Story of H2 2023: A Deep Dive into Data Leakage and Commerce in Chinese Telegram Channels (English ver.)
Author: HOTSAUCE (Threat Detection Team) | S2W TALON
Last Modified: Jan 16, 2024
 Photo by Lana Codes on Unsplash
Photo by Lana Codes on UnsplashExecutive Summary
- This report analyzes the activities within Chinese Telegram channels and chat rooms (referred to as Chinese Telegram) during the second half of 2023 (from 2023–07–01 to 2023–11–30).
- The focus is on entities identified by their corporate and institutional names within the context of Chinese Telegram Channels.
- This report aims to provide insights into recent threats initiated by Chinese Telegram, offer information about newly discovered activity patterns of newly found threat actors, and contribute to enhancing responses and security measures against cyber issues arising on Chinese Telegram Channels.
Key Findings:
1. During the second half of 2023, 620 affected businesses and institutions were identified as affected on Chinese Telegram Channels.
- The highest number of incidents occurred in July, with a decreasing trend afterward.
- Sales incidents accounted for most cases, comprising 82.9% of the total.
- Among the top 10 countries with the highest number of incidents, Taiwan had the highest count, with seven out of ten being Asian countries.
2. Contrary to the decrease in the number of incidents, the message volume on Chinese Telegram increased.
- With the growing scale of Chinese Telegram, there is an expansion in the scope of exchange and communication.
- The user @metasploit233 contributed the most to information dissemination on Chinese Telegram.
3. Chinese Telegram users actively express solidarity on domestic and international issues related to China.
- Opinions related to the Fang campaign led by China’s Public Security Bureau and vulnerability sharing were actively discussed.
- Concerns about retaliatory attacks were raised due to the Japanese wastewater discharge incident, anticipating potential harm to the country.
Introduction:
The landscape of Chinese cyber threats, traditionally centered around state-backed APT groups in the past, has diversified since the emergence of Telegram. While conventional Chinese cyber threats were primarily associated with QQ and DDW forums, recent trends indicate an increasing presence of threats on Telegram.
- QQ requires users to search for specific groups through keyword input searches and identification and apply for membership or receive direct invitations, imposing constraints on access to chat rooms.
- In contrast, Telegram allows easy channel searches and information retrieval through searches and provides an environment where users can quickly enter channels through inter-channel promotions.
- Despite unofficial censorship of Telegram in China, users continue to circumvent restrictions by joining with virtual numbers and utilizing VPNs or proxies.
Telegram channels and chat rooms have distinct characteristics:
- Channels, primarily employed by data-selling groups, involve unidirectional communication where channel administrators provide information, and subscribers’ information is not accessible to anyone other than the administrator.
- Chat rooms, mainly utilized by cybercrime groups, facilitate bidirectional communication, allowing anyone to join conversations and verify user information within the room.
Primary threat cases identified on Telegram include:
1. Data Leakage:
- Descriptions and data files are attached to messages, providing information about the leaked data.
- Sample data is provided, and if users wish to download the entire dataset, they are encouraged to contact privately.
2. Data Sales:
- Screenshots of sample data for sale are provided.
- Information about the target country and industry sector is disclosed, but specific details about the target are often not provided.
- Transactions primarily use USDT, with prices ranging from 0.2 to 0.5 CNY per transaction, equivalent to approximately 0.03 to 0.068 USD.
3. Cyber Attacks:
- Exploiting vulnerabilities in the target, cyber attacks result in data leakage.
- Chat rooms are actively utilized to share information about hacking tools and hacking operation histories.
For accurate national and sectoral statistics, this report limits its analysis to posts where the target has been explicitly identified.
Detailed Analysis:
1. Targeted Victims on Chinese Telegram
1.1. Overall Chinese Telegram Activity in H2 2023:
- The S2W Threat Intelligence Center monitored 1,252 Chinese Telegram channels during the second half of 2023. Within this period, a total of 620 threat posts, encompassing data leaks, sales, and attack-related content (referred to as threat posts), were detected.
- The classification of posts is defined as follows: ‘Leak’ is if the data is publicly disclosed for free, and ‘Sale’ is if the leaked data is offered for a certain amount, negotiated, or auctioned.
Out of the total 620 threat posts detected on Telegram, it was observed that sales posts, as shown in Figure 1, were the most frequent at 82.9%. Following that, data leaks accounted for 12.9%, and attacks were confirmed at 4.2%.
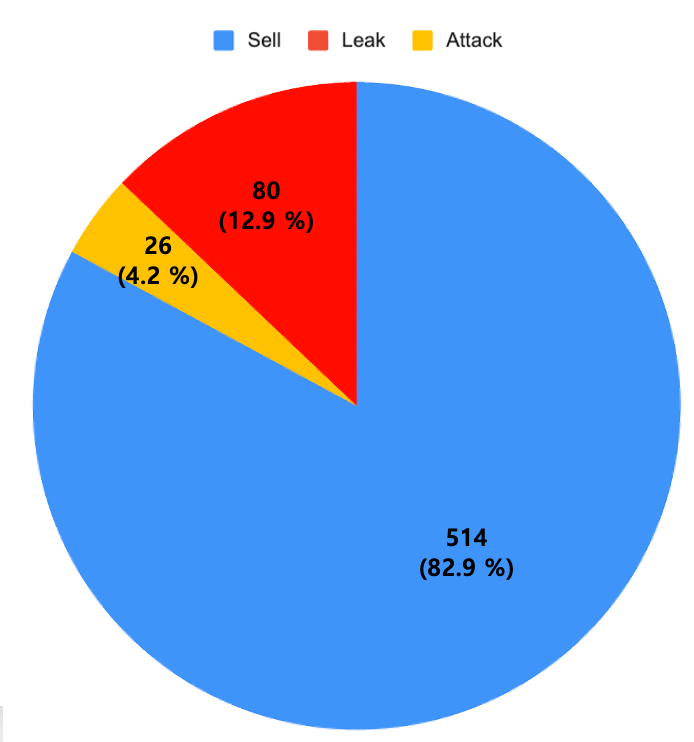 Figure 1. Frequency Graph of Threat Post Types
Figure 1. Frequency Graph of Threat Post Types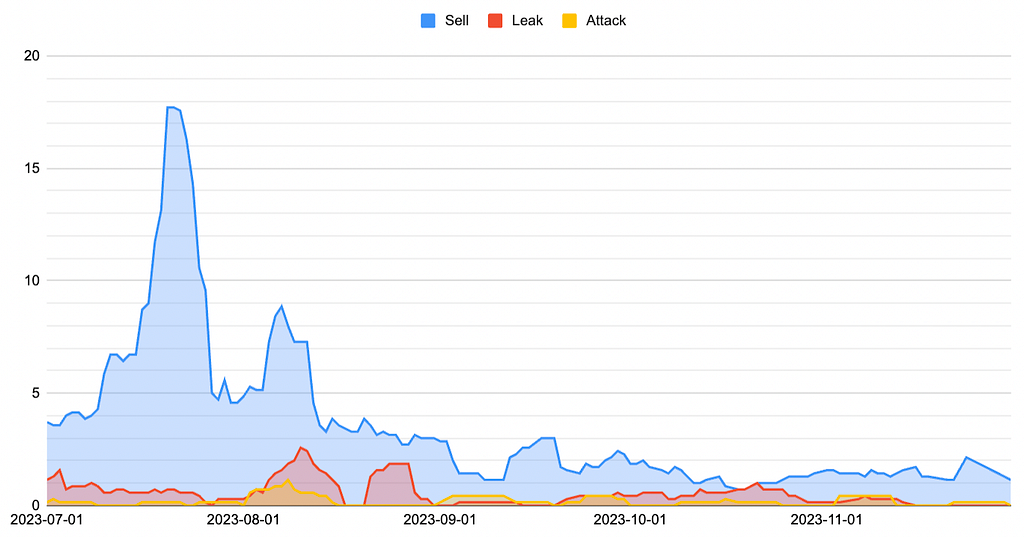 Figure 2. Time graph by threat post type
Figure 2. Time graph by threat post type- Figure 2 shows that the volume of leaked data sales within Chinese Telegram channels was highest in July 2023, followed by a decreasing trend.
- In July and August, a significant number of threat posts were observed, with a subsequent decline. The decrease in threat posts from this point onward is estimated to be influenced by two factors.
1. A decrease in the number of threat posts on the ” 湾 台 数 据” channel
- According to Table 1, the channel “ 湾 台 数 据” was identified as the channel with the highest number of threat posts, uploading 268 in July and 187 in August.
- If the median is low while the average is relatively high, it can be inferred that a few channels are pulling up the average. In July and August, the median for threat posts was 2, but the “ 湾 台 数 据” channel alone leaked 61 posts in July and 28 posts in August, contributing to an increase in the overall average number of threat posts.
- Subsequently, as the activity in that channel decreased from August onwards, it decreased the total number of threat posts and the average number of threat posts.
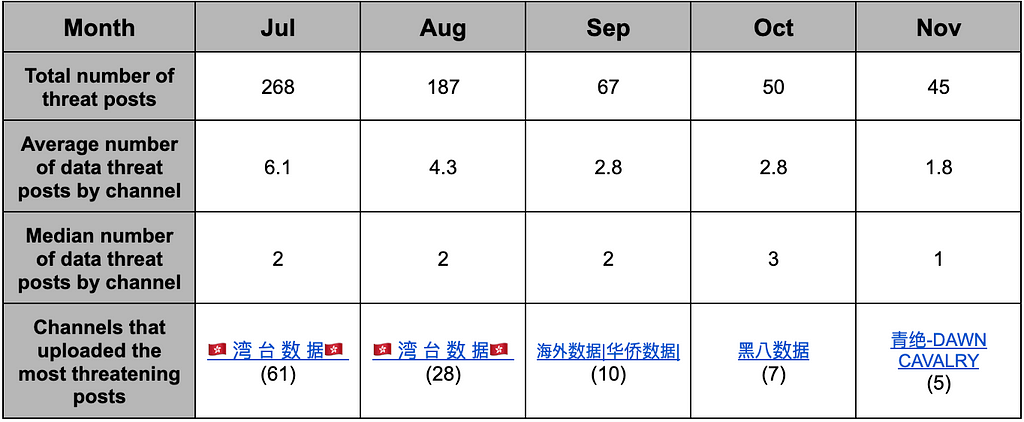 Table 1. Descriptive statistics on sales, leaks, and attacks in Chinese Telegram channels.
