With contribution from Denise Dasom Kim, Jungyeon Lim, Yeonghyeon Jeong, Sujin Lim | S2W LAB Talon

Reborn or Burned
SoW (Story of the Week) publishes a report summarizing ransomware’s activity on the Darkweb. The report includes summary of victimized firms, Top 5 targeted countries and industrial sectors, status of dark web forum posts by ransomware operators, etc.
Executive Summary
- [Statistics] During the month of July, 151 companies were found to have been damaged by ransomware. Of these, the United States accounted for 38%, and the most active ransomware group was LockBit 2.0, which accounted for 36.7% of the total activity
- [Cryptocurrency] As a result of tracking the wallet address of LockBit 2.0, it is estimated that the funds paid by the victim company were transferred to the wallet address of Binance
- [Dark Web] Ragnarok ransomware is back, 8 new victims found so far
- [Dark Web] RAMP changed to the private forum and Babuk appeared New Leak site
- [Dark Web] Is BlackMatter a rebrand of Darkside? Or is it a rebrand of REvil?
1. Monthly Status
- From July 1, 2021 to July 27, 2021, 150 victims were identified through ransomware leak sites, and 18 ransomware groups that disclosed victims were identified
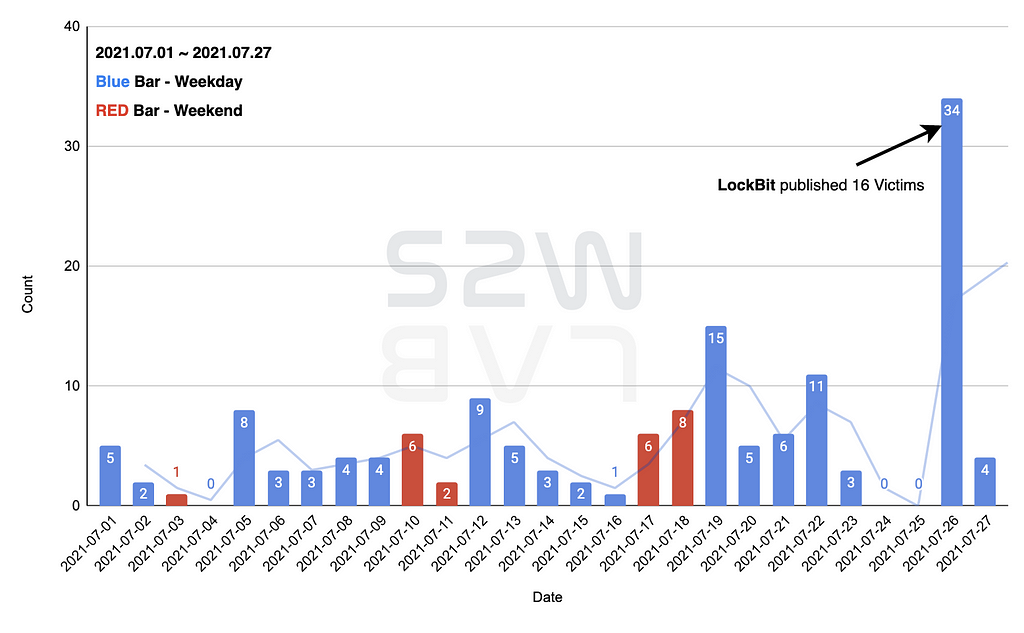
1.1. Status of the infected companies (07/01~07/27)
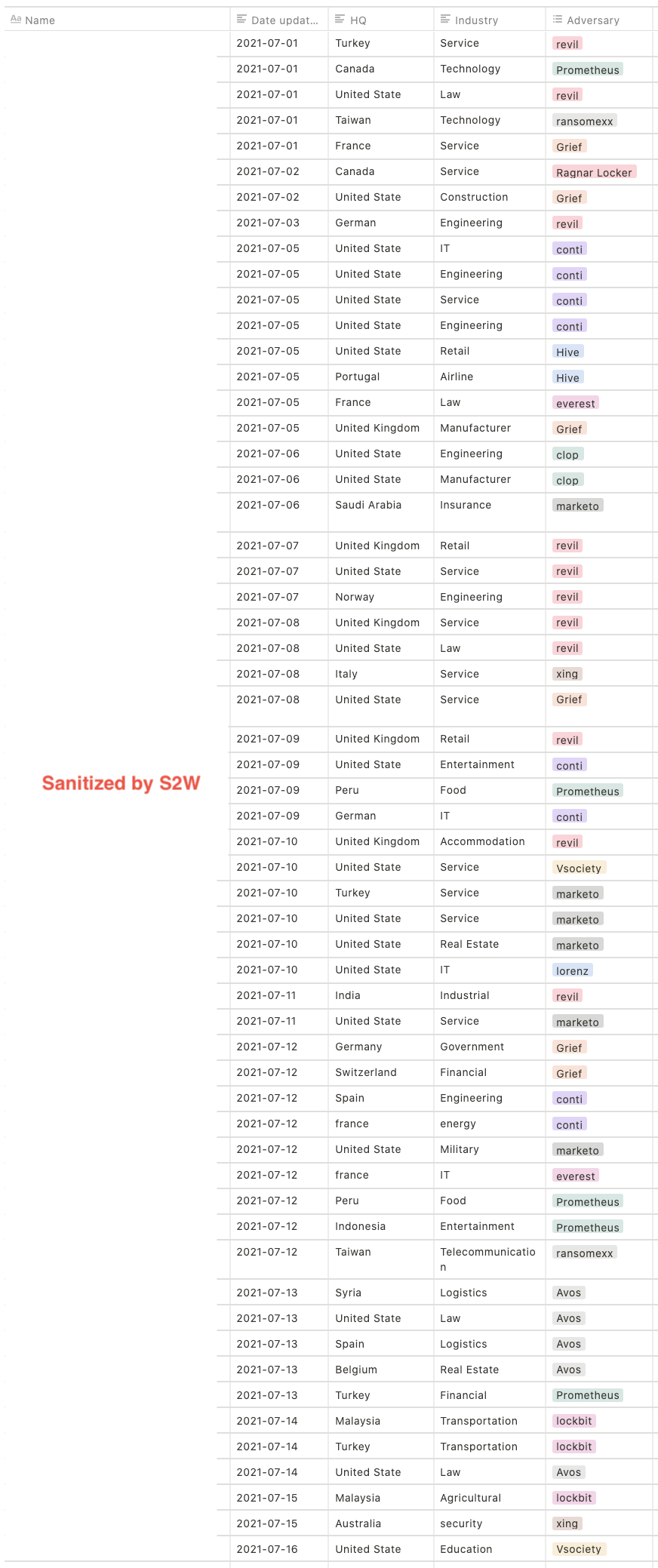
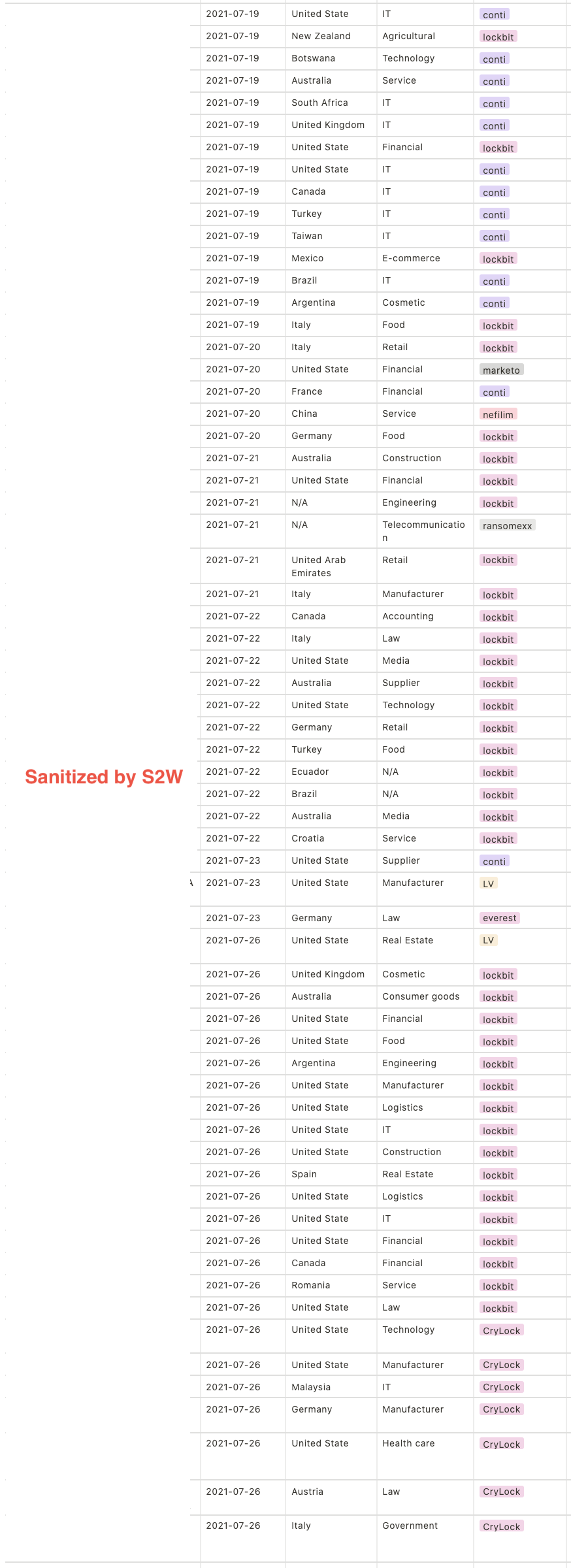
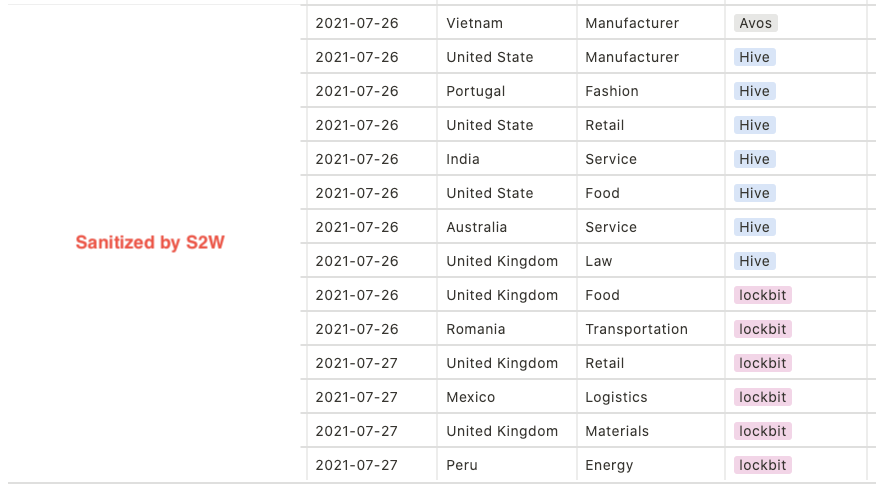
1.2. TOP 5 targeted countries
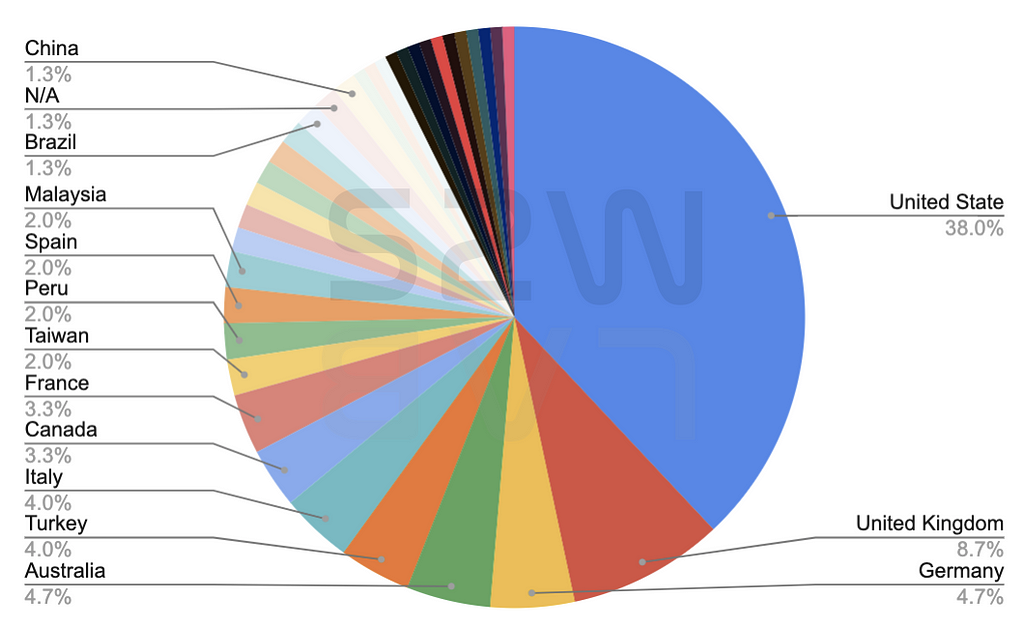
- United States — 38.0%
- United Kingdom — 8.7%
- Germany & Australia — 4.7%
- Turkey & Italy — 4.0%
- Canada & France — 3.3%
1.3. TOP 5 targeted industrial sectors
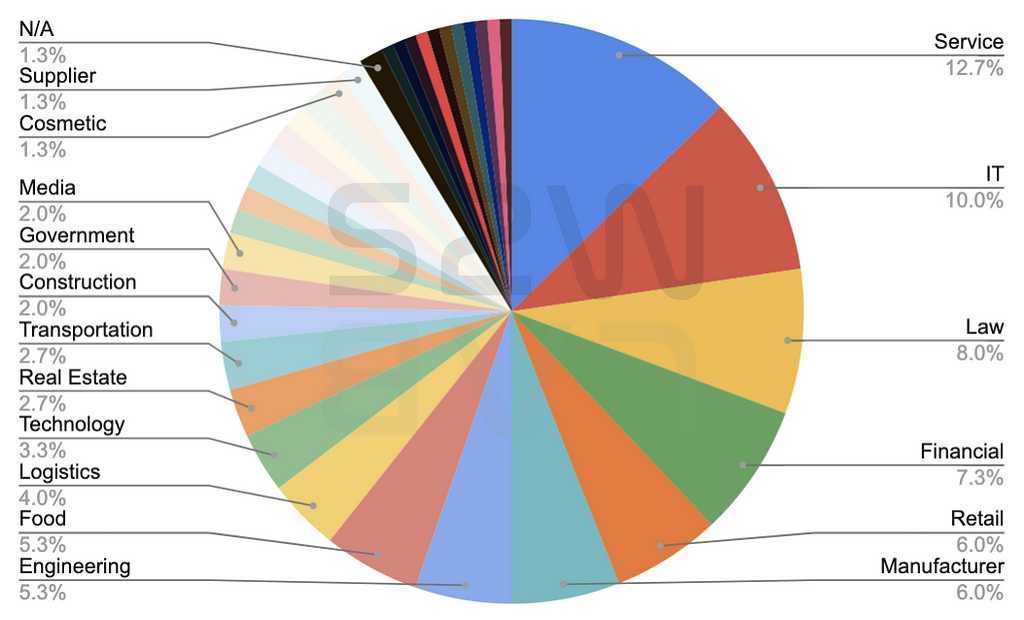
- Service — 12.7%
- IT — 10.0%
- Law — 8.0%
- Financial — 7.3%
- Retail & Manufacturer — 6.0%
1.4. Top 5 Ransomware
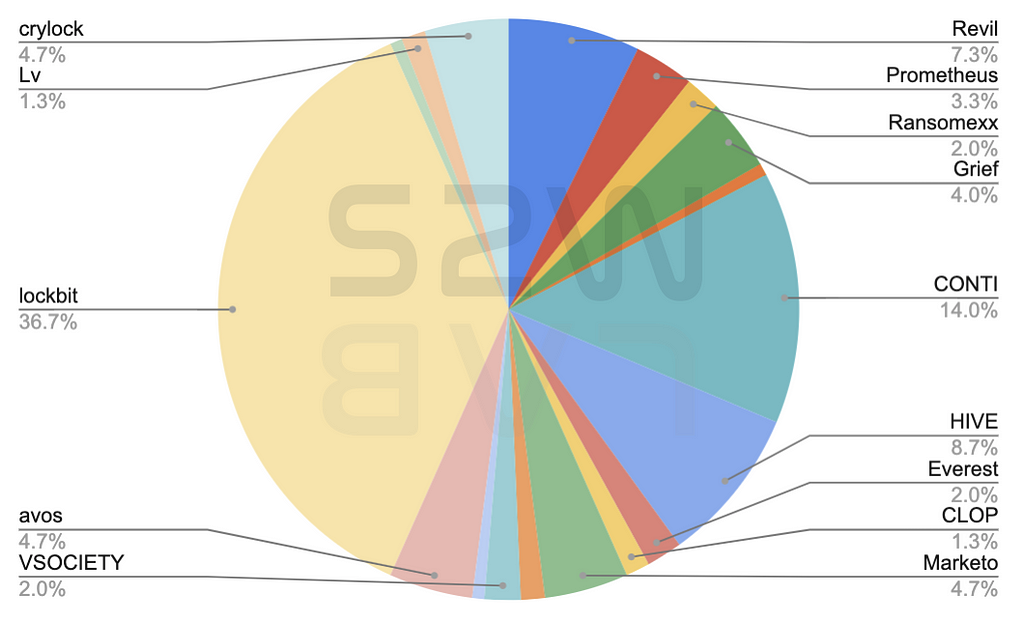
- lockbit — 36.7%
