Author: Jiho Kim & Huiseong Yang & Kyunghee Kim | S2W TALON
Last Modified : Aug 11, 2023
 Photo by Nong on Unsplash
Photo by Nong on UnsplashExecutive Summary
- This report analyzes the key issues related to new and existing ransomware groups active in the first half of 2023.
- In H1 2023, 35 new ransomware groups were identified, with May seeing the highest number of new ransomware groups during the period.
- New ransomware groups can be subdivided into those operating Leak sites and those using the source code or builders of existing ransomware.
— In H1 2023, we identified 22 ransomware groups with newly discovered Leak sites, 3 groups with changed Leak site addresses, and 1 group that ceased operations.
— When categorizing the new ransomware groups’ Leak sites by type, there is an increasing trend of groups using Telegram and Twitter, along with Onion sites built on the Tor Network.
— Among the new ransomware groups, we identified a total of 14 groups that used existing ransomware families, with the Babuk family accounting for half of them.
- Ransomware-related issues in H1 2023 were categorized into Ransomware Group, Affiliate, Attack Campaign, and Duplicated Victims.
— Ransomware Group: Ransomware has expanded its target operating system including Linux, MacOS, and more, and some ransomware groups were found to have a similar appearance to the Leak sites.
— Affiliate: Initial Access Brokers and RaaS Operators continue to be active, and pentesters are also in high demand as they are constantly being recruited on the deep & dark web.
— Attack Campaign: CLOP exploited the most vulnerabilities in H1, and the leaked data of numerous organizations affected by these vulnerabilities was uploaded to the Leak site.
— Duplicated Victims: The number of organizations victimized by overlapping ransomware groups is 27 in total, and 21 of these groups have disclosed the attack involving duplicate organizations.
1. New Ransomware Groups in H1 2023
- There were a total of 35 new ransomware groups tracked by S2W in the first half of 2023, with no new ransomware groups emerging in January and an average of 6.96 new groups discovered from February through June.
- In May, a total of 10 new ransomware groups emerged, marking it as the period with the highest number of group appearances in the first half of the year.
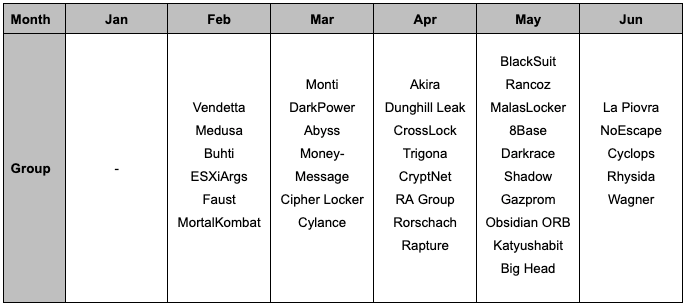 Table 1. New Ransomware Groups in H1 2023
Table 1. New Ransomware Groups in H1 20232. Categorizing New Ransomware Groups
We further analyzed the new ransomware groups that were active in H1 2023 by categorizing them according to their characteristics, and for this purpose, we subdivided them into groups operating leak sites and using existing ransomware families.
2.1. Ransomware Groups operating Leak site
Ransomware groups are using a double-extortion: encrypting files for ransom and threatening to release the data on their Leak sites. This means that most ransomware groups are operating Leak sites, and the sites are important infrastructure for ransomware groups. During H1 2023, we tracked Leak site status changes and identified groups that were taken offline due to address changes or ceased operations.
- A total of 22 new ransomware groups were found with Leak sites.
- In H1 2023, we identified 4 groups that changed their Leak site status.
- 3 groups changed their Leak site addresses, including the IceFire, Stormous, and Nokoyawa leaks.
- The ransomware group Hive was identified as the one that ceased operations and its Leak site.
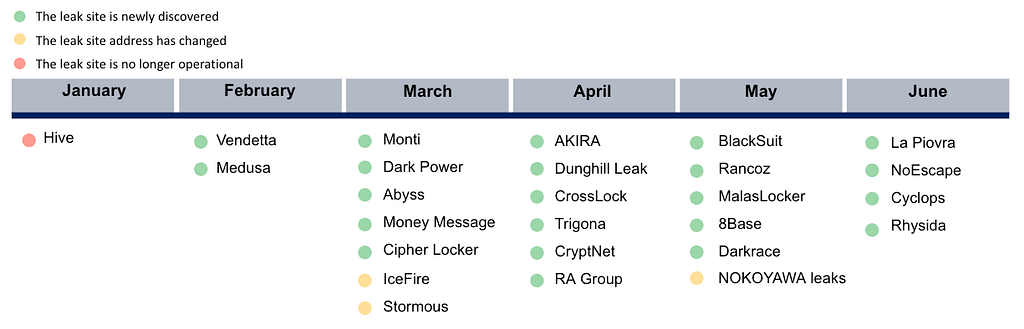 Figure 1. Ransomware Group with Leak Site Status Change
Figure 1. Ransomware Group with Leak Site Status ChangeWhile most ransomware groups build and operate their own leak sites on the Tor Network to disclose stolen data, there was an increase in the number of groups using additional channels such as Telegram and Twitter, in addition to the Onion site.
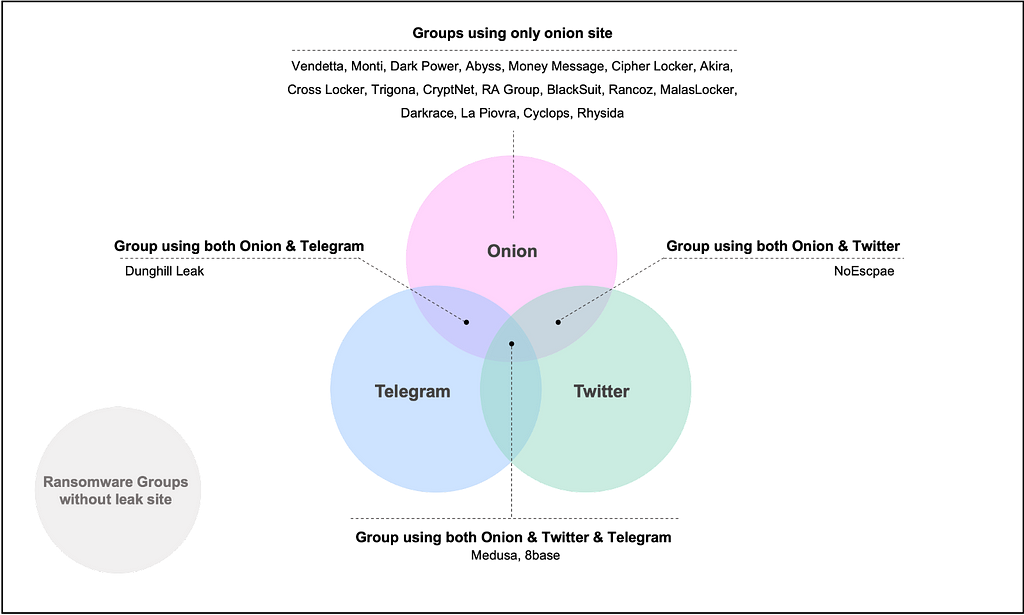 Figure 2. New Ransomware Groups with Leak Sites Found
Figure 2. New Ransomware Groups with Leak Sites Found2.2. Ransomware Family
While some ransomware groups develop and use their own ransomware, others purchase the source code of other ransomware groups or use leaked source code and builders to customize existing ransomware. In H1 2023, we identified 14 new ransomware families that were created using other groups’ builders or leaked source code, with the Babuk Family accounting for half of the total, indicating that many ransomware groups have cited the source code of the Babuk ransomware.
- Dunghill, Cyclops, RA Group, Monti, and BlackSuit were operating own leak sites.
