Story of the H2 2023: In-depth Examination of Notable Ransomware Groups and Key Issues (English ver.)
Author: Jiho Kim, Huiseong Yang, and Kyunghee Kim | S2W TALON
Last Modified: Feb 21, 2024
 Photo by Kirill Pershin on Unsplash
Photo by Kirill Pershin on UnsplashExecutive Summary
- This report is compiled by summarizing the newly emerging ransomware and major issues related to existing ransomware groups that were active in the second half of 2023 (July 1, 2023, to December 31, 2023).
- During the second half of 2023, a total of 44 newly identified ransomware groups were confirmed, representing an increase of 9 compared to the first half of the year. Among them, the highest number of groups were discovered in November, marking the peak during the entire period.
- New ransomware groups can be categorized into those operating Leak sites and groups utilizing the source code or builder of existing ransomware groups.
— During the second half of 2023, a total of 18 new ransomware groups with Leak sites were discovered. Among them, 5 groups had their Leak site addresses changed, and 2 groups were confirmed to have ceased operations.
— The number of groups utilizing Clearnet domains from Leak sites increased by 4, totaling 4 newly added groups. Additionally, there was a rise in the number of groups whose infrastructure was taken down, with 2 groups experiencing takedowns, representing an increase of 1 compared to the first half of the year.
— Among the new ransomware groups, a total of 13 were confirmed to utilize known ransomware families. During the second half of the year, the Chaos family accounted for the largest share, with 5 groups out of the total. - The ransomware-related issues that occurred during the second half of 2023 were categorized into Ransomware Group, Affiliate, Attack Campaign, and duplicate victims.
— Ransomware Group: Based on the activity levels between existing ransomware groups and newly emerging ransomware groups, numerous groups with confirmed associations were discovered.
— Affiliate: The activity between Initial Access Brokers (IABs) and Pentesters continues steadily between RaaS Operators, and in the second half of the year, external reports related to IABs and Pentesters such as GOLD MELODY and ShadowSyndicate were disclosed.
— Attack Campaign: Ransomware groups exploited more vulnerabilities in the second half of the year compared to the first half. Among them, the CLOP group utilized two 0-day vulnerabilities, while the LockBit group caused significant damage to numerous victimized companies by exploiting high-impact vulnerabilities. Additionally, commercial utilities and open-source tools such as Cobalt Strike and Mimikatz have been consistently utilized in ransomware attacks.
— Duplicated Victims: The total number of duplicate victim companies is confirmed to be 35. Among the groups that uploaded duplicate victims first, LockBit had the highest number with 11 instances, while among the groups that uploaded later, BlackCat had the highest proportion with 6 instances.
1. New Ransomware Groups in H2 2023
In the second half of 2023, a total of 44 new ransomware groups were tracked by S2W, averaging 7.3 new groups discovered per period. The number of newly emerged ransomware groups in the second half increased by 9 compared to those in the first half of the year. November stood out as the month with the highest number of new group appearances during the second half of 2023, with a total of 10 new groups emerging.
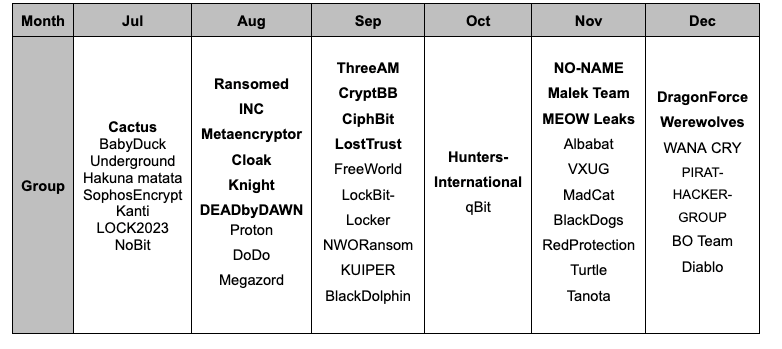 Table 1. New Ransomware Groups in the Second Half of 2023 (Bold: Groups with Leak Sites)
Table 1. New Ransomware Groups in the Second Half of 2023 (Bold: Groups with Leak Sites)2. Categorizing New Ransomware Groups
In this section, we conducted further analysis of new ransomware groups active in the second half of the year, categorizing them based on their distinct characteristics. To achieve this, the groups were subdivided according to those operating leak sites and by ransomware family criteria.
2.1. Ransomware Groups operating Leak Site & Negotiation Site
Throughout the second half of 2023, similar to the first half, numerous ransomware groups continued to employ a double extortion tactic, demanding money through file encryption and threatening to release stolen data. These groups are utilizing negotiation sites to conduct discussions with victims and leak sites to publish the pilfered data, both of which are critical infrastructures in ransomware operations.
S2W has been persistently tracking ransomware groups that operate leak sites. A comparison between the first and second halves of 2023 reveals a decrease in the number of ransomware groups that introduced new leak sites, while an increase was observed in the number of groups that either changed their address or ceased operations, thus going offline.
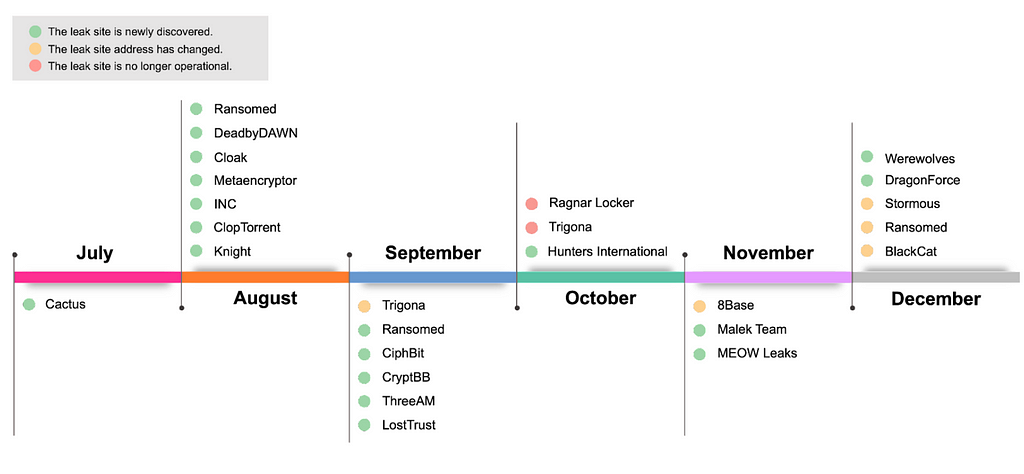 Figure 1. Second Half of 2023: Changes in the Status of Leak Sites
Figure 1. Second Half of 2023: Changes in the Status of Leak SitesUpon examining the status of leak sites operated in the second half of 2023, a total of 18 new leak sites were discovered. Among these, ClopTorrent, Ransomed, Knight, and Metaencryptor were identified as operating new sites alongside their existing ones. This expansion includes the introduction of new types of leak sites, such as those utilizing Torrent and Telegram, or occurred as a result of the ransomware groups’ rebranding efforts.
- Groups that added new types of leak sites (2): ClopTorrent, Ransomed
- Groups operating new leak sites after rebranding (2): Knight, Metaencryptor
Furthermore, there were changes in the status of some leak sites, including five groups that changed their leak site addresses and two that ceased operations.
- Groups with changed leak site addresses (5): Trigona, Ransomed, 8Base, BlackCat, Stormous
- Groups that ceased leak site operations (2): Trigona, Ragnar Locker
2.1.1. Leak sites were taken down in H2 2023
In the second half of 2023, compared to the first half, there was an increase in the number of takedown operations against leak sites. Notably, in October 2023, most of the infrastructure belonging to Trigona, including its leak site, was taken down by the Ukrainian hacktivist group UCA. This takedown resulted in the shutdown of Rocketchat and Atlassian services, related cryptocurrency wallet addresses, and development servers, temporarily halting operations. However, in January 2024, a new leak site associated with the Trigona ransomware group was discovered, indicating a continuation of their activities.
Subsequently, Europol disclosed a successful takedown of the infrastructure belonging to the Ragnar Locker ransomware group. It was revealed that key individuals associated with this ransomware operation group were arrested in France.
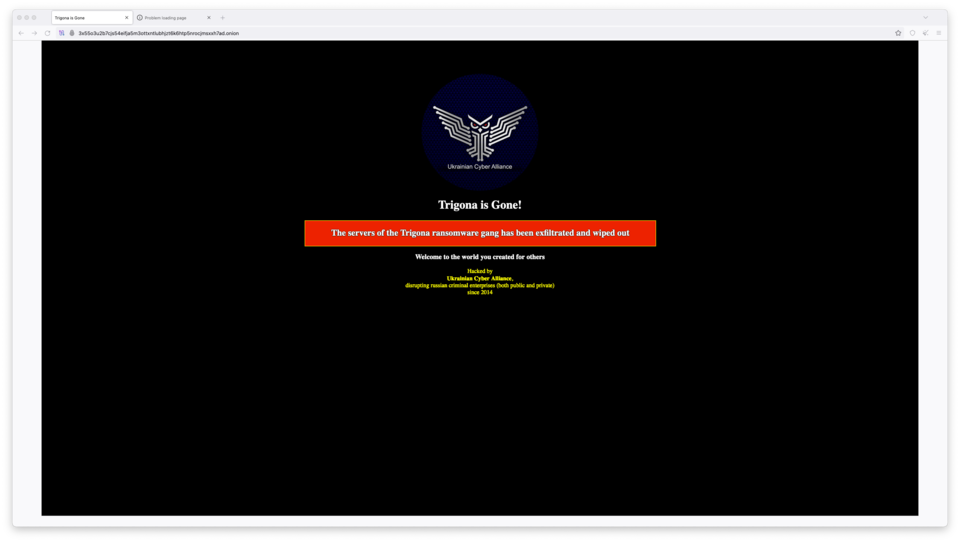
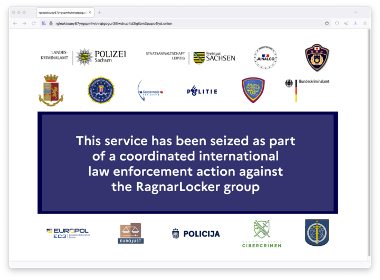 Figure 2. Take-down of the Trigona Leak Site (Left) / Figure 3. Take-down of Ragnar Locker Leak Site (Right)
Figure 2. Take-down of the Trigona Leak Site (Left) / Figure 3. Take-down of Ragnar Locker Leak Site (Right)In December 2023, the infrastructure of the BlackCat ransomware group was taken down by the FBI, and it was revealed that a decryption tool was distributed free of charge to approximately 500 affected companies. According to the search warrant released by the FBI, agents infiltrated the group as affiliates of the BlackCat ransomware, gaining access to the panel and subsequently obtaining decryption keys for the victimized companies. Following the takedown, the BlackCat ransomware group announced a new leak site address and has continued to be active. However, information about the victimized companies uploaded before the takedown was deleted.
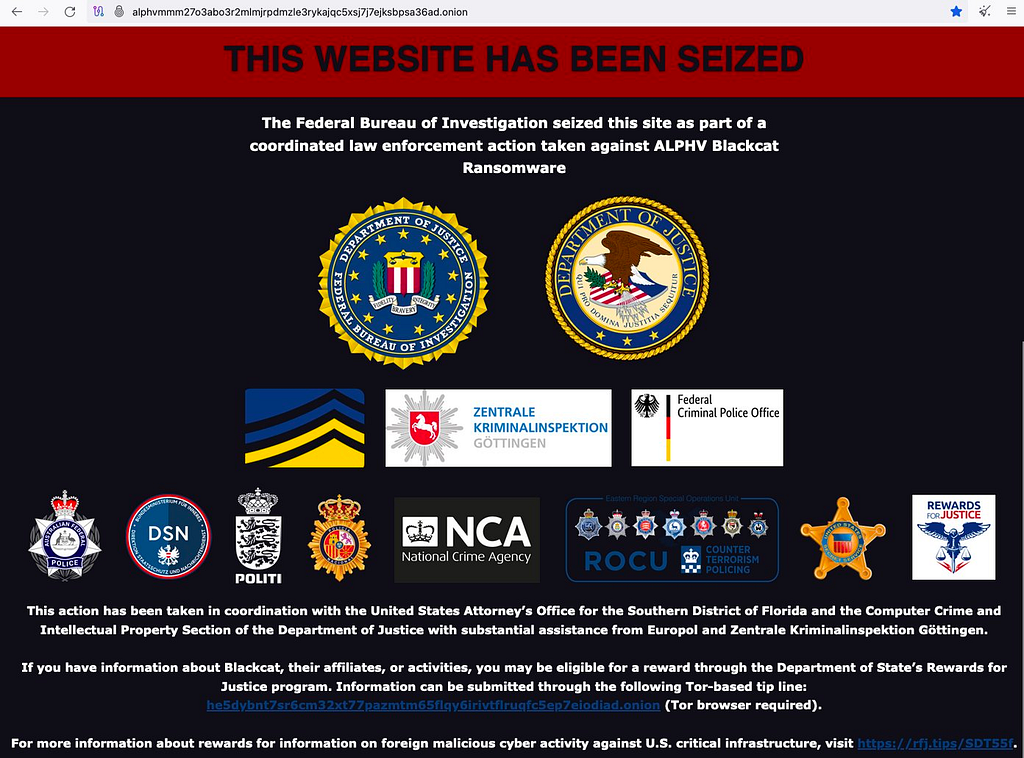 Figure 4. Temporarily Closed Leak Site of the BlackCat Ransomware Group
Figure 4. Temporarily Closed Leak Site of the BlackCat Ransomware Group2.1.2. Classification of Leak sites by type
Leak sites are operated to expose corporate victimization and leak stolen data. Recently, there has been an increase in the use of social media and Clearnet domains as leak sites, which are relatively easier to access and can be discovered through searches, as opposed to Onion sites. In the second half of the year, there was a notable addition of four groups utilizing Clearnet domains for their leak sites, a significant change considering no groups were using Clearnet domains in the first half of 2023.