Table 1. Descriptive statistics on sales, leaks, and attacks in Chinese Telegram channels.2. Encouraging the Leaked Data Transactions through Personal Contacts and Private Channels
- A recent trend has been observed wherein sellers refrain from directly mentioning specific targets and only imply approximate information such as country, industry, etc. The sellers induce potential buyers to contact them through private messages (DM) within channels.
- According to Figure 3, there has been a gradual increase in the frequency of terms encouraging inquiries within Telegram channels, such as 咨询 (inquiry), 联系 (contact), 私我 (DM me), 有的来 (someone contacts me), 私聊 (chat privately), 要的私聊 (DM me if you need it), 收 (seeking), and 滴滴 (DM), starting from July.
- However, from November onwards, there has been a decline in the mention of these keywords. This decrease may be attributed to sellers securing primary transaction customers, refraining from additional external promotional activities, or transitioning to VIP/private channels.
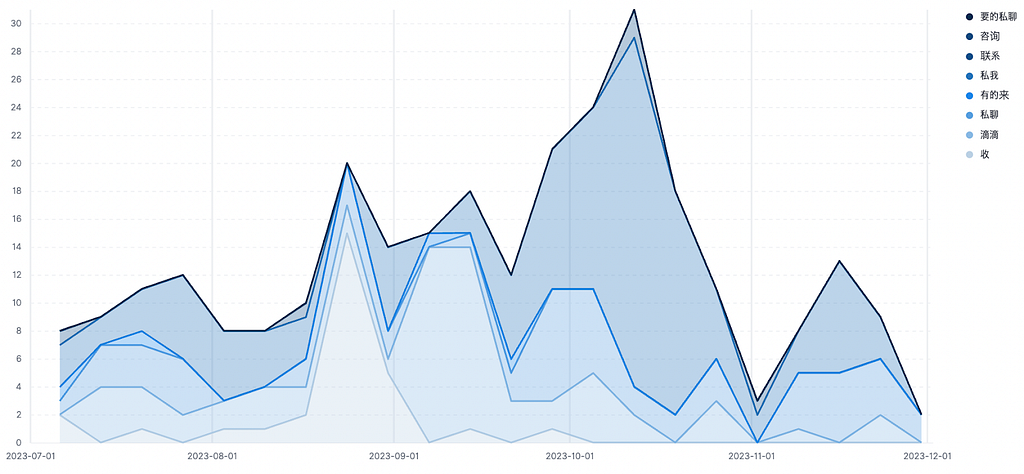 Figure 3. DM-induced keyword mention graph
Figure 3. DM-induced keyword mention graph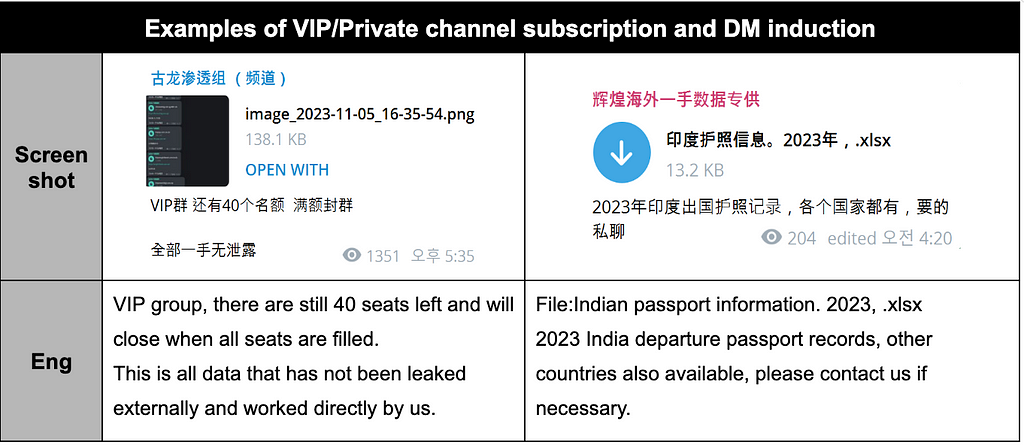 Table 2. Examples of VIP/Private channel subscription and DM induction
Table 2. Examples of VIP/Private channel subscription and DM inductionThe top 30 channels with the highest number of threat posts during the second half of 2023 are illustrated in Figure 4.
- Among them, the Top 10 channels accounted for 56.6% of the total leakage cases.
- As observed in the case of the “ 湾 台 数 据” channel, which dominated the majority of threatening posts on Chinese Telegram channels in July and August (as detailed in Table 1), it is notable that threat posts tend to be uploaded predominantly in specific channels rather than being evenly distributed across various Chinese Telegram channels.
- The channel identified as the most prolific in posting threat content is operated by 古龙渗透组 (Ancient Dragon Penetration Team named “AncientDragonCrow” by S2W) within the “ 湾 台 数 据” channel. AncientDragonCrow is known for concurrently managing multiple channels, and further details are discussed in Section 1.4.1.
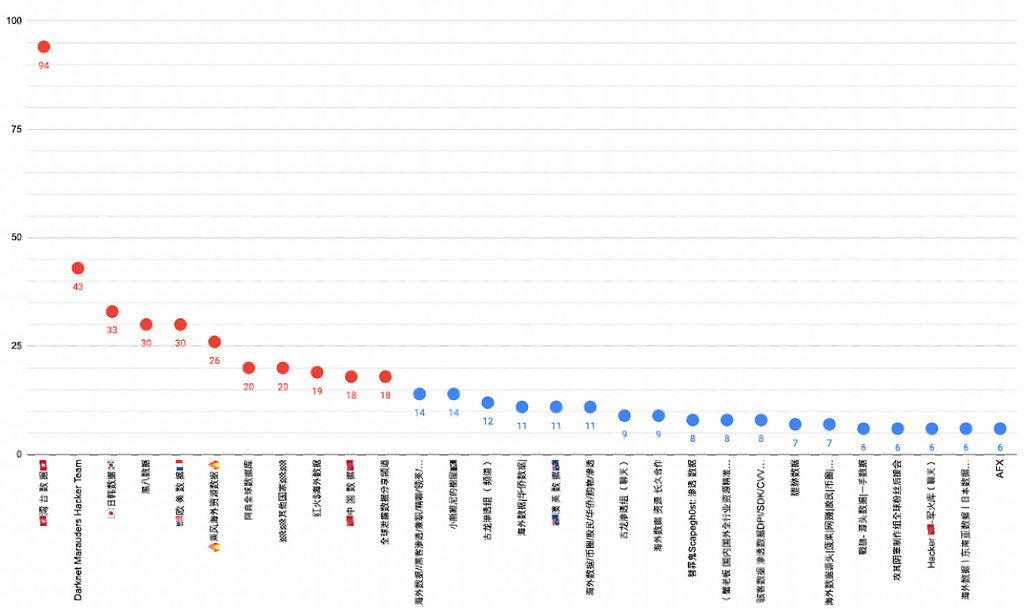 Figure 4. Graph of the number of threat posts by channel in the second half of 2023
Figure 4. Graph of the number of threat posts by channel in the second half of 2023- According to Figure 5, during the second half of this year, among the channels where at least one threat post was detected, 50% had two or fewer threat posts. However, 17 channels were identified as outliers, exceeding the upper limit of the threat post count in the box plot due to their high posting activity. These channels include “ 湾 台 数 据”, Darknet Marauders Hacker Team, and “ 日韩数据” (Japanese, Korean data).
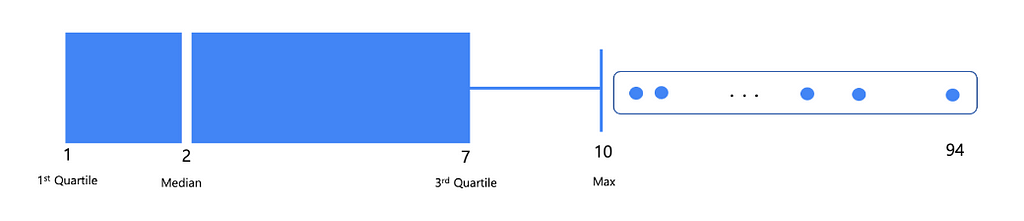 Figure 5. Boxplot graph of the number of threat posts by channel in the second half of 2023
Figure 5. Boxplot graph of the number of threat posts by channel in the second half of 20231.2. Targeted Victim Sector
1.2.1. Top 10 Targeted Victim Sectors
During the second half of 2023, the top 10 sectors targeted in threat posts on Chinese Telegram channels are outlined in Table 3.
- The combined share of the top 10 victim sectors accounted for 74.8% of all cases.
- The sector that suffered the most significant impact was the E-commerce sector, followed by Finance in the second position and Government in the third.
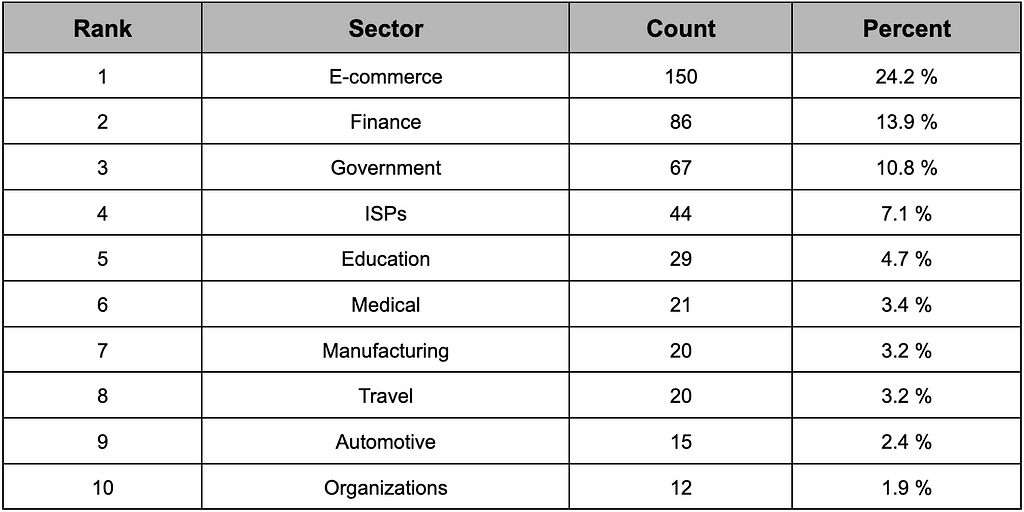 Table 3. Top 10 industries affected by Telegram in China
Table 3. Top 10 industries affected by Telegram in China1.2.2. Characteristics of Victims by Post Type
- Table 4 shows a distinction between the sectors from which data is leaked and the sectors for which data is sold.