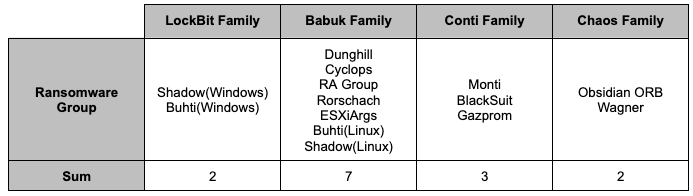 Table 2. New ransomware groups categorized into ransomware families
Table 2. New ransomware groups categorized into ransomware families2.2.1. LockBit Family
- Analyst1 noted that LockBit previously employed a developer from the BlackMatter ransomware group, and that developer built LockBit 3.0/Black on top of the BlackMatter ransomware.
- The LockBit-based ransomware families all refer to the ransomware generated from the LockBit 3.0/Black builder, which was leaked by a developer in September 2022.
- Among the ransomware families that emerged in H1 2023, the LockBit family includes Shadow (Windows) and Buhti (Windows) ransomware.
- Symantec has dubbed the ransomware group using Buhti ransomware Blacktail.
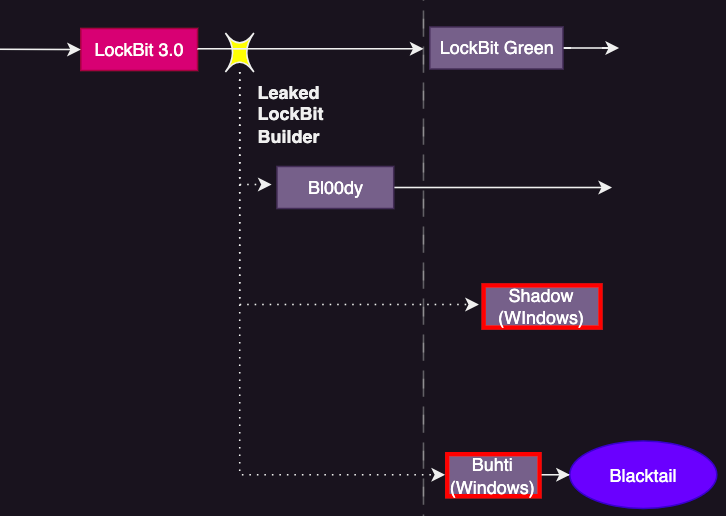 Figure 3. LockBit Family
Figure 3. LockBit Family2.2.2. Babuk Family
- The Babuk Family refers to ransomware generated by reusing the builder and code of the Babuk ransomware, following the disclosing of the Babuk ransomware builder in June 2021 and the leak of the Babuk source code in September 2021.
- Among the ransomware families that emerged in H1 2023, Babuk Family includes Dunghill, Cyclops, RA Group, Rorschach, ESXiArgs, Buhti (Linux), and Shadow (Linux) ransomware.
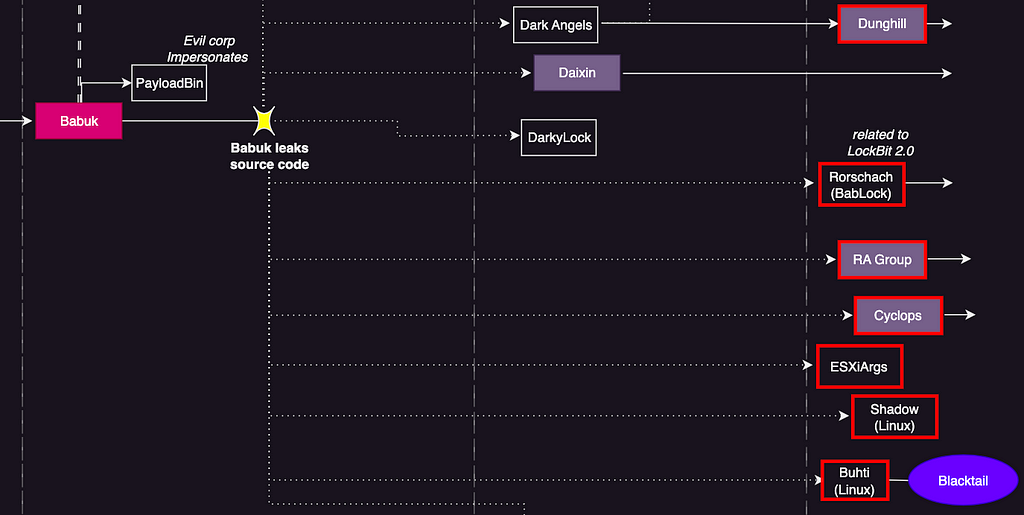 Figure 4. Babuk Family
Figure 4. Babuk Family2.2.3. Conti Family
- The Conti Family refers to ransomware generated by citing Conti’s source code leaked from an insider of pro-Russian Conti during the Russian invasion of Ukraine in February 2022, as well as ransomware derived from ransomware used by subgroups of Conti (BlackBasta, BlackByte, and Royal).
- Among the ransomware families categorized as Conti Family in H1 2023 are Monti, BlackSuit, and Gazprom ransomware.
- According to Yelisey Bohuslavskiy, the Royal Spider group, which operates Royal ransomware as RaaS, uses not only Royal ransomware but also BlackSuit ransomware.
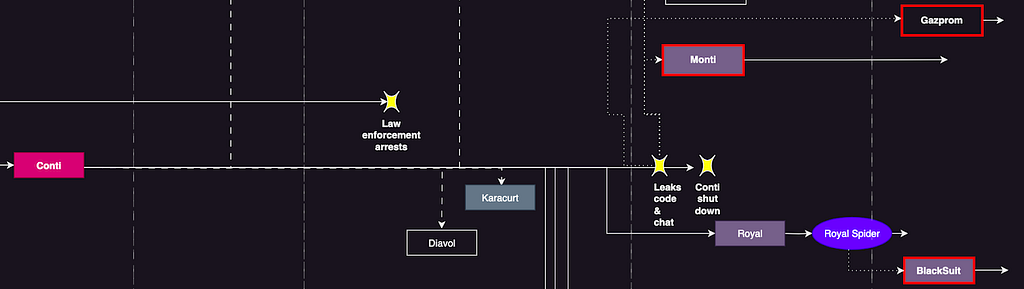 Figure 5. Conti Family
Figure 5. Conti Family2.2.4. Chaos Family
- Chaos Family refers to ransomware families generated by the Chaos ransomware builder that have been uploaded to dark web forums for user advice since June 2021.
- Ransomware families categorized as Chaos Family in H1 2023 include Obsidian ORB and Wagner ransomware.
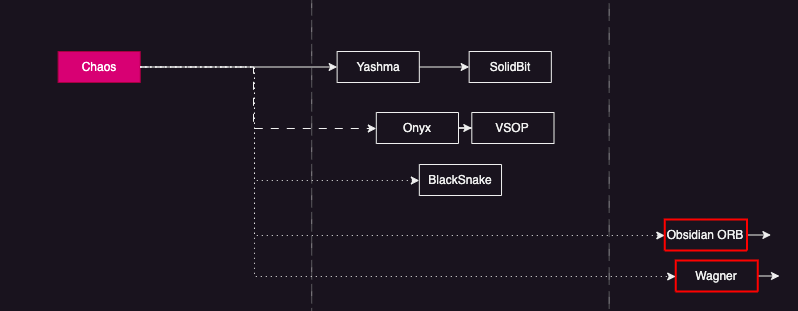 Figure 6. Chaos Family
Figure 6. Chaos Family3. Key Issues in the first half of the year
We summarized key issues that occurred in H1 2023 and categorized them into Ransomware Group, Affiliate, Attack Techniques, and Duplicated Victims. In this context, not only new ransomware groups are discussed, but also the major trends of existing ransomware groups are covered.