- Ransomware group utilizing Torrent: CLOP
- Ransomware groups utilizing Clearnet domains: INC, Werewolves, Ransomed, Malek Team
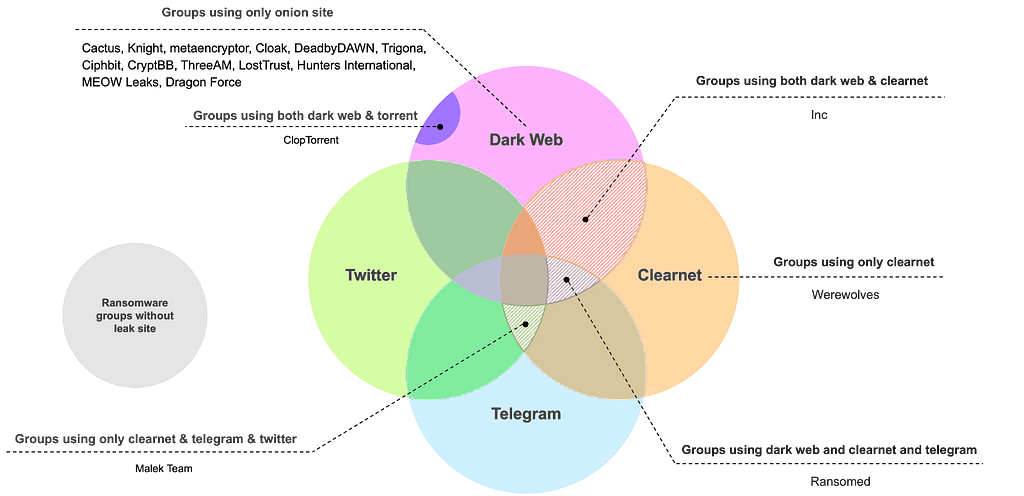 Figure 5. Ransomware Groups Among Newly Identified Groups with Discovered Leak Sites
Figure 5. Ransomware Groups Among Newly Identified Groups with Discovered Leak Sites2.1.3. Recent negotiation strategies used by ransomware groups
Ransomware groups traditionally use a method of extortion that involves posting victimized companies on leak sites and threatening to publicly release their data if the ransom is not paid within a specified period. However, recent findings have revealed that some ransomware groups have been identified as employing a new tactic of extortion based on established laws.
- The BlackCat ransomware group claimed to have infiltrated the network of MeridianLink, a digital loan solution company targeting financial institutions in the United States, on November 7, 2023. Subsequently, they exploited a rule set by the U.S. Securities and Exchange Commission (SEC), which mandates the disclosure of data within four business days following a cyberattack (as per Form 8-K, section 1.05), as leverage to demand ransom. After negotiations failed, on November 15, they reported the company to the SEC complaint page for not adhering to this rule, employing a threat tactic to further pressure the company.
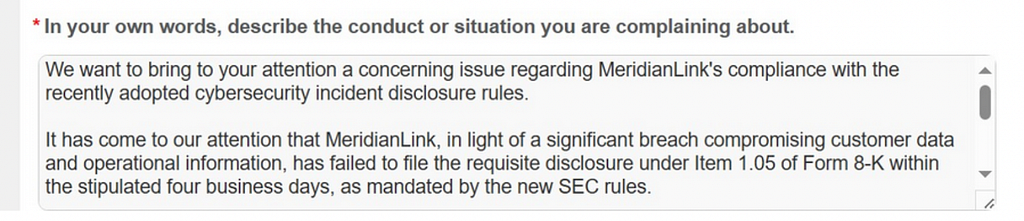 Figure 6. Content Submitted by the BlackCat Ransomware Group on the SEC Complaint Form (Source: Malwarebytes)
Figure 6. Content Submitted by the BlackCat Ransomware Group on the SEC Complaint Form (Source: Malwarebytes)- The Ransomed ransomware group claimed to have obtained data from a U.S. supply chain provider and employed a threat tactic by stating that failure to pay the ransom, resulting in the publication of the data, would necessitate reporting the breach in accordance with the European Union’s General Data Protection Regulation (GDPR).
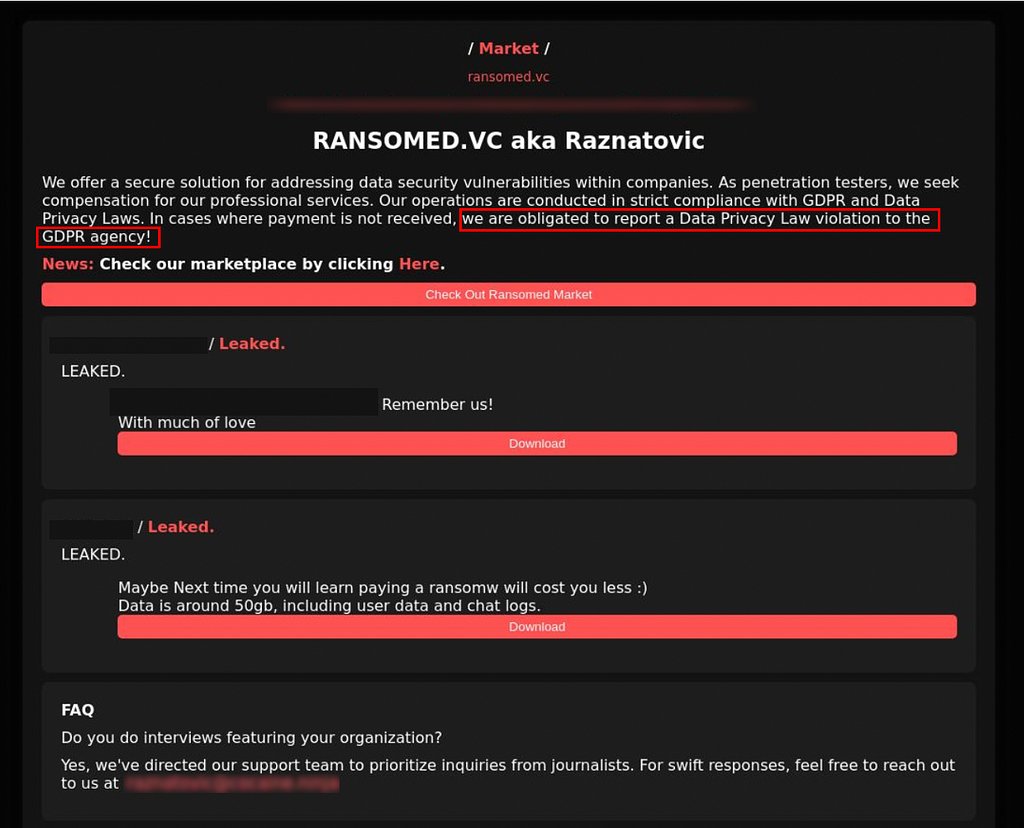 Figure 7. Screenshot of the Ransomed Leak Site
Figure 7. Screenshot of the Ransomed Leak Site2.2. Ransomware Family
Ransomware groups not only develop their ransomware but also purchase or use leaked source code and builders from other ransomware groups to customize or directly employ existing ransomware. In the second half of the year, it was identified that 13 new ransomware instances were created using builders or leaked source codes from other groups. While the Babuk family was predominantly used in the first half of the year, the second half saw a higher number of instances using the Chaos family.
- Among these, three groups (Knight, RA World, MEOW) have been confirmed to be operating leak sites as well.
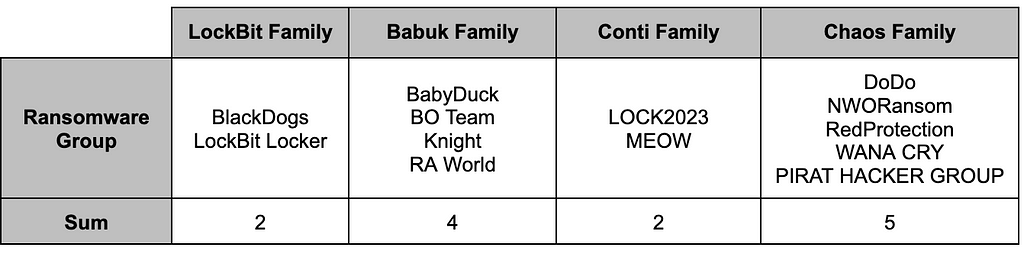 Table 2. Ransomware Groups Categorized by Ransomware Family Among Newly Identified Groups
Table 2. Ransomware Groups Categorized by Ransomware Family Among Newly Identified Groups2.2.1. LockBit Family
According to Analyst1, LockBit reportedly hired developers from the former BlackMatter ransomware group, and these developers created LockBit 3.0/Black based on the BlackMatter ransomware.
- The ransomware family based on LockBit refers to all ransomware created from the LockBit 3.0/Black builder, which was leaked by a developer in September 2022.
- Among the ransomware that emerged in the second half of the year, groups classified under the LockBit Family using the leaked LockBit 3.0/Black builder include BlackDogs and LockBit Locker ransomware.
— Sophos disclosed a campaign exploiting ColdFusion servers, in which attackers attempted to distribute BlackDogs ransomware, created with the previously leaked LockBit 3.0/Black builder.
— According to a statement from the Spanish Police, it has been announced that LockBit Locker persistently targets Spanish construction companies through phishing emails.
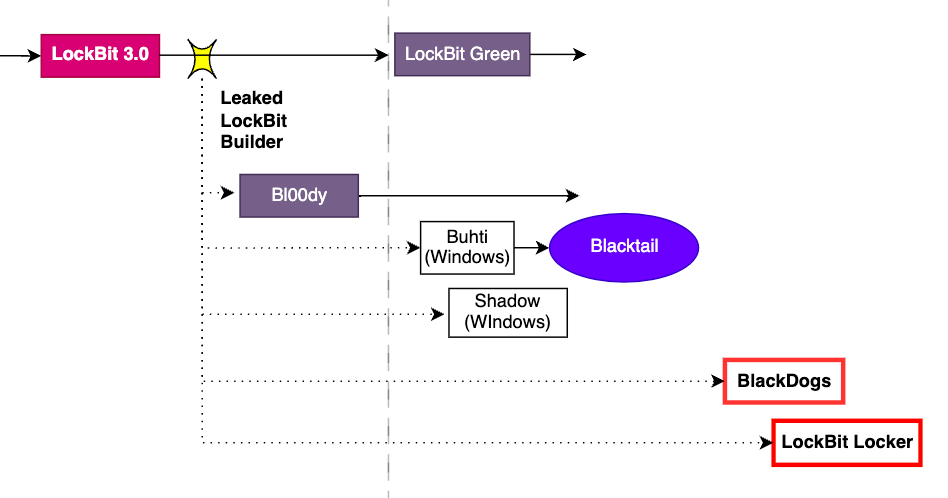 Figure 8. LockBit family ransomware
Figure 8. LockBit family ransomware2.2.2. Babuk Family
The Babuk Family refers to ransomware created using the builder and source code of Babuk ransomware, which were made public in June 2021 and leaked in September 2021, respectively.
- Among the ransomware that appeared in the latter half of the year, groups classified under the Babuk Family include RA World, Knight, BabyDuck, and BO Team ransomware.
— RA World was identified as a rebranding of the RA Group after the title on its existing leak site was changed to RA World, along with a change in the address. The ransomware binary continues to cite the Babuk source code, and the similarity in ransom notes has led to its identification as a rebranding of the RA Group.
— Knight, rebranded from the Cyclops group, was confirmed to quote the Babuk source code due to the encryption logic being significantly similar to that of Babuk ransomware, as identified by Uptycs.
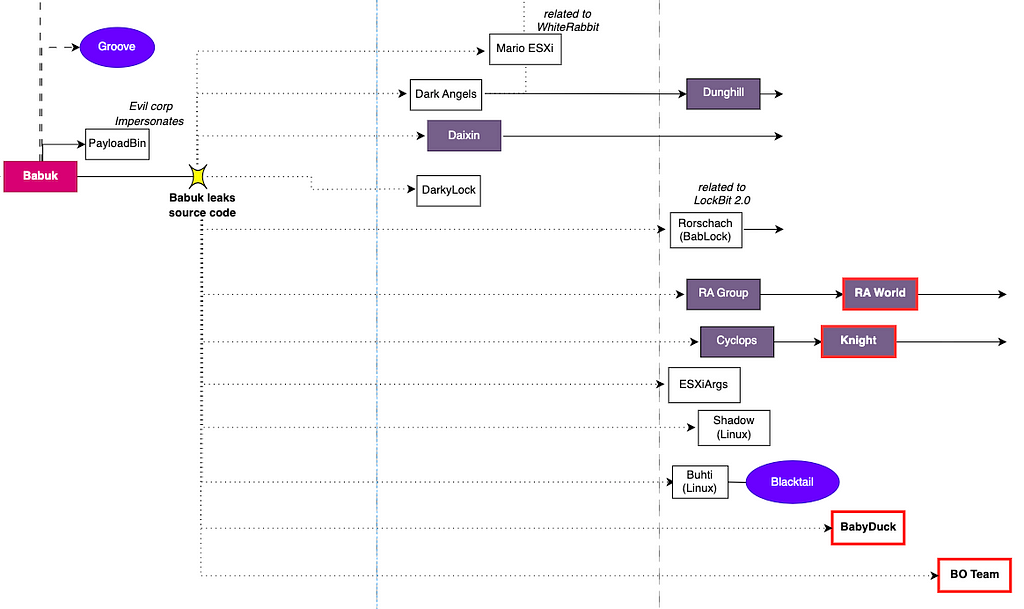 Figure 9. Babuk family ransomware
Figure 9. Babuk family ransomware2.2.3. Conti Family
In February 2022, the source code of Conti ransomware was leaked by an insider showing pro-Russian sympathies during Russia’s invasion of Ukraine. The Conti Family refers to ransomware created using the leaked source code of Conti ransomware, as well as ransomware derived from sub-groups of Conti, including Black Basta, BlackByte, and Royal.
- Among the ransomware that appeared in the first half of the year, groups classified under the Conti Family include Lock2023 and Meow ransomware.
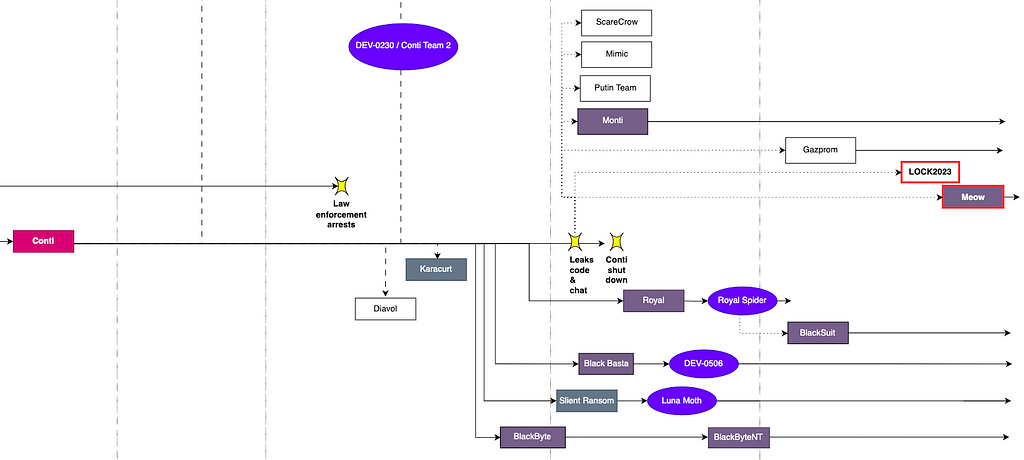 Figure 10. Conti family ransomware
Figure 10. Conti family ransomware2.2.4. Chaos Family
The Chaos Family refers to ransomware created using the Chaos ransomware builder, which was uploaded to dark web forums from June 2021 to seek advice from users.
Among the ransomware that appeared in the first half of the year, groups classified under the Chaos Family include DoDo, NWORansom, RedProtection, WANA CRY, and PIRAT HACKER GROUP ransomware.
