
Overview
Remote Access Tools (RATs), also referenced as Remote Monitoring and Management (RMM) tools, are legitimate software designed to remotely access servers. Typically, these tools are convenient for the commercial users who want to access different devices within one system. Unfortunately, these tools are popular gateways for threat actors to gain access to victim machines. In this report, the following tools are free and have been abused by threat actors: AeroAdmin, MeshCentral, mRemoteNG, UltraVNC, and DWService.
AeroAdmin
AeroAdmin is a free remote desktop tool primarily available in Windows machines. The installation process does not require a login as the local operator would only need a client IP to connect to the machine. Some of the tool capabilities include file transfer, unattended access, and support for simultaneous remote connections to an unlimited number of computers.
 Figure 1.1 — AeroAdmin Welcome Interface
Figure 1.1 — AeroAdmin Welcome InterfaceAeroAdmin Case
eBay Port Scanning (May 2020)
On May 30th, 2020, researchers have found that eBay port scans visiting computers for various remote desktop applications, including AeroAdmin. The port scanner was meant to monitor visitors of remote programs as eBay has had issues with threat actors using the tools to carry out attacks.1 Reports in 2016 stated that the victim’s computers were being taken over by remote access tools to log into eBay accounts and make fraudulent purchases. eBay conducts the local port scan using a ‘check.jd’ script that scans fourteen different TCP ports and the associated programs.[2] The port looks for the following tools: AeroAdmin, Teamviewer, AnyDesk, VNC, etc.
Additionally, AeroAdmin was associated with a malware sandbox. The following are the IOCs[3]:

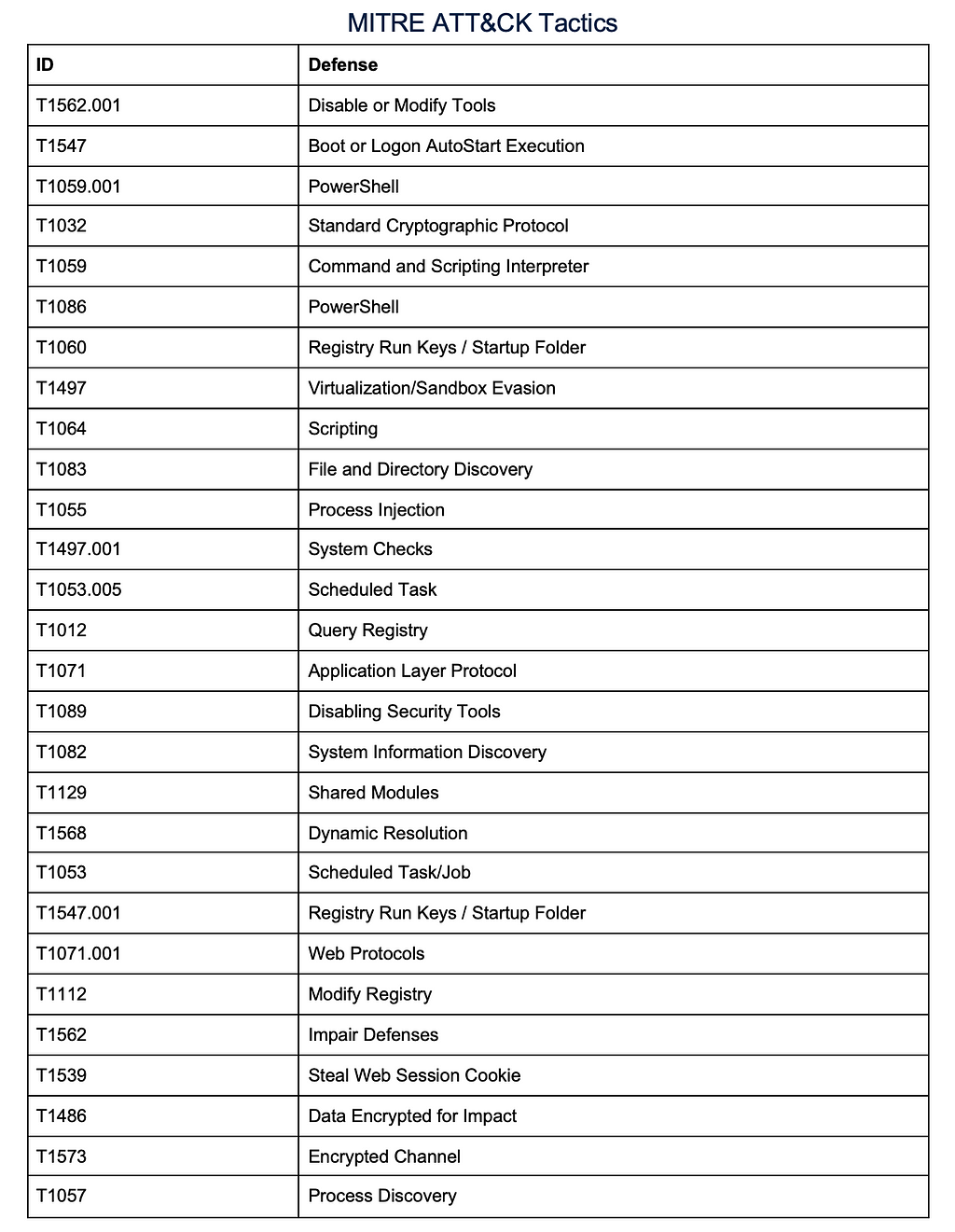
Under normal circumstances, AeroAdmin typically executes these paths:
%SAMPLEPATH%\AeroAdmin.exe
C:\Users\admin\AppData\Local\Temp\AeroAdmin.exe
Verified Signers:
AeroAdmin LLC
GlobalSign GCC R45 EV CodeSigning CA 2020
Associated Files Names:
AeroAdmin.exe
AeroAdmin 4.8.3610_Portable.exe
aao.exe
AeroAdmin PRO - remote desktop.exe
AeroAdmin (26.2.2023).exe
AeroAdmin 4.9.3612.exe
AeroAdmin_2.exe
AeroAdmin-v4_9.exe
AeroAdmin PRO.exe
AeroAdmin_3612.exe
Uzak.exe
1.exe
blah.bin
ar.txt
aero.exe
SOSeEscola.exe
aeroadmin 4.8.3610_portable.exe
Associated Domains:
auth17.aeroadmin[.]com
auth11.aeroadmin[.]com
dev.aeroadmin[.]com
auth1.aeroadmin[.]com
auth13.aeroadmin[.]com
Support.aeroadmin[.]com
auth14.aeroadmin[.]com
ports.aeroadmin[.]com
auth4.aeroadmin[.]com
account77.aeroadmin[.]com
Auth25.aeroadmin[.]com
ports.aeroadmin[.]com
auth4.aeroadmin[.]com
auth19.aeroadmin[.]com
account77.aeroadmin[.]com
auth25.aeroadmin[.]com
auth0.aeroadmin[.]com
auth16.aeroadmin[.]com
auth.aeroadmin[.]com
ssc.aeroadmin[.]com
auth23.aeroadmin[.]com
authoritywww.aeroadmin[.]com
account.aeroadmin[.]com
auth21.aeroadmin[.]com
auth15.aeroadmin[.]com
auth20.aeroadmin[.]com
auth3.aeroadmin[.]com
auth18.aeroadmin[.]com
ulm.aeroadmin[.]com
authorityulm.aeroadmin[.]com
auth12.aeroadmin[.]com
sims.aeroadmin[.]com
download.aeroadmin[.]com
ts.aeroadmin[.]com
auth2.aeroadmin[.]com
Auth10.aeroadmin[.]com
www.aeroadmin[.]com
Associated Registry Keys:
<HKLM>\SYSTEM\ControlSet001\Control\SafeBoot\Network\AeroadminService
<HKLM>\System\CurrentControlSet\Services\AeroadminService
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\CTF\Compatibility\AeroAdmin.exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap
HKEY_LOCAL_MACHINE\SOFTWARE\AeroAdmin
Associated IPs:
131.253.33.203:80
142.250.217.99:80
142.251.211.227:80
142.251.33.67:80
142.251.33.99:80
172.67.214.170:443
188.114.96.0:443
188.114.96.1:443
188.114.97.0:443
188.114.97.3:443