3.1. Ransomware Group
Ransomware groups are active on various deep and dark web forums and Telegrams to recruit affiliates, promote RaaS, and purchase Initial Access from Initial Access Brokers (IABs). The following ransomware groups have been identified with such activity in H1 2023.
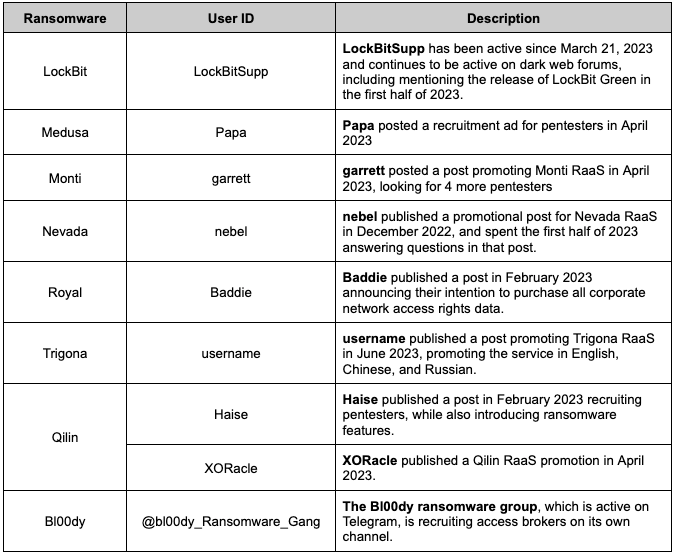 Table 3. Ransomware groups and DDW users active in the first half of 2023
Table 3. Ransomware groups and DDW users active in the first half of 20233.1.1 Version Control
Ransomware-as-a-Service groups are constantly updating their ransomware to avoid detection and maintain their brand reputation. In H1 2023, ransomware from the LockBit, BlackCat, BlackByte, Trigona, CLOP, and IceFire groups have been updated. In particular, the LockBit, Trigona, CLOP, and IceFire ransomware have expanded target operating system from Windows to Linux and MacOS.
LockBit
- LockBit appeared in September 2019 and has been updated a total of 4 times, and the ransomware has been consistently updated every 6 to 12 months.
- In January 2023, LockBit 4.0/Green was released, and the ransomware was built on the leaked Conti source code.
- In April 2023, LockBit ransomware targeting MacOS was discovered, marking it as the first large RaaS group to develop ransomware specifically aimed at MacOS.
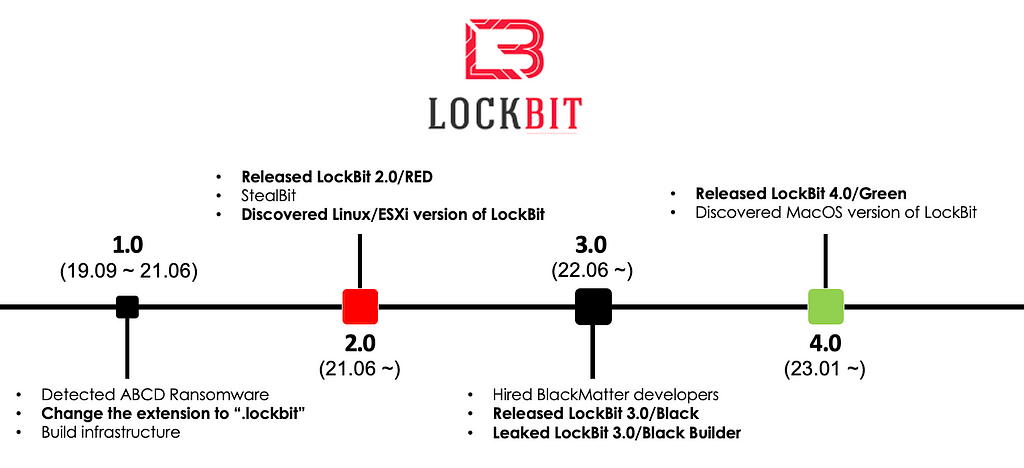 Figure 7. History of LockBit
Figure 7. History of LockBitBlackCat
- The BlackCat ransomware was first disclosed in December 2021, when the group admitted to being a rebranding of BlackMatter in an interview published by The Record.
- In February 2023, BlackCat updated the ransomware to BlackCat 2.0(Sphynx) and released the update to its affiliates.
- In March 2023, a post was published on a dark web forum promoting the updated ransomware.
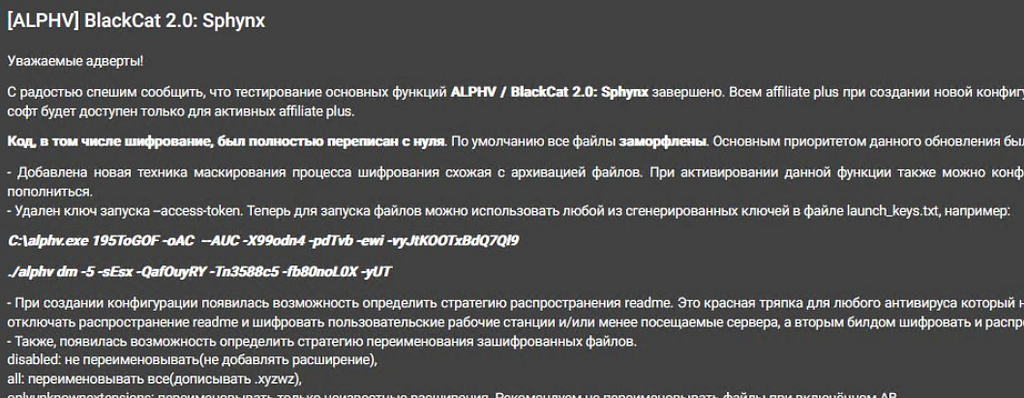
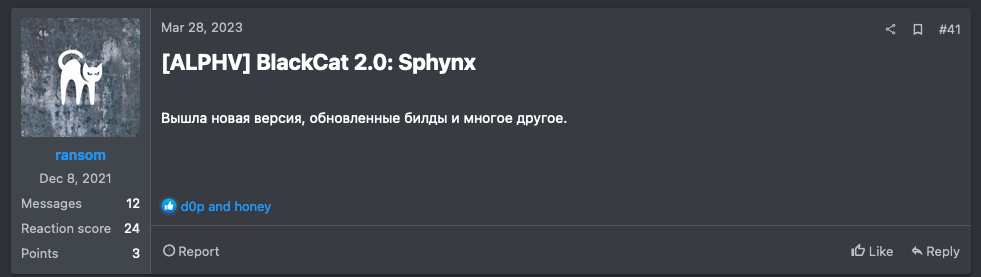 Figure 8. BlackCat 2.0 update announcement (Left) / Figure 9. BlackCat 2.0 promotional post (Right)
Figure 8. BlackCat 2.0 update announcement (Left) / Figure 9. BlackCat 2.0 promotional post (Right)BlackByte
- BlackByte is formerly known as a subgroup of the Conti ransomware group, whose ransomware was first detected in July 2021.
- The initial BlackByte ransomware from July to September 2021 was executed via an obfuscated JavaScript loader, which would eventually execute a .NET DLL in memory.
- Beginning in September 2021, BlackByte ransomware written in Go was discovered, and since then, it has continued to update its capabilities, adding encryption algorithm changes, obfuscation via GoObfuscate, and EDR bypass capabilities.
- In February 2023, BlackByteNT was released, changing the programming language from Go to C++.