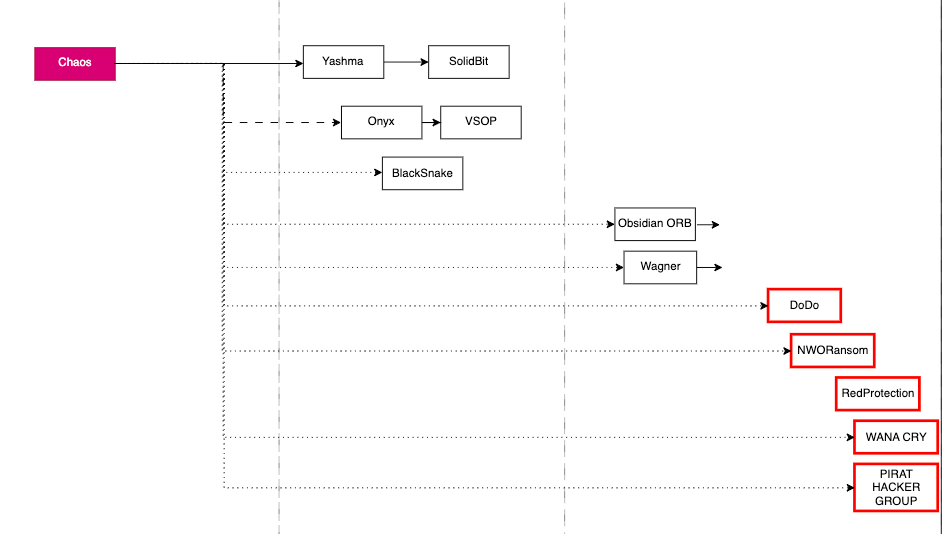 Figure 11. Chaos family ransomware
Figure 11. Chaos family ransomware3. Key Issues in the second half of the year
The following sections track the activities of both new and existing ransomware groups, summarizing major ransomware issues that occurred in the latter half of 2023. The key issues identified are categorized into major activities of Ransomware Groups and Affiliates, malware, and tools used in attack campaigns, vulnerability information, and duplicated victims.
3.1. Ransomware Groups
3.1.1. Version Control
Ransomware groups operating as Ransomware-as-a-Service (RaaS) consistently update their ransomware not only to evade detection and maintain their brand reputation but also to expand the range of targeted operating systems. The changes identified in the latter half of 2023 include the following trends.
BlackCat
- BlackCat ransomware was first publicly disclosed in December 2021, and LockBit mentioned that BlackCat ransomware is a rebranding of BlackMatter. An interview published by The Record also acknowledged its association with the BlackMatter group.
- Microsoft analyzed a new version of BlackCat ransomware, dubbed Sphynx, and identified it as BlackCat 3.0. This version attempts lateral movement within networks using the Impacket framework and includes the Remcom tool for executing commands remotely on other devices.
- According to BleepingComputer, Scattered Spider (Storm-0875), an affiliate of BlackCat, has been confirmed to be using BlackCat 3.0 since July 2023.
- In addition to ransomware version updates, in July 2023, BlackCat provided an API on its leak site to fetch various information about new victims, enhancing its operational capabilities.
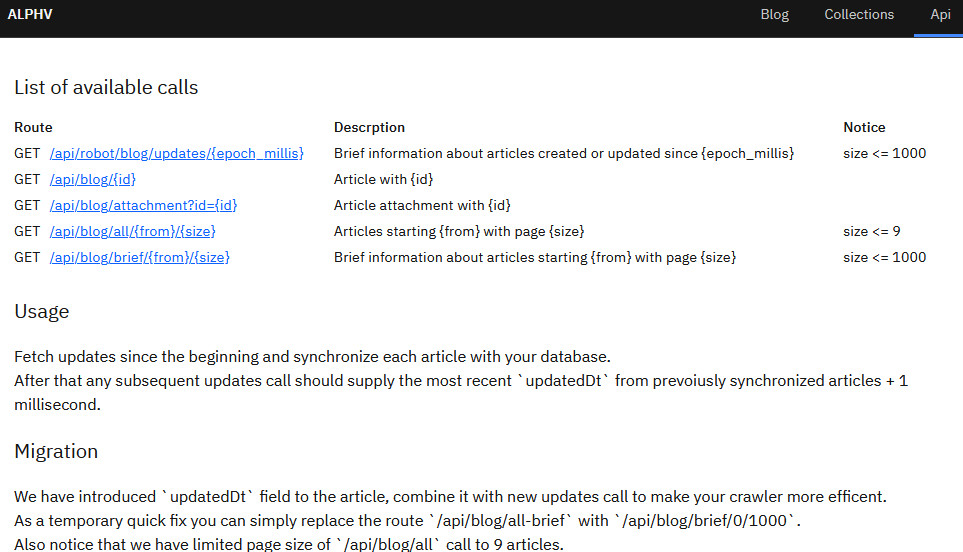 Figure 12. API List of the BlackCat Leak Site (Source: BleepingComputer)
Figure 12. API List of the BlackCat Leak Site (Source: BleepingComputer)AKIRA
- The AKIRA ransomware group has been confirmed to be active since at least March 2023, and in June 2023, they released a version of their ransomware for Linux.
- Avast released a decryption tool capable of decrypting files encrypted by both the Windows and Linux versions of AKIRA ransomware. In July 2023, the AKIRA ransomware group launched a new version of their ransomware with a patch for the encryption flaw.
- In August 2023, the ransom note of a ransomware named Megazord, which was developed based on the Rust language, indicated the use of the AKIRA group’s infrastructure. It remains unclear whether Megazord ransomware is a new version or a rebranded group.
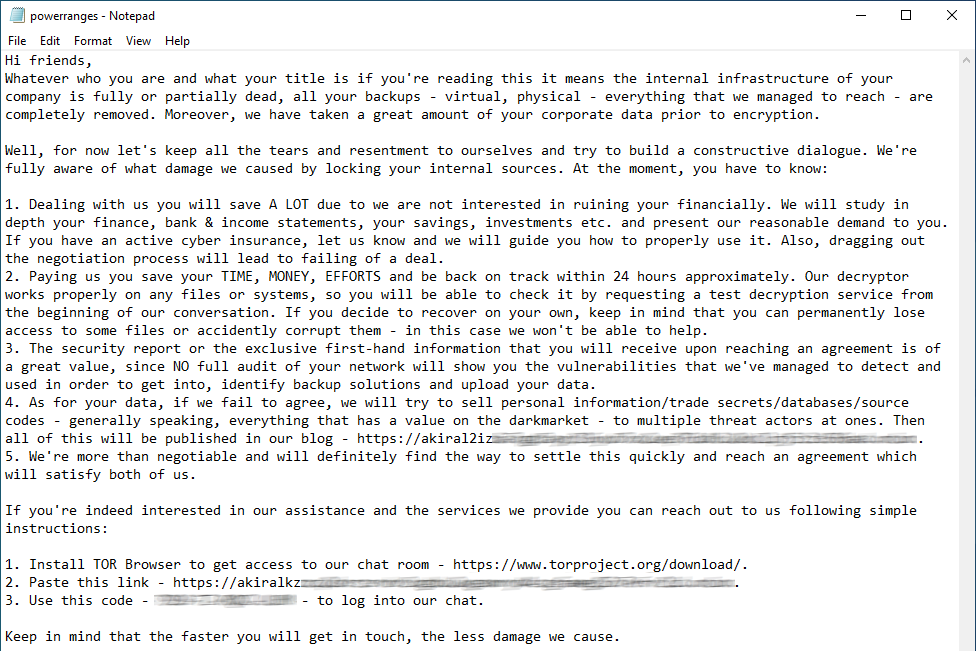 Figure 13. Megazord Ransom Note (Source: X)
Figure 13. Megazord Ransom Note (Source: X)Monti
- Monti, not only shares the name but also exhibits very similar TTPs to Conti ransomware, gaining attention as one of the notable ransomware variants. It is believed to have been crafted using the leaked source code of Conti.
- According to Trend Micro, while previous ransomware variants that utilized the leaked Conti source code replicated it entirely, a new Linux version of the ransomware has been discovered, which only partially quotes the original source code.
Knight
- Knight is a rebranded group of the Cyclops ransomware group, which updated its RaaS program extensively in July 2023, promoting it as the Knight version of Cyclops 2.0.
- In October 2023, they further updated to version 3.0, introducing improvements such as enhanced encryption speed, random obfuscation, and file icon replacement. Additionally, they added features like a management panel, encrypted chat rooms, and the ability to directly add their wallet addresses.
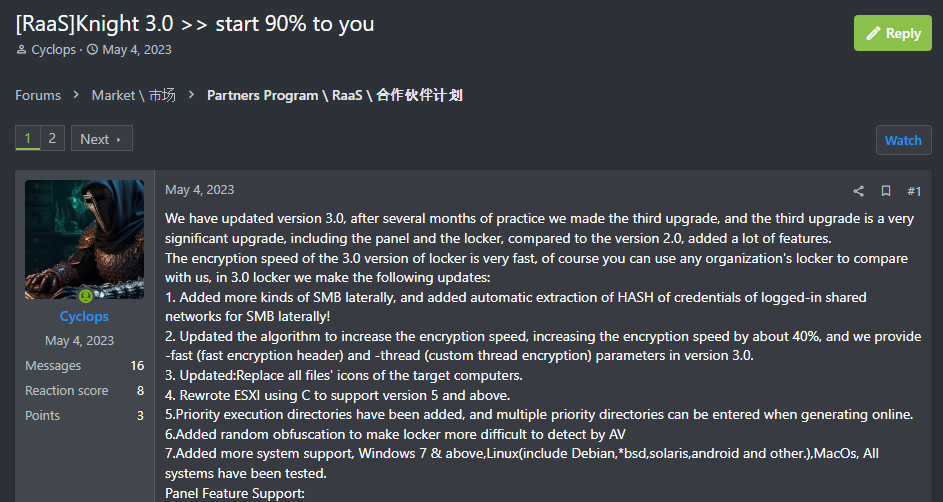 Figure 14. Knight 3.0 RaaS Advertising Post
Figure 14. Knight 3.0 RaaS Advertising PostBig Head
- Big Head ransomware was first discovered in May 2023, with two variants found disguised as Windows Update and Microsoft Word software at the time of discovery.
- Subsequently, Trend Micro attempted additional hunting using these variants and discovered three versions of Big Head ransomware that utilized the same email and Telegram addresses in their ransom notes.
- While all three versions included additional payloads in their resources, they differed in the malicious actions performed by these payloads.
— The first version included an EXE file serving as the attacker’s Telegram address and command control.
— The second version revealed a stealer behavior aimed at extracting information from the victim system.
— The third version was identified to use Neshta in its infection chain.
Qilin
- Also known as Agenda ransomware, Qilin ransomware is written in the Go language and was first discovered in August 2022.
- Trend Micro, the first to discover Qilin ransomware, mentioned that the Tor site used for paying ransoms by victimized companies resembles those used by Black Basta and BlackMatter ransomware.
- In December 2023, a sample of Qilin ransomware targeting VMware ESXi was found. This variant was confirmed to be a new ransomware strain, not derived from the leaked source code of Babuk, despite citing it as a reference.
3.1.2. Revealed connections between ransomware groups
During the second half of 2023, ransomware groups continued to evolve not only by updating their binaries but also by altering attack strategies through cooperation between groups. Additionally, they engaged in rebranding efforts to manage affiliates and maintain their reputations. Here are some highlights of the observed interrelations and rebranding efforts among ransomware groups:
NoEscape — Avaddon (Rebrand)
- The NoEscape ransomware group began its operations in June 2023, targeting Windows, Linux, and VMware ESXi systems.
- The Avaddon ransomware group ceased its operations and shared decryption keys in June 2021, a month after the FBI released a warning about Avaddon-related activities.
- Ransomware expert Michael Gillespie noted that the ransomware used by both NoEscape and Avaddon shared nearly identical encryption logic, except for the file encryption algorithms (NoEscape: Salsa20/Avaddon: AES). Additionally, researchers confirmed matching Config values between the two.
- While there is a possibility that NoEscape obtained the source code from Avaddon, some researchers speculate that certain core members of Avaddon may have joined the NoEscape group.
BlackSuit — Royal (Rebrand)
- BlackSuit was first discovered by Unit42 in May 2023, targeting both Windows and Linux systems.
- Subsequently, Trend Micro revealed that BlackSuit and Royal ransomware showed a very high similarity in functionality, blocks, and jumps, with over 98% similarity based on BinDiff-based similarity checks. They also shared similar features in execution parameters and intermittent encryption based on size.
- In September 2023, evidence emerged that both BlackSuit and Royal ransomware were using the same Onion Share address for leaking stolen data, leading to speculation that BlackSuit might be a rebranded version of the Royal group.
- Interestingly, while the Leak site for Royal ransomware has not been updated with new victim companies since July, the Leak site for BlackSuit ransomware has been continuously updated with new victim companies since June 2023, indicating a potential rebranding process during this period.
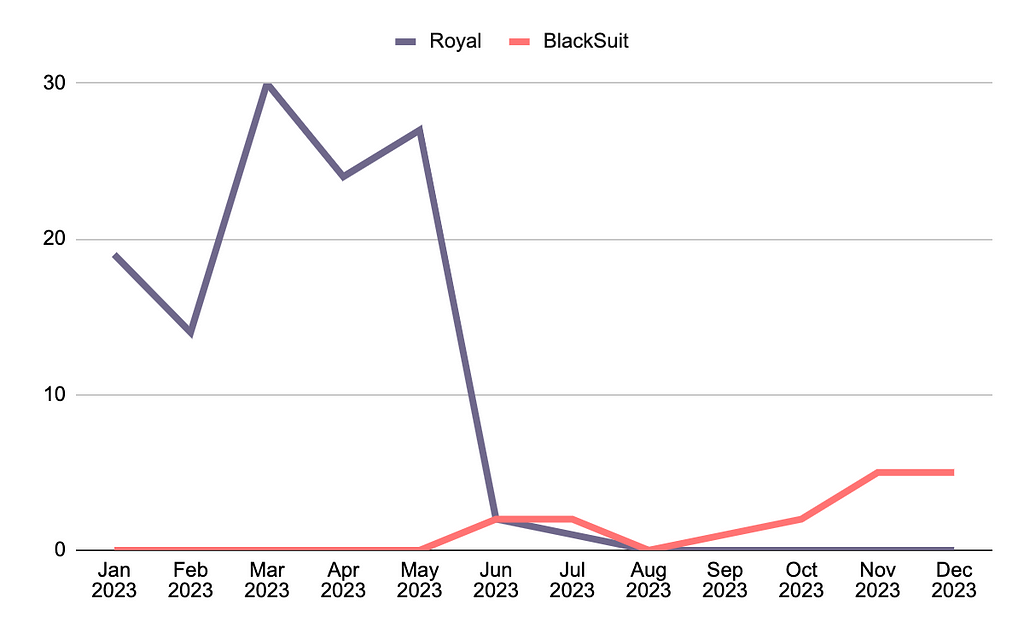 Figure 15. Timeline of Activities for Royal and BlackSuit Based on Leak Sites
Figure 15. Timeline of Activities for Royal and BlackSuit Based on Leak SitesLostTrust — SFile, Mindware, Metaencryptor (Rebrand)
- LostTrust ransomware first emerged in September 2023, with SentinelOne mentioning it as a rebranded group of Metaencryptor, which began its activities in August 2023. Both ransomware groups were noted to use the same template for their leak sites, and while they did not upload overlapping victim companies, their TOX addresses listed in the blogs were identical.