192.168.0.102:138
192.229.211.108:80
20.62.24.77:443
20.99.132.105:443
20.99.133.109:443
20.99.184.37:443
20.99.186.246:443
23.202.223.52:443
23.216.147.64:443
23.216.147.76:443
23.40.197.137:443
37.48.87.53:5665
89.40.115.70:5665
89.40.115.70:8080
93.184.220.29:80
Associated Hashes:
ee54577067550559c4711c9e5e10435807f9deee9a5adb4409cb60a6b0108700
9dcebe8160c0322edb3de8d01f0ede79a722a385a27ed969c5fd9579f1769a14
cdc7b9194e6772353fd2cc142e8e2ca4048c81a3535d9d6fcf48ea50d953085f
10aff0513ad9d844335806dc596c085a8239a41c2e0c31c60ad793984d3acc06
208b46527a4b8333435426c0c71a95b4780fd18e93b67aca9cf8ab028243db1e
b5d190856978a2d655300753489a63eb6616faf556bf8d51a1b08e4ec48013fc
37aeff3c927bfa6ce53d45334475045684cc0288120d1e17454519b54c4515f7
MeshCentral
MeshCentral is a RMM tool that can be used primarily on a web browser. Users also have the option to install agents to remote desktop devices on the local network or over the internet. MeshCentral is not only an open source free to use tool, it is available across multiple platforms including Windows, Linux and macOS.
MeshCentral Case
SparkRAT Malware (May 2023)[5]
On May 26th, 2023, threat actors were able to distribute a malware called SparkRAT on a well-known Chinese VPN site and control users’ machines with the MeshCentral software. Initially, the actors attack the site by replacing the VPN installation file with one that includes the SparkRAT malware package. When victims download the file, it will install the following: VPNSetup.exe (legitimate VPN Installer), stat.exe (downloader file), services.exe (SparkRAT), update.exe (dropper file), and go-memexec-3198337413.exe (MeshAgent Remote Admin).
SparkRAT, written in GoLang, delivers a powershell command that installs and executes MeshAgent in the background without the user’s knowledge (as shown Figure 2.1). Once the MeshAgent is installed, it connects to a remote-control page to register as an agent. Thus, threat actors gain control over the device registered on the public MeshCentral server.