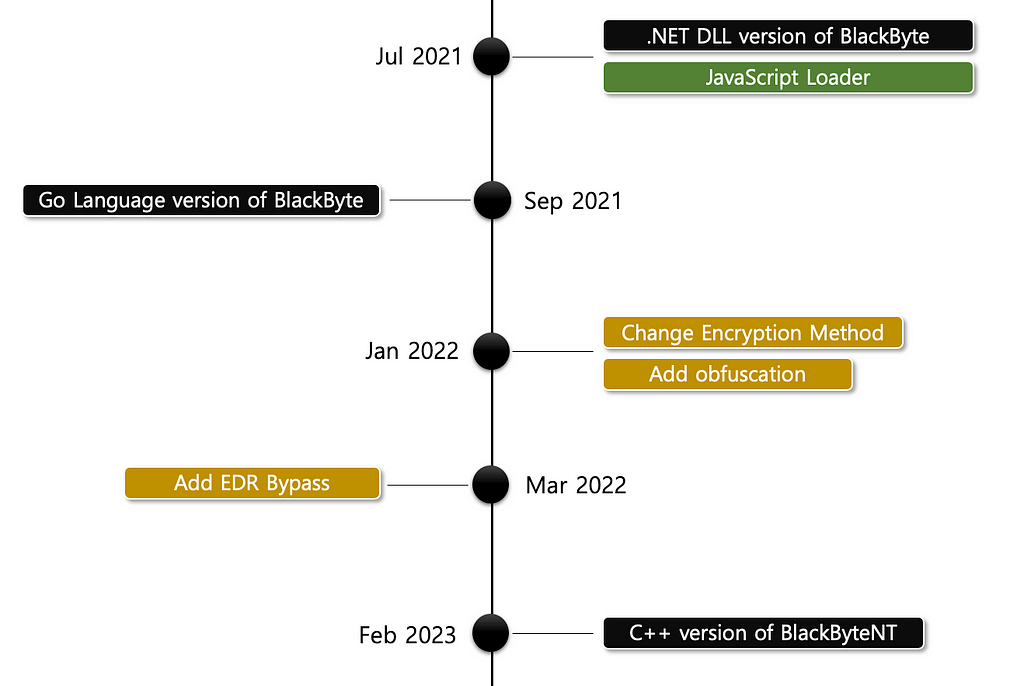 Figure 10. History of BlackByte ransomware
Figure 10. History of BlackByte ransomwareTrigona
- Trigona was discovered in June 2022, and its negotiation site was first disclosed in November 2022.
- In May 2023, a Linux version of the Trigona ransomware was discovered, and it was speculated that it was still in development as the ransom note did not include a negotiation site and a leak site.
- In June 2023, a Windows 64-bit version of the Trigona ransomware was discovered, with some additional parameters from the 32-bit version.
CLOP
- CLOP ransomware was first discovered in February 2019, when the TA505 group used it to launch a large spear-phishing email campaign, and later FIN11, a subgroup of TA505, began utilizing it in their attacks.
- In February 2023, a Linux version of CLOP was discovered, which used similar encryption methods to the Windows version.
- The Linux version had a flaw in its encryption algorithm that allowed it to decrypt encrypted files without paying the ransom.
IceFire
- IceFire was first discovered in August 2022 and initially only targeted Windows operating systems.
- In March 2023, a Linux version of IceFire ransomware was distributed that exploited a vulnerability (CVE-2022–47986) in IBM Aspera Faspex file-sharing software.
3.1.2. Revealed connections between ransomware groups
During the first half of 2023, connections between some ransomware groups were identified as below in order of disclosure.
Nevada — Nokoyawa
- The Nevada ransomware first appeared on the dark web in December 2022, promoting a RaaS program, written in the Rust language with support for Linux and 64-bit Windows operating systems.
- Zscaler raised the link between Nevada and Nokoyawa ransomware in March 2023, stating that it had identified significant code similarities between them, including debug strings, execution parameters, and encryption algorithms.
- The published report also noted that the Nokoyawa ransomware, which was written in C++, began using the Rust language in version 2.0 and has been modified into the Nevada ransomware in later versions, possibly for the purpose of leaking source code or evading detection.
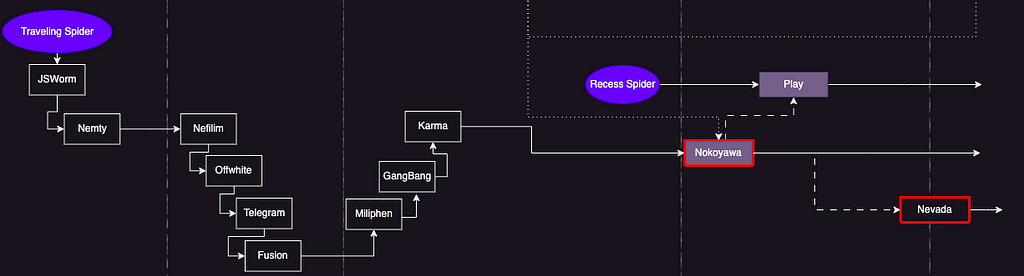 Figure 11. The Nokoyawa-Nevada connection
Figure 11. The Nokoyawa-Nevada connectionRancoz — 0mega
- The Rancoz ransomware’s leak site was first discovered in May 2023. At the time of its initial discovery, it was found to be highly similar to the 0mega ransomware’s leak site, but no further connections have been identified since then.
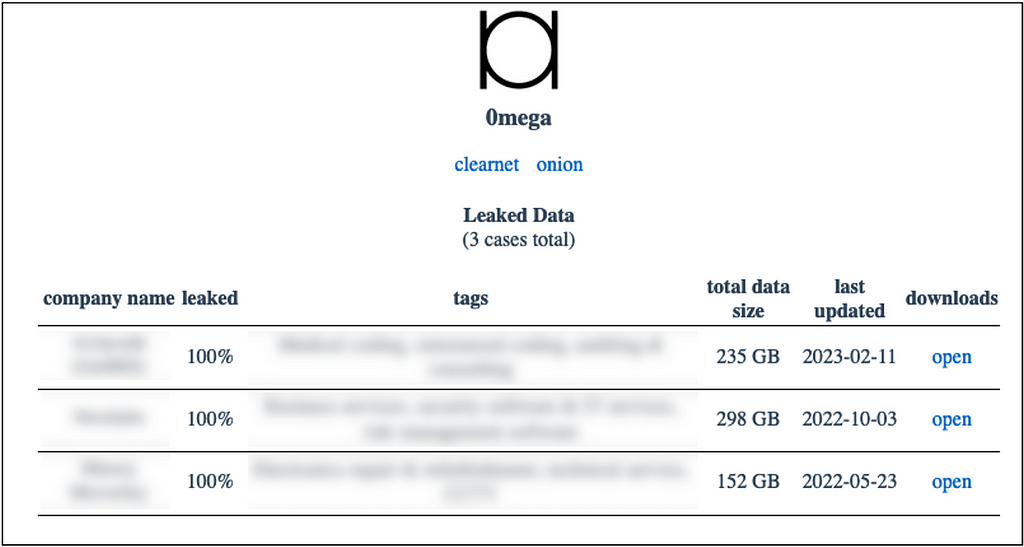
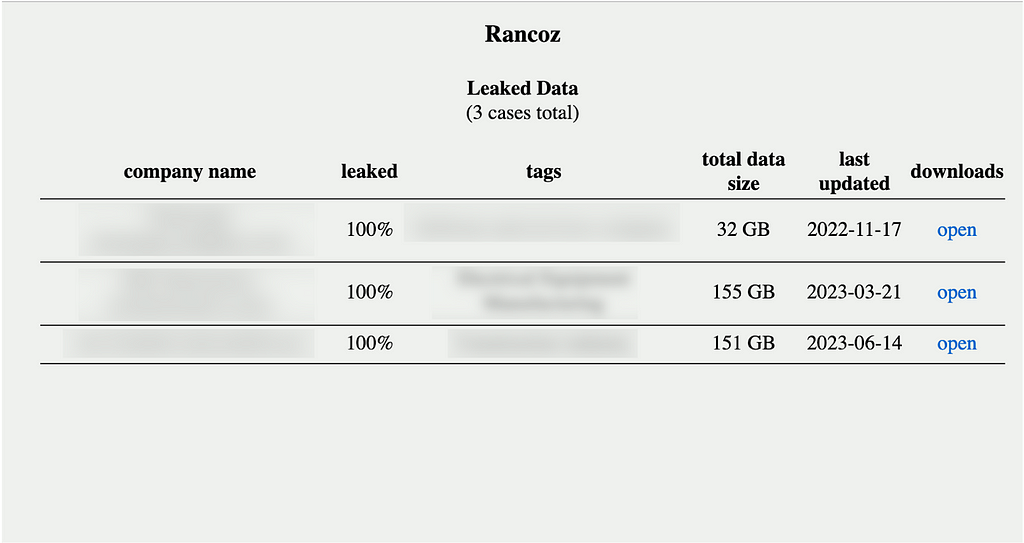 Figure 12. 0mega Leak Site Configuration (Left) / Figure 13. Rancoz Ransomware Leak Site Configuration (Right)
Figure 12. 0mega Leak Site Configuration (Left) / Figure 13. Rancoz Ransomware Leak Site Configuration (Right)8Base — Ransom House & Phobos
- The 8Base ransomware group, whose first leak site was discovered in late May 2023, is also active on Telegram and Twitter.