- CONTI — 14.3%
- HIVE — 8.7%
- Revil — 7.3%
- crylock & avos & Marketo — 4.7%
2. Posts related to Ransomware threat actors @Dark Web
2.1. Case study of Victim infected by LockBit 2.0
- LockBit 2.0 operating 2 contact sites for negotiation with victims
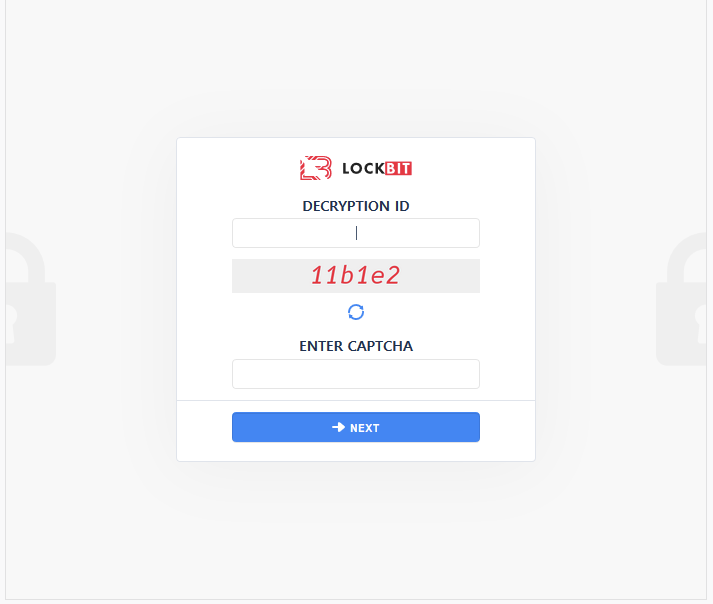
- When Victim was infected by LockBit 2.0, Ransomware created Ransom note on Victim’s PC as below
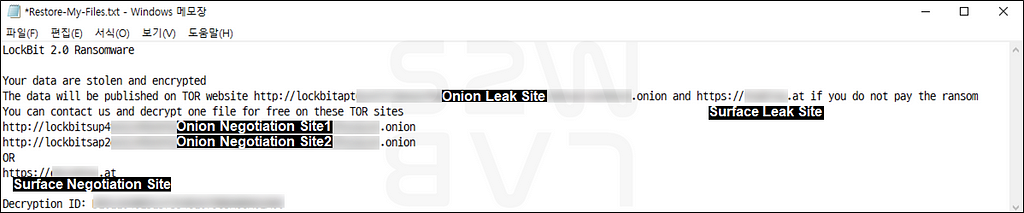
- In Ransom note, a different Decryption ID value is created for each victim, and through this value, the chat page is accessed and 1:1 negotiations are continued
2.1.1. Tracing the transaction to Bitcoin wallet address of LockBit 2.0
- Confirmed the Bitcoin deposit address through the chat history of the ransomware-infected victim and the LockBit 2.0 operator
- LockBit 2.0 asked the victim to deposit bitcoin to the address below
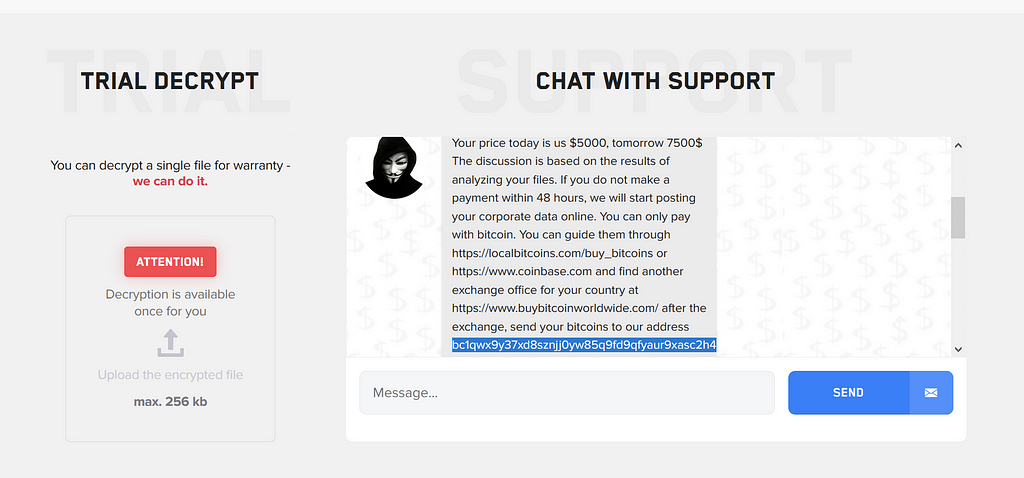
Victim finally pays 0.24993 BTC after negotiation.