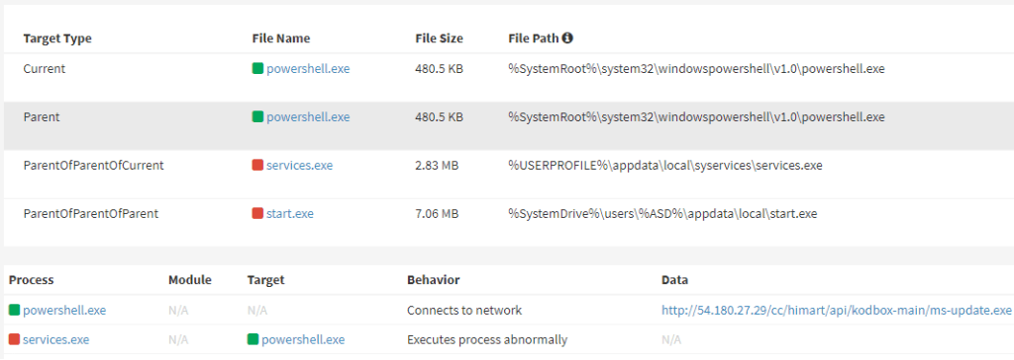 Figure 2.1 — SparkRAT installing MeshAgent[5]
Figure 2.1 — SparkRAT installing MeshAgent[5]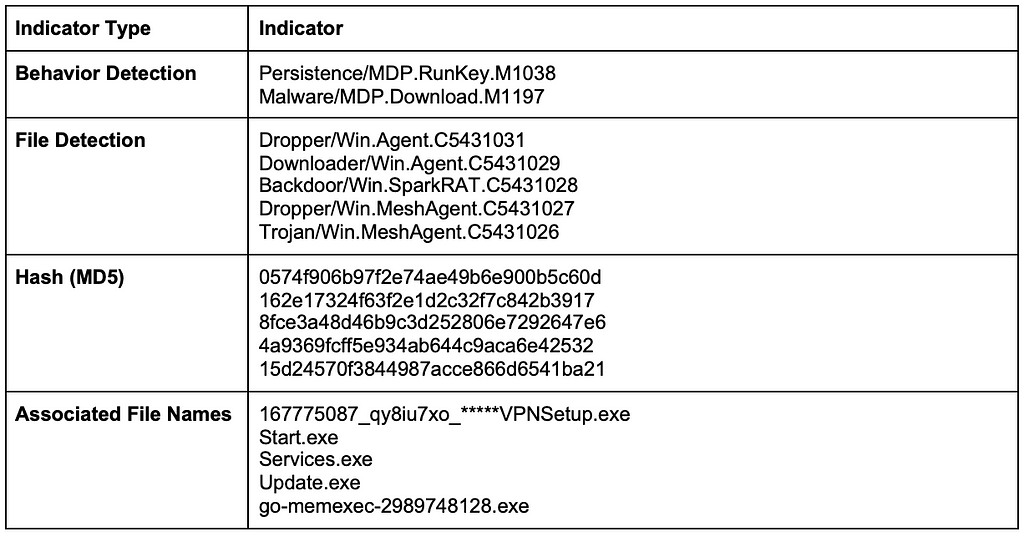 SparkRAT IOCs[5]
SparkRAT IOCs[5]Under normal circumstances, MeshCentral typically executes these paths:
\meshcmd.exe
Verified Signers:
meshcentral[.]com-94d5d0
MeshCentralRoot-89fe49
Associated Files Names:
meshagents
Meshcmd.exe
Meshcmd64.exe
Associated Domains:
meshcentral[.]com
altrelay3.meshcentral[.]com
relay2.meshcentral[.]com
relay3.meshcentral[.]com
relay1.meshcentral[.]com
altrelay1.meshcentral[.]com
e.meshcentral[.]com
mail.meshcentral[.]com
pop.meshcentral[.]com
ftp.meshcentral[.]com
amt.meshcentral[.]com
Associated Registry Keys:
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\meshcmd.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\meshcmd.exe
Associated IPs:
54.200.250.157
20.112.22.5
52.32.58.254
45.40.130.41
72.167.218.173
173.201.192.133
97.74.135.143
68.178.252.117
173.201.192.129
173.201.193.129
97.74.135.10
34.219.197.154
52.43.128.180
Associated Hash:
5c3c0926238a91fdc64cd2696887551d0a7b799b3e8f1eee678b15df6c1821f8
mRemoteNG
mRemoteNG is primarily a Windows tool that supports multi-protocol remote connections. The platform allows for multiple remote connection within one interface and supports the following protocols[7]:
● Remote Desktop protocol (RDP)
● VNC (Virtual Network Computing)
● SSH (Secure Shell)
● Telnet (TELecommunication NETwork)
● HTTP/HTTPS (Hypertext Transfer Protocol)
● rlogin (Remote Login)
● Raw Socket Connections
● Powershell Remoting
Currently, there are three versions of the installation (Stable, Preview, Nightly) with Stable being the most complete package (as shown in Figure 3.1).