- VMware noted that the 8Base ransomware uses several previously existing ransomware, most notably the Ransom House and Phobos ransomware.
- According to the report, the wording on the main page of the 8Base ransomware’s leak site and the type of ransom note show a high degree of similarity to Ransom House, but after the initial infiltration, the ransomware was found to be using version 2.9.1 of the Phobos ransomware during the decompression and loading process.

 Figure 14. 8Base ransomware leak site text (Left) / Figure 15. Ransom House leak site text (Right)
Figure 14. 8Base ransomware leak site text (Left) / Figure 15. Ransom House leak site text (Right)Snatch — Nokoyawa
- Since the Nokoyawa ransomware changed its leak site address in May 2023, the Snatch group’s leak site has been linked to the Nokoyawa ransomware due to similarities in UI and wording, as well as a number of overlapping victim organizations.
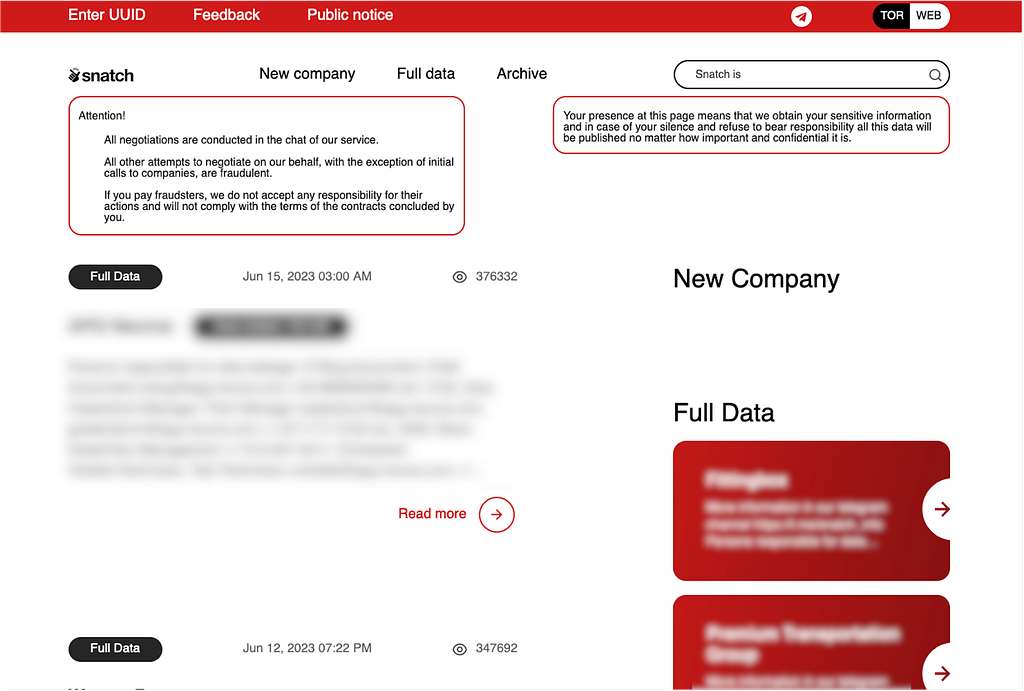
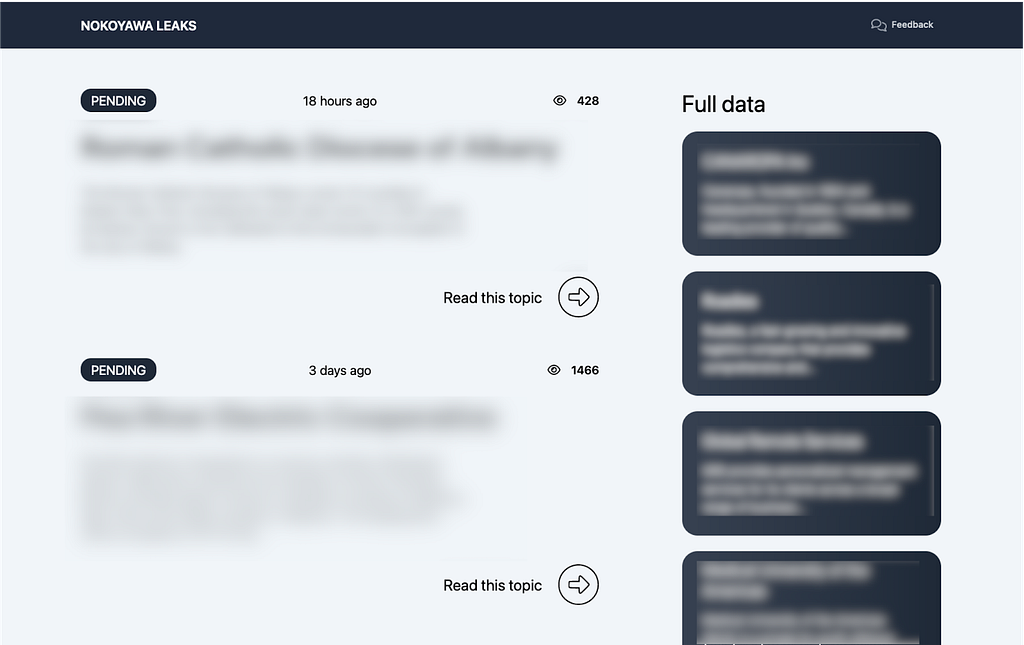 Figure 16. Snatch group’s leak site (Left) / Figure 17. Nokoyawa group’s leak site (Right)
Figure 16. Snatch group’s leak site (Left) / Figure 17. Nokoyawa group’s leak site (Right)3.2. Affiliate
‘Affiliate’ is an individual or group that collaborates with RaaS operators to perform actions such as initial penetration, network lateral movement, data theft, and ransomware distribution.
In this report, unlike the previously known meaning of affiliates, we have approached affiliates as any user or group that helps to gain initial access, and we have divided affiliates into 2 aspects. Initial Access Brokers, selling access information for individuals and specific organizations within the deep and dark web, and Pentesters, who are responsible for the initial penetration process to distribute the ransomware payload.
3.2.1 Initial Access Broker
RaaS operators purchase initial access to targets from Initial Access Brokers (IABs) who are active on various deep and dark web forums. A summary of the disclosures regarding IABs that worked with RaaS Operators in H1 2023 is as follows.
BianLian: 3ger
- After a sale of RDP credentials to a Korean pharmaceutical company was posted on a dark web forum with a completed sale message, the BianLian group disclosed the victimization of the company.