- Furthermore, SentinelOne claimed that LostTrust ransomware evolved from Mindware and SFile ransomware, which started operating in March 2022. This assertion was supported by the similarities observed in the execution parameters, strings present within the binaries, and certain phrases identified in the ransom notes used by each ransomware variant.
AKIRA — Conti, Snatch (Rebrand, Cooperation possible)
- AKIRA ransomware shares several code similarities with Conti ransomware, including the list of files and directories excluded from encryption, the ChaCha algorithm, key generation code, and the structure of encrypted files.
- Additionally, according to Arcticwolf, blockchain analysis of Bitcoin transactions related to AKIRA revealed funds flowing from AKIRA wallet addresses to addresses associated with Conti on at least three occasions.
- In August 2023, Stairwell discovered some tools used by the AKIRA ransomware operators via OpenDir. Analysis of the targeted companies revealed that one consulting firm targeted by these tools had suffered from Snatch group attacks approximately two months earlier, around early June, suggesting a connection between the two incidents.
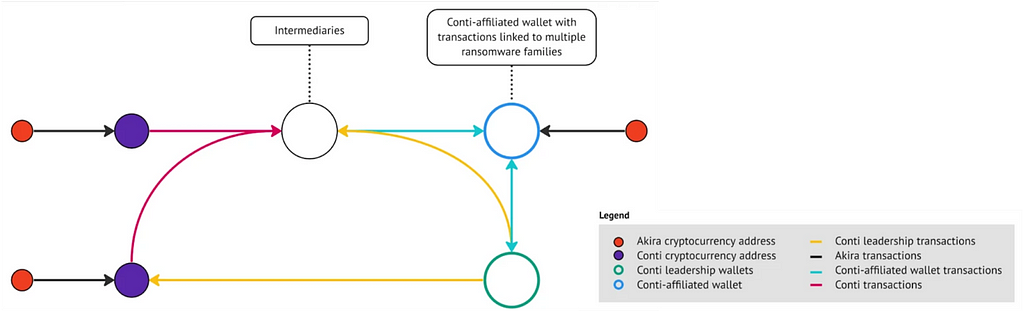 Figure 16. Blockchain analysis for AKIRA and Conti (Source: Arcticwolf)
Figure 16. Blockchain analysis for AKIRA and Conti (Source: Arcticwolf)Rhysida — Vice Society (Rebrand possible)
- Rhysida was first detected in May 2023 and gained attention by leaking documents related to the Chilean Army on leak sites. As their attacks expanded into the healthcare sector, the U.S. Department of Health and Human Services (HHS) designated the group as a significant threat, issuing a report on their activities.
- Following the emergence of Rhysida, there was a decline in Vice Society ransomware activity. The overlap in targeted sectors, particularly in the education field, and the striking similarity in Tactics, Techniques, and Procedures (TTPs) suggest a connection between Rhysida and Vice Society.
- In December 2023, the Korea Internet & Security Agency (KISA) distributed decryption tools for Rhysida ransomware.
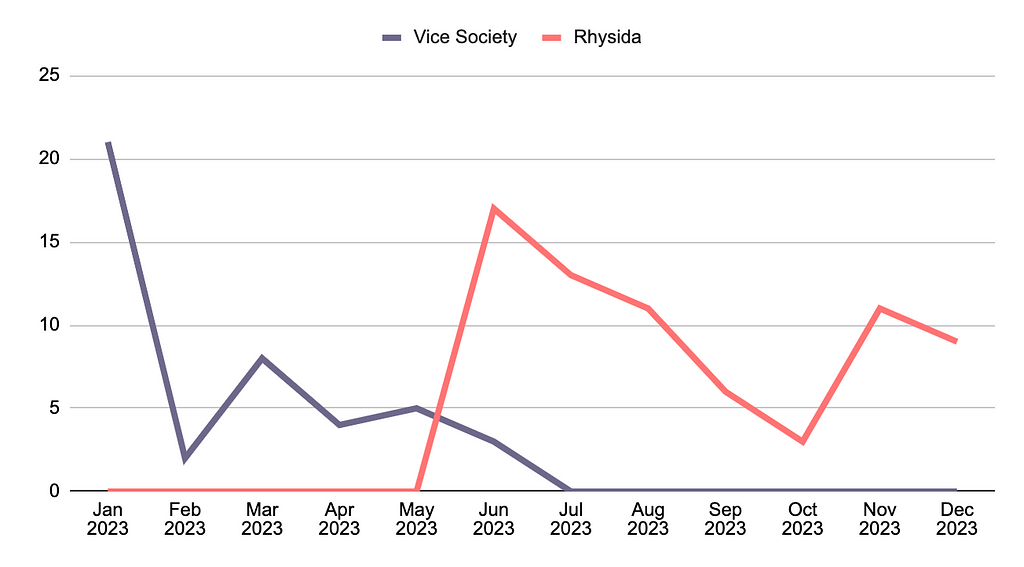 Figure 17. Timeline of Activities for Vice Society and Rhysida Based on Leak Site Activities
Figure 17. Timeline of Activities for Vice Society and Rhysida Based on Leak Site ActivitiesHunters International — Hive (Rebrand possible)
- Hunters International was initially discovered in October 2023 and was speculated to be a rebranding of the Hive ransomware group, which was taken down by the FBI and Europol. This speculation arose due to at least a 60% code similarity between Hunters International and the Hive ransomware group.
- However, Hunters International issued an official statement refuting the claims of being a rebranding of the Hive group.
— They stated that they had acquired legacy C and Go language source codes from Hive and identified bugs in the decryption process, which they subsequently fixed.
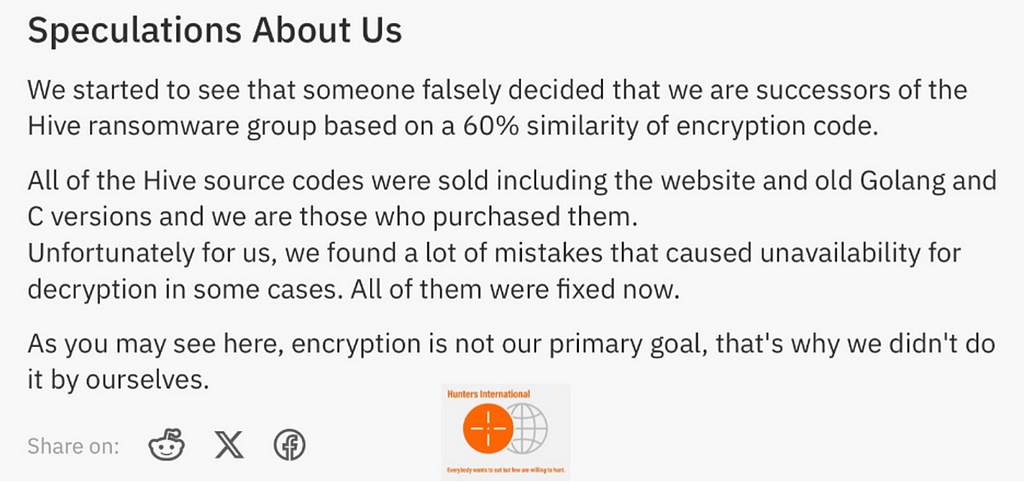 Figure 18. Statement of Hunters International
Figure 18. Statement of Hunters InternationalUnderground — Industrial Spy (Rebrand possible)
- Underground ransomware was first discovered in July 2023 and has been associated with the attack group tracked by Microsoft as Storm-0978.
- The Storm-0978 group is known to use the Industrial Spy ransomware, and it was confirmed in July 2023 that they explicitly identified themselves as the “Underground team” in the ransom notes.
- Both ransomware binaries share similar codes, and they utilize Onion sites with similar themes for negotiating with victimized companies, suggesting that Underground ransomware is a rebranded version of Industrial Spy.
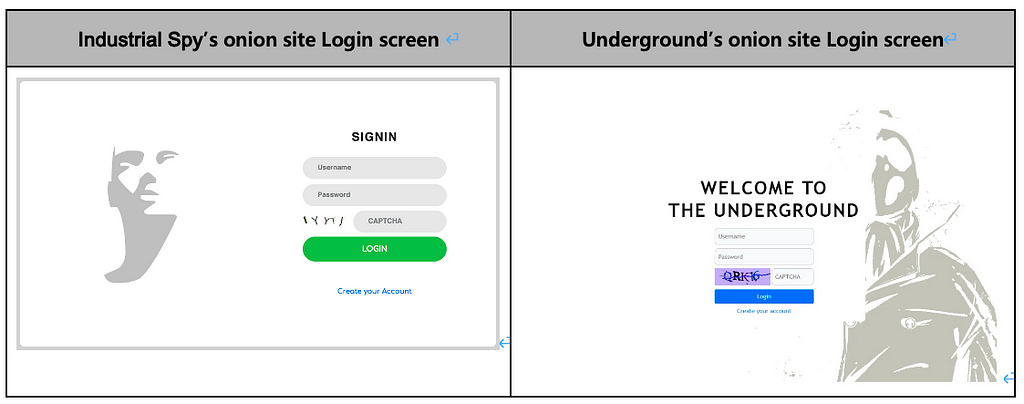 Figure 19. Login screen of Industrial Spy’s Onion site (left) / Figure 20. Login screen of Underground’s Onion site (right)
Figure 19. Login screen of Industrial Spy’s Onion site (left) / Figure 20. Login screen of Underground’s Onion site (right)CLOP — Stormous (Cooperation possible)
- CLOP emerged in February 2019 with a ransomware variant called CryptoMix and remains active to this day.
- Stormous group posted messages on the Leak site mentioning several CyberCrime groups, indicating collaboration with them, including CLOP. However, there is currently no clear evidence confirming a direct association between the two groups.
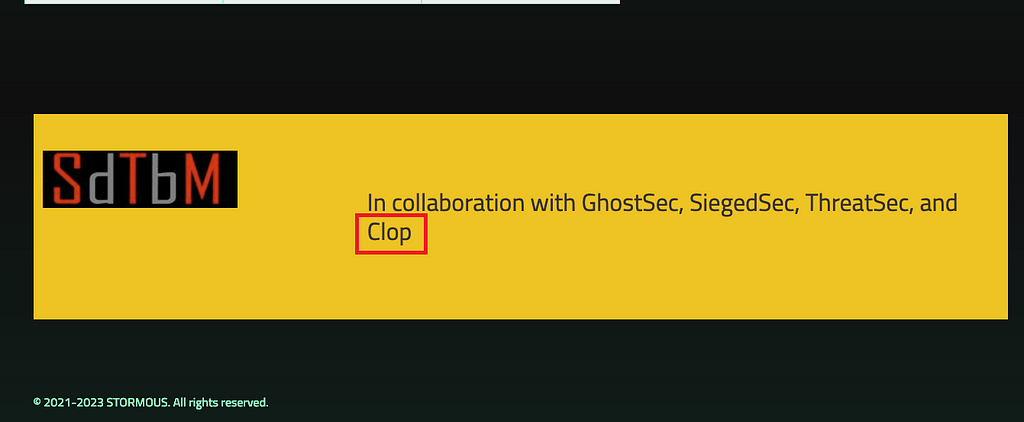 Figure 21. Cooperation message within Stormous Leak Site
Figure 21. Cooperation message within Stormous Leak SiteEverest — Ransomed (Cooperation possible)
- The Everest group began its activities in November to December 2020. On December 16, 2020, a Leak site named Everest ransom team was publicly disclosed.
- On August 1, the Everest group recruited other groups to collaborate on their Leak site until August 7. Subsequently, in early September, they collaborated with the Ransomed group to infiltrate corporate networks, steal data, and upload it to the Leak site.
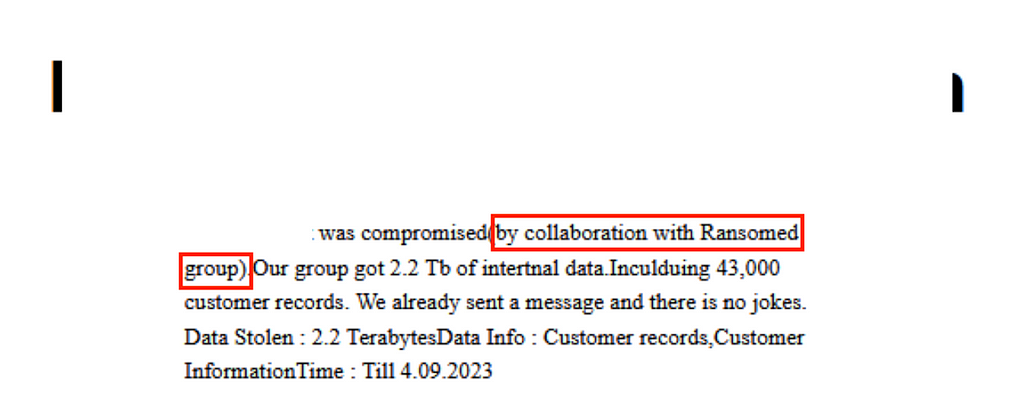
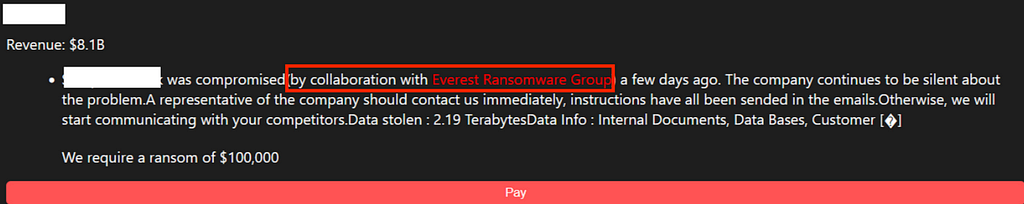 Figure 19. Cooperation message within Everest’s Leak site (left) /
Figure 19. Cooperation message within Everest’s Leak site (left) / Figure 20. Cooperation message within Ransomed’s Leak site (right)
BianLian — RansomHouse & White Rabbit & Mario (Cooperation possible)
- The BianLian group first emerged in 2019, initially appearing with Android malware. However, true to its name, which means “face-changing” in Chinese, the group shifted tactics to ransomware attacks in July 2022.
- Affiliates using both the White Rabbit and Mario ransomware are suspected to be associated with RansomHouse, as indicated by the use of RansomHouse’s infrastructure such as Leak sites and Telegram channels in the ransom notes of White Rabbit and Mario.
- Operators of the White Rabbit and Mario ransomware conducted a three-month-long attack on a financial services company in Singapore. Following this attack, a forum user named Paulsen publicly disclosed the stolen data on the forum, which was subsequently posted on the Leak sites of RansomHouse and BianLian. This suggests a shared Affiliate relationship between BianLian and RansomHouse.