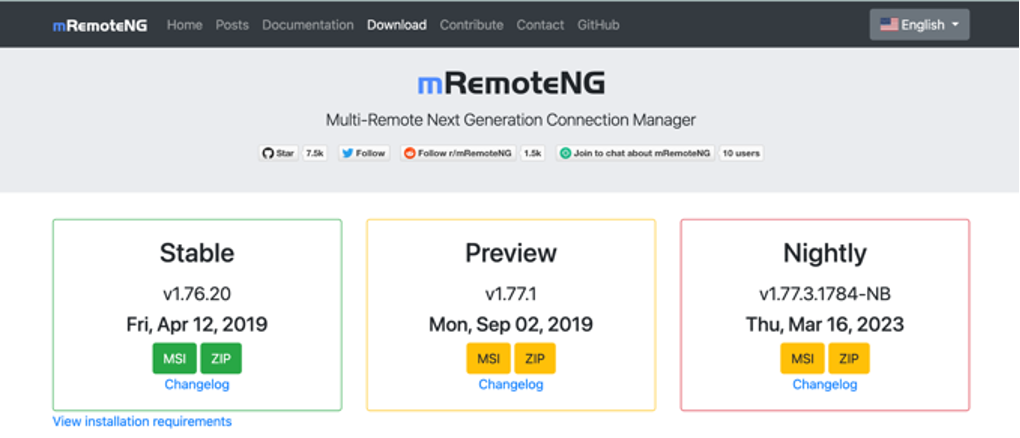 Figure 3.1 — mRemoteNG Website
Figure 3.1 — mRemoteNG WebsiteCVE Vulnerability[8]
In early 2023, researchers discovered a vulnerability with mRemoteNG v1.76.20 that granted modification permission to any authenticated user. The CVE report (CVE-2020–24307) labeled this type of vulnerability as a privilege escalation.
Under normal circumstances, mRemoteNG typically executes these paths:
“C:\Users\admin\AppData\Local\Temp\mRemoteNG.exe”
Verified Signers:
David Sparer
DigiCert SHA2 Assured ID Code Signing CA
Associated Files Names:
mRemoteNG.exe
mRemoteNG-Portable-1.76.20.24669.zip
mRemoteNG_1.76.20.24669.zip
mRemoteNG-Portable-1.76.20.24669-RSLOAD.NET-.zip
mRemoteNG-Portable-1.77.1.27713.zip
Portable.-.1.77.3.NB.rar
is-6D69C.tmp
mRemoteNGPrivat.exe
ss.exe
ogyxoaw.tmp
tjnbegv.tmp
udpdxcw.tmp
mremoteng.exe
mRemoteNG-Installer-1.69.exe
mRemoteNG-win-1.69.exe
mRemote_Update.exe
Associated Domains:
mremoteng.org
Associated Registry Keys:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mRemoteNG.exe
Associated IPs:
172.67.163.80
104.42.151.234:443
104.86.182.8:443
114.114.114.114:53
117.18.237.29:80
13.107.4.50:80
13.107.4.52:80
192.229.211.108:80
20.62.24.77:443
20.80.129.13:443
20.99.132.105:443
20.99.133.109:443
20.99.184.37:443
20.99.185.48:443
20.99.186.246:443
23.216.147.64:443
23.216.147.76:443
23.223.246.81:443
23.40.197.137:443
23.40.197.184:443
40.81.188.85:123
52.251.79.25:443
Associated Hashes:
9476fe1896669163248747785fa053aca7284949945abd37c59dae4184760d58
7542a1b2e0f78f6a738daf4ec6cce84256eee3610722ef7c451e72b10401b589
97b0e94bbdc409f3eb09b1017b3b58ccc0eae145a98a3bc6ea651ef1d5bc2d8e
49ca9646e42123f0258caf547b29577b1b24ab9e3effe1b8df6ba250d7ed0de0
0b7b711241d5a15fba168a623f19a9d431dc062134cbf612b8f749511aa60758
2fc824c78bc5686a4a05242e8fd512cc0e8af30ad994dc45d617e4e810eed03c
1bfdd4997388c0caa7b49862d764510421a48c7e072872e69d495ad2d4977c03
UltraVNC
UltraVNC is a popular tool supported on Windows and Linux operating systems. The tool has been featured in multiple use cases with threat actors utilizing the tool for malicious activities.