LockBit, REvil: Bassterlord
- An IAB active since 2016, Bassterlord is known to have worked with various ransomware groups since 2019 selling RDP permission information.
- In March 2023, Bassterlord, which has a history of working with ransomware groups such as LockBit and REvil stole access from organizations, announced his retirement.
AvosLocker: sganarelle
- AvosLocker ransomware operator was active on XSS forums and was found to have purchased access to certain organizations from a user, sganarelle.
3.2.2. Pentester
Pentester refers to an attacker who infiltrates the internal infrastructure of the target and distributes ransomware, they are the most important in RaaS. RaaS operators collaborate with them through affiliate programs, and pentesters use the ransomware provided by the RaaS to encrypt files after internal penetration and force the victim company to pay the ransom. They distribute a portion of the earnings to operators through the predetermined distribution ratio of fees set for each RaaS, and they take the majority of the money. The pentesters revealed in H1 2023 in the realm of ransomware are as follows:
BlackCat: UNC4466, DEV-0237, DEV-0501, DEV-0504, DEV-0832
- According to a Mandiant report published in April 2023, UNC4466 is an affiliate of Alphv/BlackCat, a group that uses vulnerabilities in Veritas Backup Exec (CVE-2021–27876, CVE-2021–27877, CVE-2021–27878) to gain access to victimized systems.
- In addition to the UNC4466 group, Will, a CTI researcher at Equinux, tweeted that DEV-0237/Pistachio Tempest, Storm/DEV-0501, DEV-0504/Velvet Tempest, and DEV-0832/Vanilla Tempest are also affiliates of BlackCat.
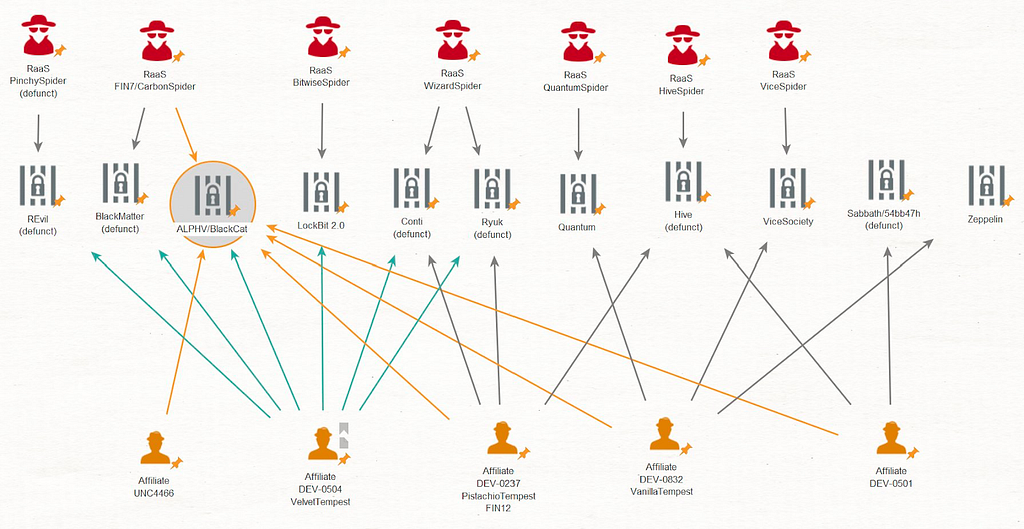 Figure 18. BlackCat Affiliates
Figure 18. BlackCat Affiliates3.3. Attack Techniques
We categorized the impressive attack techniques of RaaS operators in the first half of 2023 based on the vulnerabilities, malware, and tools used.
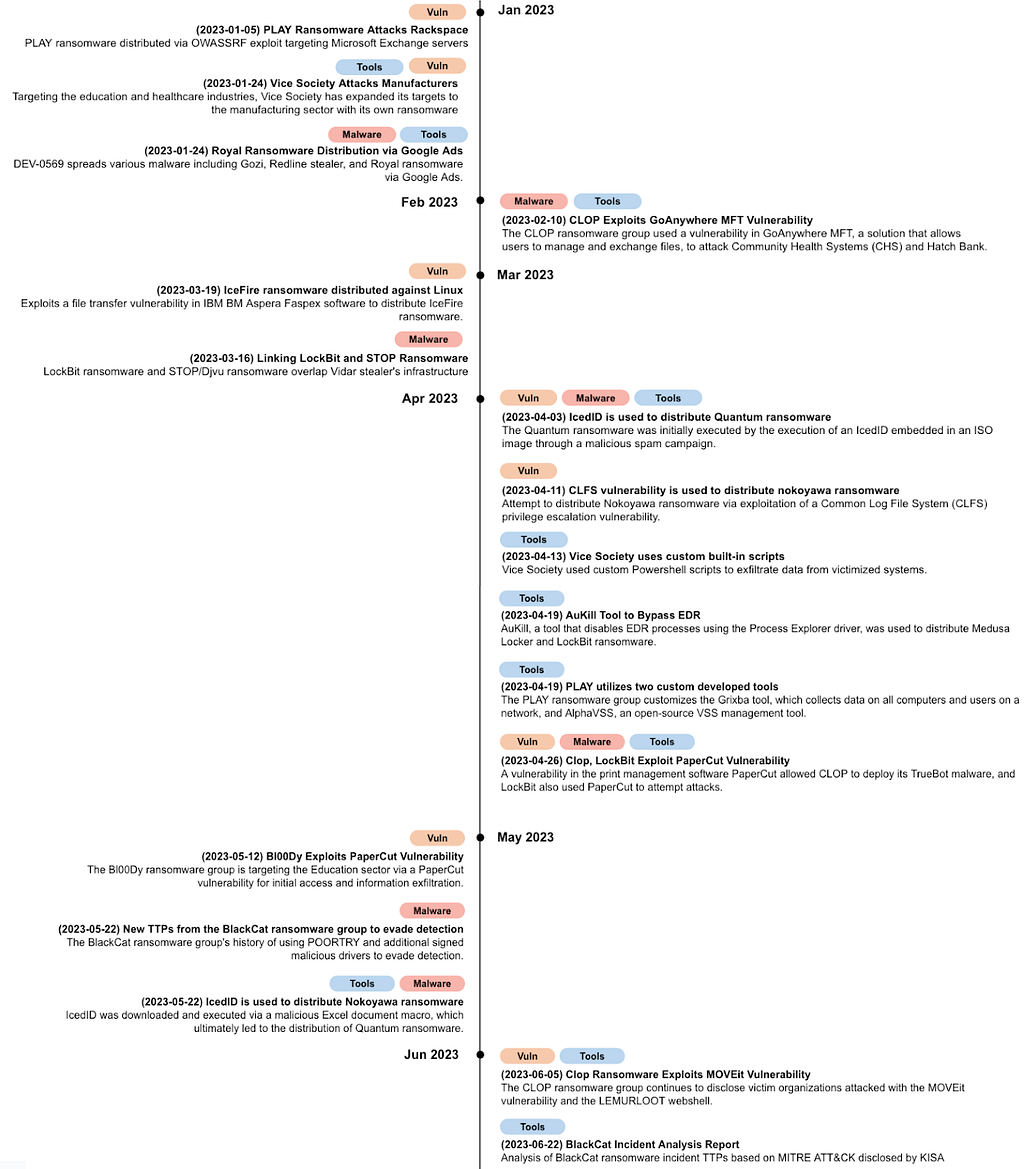 Figure 19. Campaign Timeline
Figure 19. Campaign TimelineIn the above-mentioned attack techniques, RaaS operators used a total of 11 vulnerabilities in their attacks, of which 8 exploited publicly available (1-day) vulnerabilities and 3 exploited 0-day vulnerabilities.