3.2. Affiliate
An “Affiliate” refers to an individual or group that collaborates with RaaS (Ransomware as a Service) operators to carry out actions such as initial penetration, network traversal, data exfiltration, and ransomware distribution. In this report, the term “Affiliate” has been approached differently from its conventional meaning, encompassing all users or groups who assist in initial access. Affiliates have been further categorized into two aspects:
- Initial Access Broker: Users or groups within the deep dark web who sell access information for individuals and specific companies.
- Pentester: Users or groups responsible for the initial penetration phase to disseminate ransomware payloads.
3.2.1. Initial Access Broker
RaaS operators procure initial access permissions for their targets from various deep and dark web forums through the activities of IABs (Initial Access Brokers). A summary of publicly disclosed information regarding IABs who collaborated with RaaS operators in the second half of 2023 is as follows:
Egregor, MountLocker, CryptoDefense: GOLD MELODY
- GOLD MELODY, also known as Prophet Spider or UNC961, is identified as an IAB that has been active since at least 2017.
- Secureworks has publicly disclosed tools, infrastructure, and TTPs (Tactics, Techniques, and Procedures) related to GOLD MELODY through investigations into five security incidents. Following these breaches, access rights were transferred to others, and ransomware such as Egregor, MountLocker, and CryptoDefense was distributed.
— It is suspected that GOLD MELODY has been active as an IAB, generating revenue by selling initial access permissions to other affiliates or RaaS operators.
Black Basta: Storm-1674
- Storm-1674 is an Access Broker known for distributing DarkGate based on the open-source tool TeamsPhisher.
- This group typically sends malicious emails containing malicious attachments via Teams. Within the ZIP file of the attachment, they employ a method of dropping DarkGate and PikaBot ultimately through LNK files.
- According to Microsoft, during a campaign in September 2023, a handoff from Storm-1674 to a ransomware operator was identified, ultimately leading to the distribution of the Black Basta ransomware.
3.2.2. Pentester
A “Pentester” refers to an attacker who infiltrates the internal infrastructure of a target to distribute ransomware, playing a crucial role in RaaS (Ransomware as a Service) operations. RaaS operators collaborate with these individuals through affiliate programs, and pentesters utilize the ransomware provided by RaaS to encrypt files after infiltrating the target’s internal systems, coercing the victimized organizations into paying a ransom. They then transfer a portion of the ransom, determined by the predefined distribution ratio set by the RaaS, to the operator and keep the majority of the funds for themselves. The pentesters disclosed in the second half of 2023 are as follows:
BlackCat: Scattered Spider(0ktapus)
- Scattered Spider, first identified by Group-IB in August 2022, is a CyberCrime group primarily known for conducting initial access through phishing SMS messages.
- According to BushidoToken, a foreign security analyst, connections between Scattered Spider and BlackCat have been revealed.
— Following the Reddit breach incident involving Scattered Spider in February 2023, BlackCat posted Reddit as a victim on their Leak site in June.
— BlackCat affiliates used POORTRY, the same tool utilized by UNC3944.
— The Canadian Centre for Cyber Security (CCCS) published advisory notes on BlackCat attacks targeting Canadian organizations. The TTPs (Tactics, Techniques, and Procedures) disclosed in the advisory closely resembled those previously published by Scattered Spider, along with IoCs (Indicators of Compromise).
Quantum, Nokoyawa, BlackCat, Royal, CLOP, Cactus, Play: ShadowSyndicate
- ShadowSyndicate is a Threat Actor known for collaborating with various ransomware groups and affiliates, starting its activities at least since July 2022.
- ShadowSyndicate has conducted attacks using tools such as Cobalt Strike, IcedID, and Sliver. It was revealed that multiple servers shared the same SSH fingerprint (1ca4cbac895fc3bd12417b77fc6ed31d), with at least 52 servers being utilized as part of Cobalt Strike’s C2 framework.
- Group-IB considers ShadowSyndicate to be an affiliate of several RaaS groups. RaaS groups suspected to have connections with ShadowSyndicate include Quantum, Nokoyawa, BlackCat, Royal, CLOP, Cactus, and Play.
3.3. Attack Techniques
Attackers constantly evolve their Tactics, Techniques, and Procedures (TTPs), including the malware, tools, and vulnerabilities they use, to evade detection. Similarly, RaaS operators and affiliates continue to evolve to distribute ransomware and acquire funds from targets. Below are the major ransomware distribution campaigns disclosed in the second half of 2023.
(A separate timeline for issues occurring in the second half is attached in Appendix A.)
3.3.1. Malware & Tools
During the second half of 2023, a list of malware and custom tools confirmed to have been used by ransomware groups and affiliates is as follows in Table 3:
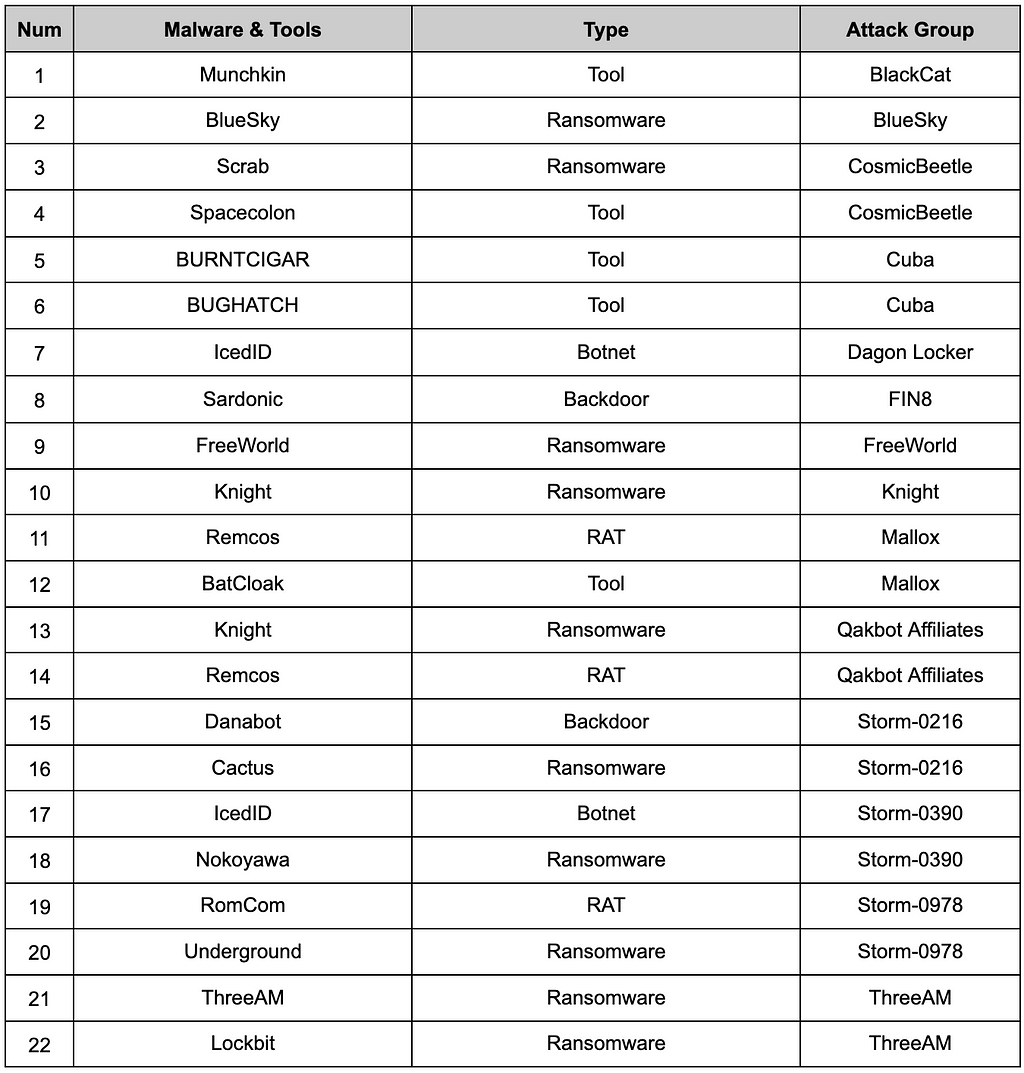 Table 3. List of Malware and Tools Used in Campaigns:
Table 3. List of Malware and Tools Used in Campaigns:In addition, numerous ransomware groups utilize open-source and cracked commercial utility tools to carry out attacks for credential theft and ransomware distribution. Based on information disclosed during the second half of the year, utility tools used by ransomware groups were examined. It was found that Cobalt Strike was the most commonly used, followed by Mimikatz and PsExec in descending order of frequency.
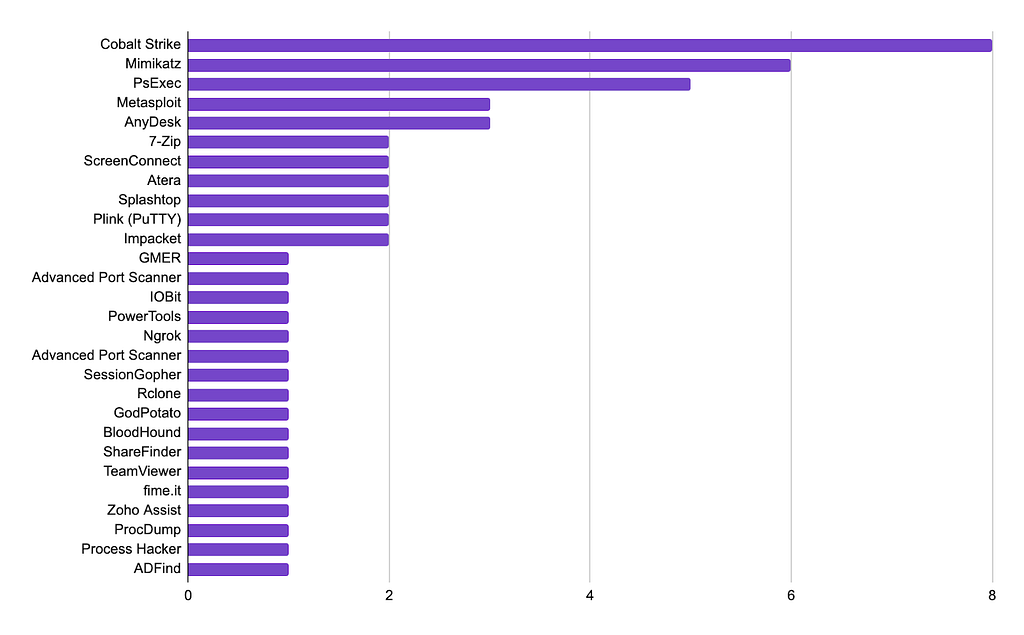 Figure 24. List of Open-Source and Cracked Commercial Utility Tools Used in Campaigns:
Figure 24. List of Open-Source and Cracked Commercial Utility Tools Used in Campaigns:3.3.2. Vulnerabilities
During the second half of the year, there were 17 groups identified as using vulnerabilities in major attack campaigns, with a total of 16 vulnerabilities exploited by these groups. Among these, 12 vulnerabilities were exploited using publicly disclosed vulnerabilities (1-day), while 4 vulnerabilities were exploited using undisclosed vulnerabilities (0-day). The list of vulnerabilities exploited by ransomware groups during the second half of the year is as follows:
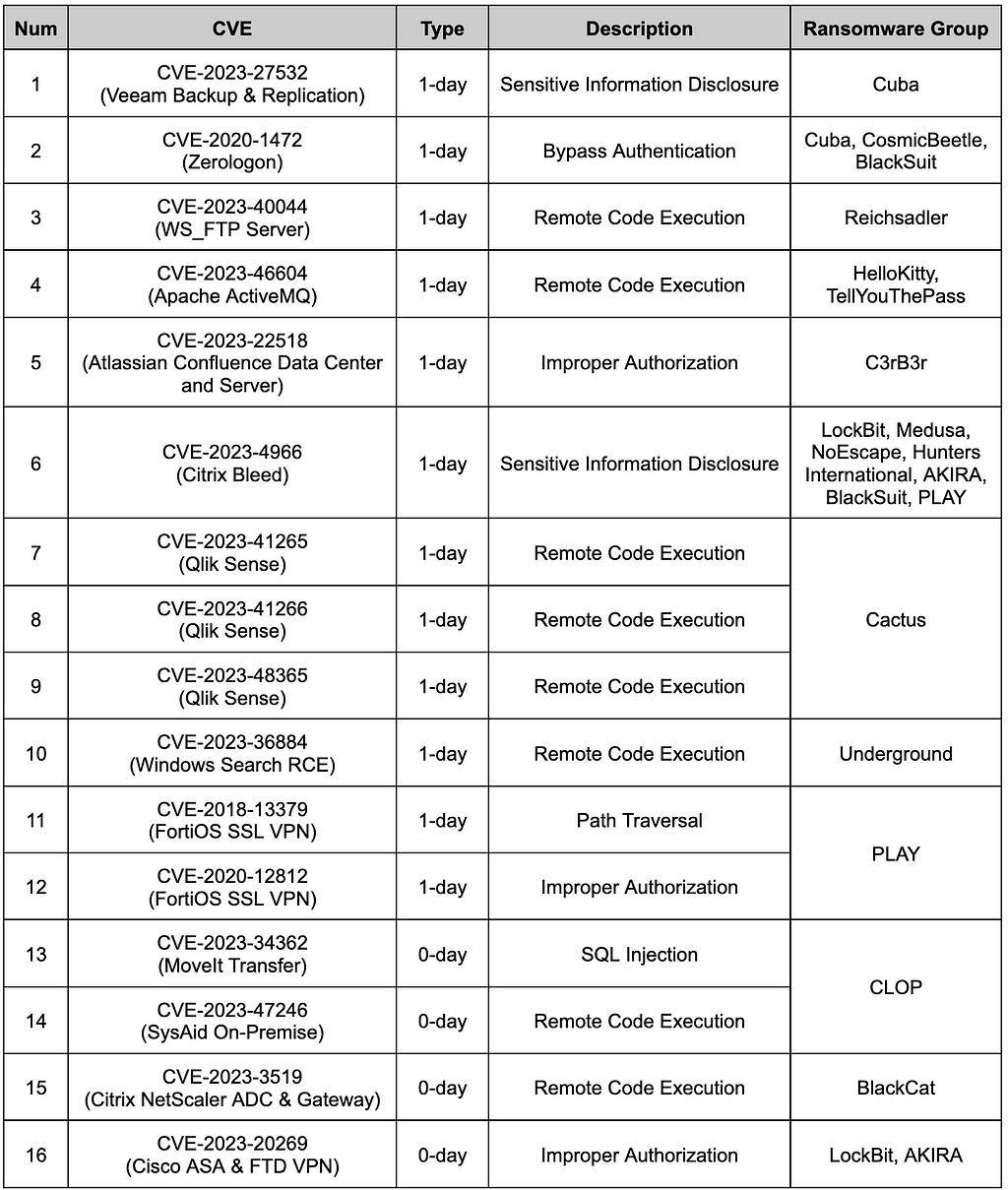 Table 4. List of CVE exploited in Campaigns
Table 4. List of CVE exploited in CampaignsAmong ransomware groups, LockBit, AKIRA, CLOP, and BlackCat utilized 0-day vulnerabilities. CLOP stands out, having exploited 2 0-day vulnerabilities throughout the period and causing damage to over 160 companies in July 2023 alone through the MoveIt Transfer vulnerability. Additionally, the LockBit and Cuba ransomware groups each targeted 2 systems or software with vulnerabilities, while the Cactus ransomware group exploited 3 vulnerabilities in Qlik Sense software.