UltraVNC Cases
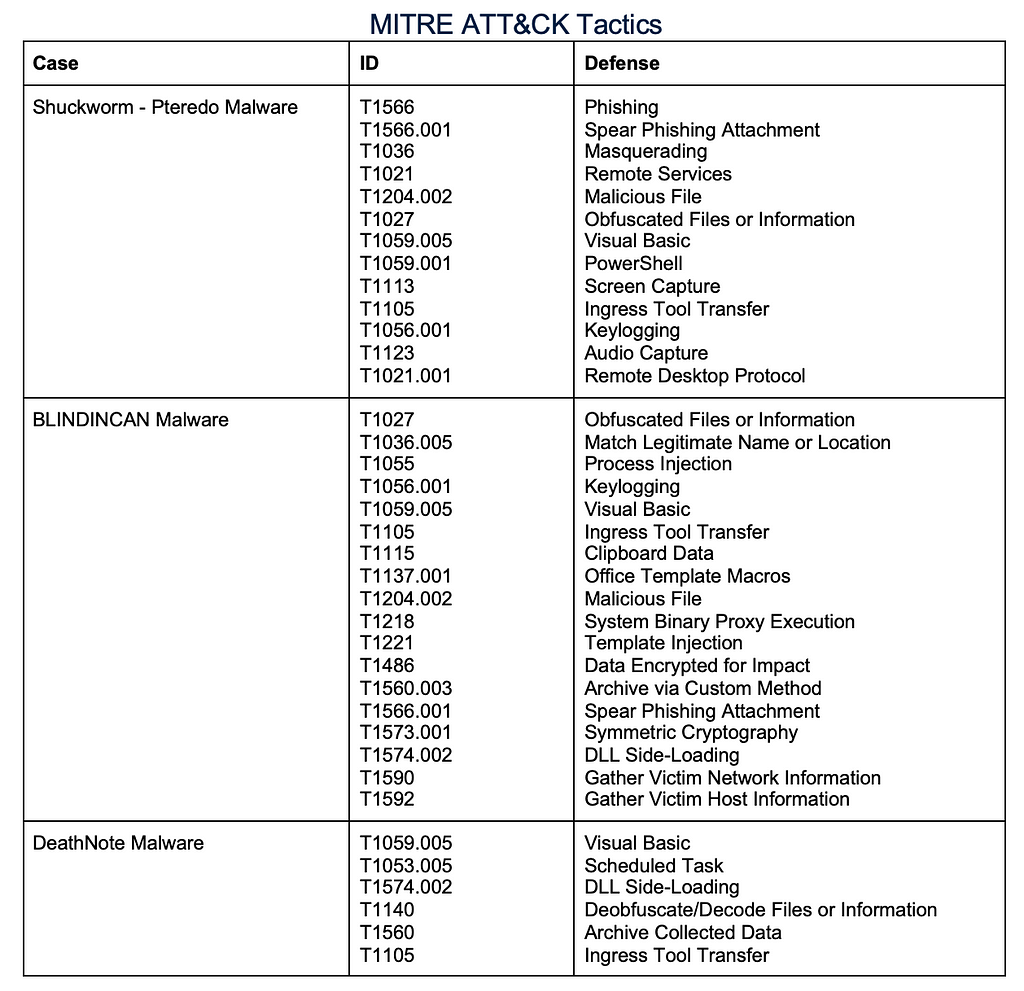
Siamesekitten Threat Group (2021)[10] & Shuckworm Threat Group (2022)[11]
In August 2021, the Iranian Siamesekitten threat group utilized their DanBot malware to create a malicious version of UltraVNC to target victims. Additionally, in April 2022, Russian state threat actors, Shuckworm, abused the tool when deploying their Pteredo backdoor malware.
Lazarus Threat Group: BLINDINCAN (January 2023)[12] & DeathNote Malware[13] (April 2023)
In January 2023, researchers at Kaspersky reported the Lazarus threat group leveraging UltraVNC to deploy the BLINDINCAN malware payload to victim machines. When downloaded, the software operates as normal, however, data is exfiltrated in the background without the victim’s knowledge. While the data is exfiltrated, it is transmitted to the C2 servers. Analysis of the campaign suggested that BLINDINCAN was deployed against various organizations including telecommunications companies in Pakistan and Bulgaria and real estate sectors in India. Similarly, the Lazarus threat actor group used the same technique when deploying the DeathNote malware to victim machines. The threat actors utilize UltraVNC as a mask to hide the trojanized application as it executes.