- Payment Address : bc1qwx9y37xd8sznjj0yw85q9fd9qfyaur9xasc2h4
- Transaction date : 2021–07–29 02:17
- Amounts : 0.24993
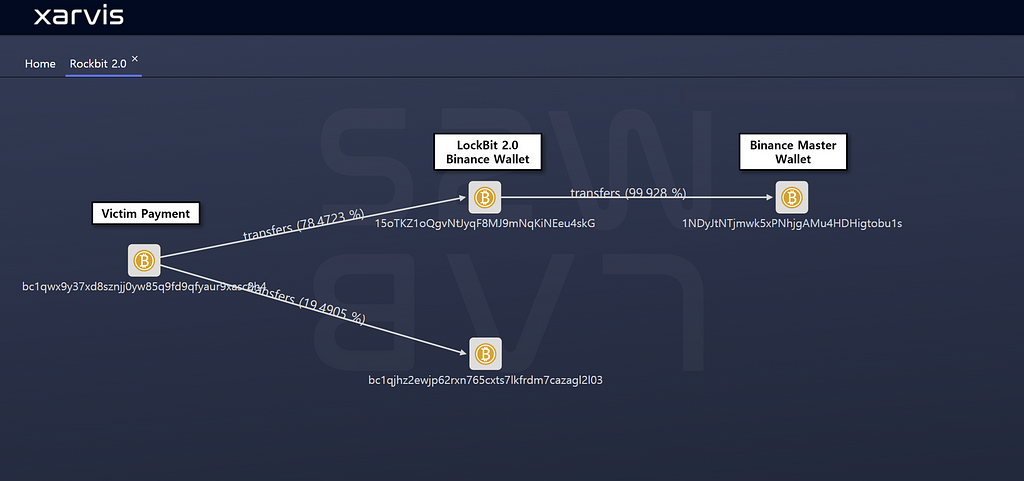
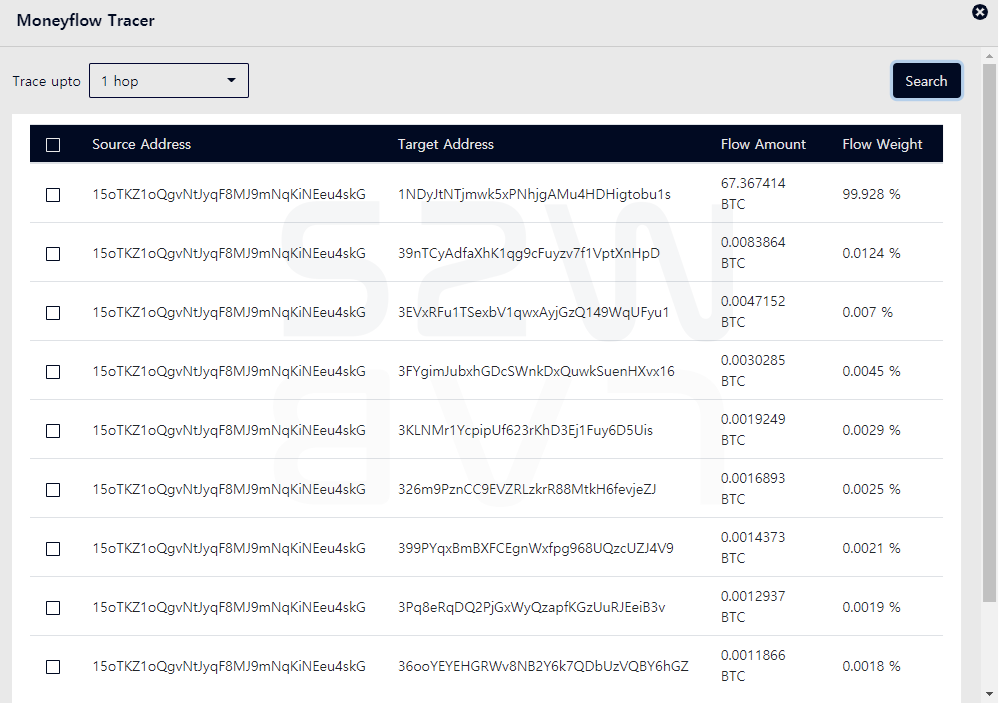
LockBit 2.0 who confirmed the deposit sent about 78% of 0.1798 BTC to the address below
- Bitcoin Address : 15oTKZ1oQgvNtJyqF8MJ9mNqKiNEeu4skG
- Transaction date : 2021–07–29 05:01
- Amounts : 0.1798
Since 99% of the amount in the account is transferred to the Binance Master Wallet, it is assumed that it is a Binance personal wallet owned by LockBit 2.0
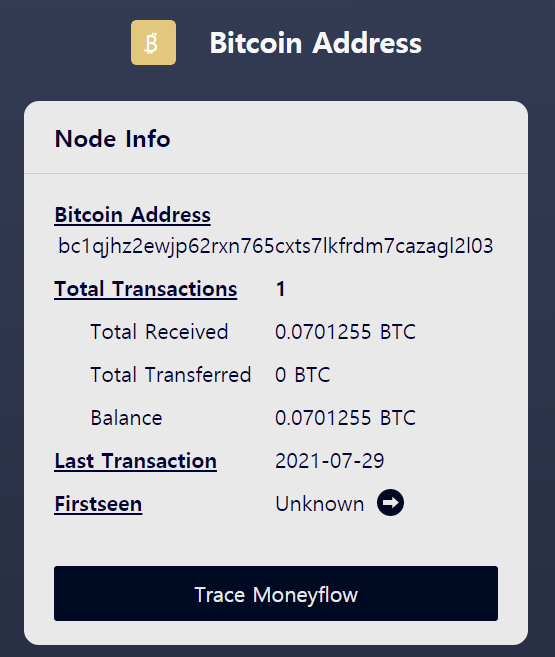
2.1.2. LockBit 2.0 Bitcoin address requiring continuous monitoring
The remaining 0.07012553 BTC, which is about 19%, has not changed since it moved to the address below
It seems that Bitcoin address needs to be monitored
- Bitcoin Address : bc1qjhz2ewjp62rxn765cxts7lkfrdm7cazagl2l03
- Transaction date : 2021–07–29 05:01
- Amounts : 0.07 BTC