The CVE-2023–4966 vulnerability, also known as Citrix Bleed, found in NetScaler ADC & NetScaler Gateway devices, was exploited by at least 7 ransomware groups and had the most significant impact during the second half of the year. Companies affected by this vulnerability were even uploaded to Leak sites associated with LockBit and Medusa. According to available reports, multiple attack groups including AKIRA and Hunters International were found to have exploited the Citrix Bleed vulnerability. Indeed, there was a trend of an increase in the number of affected companies uploaded to Leak sites coinciding with the onset of each ransomware group exploiting this specific vulnerability.
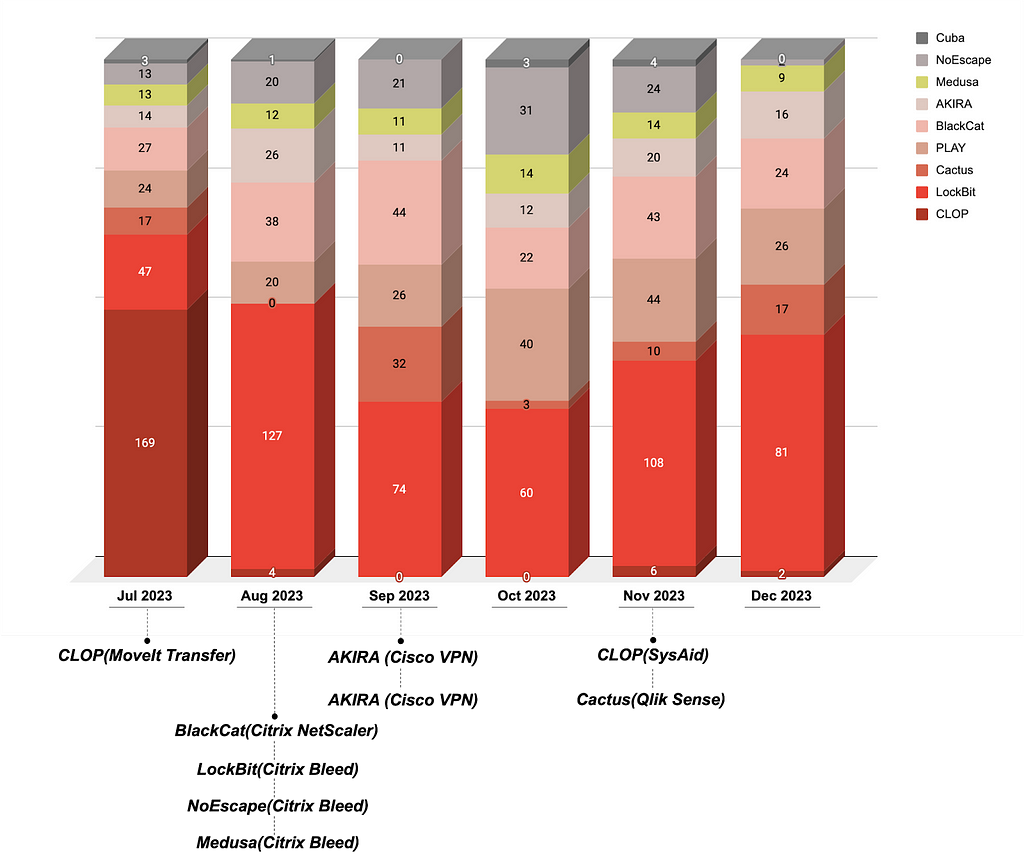 Figure 25. Number of Affected Companies by Ransomware Groups Exploiting Vulnerabilities
Figure 25. Number of Affected Companies by Ransomware Groups Exploiting Vulnerabilities3.4. Activities in DDW & Telegram
Ransomware groups are active on various deep and dark web forums as well as Telegram channels to recruit affiliates, promote RaaS, and purchase initial access permissions from Initial Access Brokers (IABs).
3.4.1. Posts for promoting RaaS
In recruitment advertisements from existing ransomware groups, they typically seek RaaS members without specifying detailed roles, often directing potential recruits through instant messaging platforms like TOX, Jabber, or DM (Direct Message) within forums. Some advertisements are relatively specific, targeting pentesters who specialize in infiltrating the internal infrastructure of target organizations to distribute ransomware.