Under normal circumstances, UltraVNC typically executes these paths:
C:\Program Files\uvnc bvba\UltraVNC\winvnc.exe
Verified Signers:
uvnc bvba
Sectigo Public Code Signing CA R36
Associated Files Names:
WinVNC.exe
is-LDHPV.tmp
is-8GB2E.tmp
is-7L4SG.tmp
7cd339f9be1417421acf8790c9738922_c25eff4d9d2d5b55f1cc4ffc623354004565e8b9_winvnc.exe
1.4.2.0_original_original.exe
1.4.2.0.exe
is-N32MV.tmp
Associated Domains:
Uvnc[.]com
www.sponsor4.uvnc[.]com
support2.uvnc[.]com
sc.uvnc[.]com
support.uvnc[.]com
sponsor2.uvnc[.]com
beta.uvnc[.]com
cloud.uvnc[.]com
sponsor4.uvnc[.]com
doc.uvnc[.]com
sponsor5.uvnc[.]com
support2.uvnc[.]com
sc.uvnc[.]com
support.uvnc[.]com
sponsor2.uvnc[.]com
beta.uvnc[.]com
cloud.uvnc[.]com
www.uvnc[.]com
Sponsor4.uvnc[.]com
doc.uvnc[.]com
Sponsor5.uvnc[.]com
t0www.uvnc[.]com
sponsor.uvnc[.]com
hostwww.uvnc[.]com
forum.uvnc[.]com
mail.uvnc[.]com
support1.uvnc[.]com
_.uvnc[.]com
Associated Registry Keys:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\CTF\Compatibility\winvnc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winvnc.exe
Associated Hashes:
ec0ec7ce8ef71cb7e7d1c2418c47ad94cea8833db8578ccdf94271f8efed38d3
36a31b37b98f70c1db0428f5ad83170d604fb352
DWService
Similar to some of the other tools, DWService can be used to remotely access different systems directly from the web browser. Alternatively, the tool also supports a variety of operating systems apart from Windows as shown in Figure 4.1 below:
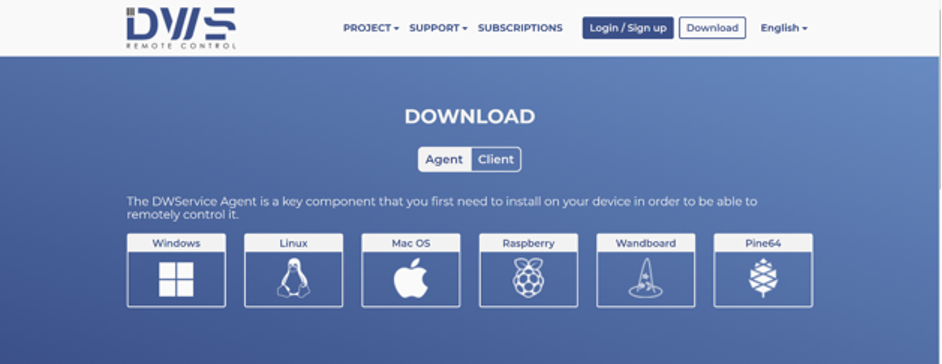 Figure 4.1 — DWService Website
Figure 4.1 — DWService WebsiteDWService Case
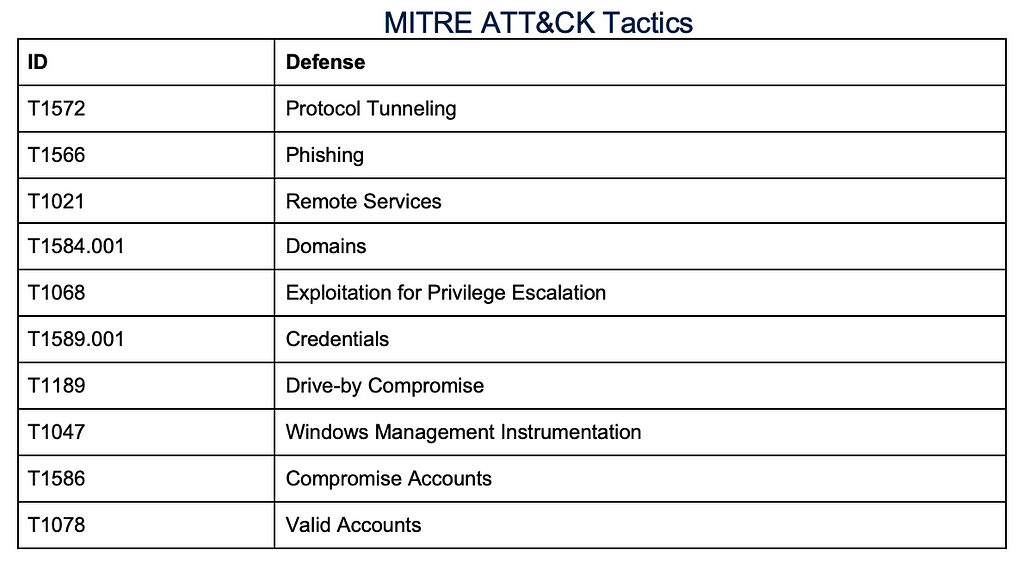
Scattered Spider (December 2022)[15]
Another use case stems from a December 2022 report detecting threat actors accessing corporate networks via social engineering tactics. The threat actor, ‘Scattered Spider’, would impersonate IT staff and contact employees directly to harvest their credentials and gather multi-factor authentication codes if prompted. Researchers noticed that the Scattered Spider actors installed a number of RMM tools, one of which being DWService. As a result, threat actors were able to extract various types of reconnaissance.
Under normal circumstances, DWService typically executes these paths:
\dwagent.exe
%USERPROFILE%\AppData\Local\Temp\dwagent20230508155627\runtime\dwagent.exe
%USERPROFILE%\AppData\Local\Temp\50350bce3908539a15a51d661a698e52937348f18fffbfa525dc8baa8031522020230518113922\runtime\dwagent.exe
C:\DOCUME~1<USER>~1\LOCALS~1\Temp\50350bce3908539a15a51d661a698e52937348f18fffbfa525dc8baa8031522020230510200338\runtime\dwagent.exe
C:\DOCUME~1<USER>~1\LOCALS~1\Temp\50350bce3908539a15a51d661a698e52937348f18fffbfa525dc8baa8031522020230510200338\runtime\dwagent.exe" -S -m installer"
Verified Signers:
DWSNET srl
Sectigo
Associated Files Names:
dwagent.exe
getAgentFile.dw
Dwagent.sh
dwagent.dmg
Dwagsvc.exe
Dwm.exe
ra_setup_20200322.exe
Associated Domains:
dwservice.net
Associated Registry Key:
HKU\S-1-5-21-4270068108-2931534202-3907561125-1001\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts.exe\OpenWithProgids\exefile
Associated IPs:
116.203.208.186:443
147.135.78.236:443
178.63.42.248:80
212.7.200.218:443
239.255.102.18:50001
51.178.59.252:137
51.178.59.252:443
85.10.192.135:443
85.195.107.63:80
192.229.211.108:80
20.99.133.109:443
20.99.184.37:443
20.99.186.246:443
23.216.147.64:443
104.76.210.84:443
184.25.164.177:443
255.255.255.255:67
67.195.204.56:443
20.80.129.13:443
20.99.132.105:443
23.35.98.25:443
Associated Hashes:
72548408e4be88e18188fc424405134a9ea56b690ed1b24f62d52c783eaca670
50350bce3908539a15a51d661a698e52937348f18fffbfa525dc8baa80315220
e11e0e90f6142204c1213c179c830245015c88c5636505a71e3962e788f18f90
a3bac548b5bc91c526b4d6707623ddbd1a675aa952f0d1f9a0aa6f7230f09f23
Referenced Reports
5. https://asec.ahnlab.com/en/53267/
8. https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-24307
9. https://github.com/login-securite/DonPAPI
10. https://heimdalsecurity.com/blog/iranian-threat-actor-siamesekitten-spies-on-israeli-organizations/
12. https://malware.news/t/apt-trends-report-q1-2023/69035
13. https://securelist.com/the-lazarus-group-deathnote-campaign/109490/
State of the Remote Access Tools, Part 2 was originally published in Walmart Global Tech Blog on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: https://medium.com/walmartglobaltech/state-of-the-remote-access-tools-part-2-6e290ca7261b?source=rss----905ea2b3d4d1---4