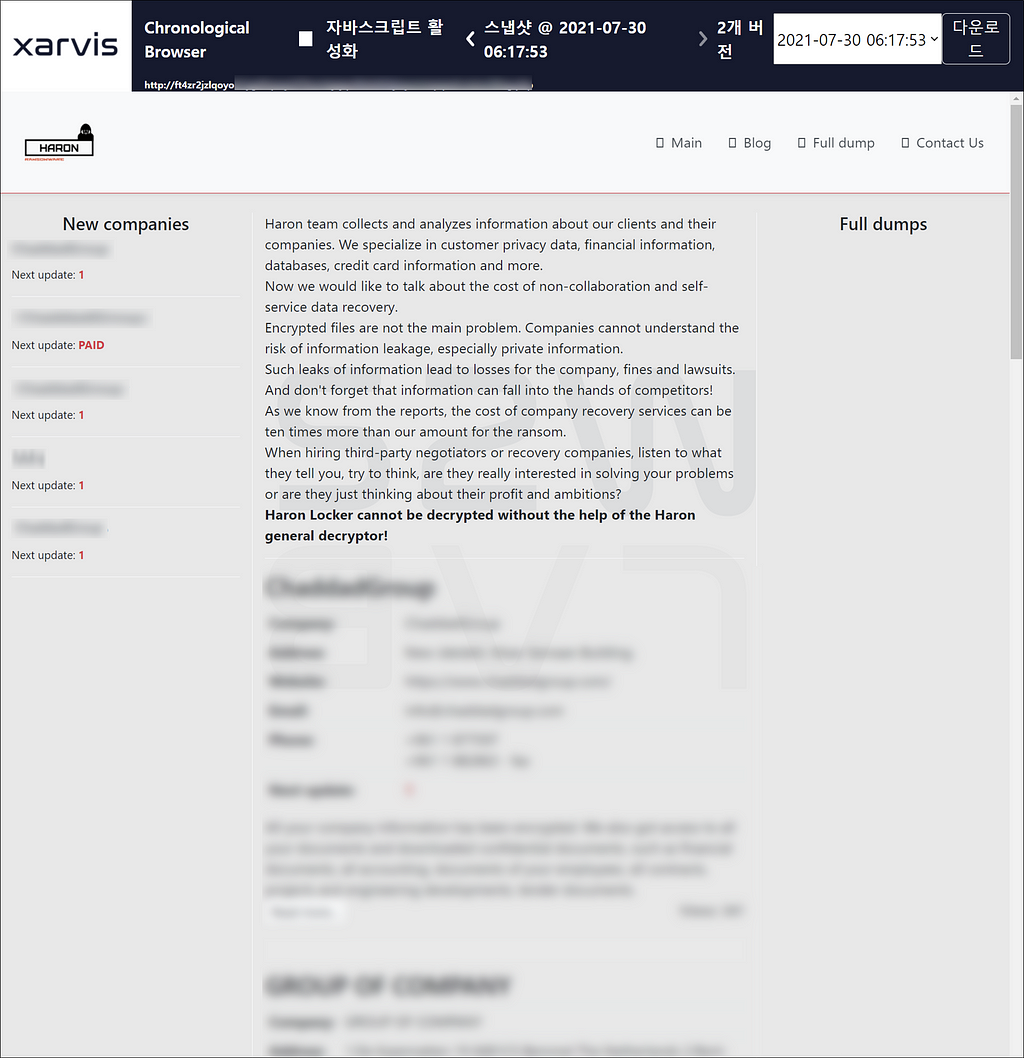
2.2. Haron Ransomware published New victims on a private blog
- Haron, which has a lot of issues about its relationship with Avaddon, is currently continuously updating the affected company
- However, unlike Avaddon, where large-scale victims accounted for a large proportion, most of the small-scale victims suffered damage from Haron
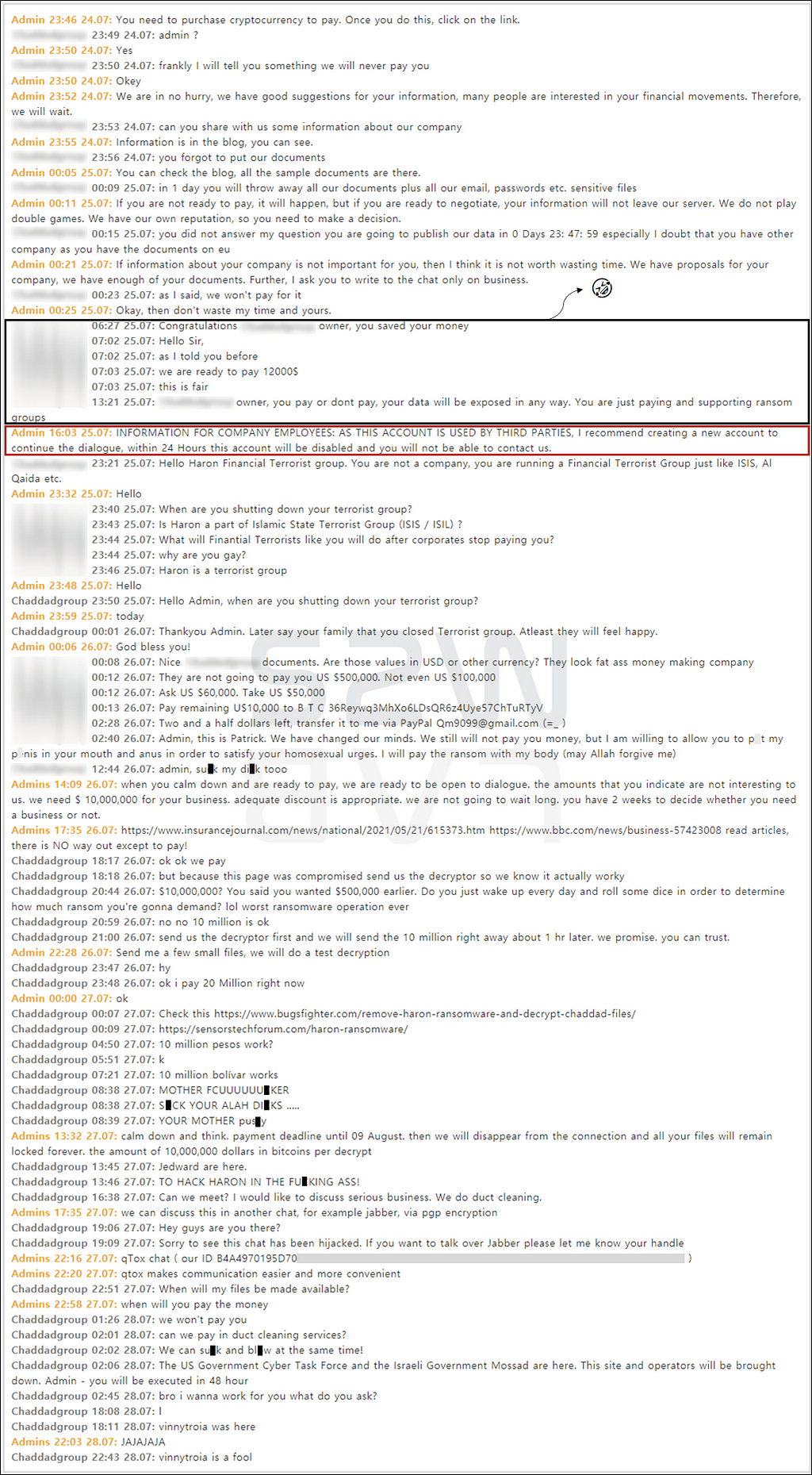
2.1.1. Contact site for infected companies by Haron
- Someone broke into the chat while talking with the first victim company. Someone advises the victim that Haron will disclose the data whether you pay them or not, only helping the ransomware group
- In the end, Haron recommended creating a new account because a third party was involved in the negotiating account
2.2.2. Comparison with Suncrypt
- However, the chat window in which Someone or more has intervened still loses its function as a negotiation page, with profanity and obstruction of negotiations.