- E-commerce emerged as the most prevalent sector in sales transactions, while government institutions were most frequently associated with leaked data cases.
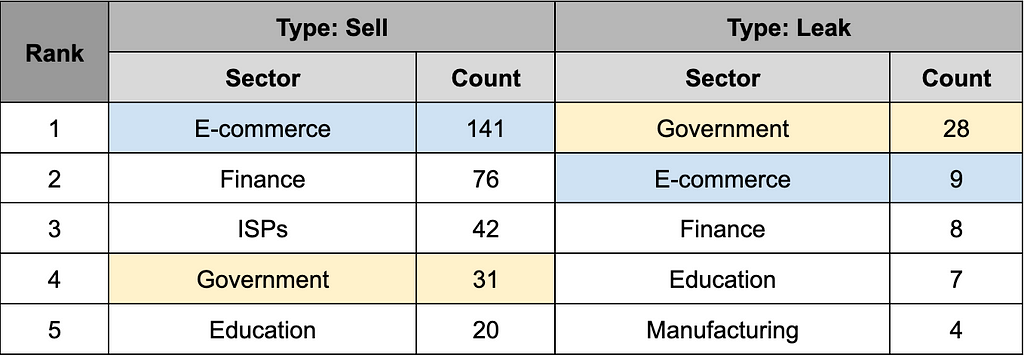 Table 4. Top 5 industries affected by sales/leakage
Table 4. Top 5 industries affected by sales/leakage- The difference between the sectors for which data is sold and leaked is presumed to involve the author’s profit-seeking objectives, the demonstration of hacking capabilities, and inclinations toward hacktivism.
- As seen in Table 5, the Darknet Marauders Hacker Team recruited members to pursue profits through data sales but also showcased their hacking capabilities by leaking data from government agencies and businesses. Further details about this team can be found in Section 1.4.1.
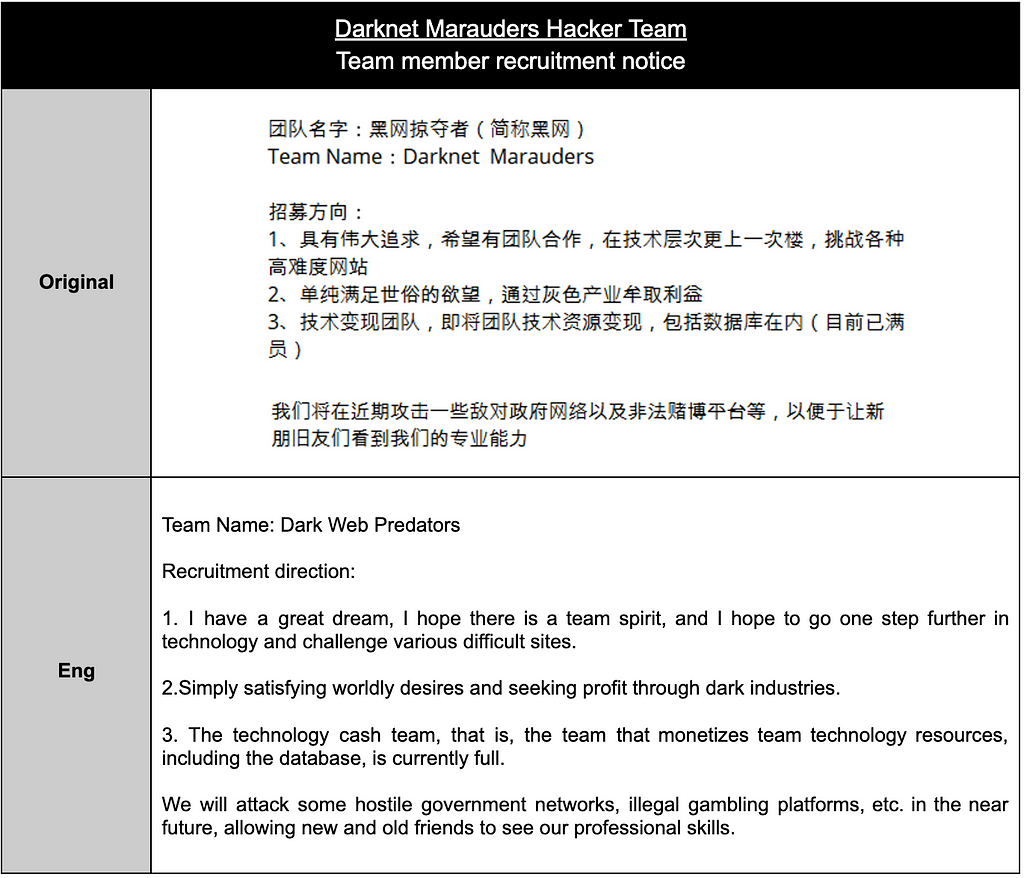 Table 5. Examples of purposes for data sales and leaks
Table 5. Examples of purposes for data sales and leaksThe factors contributing to the high ranking of data sales in the E-commerce sector are estimated as follows:
- Sellers categorize all online shopping malls as ‘购物’ (Shopping), resulting in a high numerical measurement for E-commerce as various shopping malls are grouped under this category.
- Customer information in shopping malls includes personal data such as email addresses, names, phone numbers, purchase history, payment details, addresses, etc. This diverse personal information, which can be utilized for marketing messages or phishing attempts, may contribute to the high demand for E-commerce sector data.
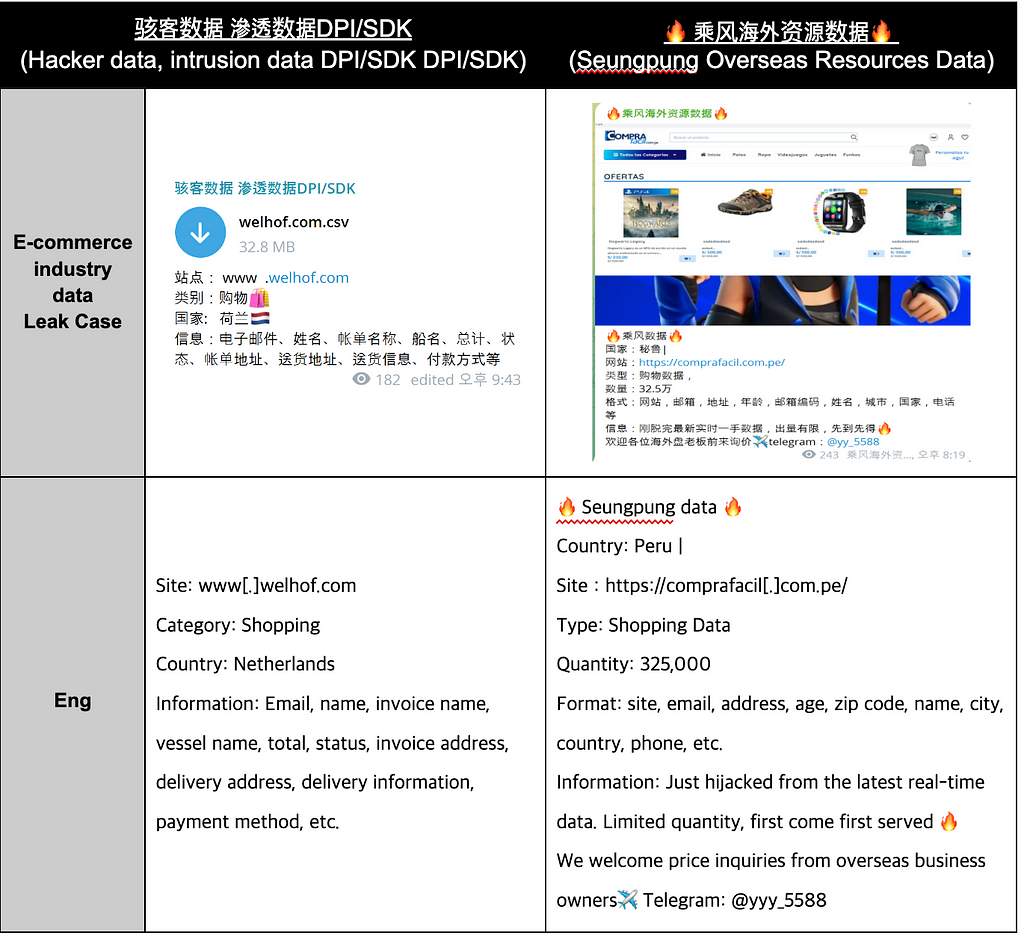 Table 6. E-commerce industry data leak cases
Table 6. E-commerce industry data leak cases- Furthermore, according to Figure 6, it was evident that channels primarily focused on data leaks, and those primarily engaged in sales could be clearly distinguished. While there are channels, such as
- Darknet Marauders Hacker Team and Hacker “ -军火库”(聊天) (Hacker Arsenal Chat) that conduct both attacks and leaks simultaneously, channels primarily dedicated to sales are distinctly separated, indicating distinct purposes for each channel.
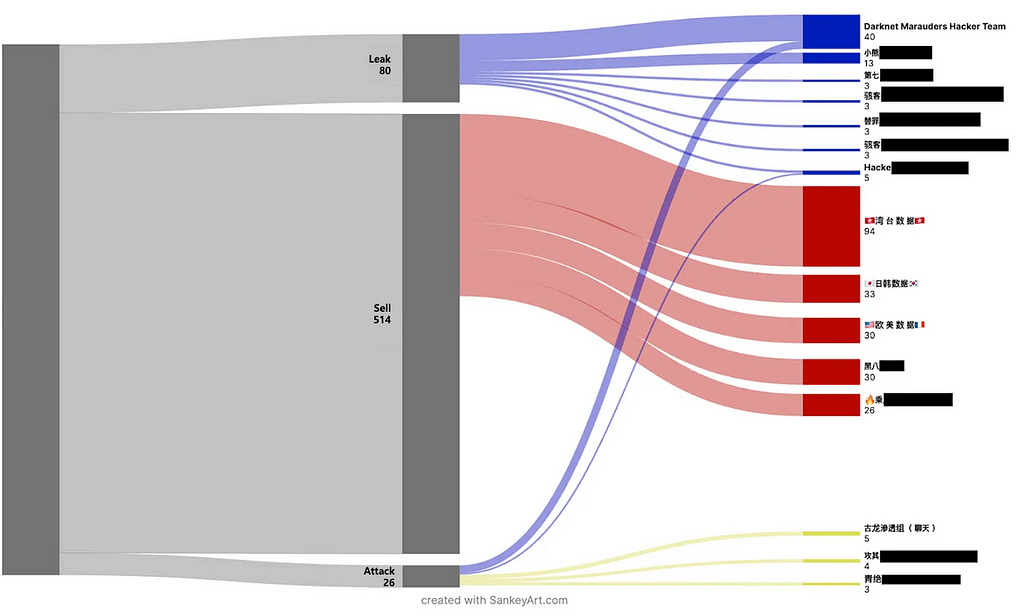 Figure 6. Distinction between outflow channels and sales channels
Figure 6. Distinction between outflow channels and sales channels1.3. Targeted Victim Country
1.3.1. Top 10 Targeted Victim Countries
During the second half of 2023, the top 10 targeted countries identified in the data leakage and sales posts on Chinese Telegram channels are outlined in Table 7.