- Among the ransomware groups, CLOP exploited 2 0-day vulnerabilities in H1 2023 and uploaded a number of victimized organizations’ information to its Leak site.
- In addition, the PaperCut vulnerabilities (CVE-2023–27350 and CVE-2023–27351) were used by CLOP, LockBit, and Bl00Dy ransomware groups.
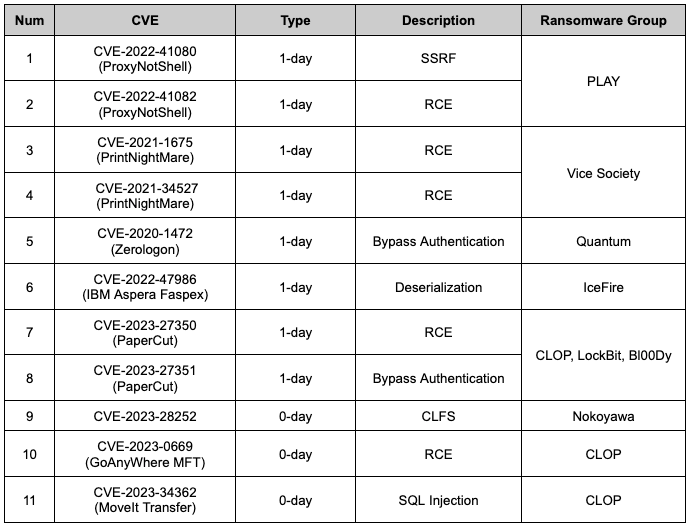 Table 4. List of vulnerabilities used in the campaign
Table 4. List of vulnerabilities used in the campaign3.4. Duplicated Victims
In this report, we conducted additional analysis to identify ransomware groups that uploaded duplicated victims. There are cases where multiple Leak sites disclose victimization of the same organization, which is likely due to the IAB associated with the ransomware group working with multiple groups.
Depending on the nature of the group, different types of Leak sites can be distinguished, and in S2W, each type is classified as either the ‘Leak type’ or the ‘Ransomware type’. In this classification, groups that have affiliations with ransomware groups or just sell initial access without direct involvement in attacks are categorized under the ‘Leak type’. Meanwhile, groups that upload leaked data from organizations by attacking with ransomware are categorized under the ‘Ransomware type’.
- Among the ransomware groups active in H1 2023, Snatch, Karakurt, and Unsafe are the ‘Leak type’.
During H1 2023, there were a total of 27 duplicated victims uploaded to the Leak site, with 21 groups disclosing the data of the same organizations. We found the following correlations between the groups that uploaded duplicated organizations.
- In Figure 20, each ransomware group has a 1:1 relationship.
- The group that uploaded the duplicated victim first on the left side, and the group that uploaded later on the right side.
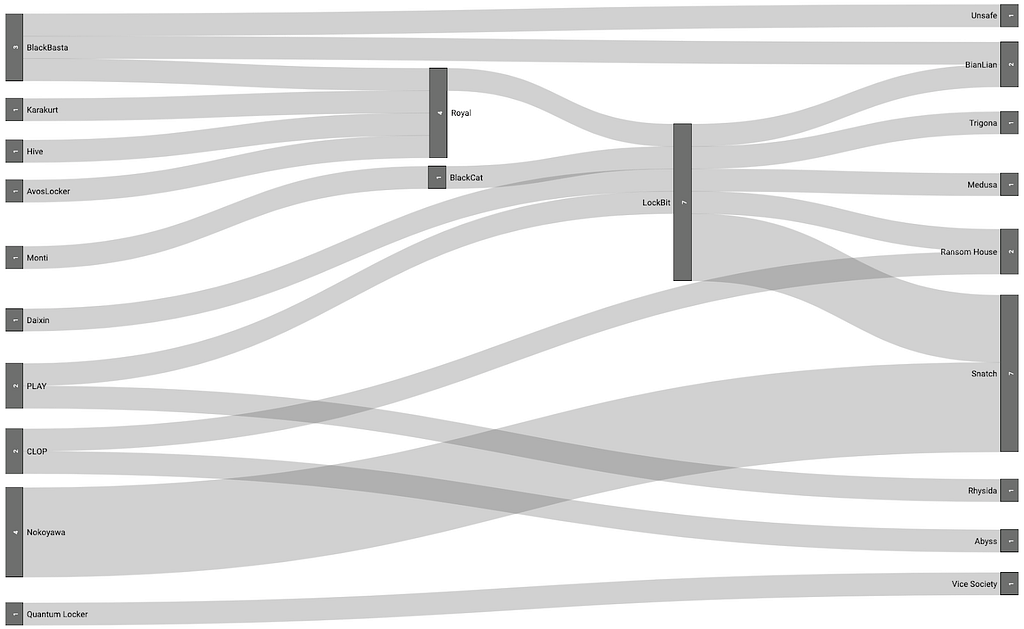 Figure 20. All duplicated victims
Figure 20. All duplicated victims3.4.1. Leak 계열
Among the ransomware groups that uploaded the same victims late in H1 2023, Snatch was the only group in the ‘Leak type’ to upload 7 duplicated victims.
- The Snatch group is known to have used ransomware in the past, but according to comments on their official Telegram channel in December 2021, the Snatch group has stated that they do not use ransomware.
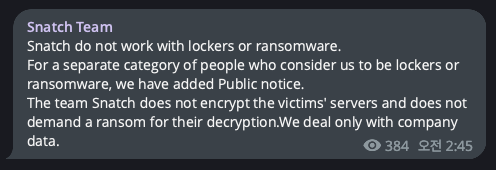
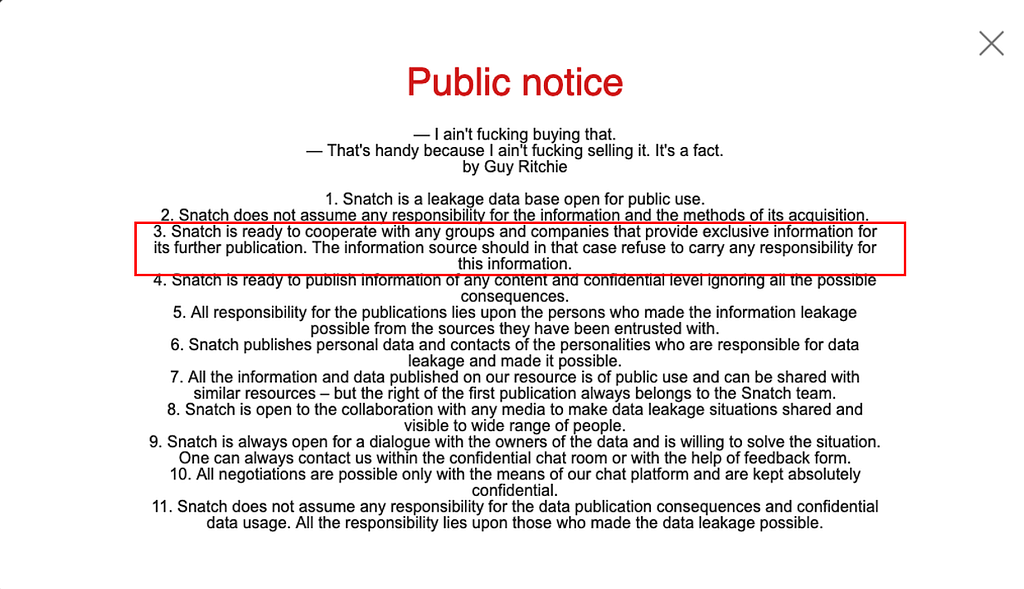 Figure 21. Snatch group’s official Telegram message (Left) / Figure 22. Snatch group’s Leak site announcement (Right)
Figure 21. Snatch group’s official Telegram message (Left) / Figure 22. Snatch group’s Leak site announcement (Right)As shown in Figure 23, the Snatch group collaborated with several affiliates to conduct additional data leaks, presumably resulting in multiple duplicated organizations.