- Suncrypt ransomware, which was discussed in the last SoW W4, has a very different appearance from the professional business appearance.
- In case of Suncrypt Ransomware, even after-sales service is provided (Ref. W4 July | KO | Story of the week: Ransomware on the Darkweb)
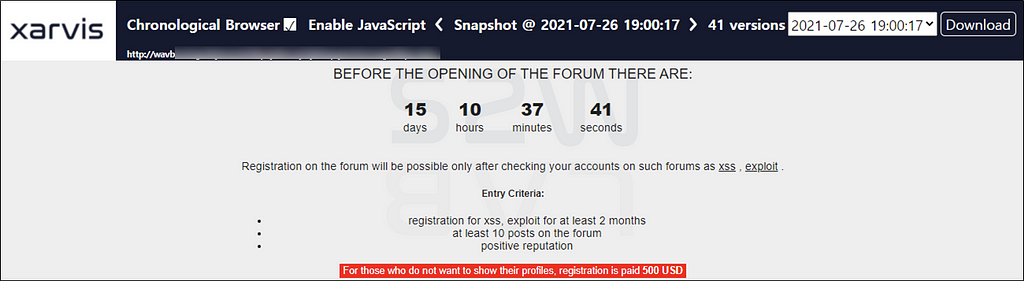
2.3. RAMP changed to the private forum and Babuk appeared New Leak site
2.3.1. After someone uploaded spam posts on the forum, RAMP changed the private forum
- RAMP (Babuk) forum has withdrawn members who are presumed to be bots due to spam posts and has stopped new members
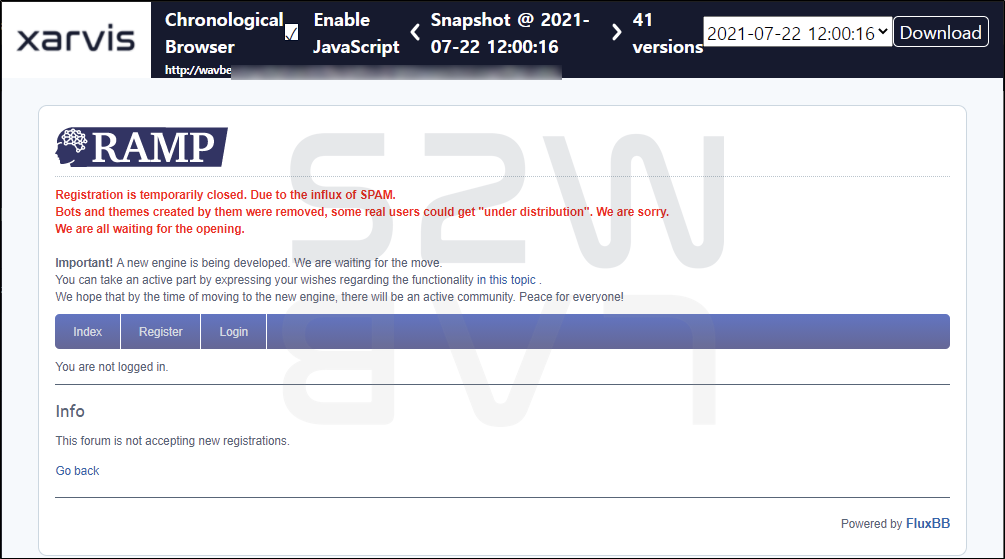
- After going through this situation, the forum was changed to a closed state. In the future, as a condition for membership registration, only users who have more than a certain amount of activity in the hacking forums XSS and Exploit will be accepted