However, in the recruitment advertisements observed in 2023, ransomware groups provided more detailed job descriptions, indicating a broader diversity of roles such as journalists, software engineers, providers, and OSCP (Offensive Security Certified Professional) professionals. This suggests that the composition of ransomware group members is systematically evolving, indicating a more structured approach to recruitment.
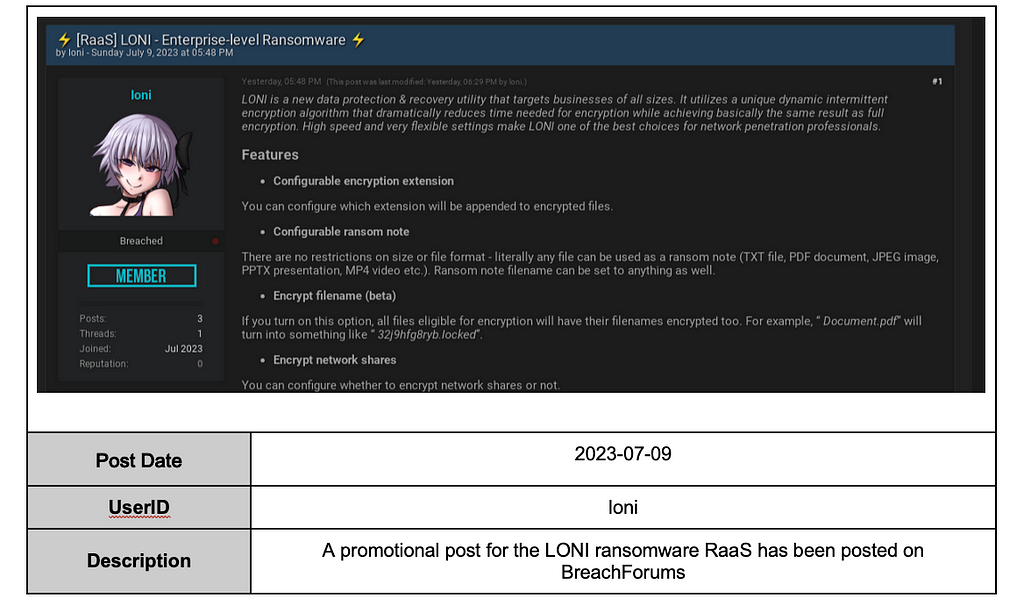
LONI Ransomware
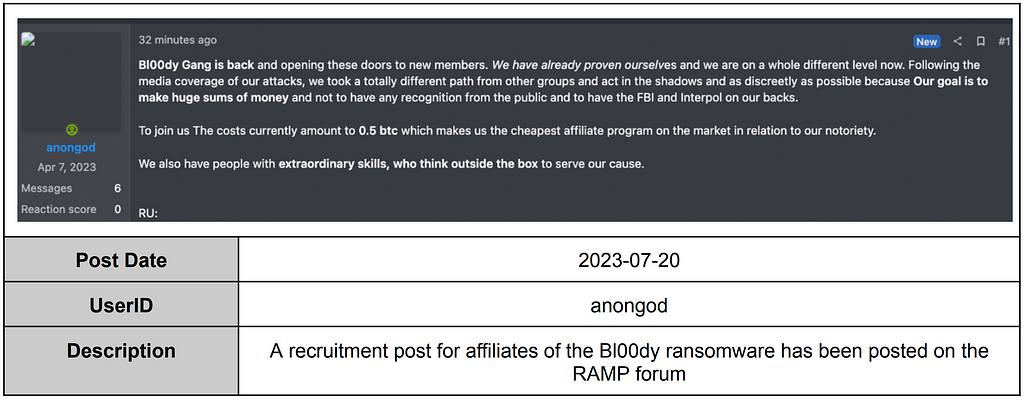
Bl00dy Ransomware
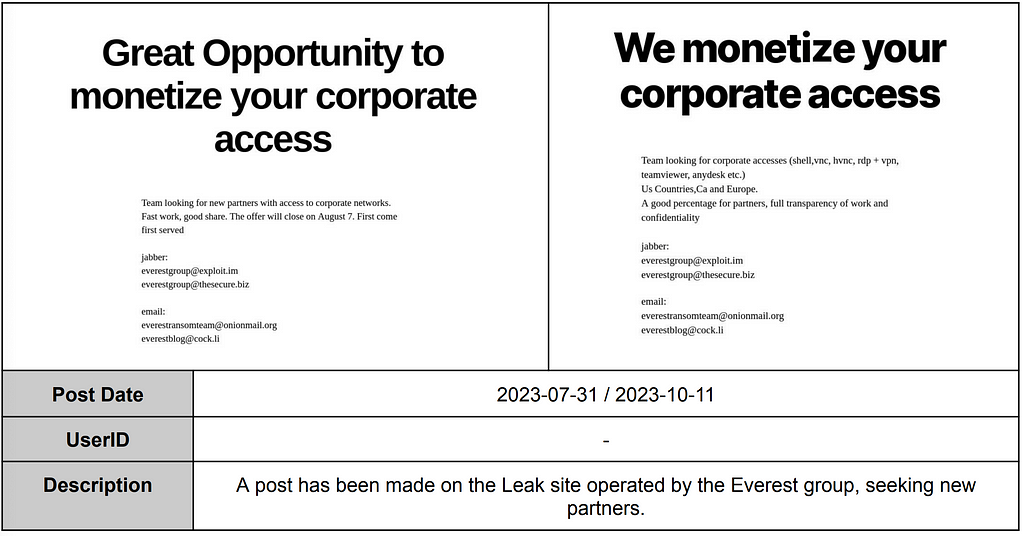
Everest
Mimic Ransomware
Kuiper Ransomware
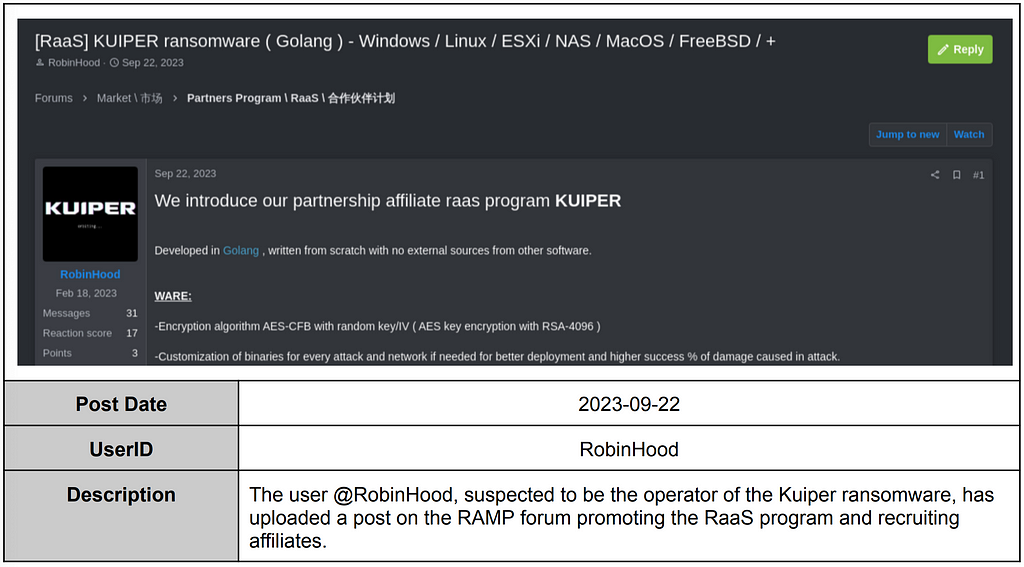
Ransomed
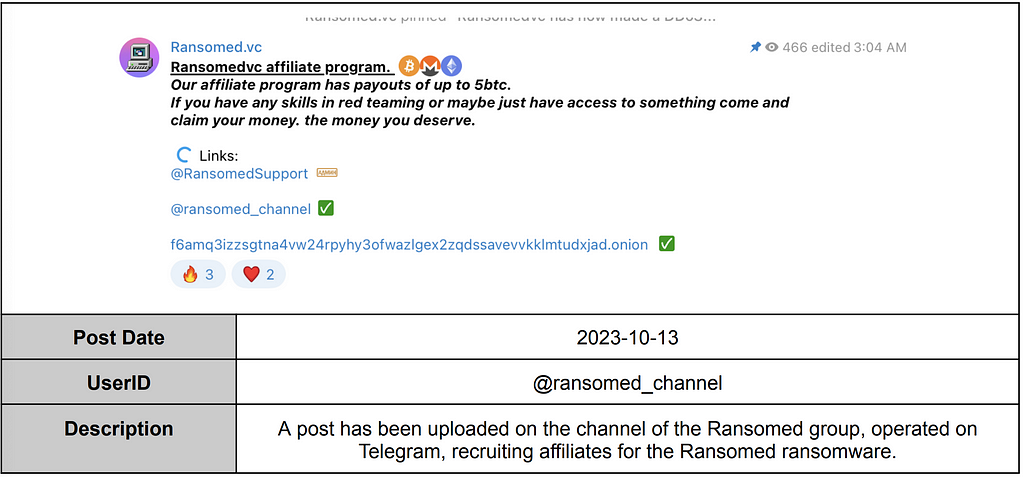
qBitSupp
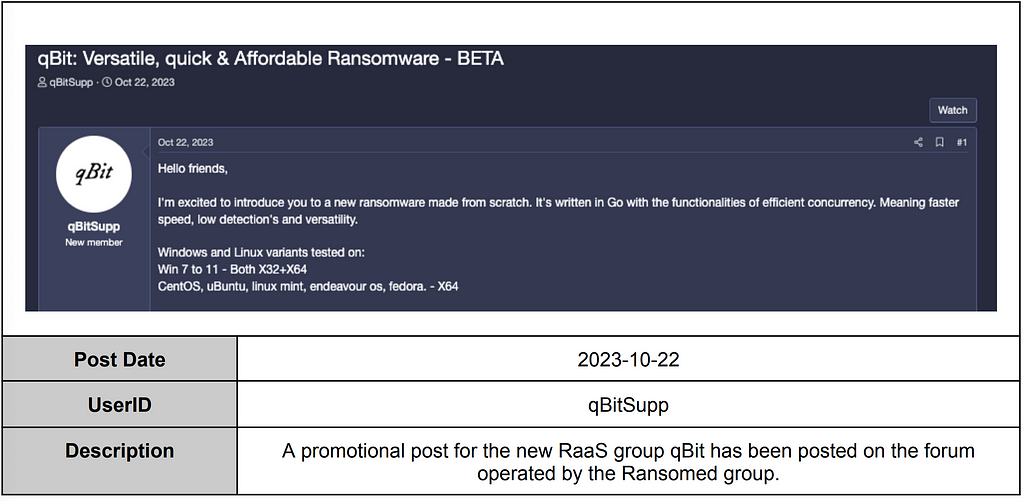
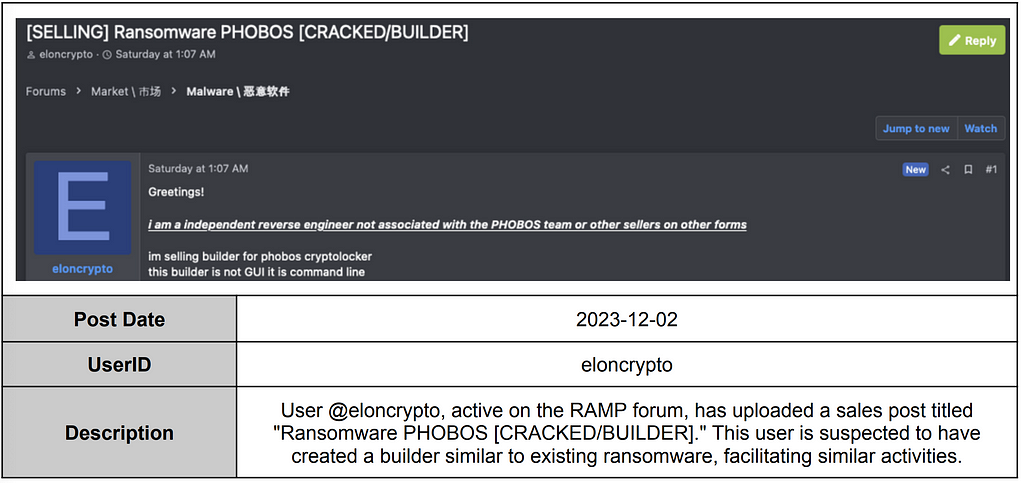
PHOBOS
Private Ransomware
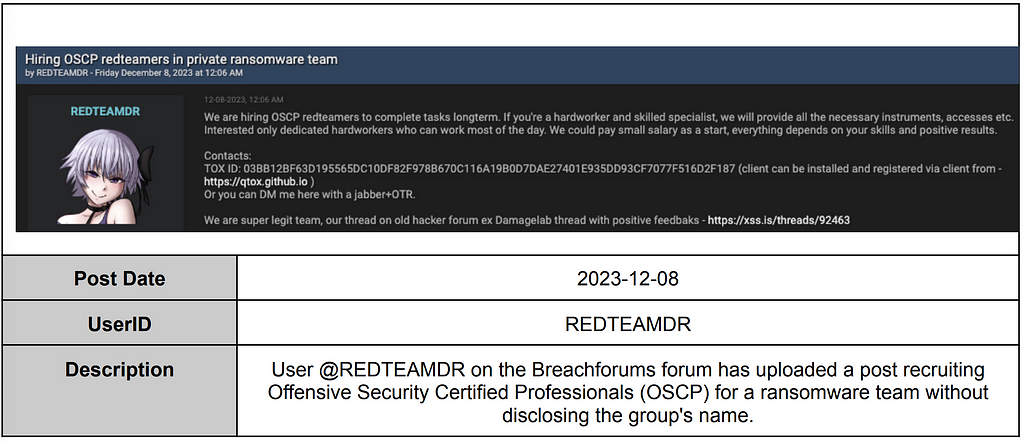
BianLian
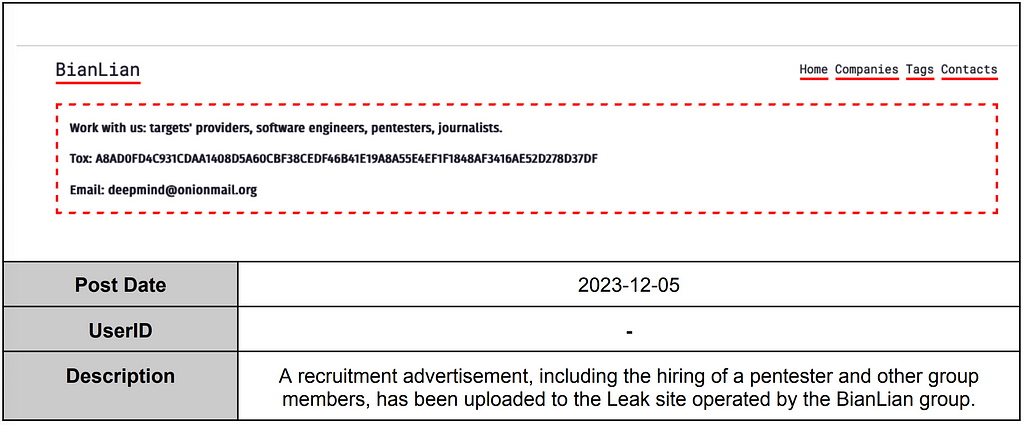
3.4.2. Posts related to Ransomware
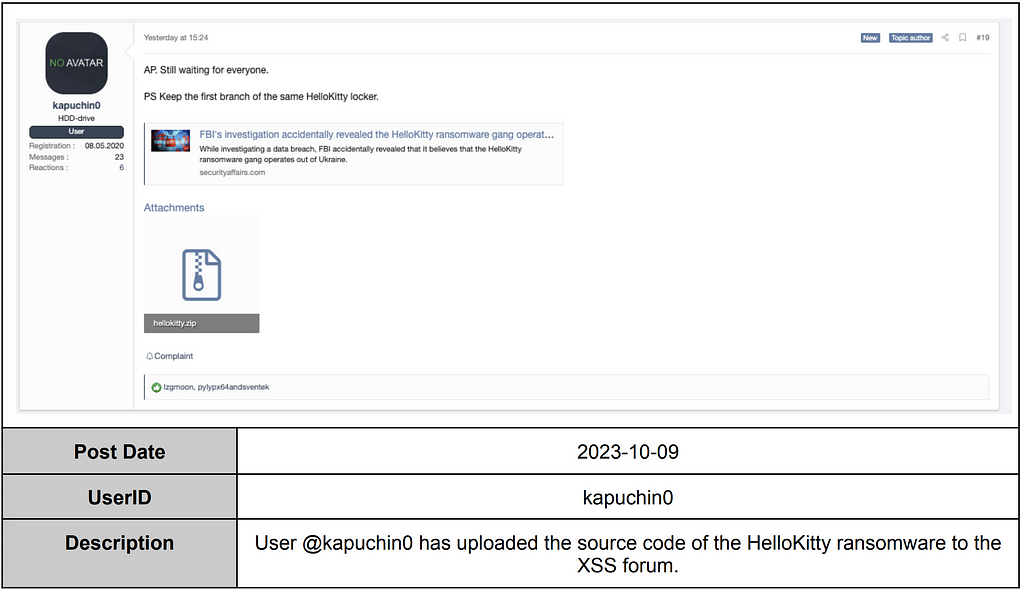
HelloKitty Ransomware
PHOBOS
NoEscape Ransomware
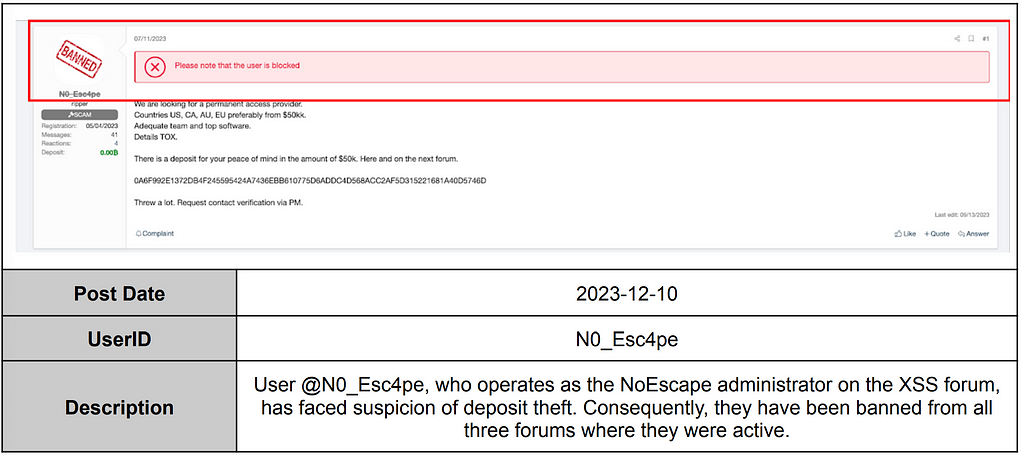
3.4.3. Posts for selling access
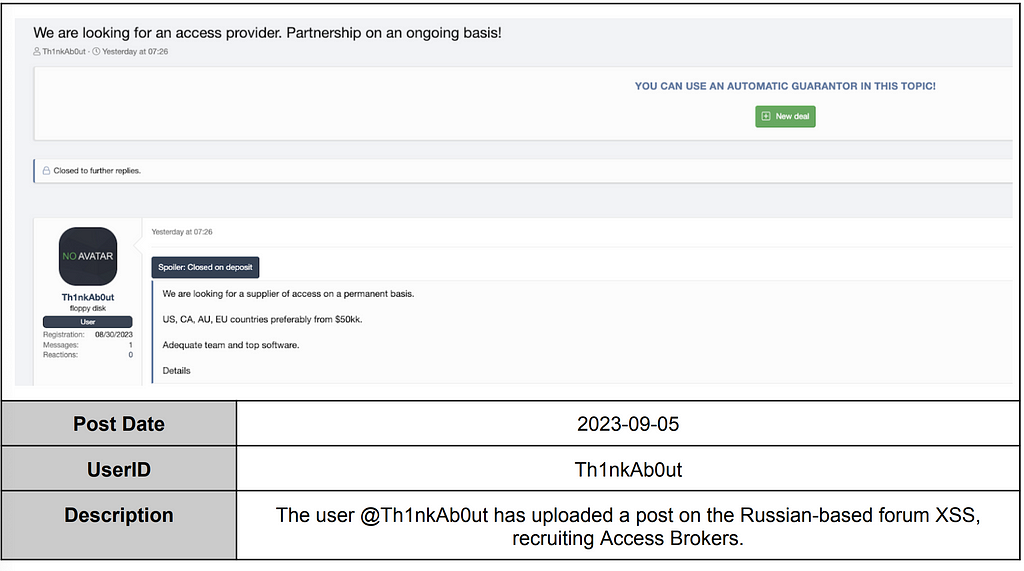
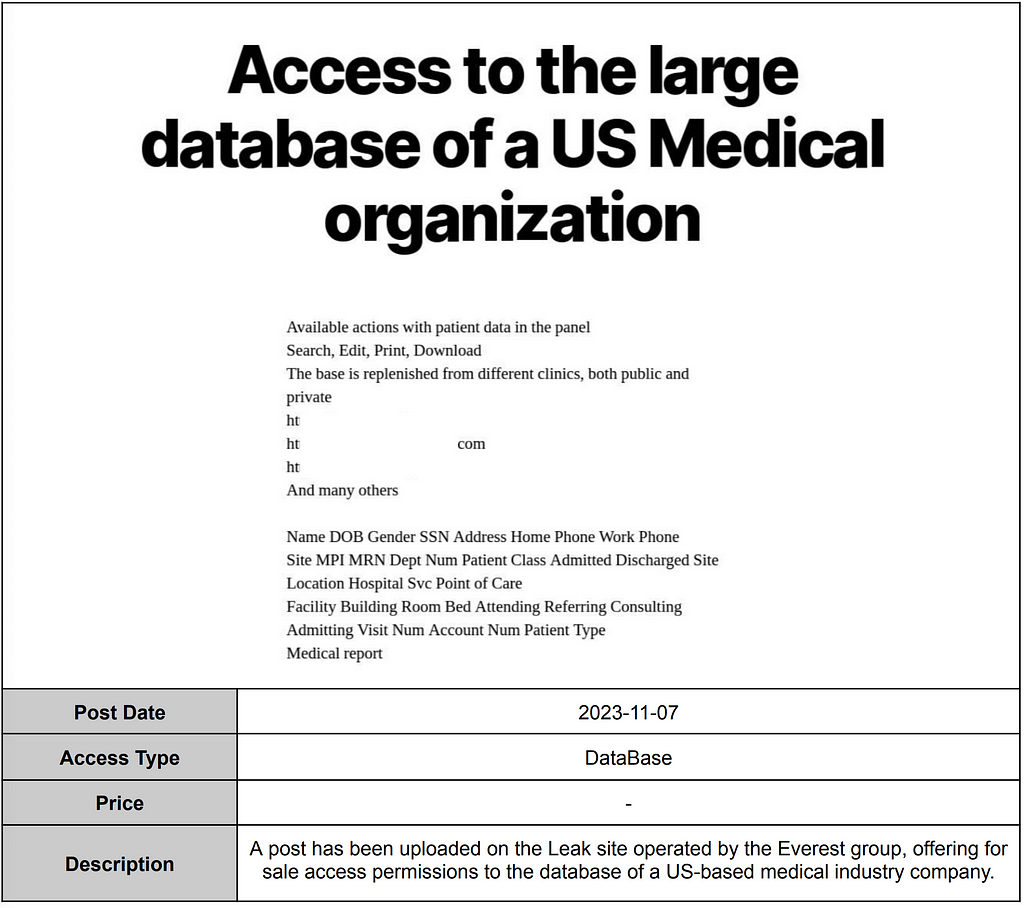
Some ransomware groups engage in the role of an Initial Access Broker (IAB) to generate revenue by selling access information to companies instead of the data stolen from those companies. They do this by posting advertisements on Leak sites or forums, offering access information to the targeted companies in exchange for money.
Everest

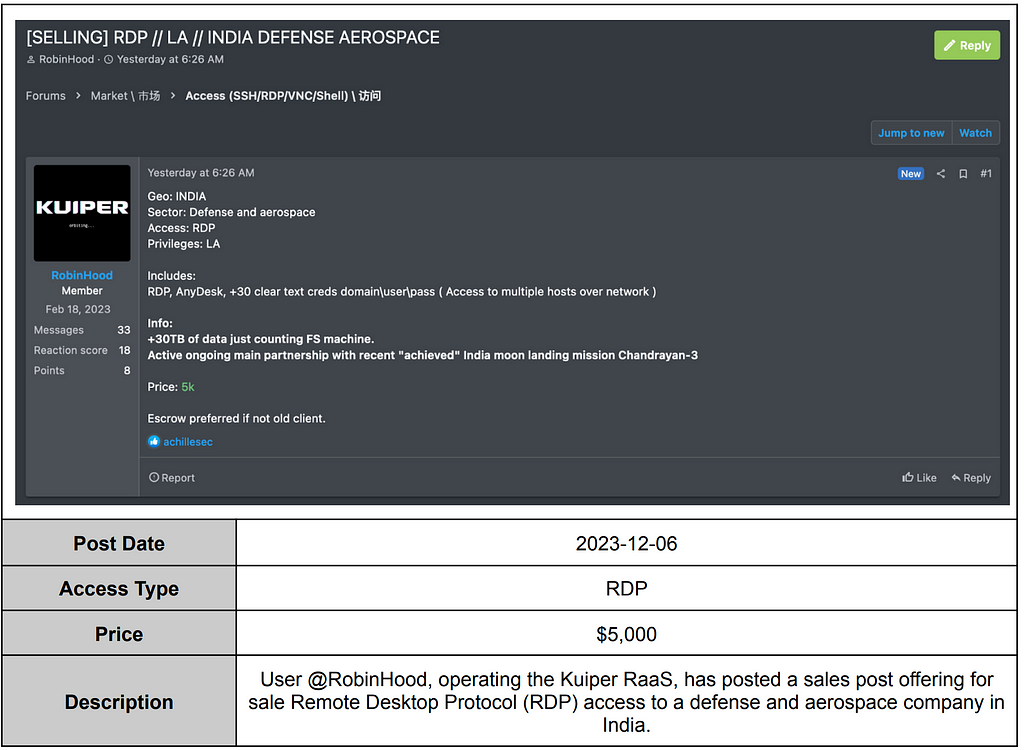
Kuiper
3.5. Duplicated Victims
In this report, additional analysis was conducted to differentiate ransomware groups that uploaded duplicated companies. There are cases where multiple ransomware groups expose the same company’s victimization on various Leak sites. This is presumed to occur due to collaboration between the ransomware groups and associated Initial Access Brokers (IABs) working with multiple groups.