- The combined share of the top 10 victim countries accounted for 70.3% of all leakage cases.
- Taiwan was confirmed as the country that suffered the most significant impact.
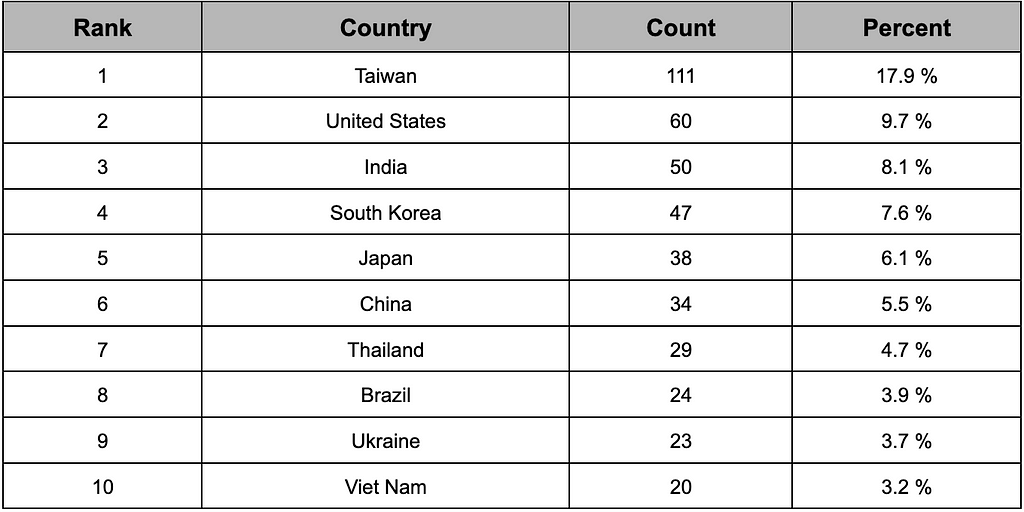 Table 7. Top 10 countries affected by Telegram in China
Table 7. Top 10 countries affected by Telegram in China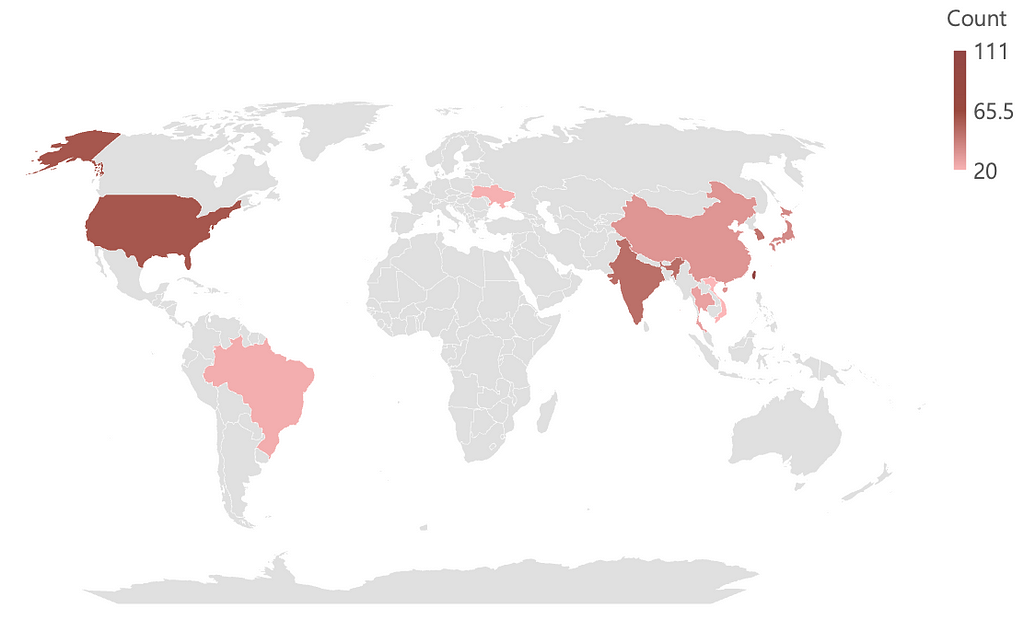 Figure 7. Top 10 affected countries map graph
Figure 7. Top 10 affected countries map graph- Among the top 10 countries that suffered the most impact, seven were located on the Asian continent, as indicated in Figure 7.
- Conversations in Table 8 reveal instances where data buyers directly requested data targeting countries in Asia.
- Furthermore, as observed in Table 9, there were contents encouraging attacks while disregarding the security levels of government sites within Asian countries. These references suggested that targets in the Asian region were perceived as relatively insecure, making data exfiltration easier.
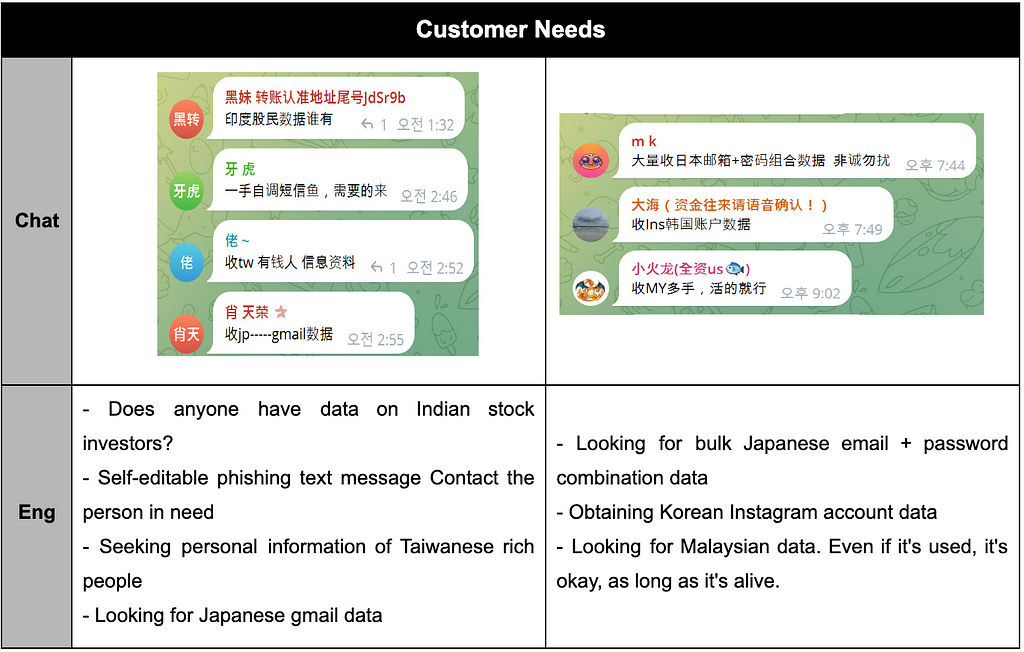 Table 8. A request message from the data purchaser in the chat room
Table 8. A request message from the data purchaser in the chat room Table 9. Chats that ignore security levels on Thai government sites.
Table 9. Chats that ignore security levels on Thai government sites.1.3.2. Chinese Companies Victimized in Chinese Telegram
- There were also cases observed, albeit to a small extent (5.5%), in Chinese Telegram channels where the same nationality as the channel, namely China, was targeted.
- Targeted Chinese businesses and institutions were predominantly identified as smaller shopping malls or investment information sites.
- In contrast, Chinese attackers demonstrated a relatively passive approach toward attacking their government websites.
- During the second half of 2023, there were no recorded instances of Chinese attackers selling or leaking data from the Chinese Government. While some users infiltrated Chinese government websites, they only posted videos showcasing successful hacks for demonstration purposes without engaging in data leakage or sales.
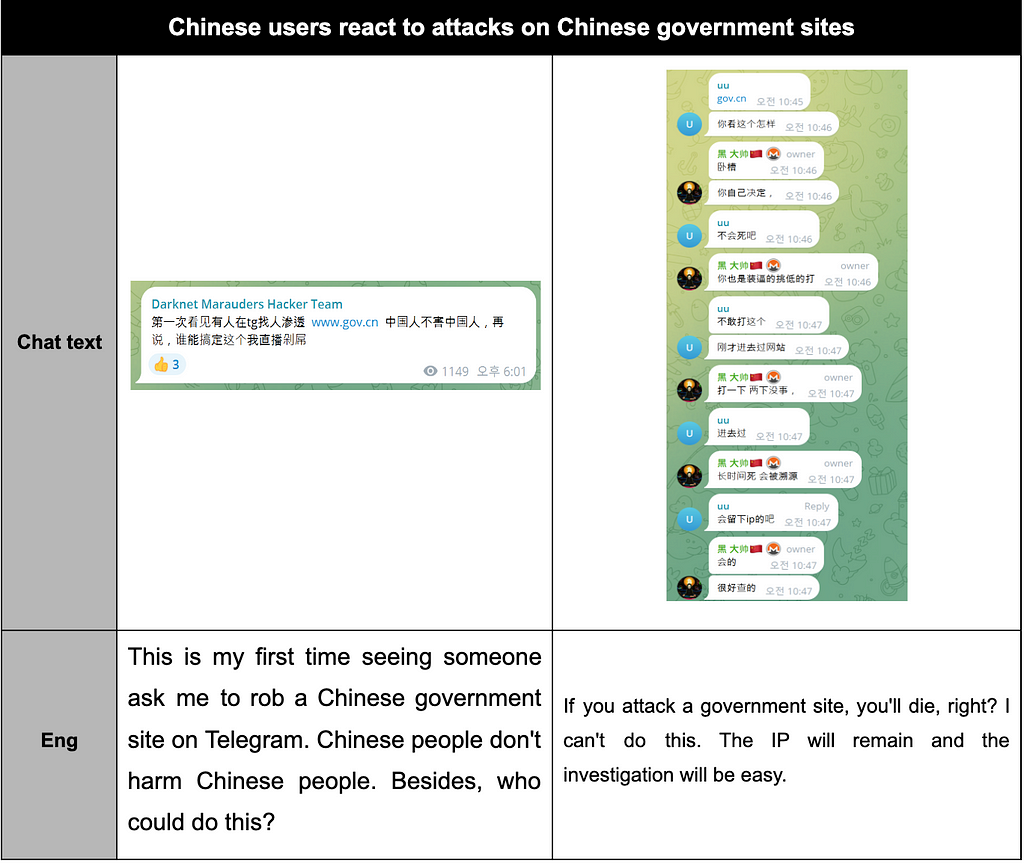 Table 10. Chinese users’ reactions to attacks on Chinese government sites
Table 10. Chinese users’ reactions to attacks on Chinese government sites1.4. Most Active Chinese Telegram
1.4.1. Most Active Commerce Channel — 古龙渗透组
- The cybercrime group 古龙渗透组(AncientDragonCrow) has been active on Telegram since April 7, 2023. Primarily utilizing the SQL Injection scanning tool SuperSQLInjectionV1, the group targets websites from various countries, exfiltrates data, and sells it. The name AncientDragonCrow is derived from the meaning of the first two characters, 古 (ancient) and 龙 (dragon).