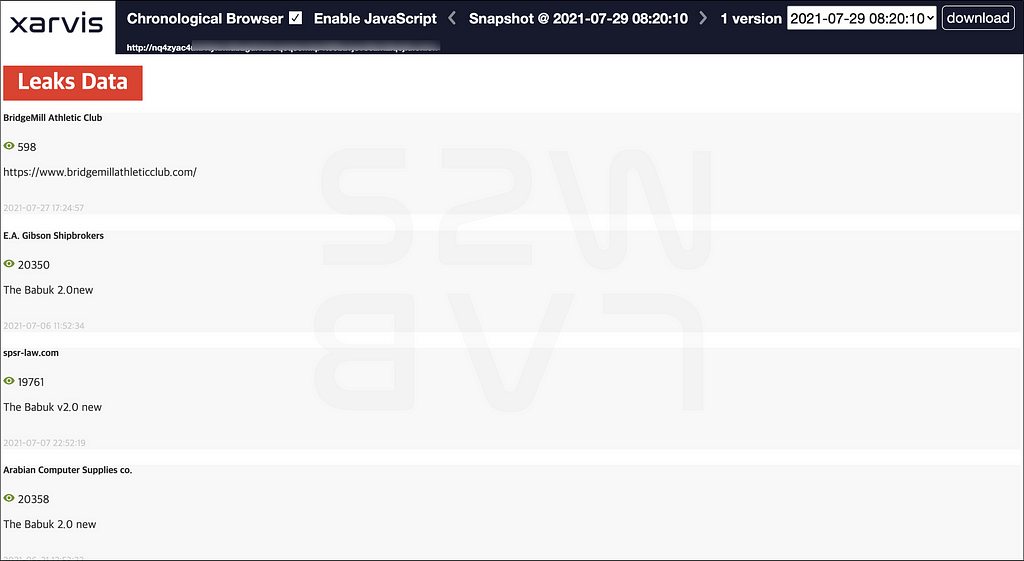
2.3.2. Babuk appeared New Leak site
- A new domain was opened instead of the domain used by Babuk
- So far, information on 6 victims has been posted
2.4. Ragnarok is come back!
- In the Leak site of the existing Ragnarok ransomware, the victim company was updated until April, 2021
- A new Ragnarok Leak Site was discovered on July, 2021 after inactivity for a while after the last victim company update
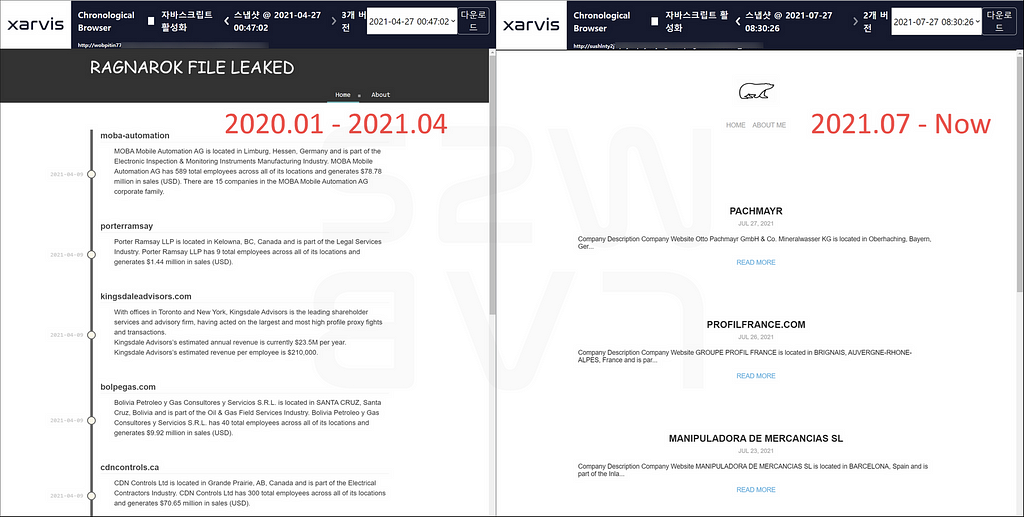
- The UI of the new ransomware Leak site has been simplified overall, but the basic framework has not changed much
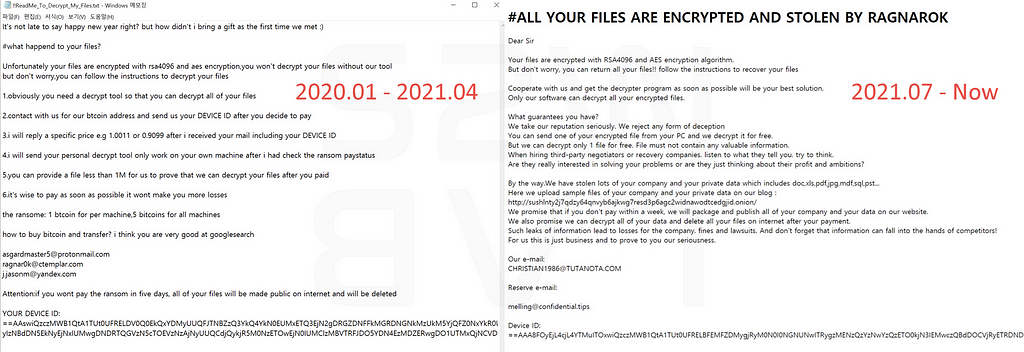
In the case of Ransom noted, which is generated by the Ragnarok malware, the text and form have slightly changed from before, but you can see the sentence “#ALL YOUR FILES ARE ENCRYPTED AND STOLEN BY RAGNAROK”
- In addition, detailed negotiations such as payment of damages are still being conducted through email without a separate chat page
- Malware : 65c3956288e16bdcc55e3c9c6b94ba5b
- Contact mail : [email protected]
Returning Ragnarok, after the first victim update on July 9, it has already updated 8 victims this month alone, and it seems that new victims will continue to occur in the future
