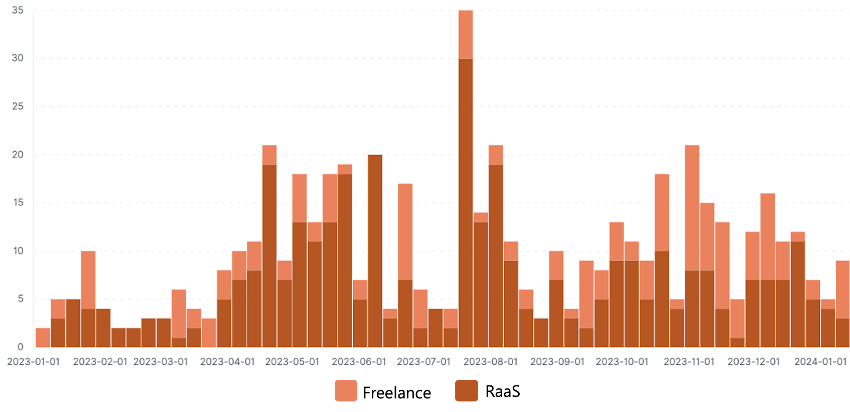 Figure 10. Frequency of Posts and Comments Combined in the Freelance and RaaS Bulletin Boards on the RAMP Forum
Figure 10. Frequency of Posts and Comments Combined in the Freelance and RaaS Bulletin Boards on the RAMP ForumRansomware-related recruitment posts have also been identified on other forums such as Breachforums and Exploit forums, besides the RAMP forum. In these posts, job descriptions are presented in more detail, and there is a broader diversity of roles, including journalists, ethical hacking experts, and others. This indicates that the composition of ransomware group members is evolving systematically. Specific cases are discussed in detail in Part 2.
6.2. Mentioned Keywords by Sources
During 2023, investigations into the trends of two sources, namely deep and dark web forums, and Telegram, regarding the mention of two keywords associated with ransomware, ‘Ransomware’ and ‘Affiliate’, yielded the following results.
- For the two mentioned keywords, during the first half of the year, they were frequently mentioned on deep and dark web forums, while during the second half of the year, the frequency of mentions increased on Telegram.
- Especially on Telegram, the frequency of mentions for the keyword ‘Affiliate’ was higher than ‘Ransomware’. This is likely due to the communicative nature of the messenger platform, where discussions about renting ransomware services (‘Affiliate’) may be more prevalent than general discussions about ‘Ransomware’.
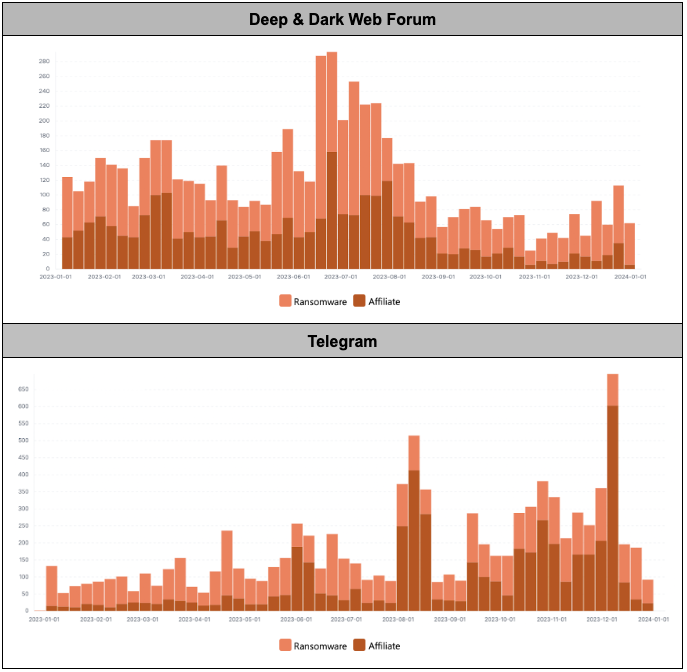 Figure 11. Trends in Ransomware Keyword Mentions on Deep & Dark Web and Telegram
Figure 11. Trends in Ransomware Keyword Mentions on Deep & Dark Web and Telegram6.3. Prohibition on Paying Ransom Money
As ransomware attacks persist, attention has also been drawn to national policies aimed at disrupting ransomware groups’ revenue by addressing ransom payments. The enactment of laws prohibiting ransom payments began on April 5, 2022, when North Carolina became the first state to declare such legislation. Subsequently, various regions, including Florida, introduced provisions prohibiting ransom payments, and in 2023, localities and countries continued to enact laws prohibiting ransom payments.