- The channels “ 湾 台 数 据”, “ 日韩数据”, “ 欧美数据” (European, American data), “ 其他国家” (other countries), “中 国 数 据” (Chinese data), “ 澳 英 数 据” (Australian, British data), 古龙渗透组(频道) (AncientDragonCrow — Channel), 古龙渗透组(聊天) (AncientDragonCrow-Chat) have all been distributed among the top 30. These channels all operated by AncientDragonCrow, and they have the characteristic of creating separate channels for each target country to upload sales posts in a decentralized manner.
- Initially, they attracted customers by posting data on open channels and creating VIP channels for monetization. Currently, the number of data shares on public channels has significantly decreased compared to the past.
- They share lists of domains with identified vulnerabilities, pricing each domain at 500 USDT. They offer a one-on-one hacking service, hacking the target desired by the buyer and privately selling the data.
- As of November 13, 2023, as shown in Figure 6, although the channel primarily focuses on sales, there is a case where loan records from a Hongdae IT storefront loan were leaked. This incident occurred when the customer requested data extraction but failed to pay appropriately, leading to the public release of the leaked data on the Telegram channel without receiving proper compensation.
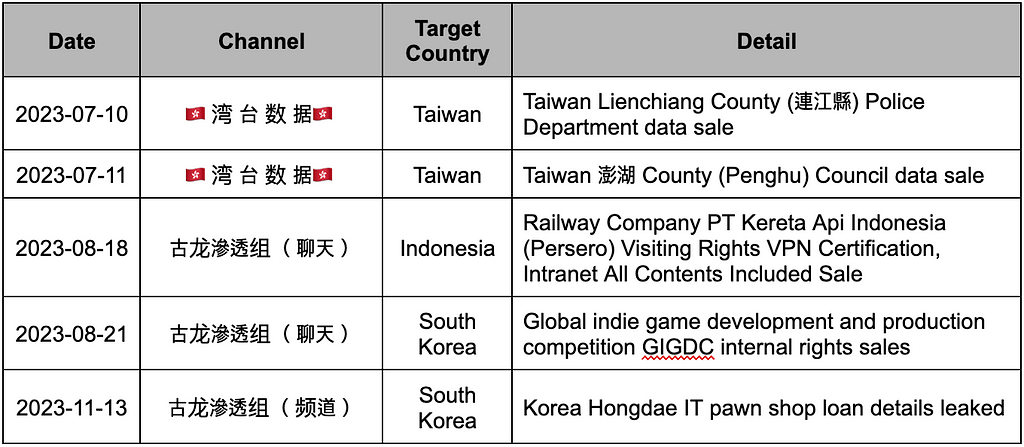 Table 11. The main threatening actions of 古龙渗透组
Table 11. The main threatening actions of 古龙渗透组1.4.2. Most Active Leak Channel — Darknet Marauders Hacker Team
Darknet Marauders Hacker Team is a cybercrime group active on Telegram since June 14, 2023. They introduced themselves as a team rebuilt by Rezz, who restructured Lucifer in 2018. Although the Darknet Marauders Hacker Team was active for three months, they abruptly halted their activities in October 2023 without any separate notice.
- The group claimed to have members such as Killnet, a retired member of the Syrian Cyber Army, and a former Ali/Tencent network engineer.
- (June 14, 2023) While initially stating that they operated solely for financial gain, during the early stages of their activities, they declared their intention to demonstrate their skills by targeting government networks of adversarial nations and illegal gambling platforms.
- (November 25, 2023) a vote was conducted to decide whether to commemorate or close the channel. As of November 30, 2023, their activities have been temporarily suspended.
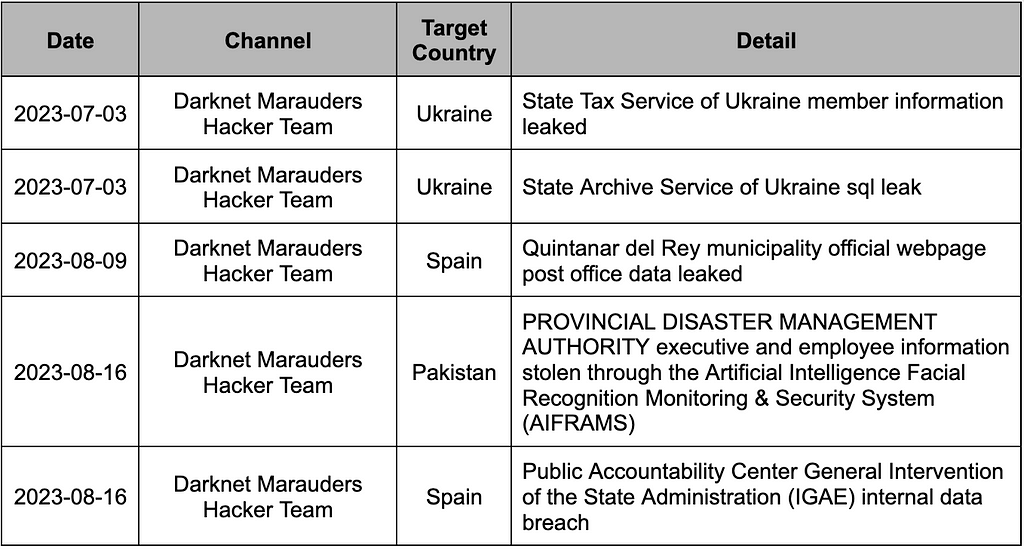 Table 12. Top threat actions by Darknet Marauders Hacker Team
Table 12. Top threat actions by Darknet Marauders Hacker Team2. Deep Dive into Chinese Telegram Activities
2.1. Overview of Chinese Telegram Channel Activity
- We analyzed the trends in Chinese Telegram based on the Top 30 channels and chat rooms with the highest number of leakage cases, as illustrated in Figure 4.
- The total number of Telegram messages generated in these 30 channels during the year's second half amounted to 115,166.
- As depicted in Figure 8, it was observed that the message count increased around mid-September, indicating a rise in communication frequency among users. This increase in message count contrasts with the decrease in threat posts observed in Figure 2.
- The speculated reasons for the increase in message count during the second half of the year are as follows:
- While user-to-user communication increased, direct transactions and attempts at attacks related to threat posts may have shifted to undisclosed locations such as DMs and VIP channels. This change could lead to increased chat activity while simultaneously reducing leakage incidents.
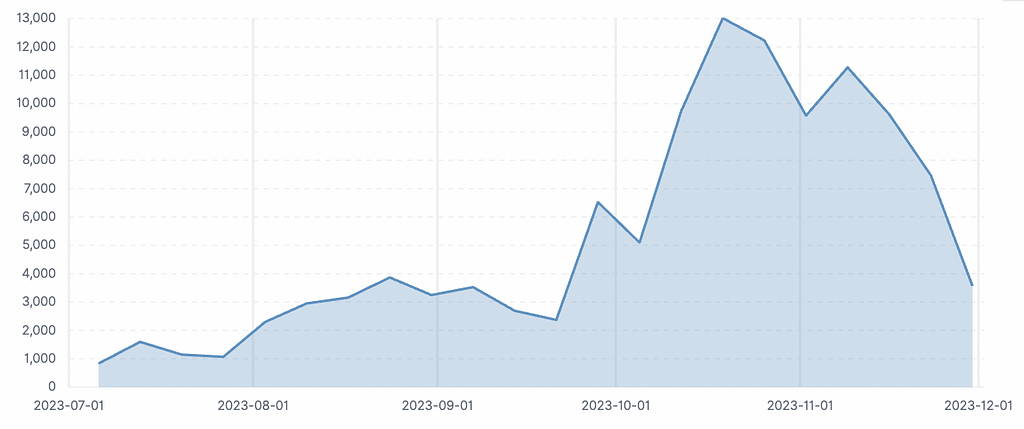 Figure 8. Message frequency graph for 30 chat rooms
Figure 8. Message frequency graph for 30 chat rooms2.2. Analysis of Connectivity of Chinese Telegram Channels
- Message Forwarding is a feature that allows messages to be shared between channels, contributing to the spread of information on Telegram. We generated a network graph based on message-forwarding indicators to identify user relationships and users leading information dissemination across the 30 channels.
- According to Figure 9, in mid-September 2023, which marked an increase in user communication, there was a surge in chat activity. However, when interpreted in conjunction with the decrease in data leaks, it raised the possibility of a change contrary to the existing pattern, where direct transactions between sellers and buyers, as well as simulated attacks, were observed in public channels.
- Therefore, futher analysis was needed for this specific period. As a result, network graphs were created for both before and after this period to grasp the overall trends during these periods, as shown in Figure 9.