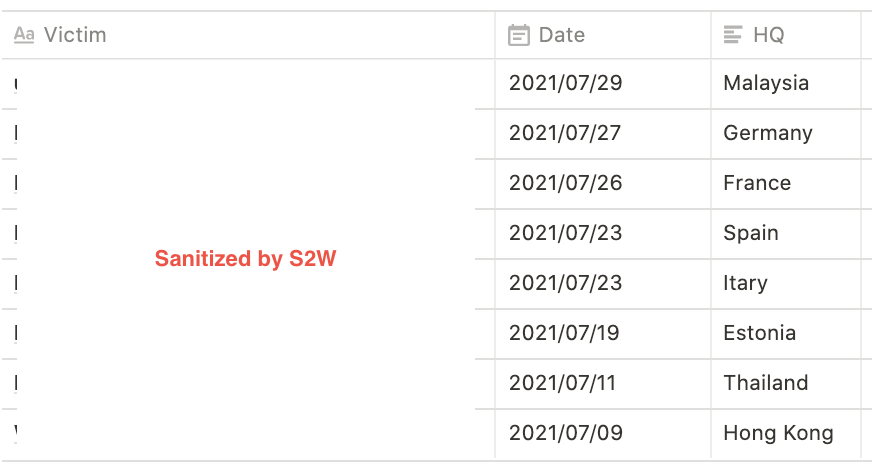
2.4.1. Infected Victim List(2021.07 ~)
2.5. Is BlackMatter a rebrand of Darkside? Or is it a rebrand of REvil?
- Recorded Future mentions that BlackMatter is related to DarkSide (Ref. https://www.recordedfuture.com/blackmatter-ransomware-successor-darkside-revil/)
- Confirmed that BlackMatter is currently recruiting people to collaborate on the Russian forum
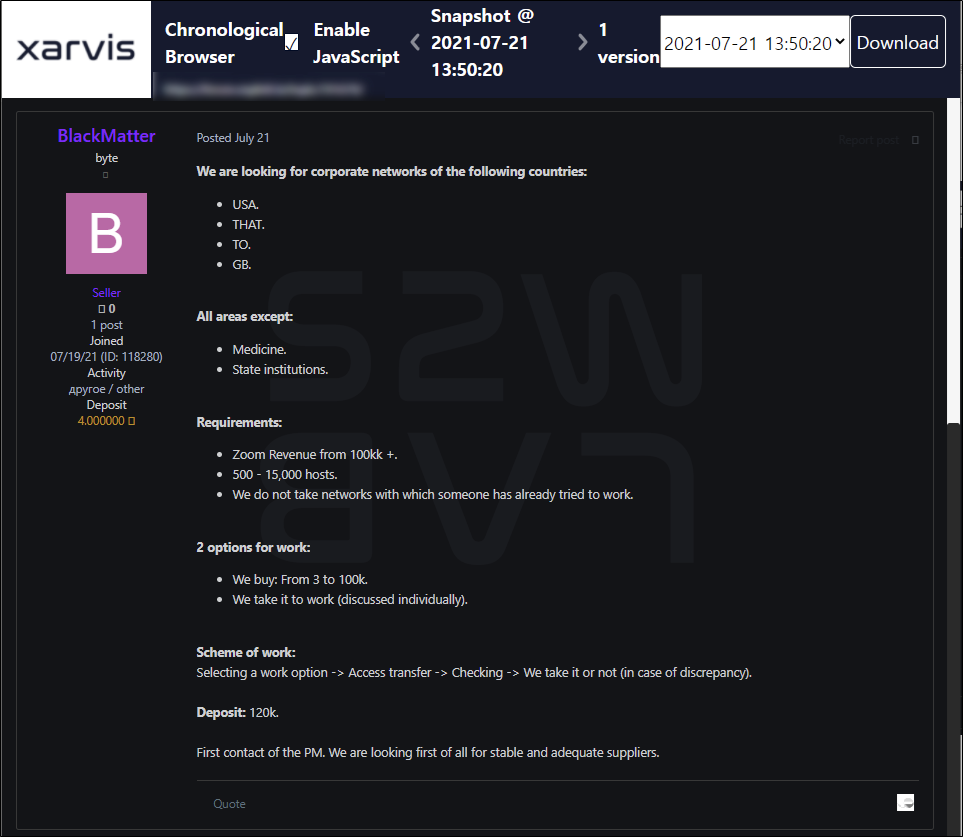
- With BlackMatter posted New corporate network, discussions on the relationship between BlackMatter and Darkside were active in deep web forums
- Mentioned the feature that Darkside’s website and BlackMatter’s website are similar, and there were also claims that Text and Template are similar
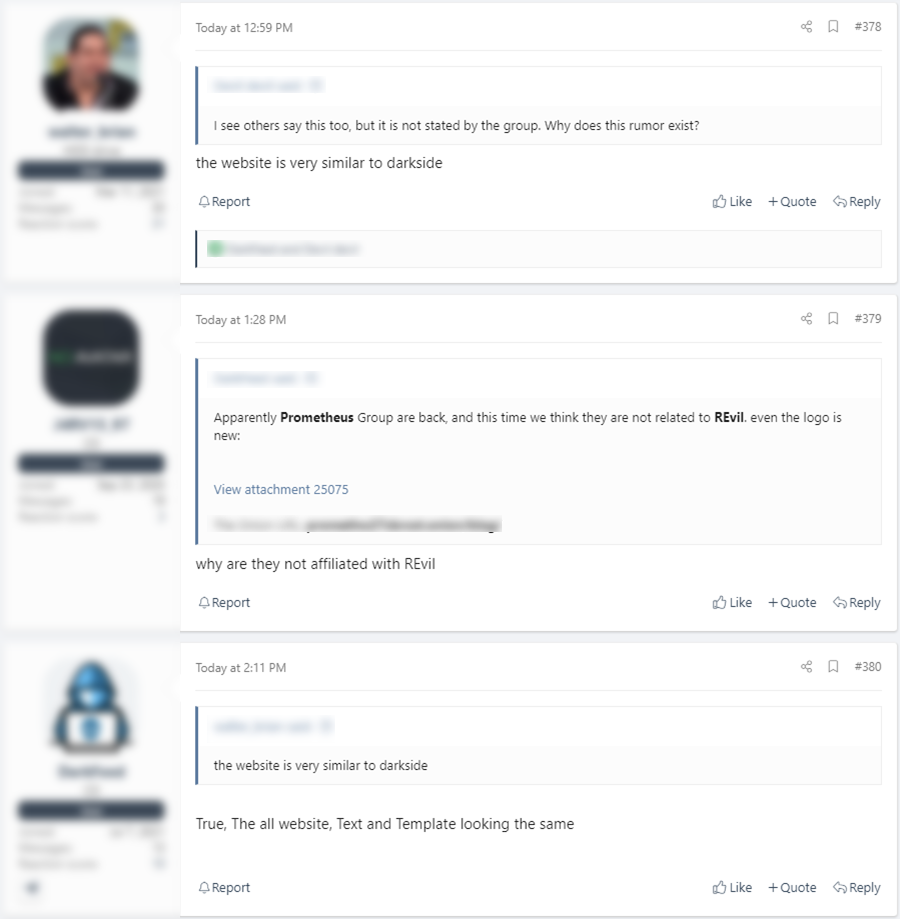
- There is talk of a connection with other ransomware groups by comparing Affiliate recruitment posts or UI comparisons, but there is no clear evidence yet
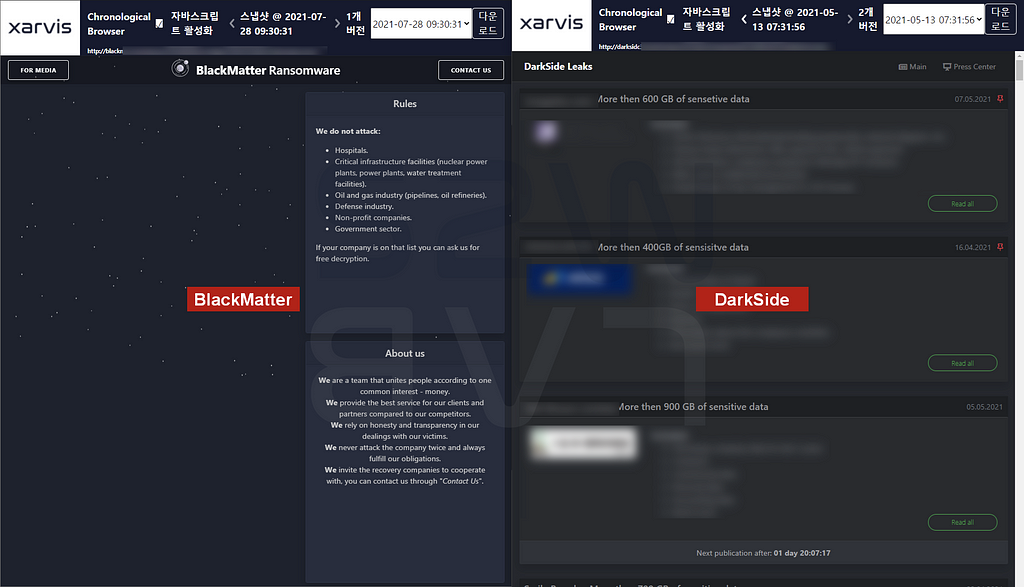
- When comparing the BlackMatter and Darkside websites collected on Xarvis, no characteristic similarity was seen except for certain strings in the Affiliate recruitment
Conclusion
- [Bitcoin Monitoring] It is necessary to continuously monitor the Bitcoin address of LockBit 2.0
- [Forum monitoring] RAMP forum monitoring because RAMP changed the policy to only approve users who are active in the XSS. XSS forum also needs to be monitored for
- [Attack Prediction] Ragnarok ransomware, which has been inactive for about 3 months, is expected to show vigorous activity for a while as it has returned.
- [Attack Prediction] With the advent of the newly appeared BlackMatter Ransomware, rumors of a rebranding of Darkside and REvil are circulating, and since samples or ransom notes have not yet been released, it is necessary to keep monitoring on BlackMatter’s activity in the forum

- Homepage: https://www.s2wlab.com
- Facebook: https://www.facebook.com/S2WLAB/
- Twitter: https://twitter.com/s2wlab
[SoW] W5 July | EN | Story of the week: Ransomware on the Darkweb was originally published in S2W LAB BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: [SoW] W5 July | EN | Story of the week: Ransomware on the Darkweb | by S2W | S2W BLOG | Medium