Depending on the nature of the group, the type of Leak site can be classified differently. S2W categorized each type as “Leak category” and “Ransomware category.” Groups engaged in facilitating data sales without direct involvement in attacks or collaborating with ransomware groups were classified as “Leak category,” while those uploading victimized companies directly affected by ransomware were categorized as “Ransomware category.”
- Among the 53 ransomware groups active in the second half of 2023, Snatch, Karakurt, and Daixin belong to the Leak category.
During the second half of 2023, the total number of duplicated victimized companies uploaded to Leak sites was 35, with 27 groups revealing victimization of the same companies. Among these, groups that uploaded duplicated victimized companies more than twice were identified as BlackCat, LockBit, 8Base, and Werewolves.
- In Figure 26, each ransomware group forms a 1:1 relationship, with the group that uploaded the duplicated victimized companies first positioned on the left and the group that uploaded them later positioned on the right.
- In the following sections, the ransomware groups that uploaded duplicated victimized companies are further categorized according to the aforementioned criteria.
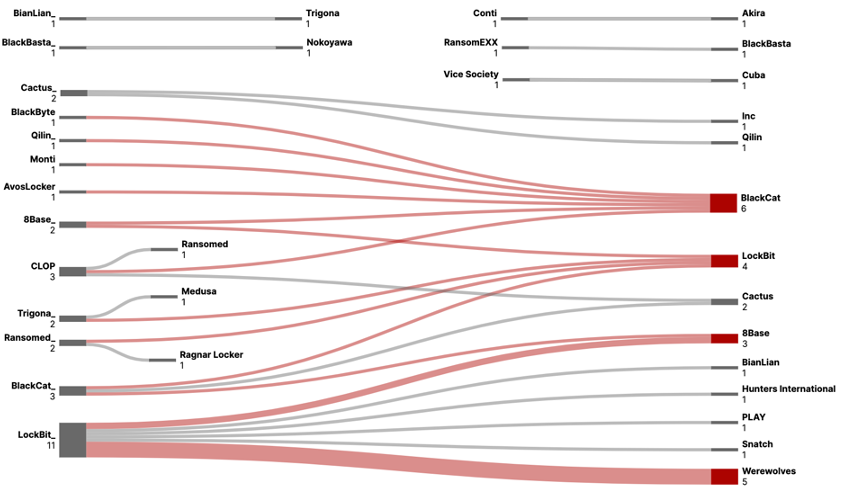 Figure 26. Total Duplicated Victim Companies
Figure 26. Total Duplicated Victim Companies3.5.1. Leak Category
Among ransomware groups that uploaded victim companies late in the second half of 2023, only one group falls into the Leak category, which is Snatch.
As mentioned in the trends report for the first half of 2023, Snatch group has been collaborating with several affiliates to leak data. Given LockBit’s significant number of affiliates among ransomware groups, it is likely to have a higher probability of occurrence of duplicated victim companies.
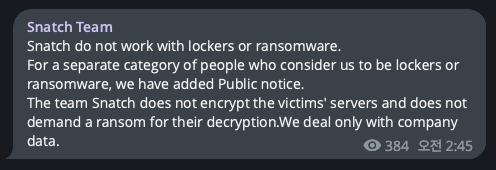
 Figure 27. Official Telegram messages by Snatch (Left) / Figure 28. Announcements on Snatch Group’s leak site (right)
Figure 27. Official Telegram messages by Snatch (Left) / Figure 28. Announcements on Snatch Group’s leak site (right)3.5.2. Ransomware Category
Among ransomware groups in the Ransomware category, BlackCat was the group that uploaded duplicated victim companies later in the second half of 2023, with a total of 6 instances. On the other hand, LockBit was the group that uploaded duplicated victim companies first, with a total of 11 instances.
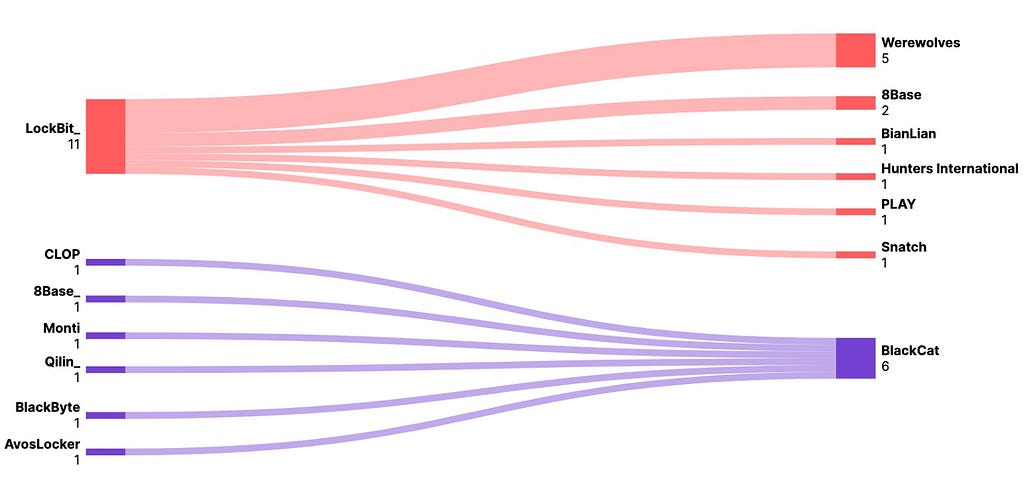 Figure 29. Duplicated victim companies among Ransomware category groups
Figure 29. Duplicated victim companies among Ransomware category groupsIn the case of the Werewolves group, among the 20 victim companies they exposed on Leak sites during the second half of the year, 5 of these companies overlapped with LockBit, and all the duplicated companies were uploaded later than LockBit’s entries. The Werewolves group has a history of mentioning the use of ransomware on Leak sites, and they are suspected of using LockBit 3.0/Black, hence classified as a group in the Ransomware category. However, considering that many of the companies uploaded on Leak sites overlap with LockBit ransomware victim companies, there is also a possibility that the Werewolves group is performing the role of an Affiliate to LockBit in the Leak category.
 Figure 30. Companies duplicated with Werewolves
Figure 30. Companies duplicated with WerewolvesConclusion
- In the second half of 2023, S2W tracked a total of 44 new ransomware groups, marking an increase of 9 groups compared to the first half of the year.
- Among these, 18 groups were newly discovered on Leak sites during the second half, while 7 groups underwent status changes. Additionally, there was an emergence of groups utilizing Clearnet for Leak sites, and the CLOP group was observed using Torrent as a Leak site, showcasing a variety of Leak site types compared to the first half.
- Among the new ransomware groups, 13 were found to utilize known ransomware families, with the Chaos family accounting for the highest proportion, totaling 5 out of the 13.
- Ransomware groups often undergo rebranding processes for legal liability avoidance and marketing purposes. In the second half, instances of rebranding were observed among ransomware groups such as Knight and RA World.
- New associations were discovered between existing ransomware groups like Vice Society and Royal and newcomers like Rhysida and BlackSuit. When the activity of existing ransomware groups decreased, the activity of new ransomware groups increased.
- Analyzing major ransomware campaigns revealed higher exploitation of vulnerabilities compared to the first half, with groups like LockBit, AKIRA, CLOP, and BlackCat exploiting 0-day vulnerabilities.
- Upon examining the status of victim companies on Leak sites, it was found that some companies experienced duplicate infections with ransomware during the second half of 2023.
— It is anticipated that the occurrence of duplicate infections with different ransomware could be due to Affiliates providing access data and performing initial penetrations, collaborating with multiple ransomware groups.
P.S. We were impressed by the Ransomware map produced by Orange Cyberdefense and created our map based on it. We would like to say thank you to them.
Appendix A. Campaign Timeline
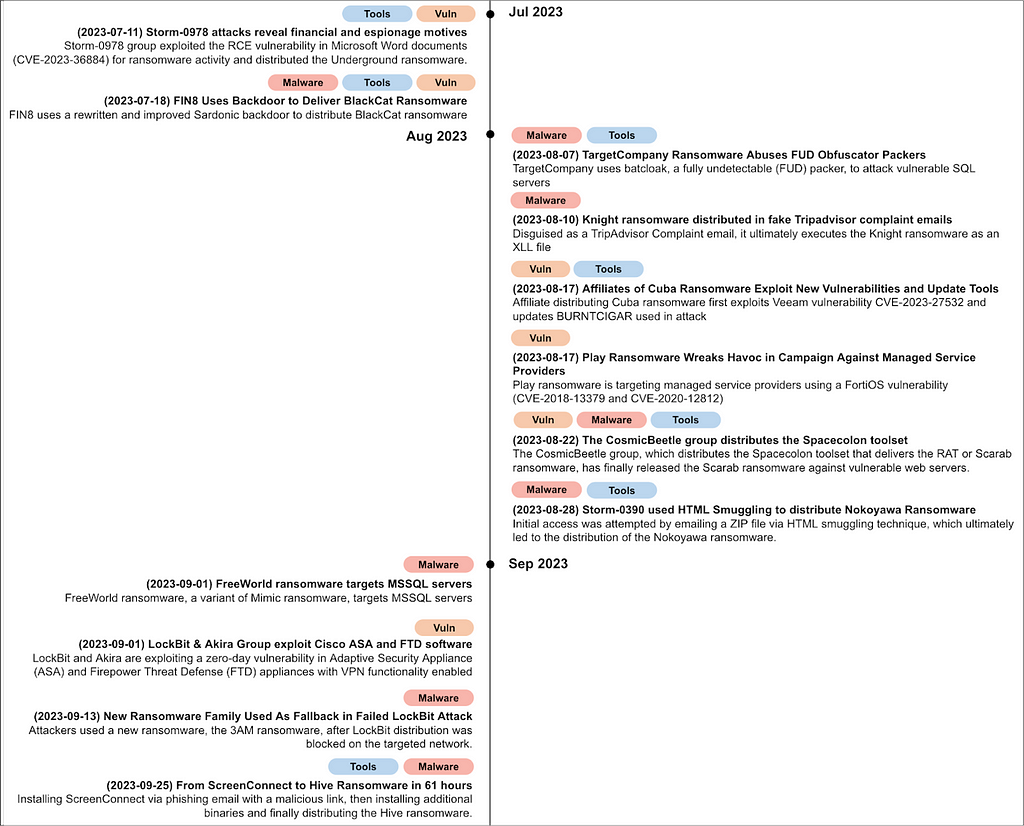

Reference
- https://www.microsoft.com/en-us/security/blog/2023/07/11/storm-0978-attacks-reveal-financial-and-espionage-motives/ (Microsoft, 2023–07)
- https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/syssphinx-fin8-backdoor (Symantec, 2023–07)
- https://thedfirreport.com/2023/08/28/html-smuggling-leads-to-domain-wide-ransomware/ (DFIR, 2023–08)
- https://www.welivesecurity.com/en/eset-research/scarabs-colon-izing-vulnerable-servers/ (ESET, 2023–08)
- https://www.trendmicro.com/en_us/research/23/h/targetcompany-ransomware-abuses-fud-obfuscator-packers.html (TrendMicro, 2023–08)
- https://blogs.blackberry.com/en/2023/08/cuba-ransomware-deploys-new-tools-targets-critical-infrastructure-sector-in-the-usa-and-it-integrator-in-latin-america (BlackBerry, 2023–08)
- https://adlumin.com/post/playcrypt-ransomware/ (Adlumin, 2023–08)
- https://twitter.com/felixw3000/status/1689541933062868992 (@Felixw3000, 2023–08)
- https://www.securonix.com/blog/securonix-threat-labs-security-advisory-threat-actors-target-mssql-servers-in-dbjammer-to-deliver-freeworld-ransomware/ (Securonix, 2023–09)
- https://www.tenable.com/blog/cve-2023-20269-zero-day-vulnerability-in-cisco-asa-and-ftd-reportedly-exploited-ransomware-groups (Tenable, 2023–09)
- https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/3am-ransomware-lockbit (Symantec, 2023–09)
- https://thedfirreport.com/2023/09/25/from-screenconnect-to-hive-ransomware-in-61-hours/ (DFIR, 2023–09)
- https://blog.talosintelligence.com/qakbot-affiliated-actors-distribute-ransom/ (Cisco, 2023–10)
- https://infosec.exchange/@SophosXOps/111222943608438109 (@SophosXOps, 2023–10)
- https://twitter.com/TheDFIRReport/status/1714250495513035087 (@TheDFIRReport, 2023–10)
- https://unit42.paloaltonetworks.com/blackcat-ransomware-releases-new-utility-munchkin/ (Unit42, 2023–10)
- https://news.sophos.com/en-us/2023/10/19/ransomware-actor-exploits-coldfusion-servers-but-comes-away-empty-handed/ (Sophos, 2023–10)
- https://www.rapid7.com/blog/post/2023/11/06/etr-rapid7-observed-exploitation-of-atlassian-confluence-cve-2023-22518/ (Rapid7, 2023–11)
- https://www.rapid7.com/blog/post/2023/11/01/etr-suspected-exploitation-of-apache-activemq-cve-2023-46604/ (Rapid7, 2023–11)
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-325a (CISA, 2023–11)
- https://arcticwolf.com/resources/blog/qlik-sense-exploited-in-cactus-ransomware-campaign/ (Arcticwolf, 2023–11)
- https://twitter.com/threatintel/status/1729904584091488675?s=61&t=qctU71F8N_rPECDReT7QKw (@threatintel, 2023–11)
- https://twitter.com/MsftSecIntel/status/1730383711437283757 (@MsftSecIntel, 2023–12)
- https://thedfirreport.com/2023/12/04/sql-brute-force-leads-to-bluesky-ransomware/ (DFIR, 2023–12)

- Homepage: https://s2w.inc
- Facebook: https://www.facebook.com/S2WLAB
- Twitter: https://twitter.com/S2W_Official
Story of the H2 2023: In-depth Examination of Notable Ransomware Groups and Key Issues (English ver. was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.