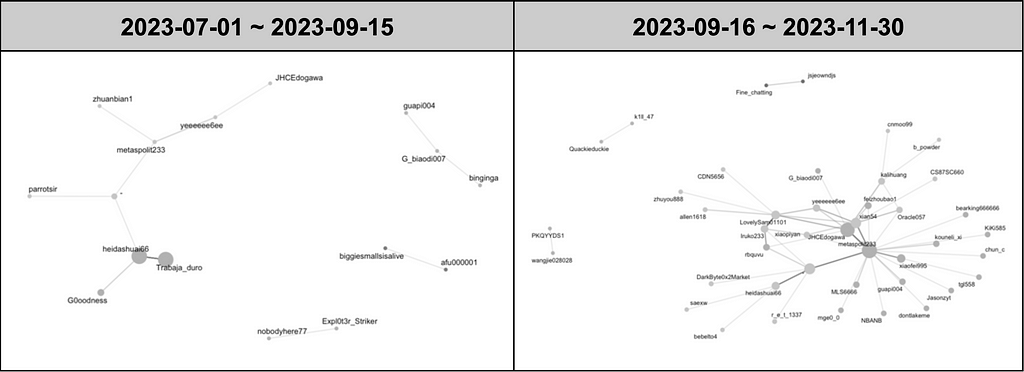 Figure 9. Network graph between users based on forwarding of 30 chat rooms by period
Figure 9. Network graph between users based on forwarding of 30 chat rooms by period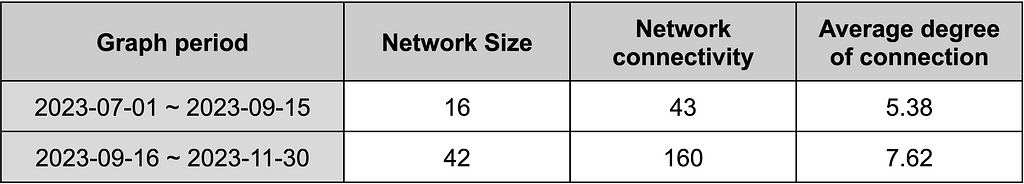 Table 13. Network indicators between users based on forwarding of 30 chat rooms by period
Table 13. Network indicators between users based on forwarding of 30 chat rooms by period- The network size based on the number of users is interpreted as more complex when larger, indicating diverse individual interactions. The network size from July 1 to September 15 was 16; however, in the network graph from September 16 to November 30, the network size increased to 42. This observation confirms that the network among Chinese Telegram users is growing over time, indicating increased interaction among more users.
- Network connectivity based on the frequency of connections among users reflects the number of direct relationships involved in information and resource exchange. A higher value suggests closer connections between user relationships. The network connectivity from July 1 to September 15 was 43, while in the network graph from September 16 to November 30, it exhibited a significant fourfold increase, reaching 160. This implies that the closeness among Chinese Telegram users has increased over time, suggesting that users accessing other channels has become more convenient, fostering a rapidly forming community environment.
- The average degree of connectivity, indicating the average number of other users each user is connected to, increased from 5.38 to 7.62.
- Moving into the recent quarter, the network size of Chinese Telegram has expanded, broadening the scope of exchanges and communications. This expansion indicates a faster pace of information dissemination and an enlarged pathway, potentially leading to changes in communication patterns, such as a shift from public disclosures of leakage, sales, and attack simulations to more private contacts to prevent information leakage to law enforcement or other users.
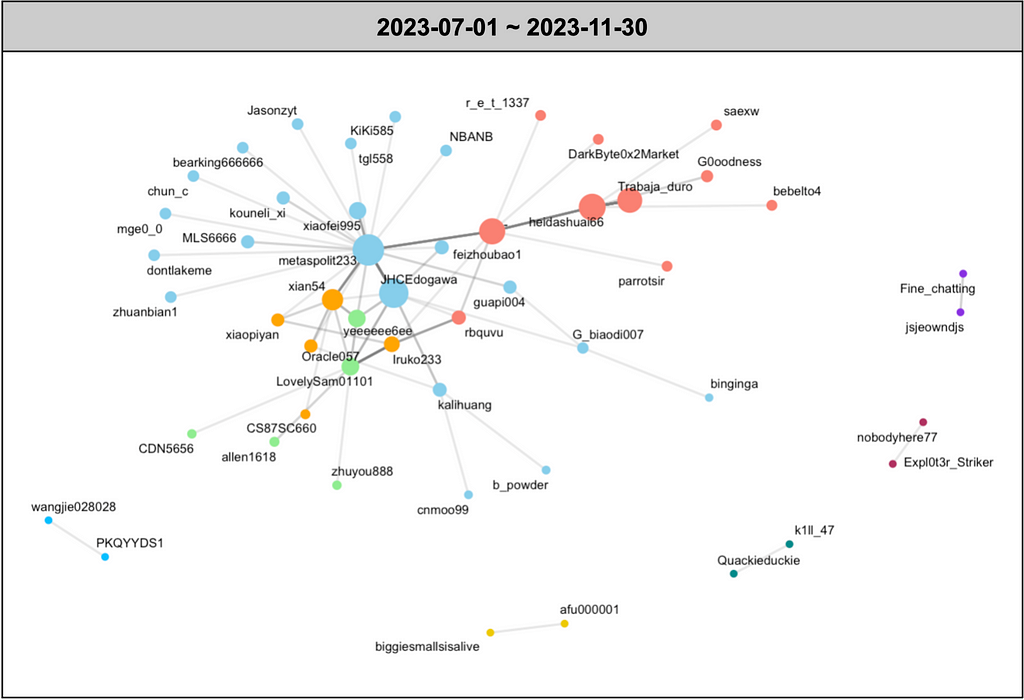 Figure 10. Network graph between users based on the forwarding of 30 chat rooms
Figure 10. Network graph between users based on the forwarding of 30 chat rooms- You can observe the user network graph for the second half of 2023, generated using the same method, in Figure 10.
- In Figure 10, different colors represent users based on the communities derived by the Infomaps algorithm, which classifies small communities within an extensive network. Among these, the community represented in sky blue was identified as a large community within the network.
- This community was found to be primarily active in the Oracle 网络空间安全交流群组 channel. Users in this community engaged in daily conversations and tended to forward messages from other channels, sharing information.
- Examples of messages forwarded to the Oracle 网络空间安全交流群组 channel are as follows:
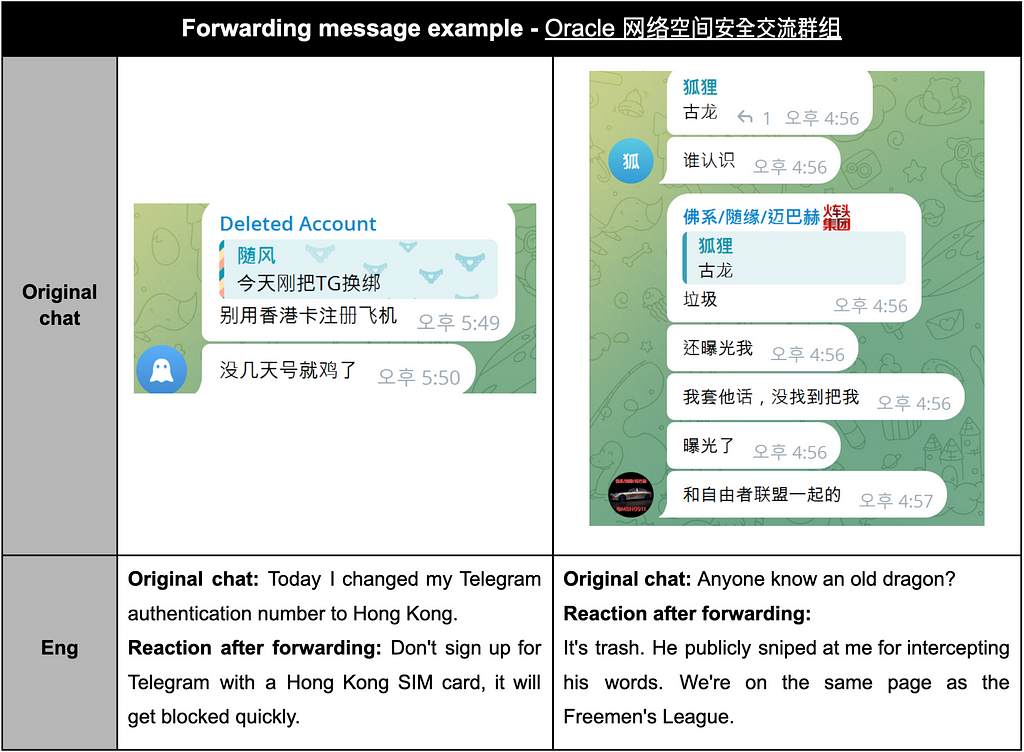 Table 14. Forwarding message example — Oracle 网络空间安全交流群组
Table 14. Forwarding message example — Oracle 网络空间安全交流群组- In Figure 10, the user who contributed the most to the dissemination of information by forwarding messages from other channels to different channels was metaspolit233. Other users contributing to this activity can be identified in Table 15.
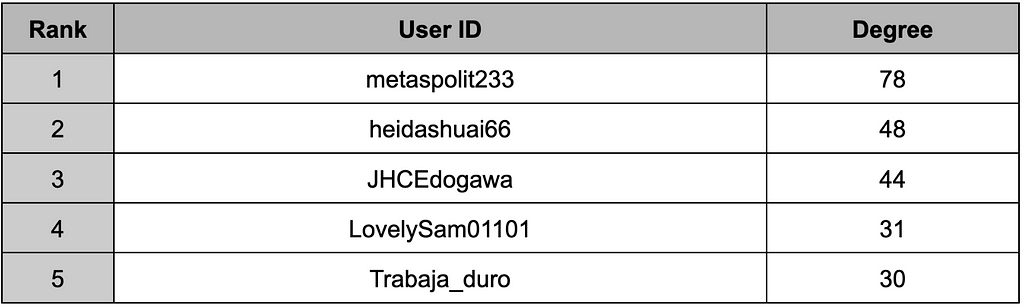 Table 15. Top 5 users with the highest number of forwarding
Table 15. Top 5 users with the highest number of forwarding2.2.1. Most Active User (1) — 年(Ni Yan, @metaspolit233)
- 年(Ni Yan) actively forwards messages by responding to messages from other users in the chat room where they are most active. It has been confirmed that they participate in conversations about cybersecurity knowledge during routine discussions.
- Moreover, 年 employs forwarding to publicly counter and mock messages that appear to involve suspicious activities or exhibit a lack of security knowledge from others.