 Figure 23. Duplicated victims across Leak
Figure 23. Duplicated victims across Leak3.4.2. Ransomware 계열
Among the ‘Ransomware type’ that uploaded duplicates late in H1 2023, LockBit and Royal had the most duplicates with 4 each, and LockBit had the most duplicates early with 7.
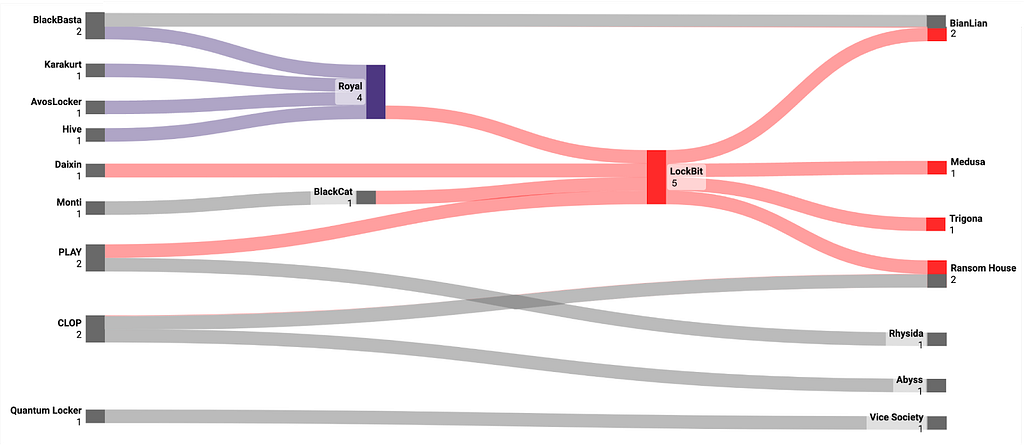 Figure 24. Duplicated victim organizations among ransomware type
Figure 24. Duplicated victim organizations among ransomware typeLockBit’s high number of duplicated victims is likely due to its large number of affiliates, with interviews with vx-underground and LockBit ransomware operators indicating that they have more than 100 affiliates.
- Other groups that have uploaded the same victims as the Royal ransomware group include BlackBasta and Karakurt, both of which are known to be associated with the Conti ransomware, according to Red Sense(Advintel).
- Google TAG disclosures indicate that IABs such as UAC-0098 have provided access data to a variety of ransomware groups, including Conti, leading to speculation that Conti-affiliated ransomware groups may have conducted attacks against the same organizations.
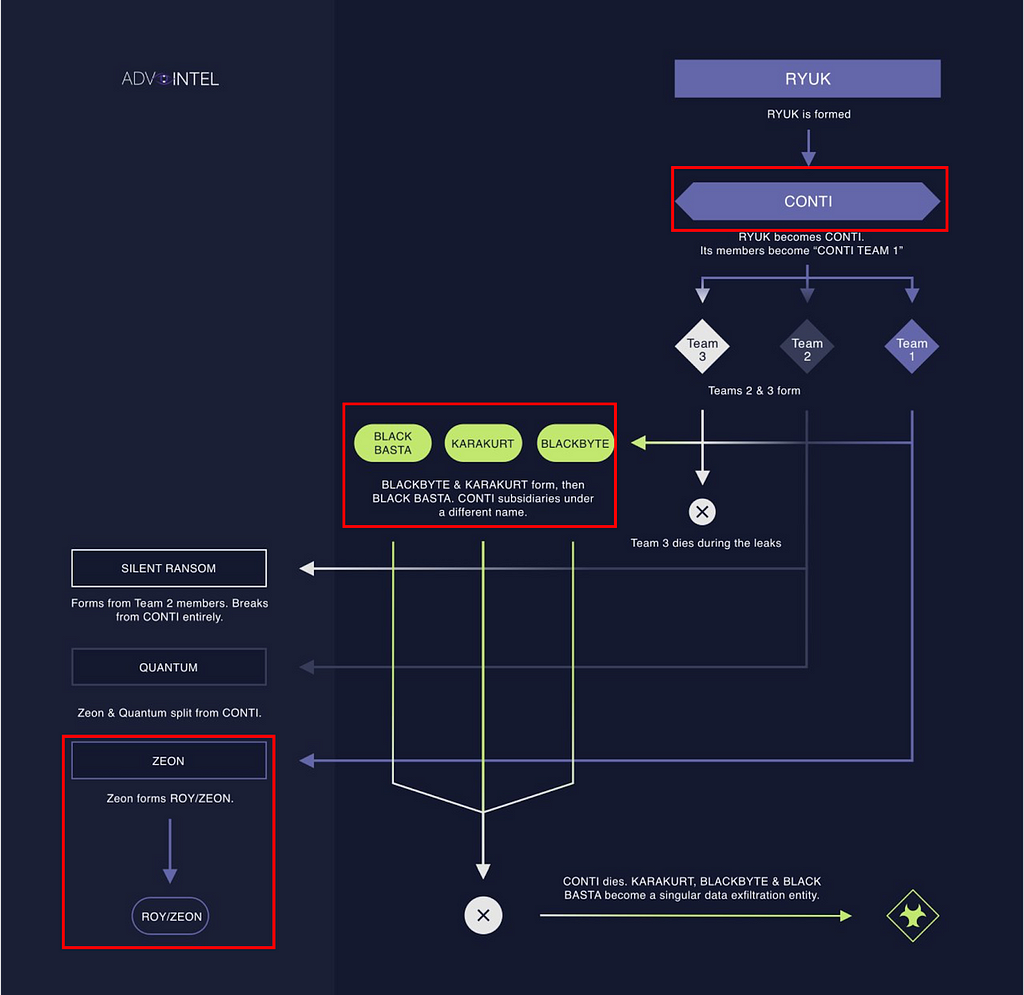 Figure 25. Conti ransomware group structure (Source: @VK_Intel)
Figure 25. Conti ransomware group structure (Source: @VK_Intel)Conclusion
- The first half of 2023 saw a total of 35 new ransomware groups tracked by S2W, and the second half of the year is likely to see a steady stream of new ransomware groups.
- Ransomware groups are increasingly expanding their target operating system including Linux and MacOS, and since Babuk was the only ransomware source code leaked for Linux, many groups have referenced the Babuk source code for Linux versions of their ransomware.
— This may have contributed to the Babuk Family’s dominance among all ransomware families.
- There are a few ransomware groups using similar wording and appearance to leak sites used by existing ransomware groups.
- Analyzing the attack techniques in which the ransomware was used, the CLOP ransomware group exploited the most vulnerabilities in H1 2023, including GoAnywhere MFT, PaperCut, and MOVEit.
- Our analysis of the victim organizations listed on the Leak site shows that victims were infected with multiple ransomware infections during the first half of 2023.
- Upon analyzing the victims appearing on the Leak sites, it has been observed that a significant number of victim organizations were repeatedly mentioned on ransomware Leak sites during H1 2023.
— We believe that many affiliates are collaborating with multiple ransomware groups to provide access data and force initial penetration, which is leading to organizations being uploaded by different ransomware groups.
P.S. We were impressed by the Ransomware map produced by Orange Cyberdefense, and created our own map based on it. We would like to say thank you to them.

- Homepage: https://s2w.inc
- Facebook: https://www.facebook.com/S2WLAB
- Twitter: https://twitter.com/S2W_Official
Story of H1 2023: In-depth Examination of Notable Ransomware Groups and Key Issues (English ver.) was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: Story of H1 2023: In-depth Examination of Notable Ransomware Groups and Key Issues (English ver.) | by S2W | S2W BLOG | Medium