- On November 1, 2023, the International Ransomware Response Initiative (CRI), comprising 50 member countries, announced the first joint CRI policy statement declaring a ban on ransom payments by member governments.
 Figure 12. Excerpt from the Joint CRI Policy Statement Declaring the Prohibition of Ransom Payments
Figure 12. Excerpt from the Joint CRI Policy Statement Declaring the Prohibition of Ransom Payments- According to research conducted by Coveware, various regions and government agencies demonstrate a continued willingness to invest in executing and preventing ransomware response laws.
- Furthermore, according to Figure 13, the percentage of companies choosing to pay ransom money dropped to a historically low level of 29% in the fourth quarter of 2023 compared to the third quarter. Consequently, while the number of ransomware victimized companies increased as discussed in Section 1, the frequency of ransom payments showed a decreasing trend.
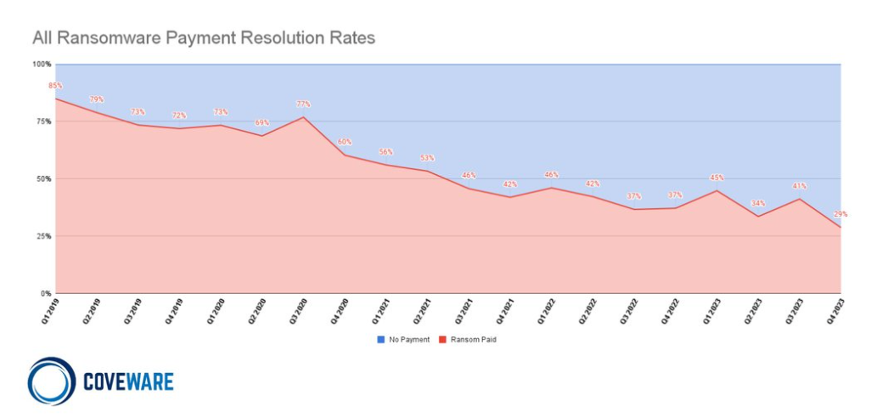 Figure 13. Graph of Ransom Payment Rates
Figure 13. Graph of Ransom Payment RatesConclusion
- The ransomware attack volume in the second half of 2023 increased by 1,036 compared to the same period last year. The overall increase in ransomware attacks was attributed to the following factors:
— During the second half of the year, the appearance of 16 or more new ransomware groups was noted.
— Steady activity from the new groups that emerged in the first half of 2023, such as 8Base and Akira, was observed.
— The emergence of new groups in the second half of 2023, such as Cactus and INC, was also characterized by active engagement. Particularly noteworthy was the heightened activity level observed in Cactus, which stood out as the most active among the new ransomware groups in the second half of 2023. - In 2023, ransomware groups exhibited a tendency to target large corporations with significant revenue, countries with high GDP, and industries with substantial profitability.
— The country with the highest ransomware damage count in 2023 was the United States. Additionally, it was observed that the United States experienced the largest increase in ransomware damages compared to 2022.
— The countries that experienced the greatest decrease in ransomware damages in 2023 were Taiwan and Vietnam.
— Among the top 10 industries targeted by ransomware, more than 5 are ranked within the top 10 most profitable industries. - Simultaneously, ransomware groups target industries such as manufacturing, where downtime itself can cause a significant impact, as well as sectors like education, which can have societal repercussions. They strategically employ coercion tactics to pressure companies by exploiting the threat of disruption.
- New ransomware group operations and activity patterns have been identified through recruitment advertisements and activity platforms.
— Roles of recruited members are becoming more defined through job postings, indicating that ransomware groups are operating in a more structured manner.
— Mentions of ransomware are increasing on Telegram. - Legislation prohibiting ransom payments in response to ransomware is also gaining attention, and there is a trend of decreasing ransom payment frequency observed in the fourth quarter of 2023.
- Ransomware attacks continued to increase and evolve throughout the second half of 2023, following a trend observed in the first half of the year. They pose a significant threat to businesses, individuals, and governments alike.
- Enterprises must recognize the importance of enhancing security measures and implementing robust backup systems. It is essential to foster close collaboration between the security industry and businesses and actively adopt the latest security technologies.
P.S. Thanks to the Data and Knowledge Engineering teams for their assistance with data collection and processing for this report.

Homepage: https://s2w.inc
Facebook: https://www.facebook.com/S2WLAB
Twitter: https://twitter.com/S2W_Official
Story of the H2 2023: Statistical Insights into Ransomware Trends and Impact on Victims (English… was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.