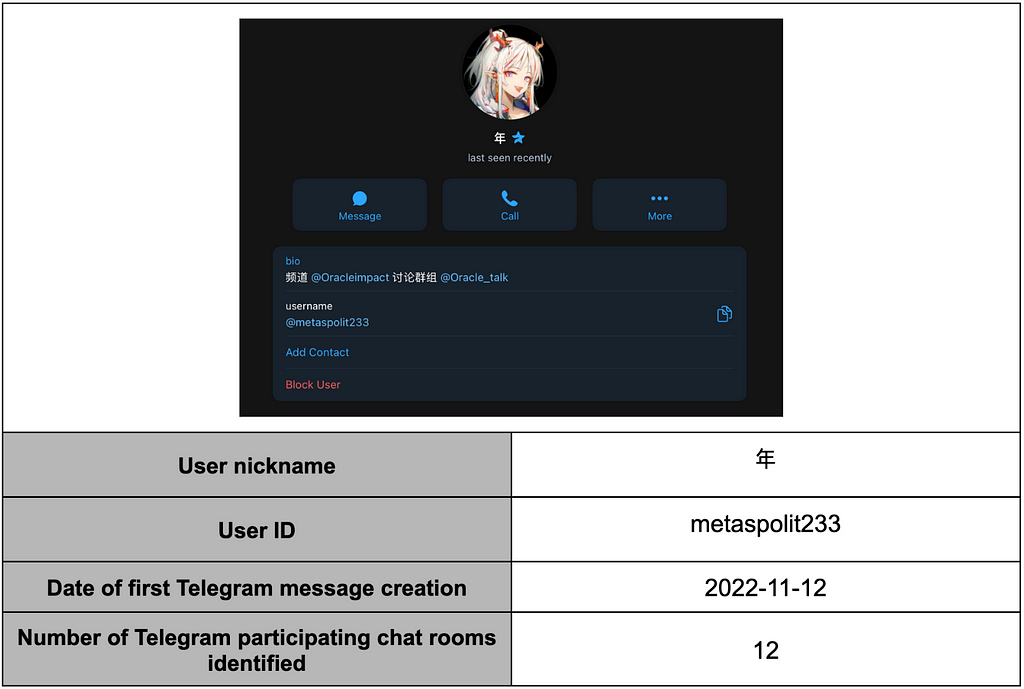 Table 16. 年(Ni Yan) User profile
Table 16. 年(Ni Yan) User profile- The user frequently discusses cybersecurity topics such as RCE, 0-day, N-day, and DDoS, alongside casual conversations.
- They emphasize that they do not hack to acquire money. Within the chat room, this user is referred to as 表姐 (older sister), the official leader. It is known that they have merged two groups, 晓骑营 (Xiaochiying), which attacked South Korea, and Teng Snake.
- The user has been observed participating in cyber threats, including defacing the Saemangeum Power Plant website and attacking a library and a public internet management center in Thailand.
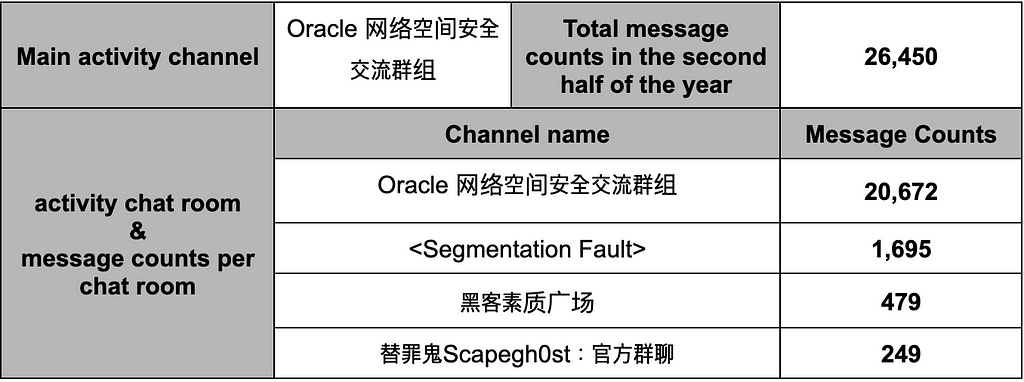 Table 17.年(Ni Yan)’s activity details in the second half of 2023
Table 17.年(Ni Yan)’s activity details in the second half of 20232.2.2. Most Active User (2) — “ 黑 大帅”(heidashuai, @heidashuai66)
- “黑 大帅” in their primary activity chat room, primarily shares GitHub addresses containing information that could be utilized for attacks, such as CVE vulnerabilities, SQL injection, and exploit tools.
- After Japan released contaminated water, this user took the lead in encouraging the chat room members to launch collective attacks on Japan (OpJapan).
- In the main activity chat room, “Hacker -军火库”(聊天), managed by “黑 大帅”, there are users not only from China but also those who communicate in Russian and English. A translation bot is used to translate foreign languages into Chinese.
- Forwarding is utilized to share knowledge, build friendships, and facilitate communication.
- Messages from “黑 大帅” are forwarded to the Oracle 网络空间安全交流群组 channel, and interactions with 年, who was active in that channel, have also been confirmed.
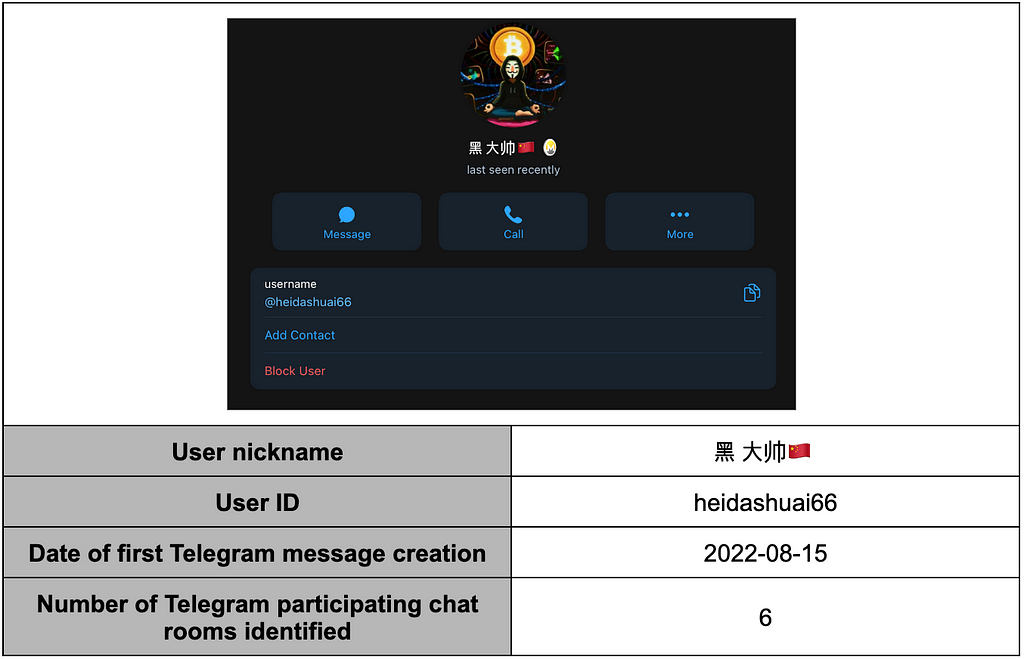 Table 18. 黑 大帅 User profile
Table 18. 黑 大帅 User profile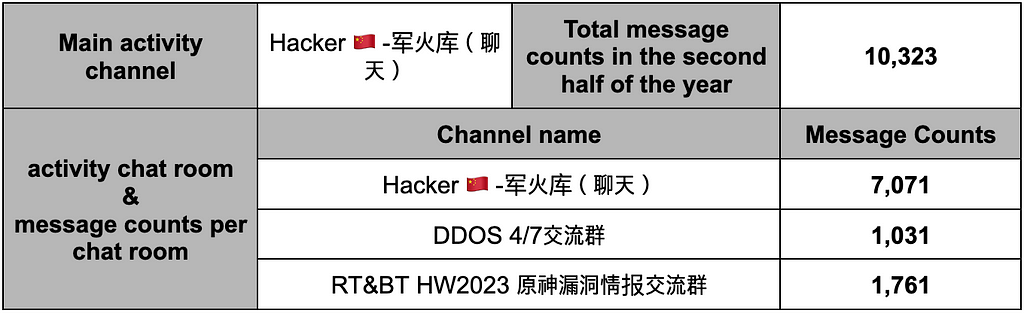 Table 19. 黑 大帅’s activity details in the second half of 2023
Table 19. 黑 大帅’s activity details in the second half of 20232.3. What Chinese Telegram Users Are Saying: A Look At Reactions to Specific Issues
2.3.1. “护网” (Huwang) Campaign
- The Huwang campaign is an annual initiative led by China’s public security department to assess the network security of enterprises and institutions.
- Red and blue teams are organized, where the red team initiates network attacks on the blue team (enterprises and institutions) within a specified period to detect their security vulnerabilities.
- The goal is to strengthen the network security of enterprises and institutions by responding to cyber attacks.
- This campaign occurs nationwide and is conducted at the city and enterprise levels in July and August. It was confirmed that 河北 廊坊市 (Hebei Langfang City) held the Huwang campaign at 北华航天工业学院 (North China Aerospace Industry Research Institute) from August 21 to August 25 this year.
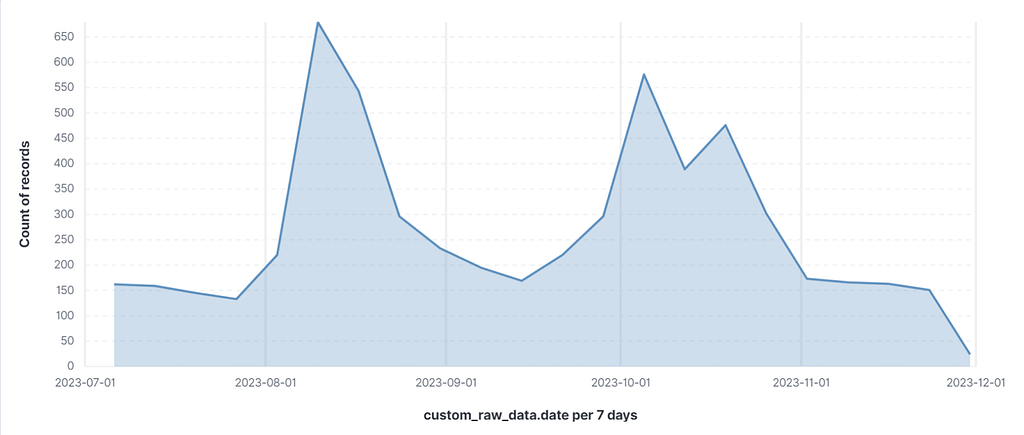 Figure 11. Change in keyword mention amount during the Huwang period
Figure 11. Change in keyword mention amount during the Huwang period- During August, when the Huwang campaign was taking place, there was an increase in mentions of keywords related to vulnerabilities, hardware (HW), etc., within the Chinese Telegram community. Through this, it can be confirmed that Chinese Telegram users actively participated in domestic network security activities.
- In August, there were many discussions about participating in the Huwang campaign, its requirements, remuneration details, etc. Even after the Huwang period ended, the high volume of discussions continued. This is because participants shared the vulnerabilities they discovered during the campaign or provided reviews of their experiences, contributing to the ongoing talks.
2.3.2. Reactions to International Issues
- To understand the responses of Chinese Telegram users to events outside China, an analysis was conducted on the mentioned frequency of specific event-related keywords and their corresponding attack activities.
- The report delves into the reactions of Chinese Telegram users during the second half of 2023 to two globally significant incidents: the release of contaminated water by Japan and the Israeli-Palestinian conflict. Further details on these issues can be found in the following sections of the report.
Detailed Analysis of ‘Operation Japan’ Campaign
Detailed Analysis of DDW Events related to Israeli–Palestine(Hamas) War
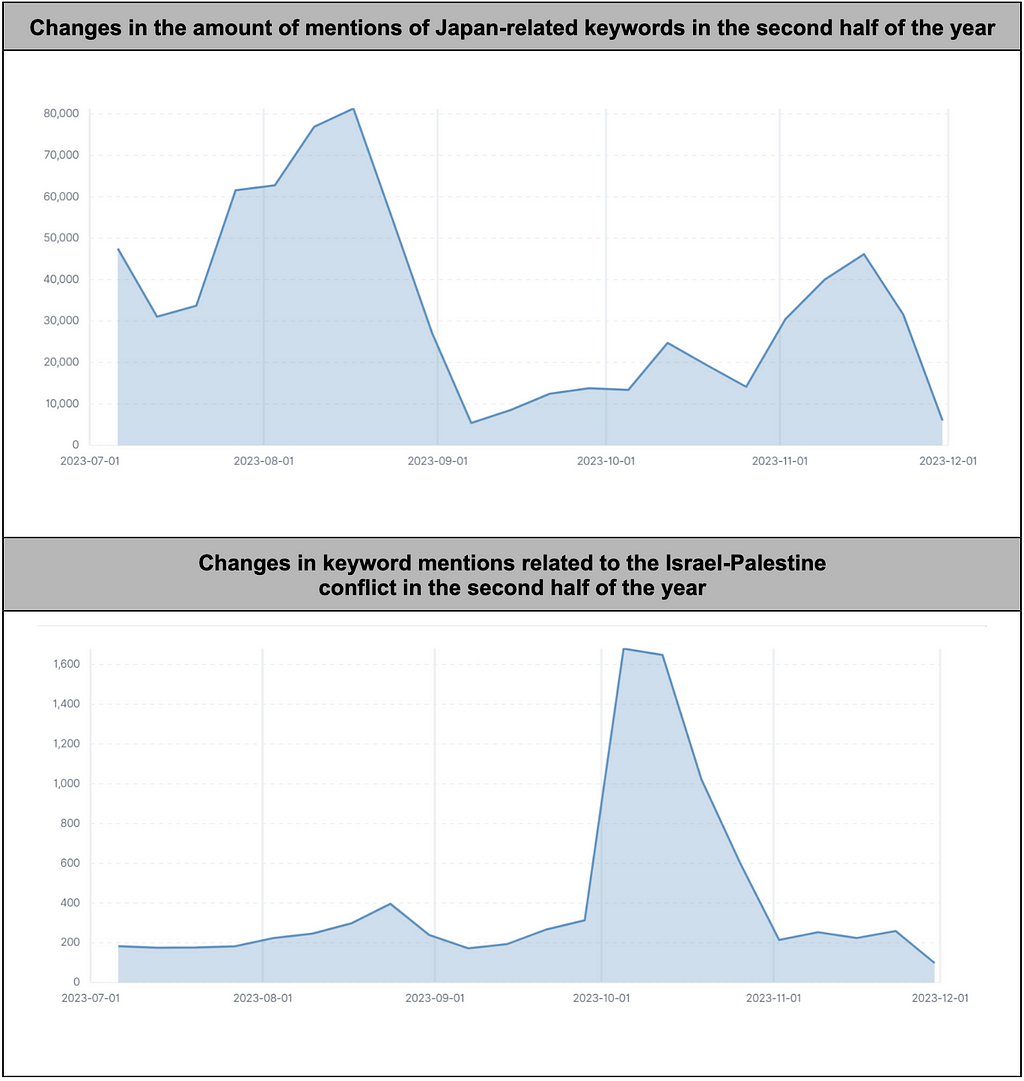 Figure 12. Change in keyword mentions related to specific issues in the second half of the year
Figure 12. Change in keyword mentions related to specific issues in the second half of the year- Comparing the mentioned frequencies of the two issues, it is evident that Chinese Telegram users show interest and reactions to global events.
- The keyword mentions related to Japan saw a sharp increase from mid-July when the final review of Japan’s contaminated water discharge was underway.
- The highest mention frequency occurred on August 24, the day of the discharge, followed by a gradual decline.
- In the case of the Israeli-Palestinian conflict, the mention frequency of keywords related to the conflict significantly rose immediately after the October 7, 2023 outbreak. While there were changes in mention frequency based on the timing of the issues, a more aggressive response involving calls for attacks or direct participation in attacks was primarily observed in the context of the Japan-contaminated water issue.
- This could be attributed to China's proximity to Japan and the potential direct impact China might face due to Japan’s contaminated water discharge.
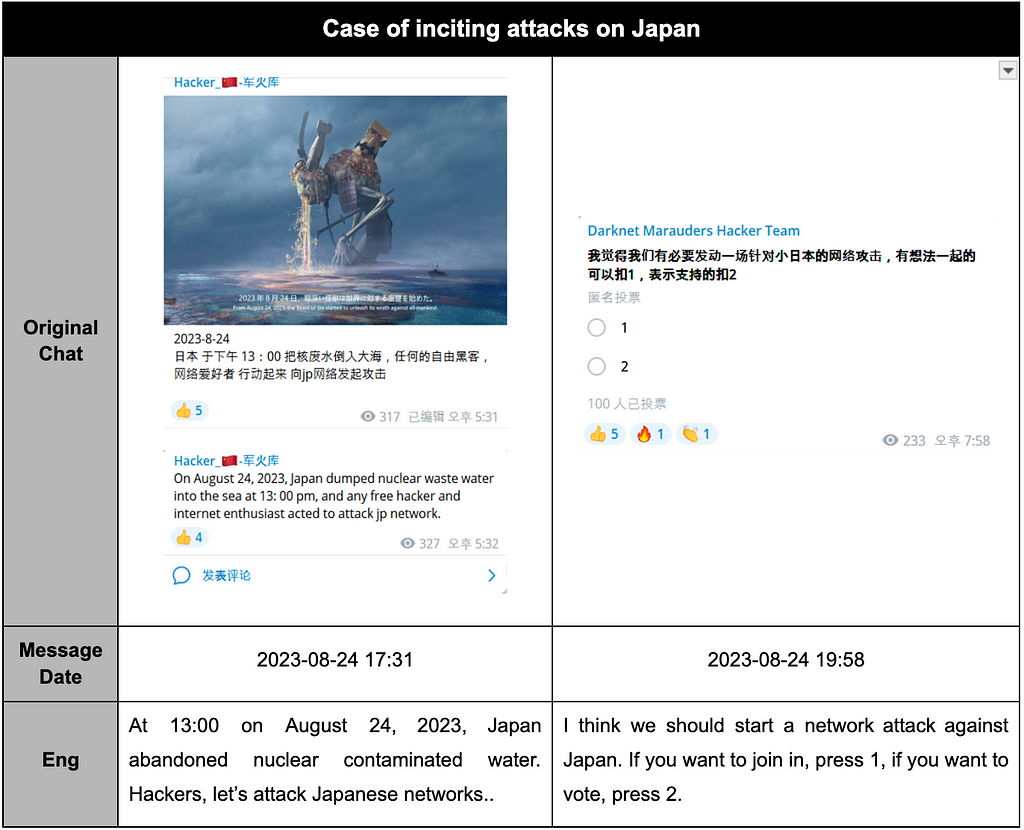 Table 20. Cases of inciting attacks on Japan
Table 20. Cases of inciting attacks on JapanConclusion
- In the second half of 2023, while monitoring 1,252 Chinese Telegram channels and chat rooms, 620 threatening posts were identified. Notably, the number of threatening posts was highest in the third quarter, followed by a decreasing trend.
- After August, there was a decrease in the activity of some channels that had uploaded many threatening posts. Additionally, there was a recent tendency to refrain from direct mentions of targets in public channels, encouraging communication through DMs, private channels, etc., which contributes to the decrease in threatening posts.
- The sectors with the most leaks were associated with the Government, while the e-commerce sector had the highest sales. Channels for leaks and sales were clearly distinguished based on profit pursuit, the display of hacking capabilities, political ideology, etc.
- The message volume on Chinese Telegram saw a significant increase in the fourth quarter compared to the third quarter of 2023. Analyzing the before and after the point of change, it was observed that the network size among Chinese Telegram channels increased, leading to a higher speed and broader range of information dissemination.
- This change facilitated the rapid and broad spread of crucial information, altering the pattern of leaks, sales, and attack simulations, which shifted to private contacts to prevent information from being publicly disclosed to investigative authorities or other users.
- On Chinese Telegram, issues directly related to China, such as the ‘护网’ (Huwang) campaign and Japan-related matters, witnessed active discussions and information sharing. However, keyword mentions were identified without substantial engagement for international issues less directly associated with China. This indicates that instigation and attacks were primarily directed toward issues with direct implications for China.
- While data leaks, sales, and other threatening posts persist on Chinese Telegram, the increasing community size suggests a higher frequency of user interactions. The reduction in direct target mentions implies that in 2024, unseen threats might emerge.
- Close monitoring and response to Chinese Telegram-based threats are recommended to respond to these changes effectively. Furthermore, adopting security solutions and fostering collaboration between the security industry and businesses is strongly advised.

Homepage: https://s2w.inc
Facebook: https://www.facebook.com/S2WLAB
Twitter: https://twitter.com/S2W_Official
Story of H2 2023: A Deep Dive into Data Leakage and Commerce in Chinese Telegram Channels (English… was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.