With contribution from Denise Dasom Kim, Jungyeon Lim, Yeonghyeon Jeong, Sujin Lim, Chaewon Moon | S2W TALON

THREE HEADED RANSOMWARE
SoW (Story of the Week) publishes a report summarizing ransomware’s activity on the Darkweb. The report includes summary of victimized firms, Top 5 targeted countries and industrial sectors, status of dark web forum posts by ransomware operators, etc.
Executive Summary
- [Statistics] For 2 weeks from July 28 to August 9, 140 companies were found that were affected by ransomware, of which 45.4% were from the United States, and the most active ransomware group was confirmed with LockBit 2.0 accounted for 49%
- [Dark Web] Separated Payloadbin and RAMP from Babuk
- [Dark Web] El_Cometa and Payloadbin mentioned the information of the same victim
- [Dark Web] AvosLocker and CryLock being active in various forums
- [Cryptocurrency] AvosLocker traced the bitcoins received from the victim and confirmed that the funds were transferred to Binance after money laundering
1. Weekly Status
- A total of 140 victim companies were mentioned on the ransomware leak site based on 17 attack groups that had been updated in the last two weeks
- The U.S. is the most cited HQ of ransomware victims, accounting for 45.4% of the total victims
- Among all ransomware attack groups, LockBit accounted for 49% of the activity, showing the highest activity
1.1. TOP 5 targeted countries
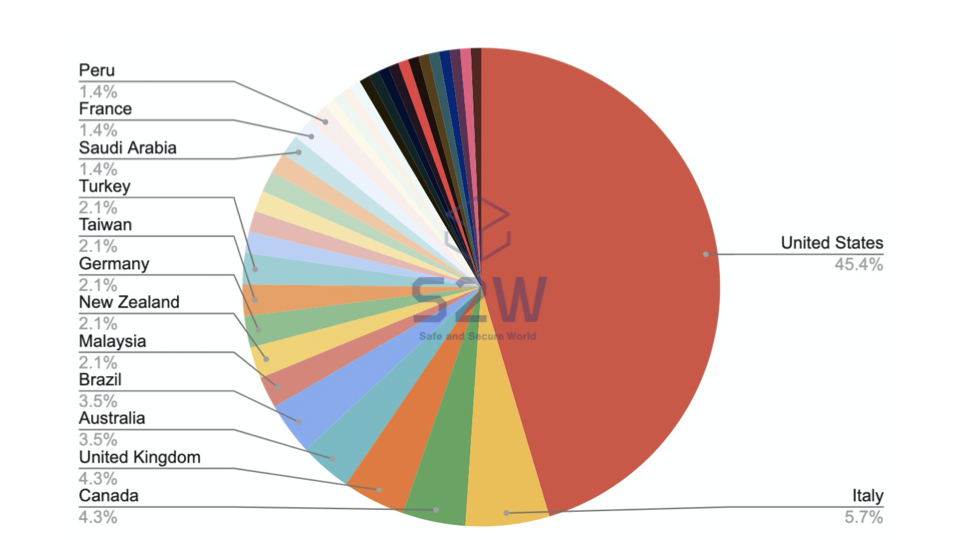
- United States — 45.4%
- Italy — 5.7%
- Canada & United Kingdom — 4.3%
- Australia & Brazil — 3.5%
- Others — 2.1%
1.2. TOP 5 targeted industrial sectors
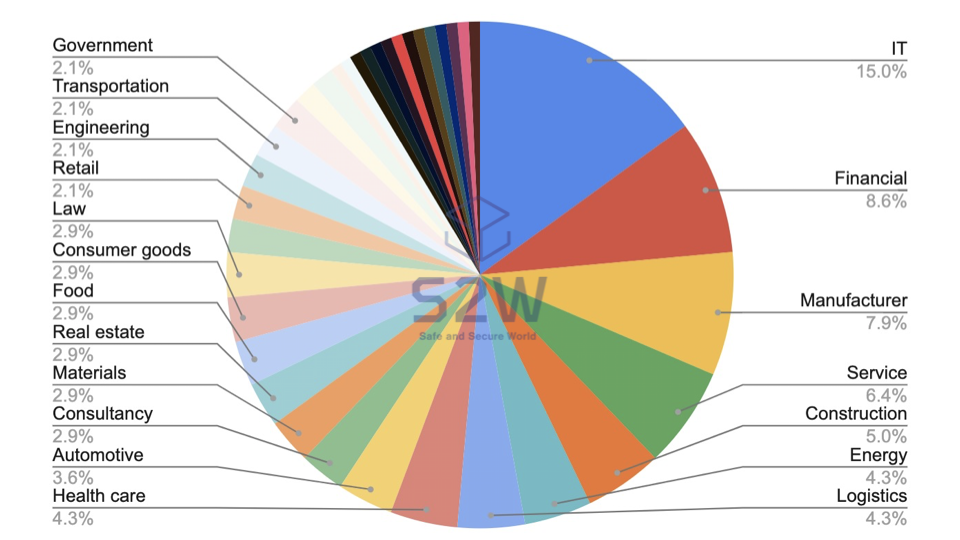
- IT — 15.0%
- Financial — 8.6%
- Manufacturer- 7.9%
- Service — 6.4%
- Construction — 5.0%
1.3. Top 5 Ransomware
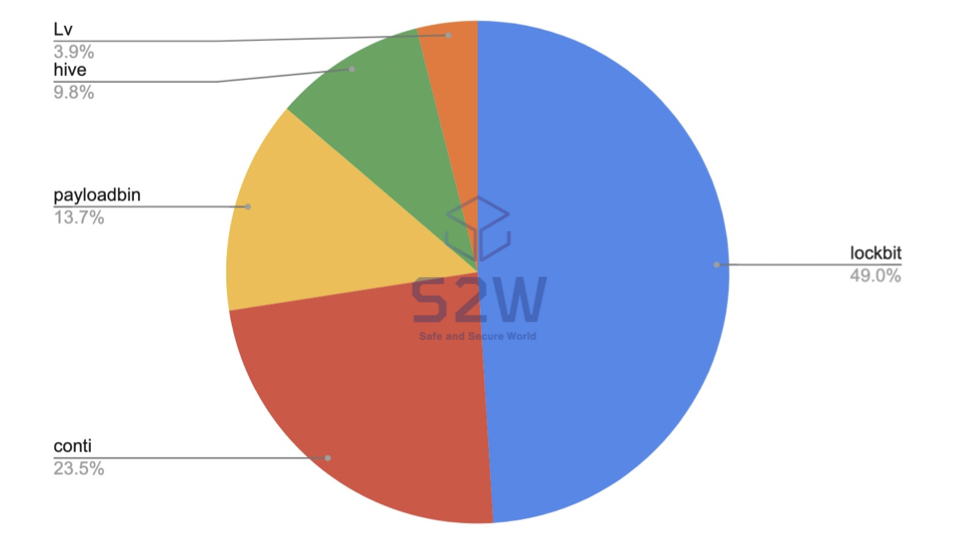
- lockbit — 49.0%
- conti — 23.5%
- payloadbin — 13.7%
- hive — 9.8%
- Lv — 3.9%
2. Posts related to Ransomware threat actors @Dark Web
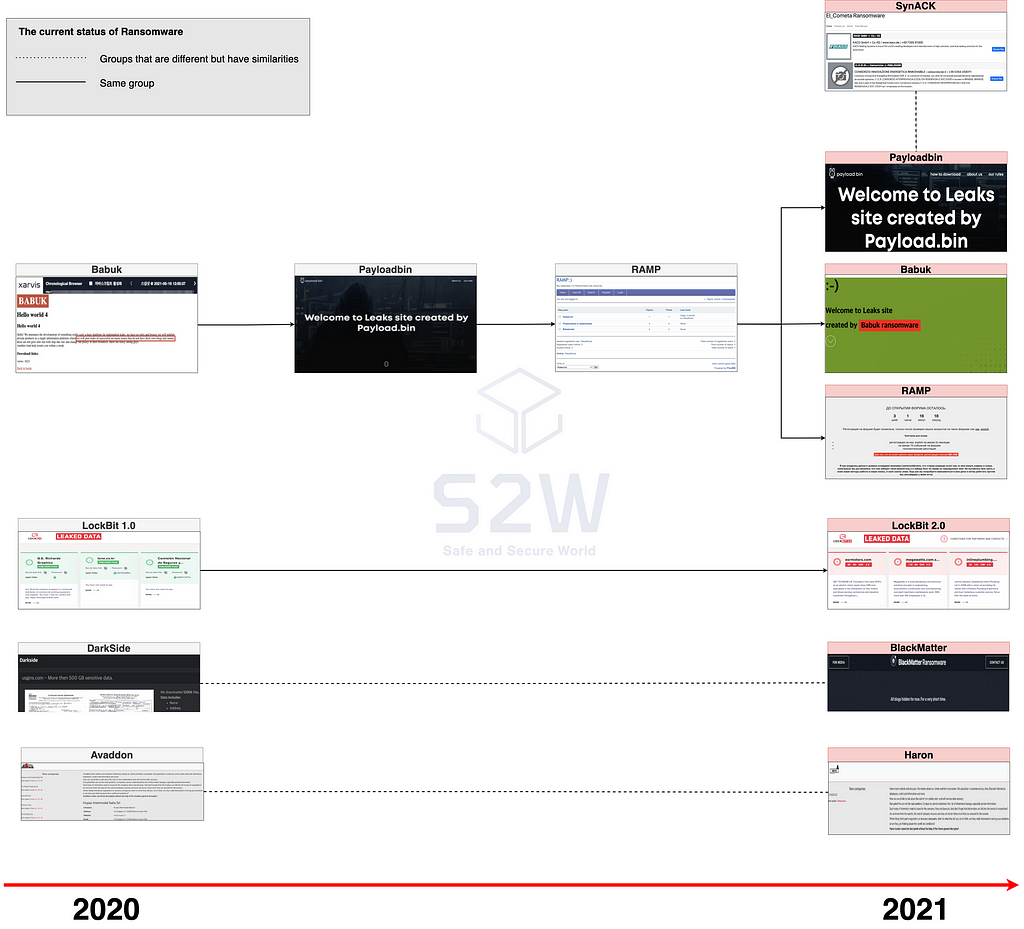
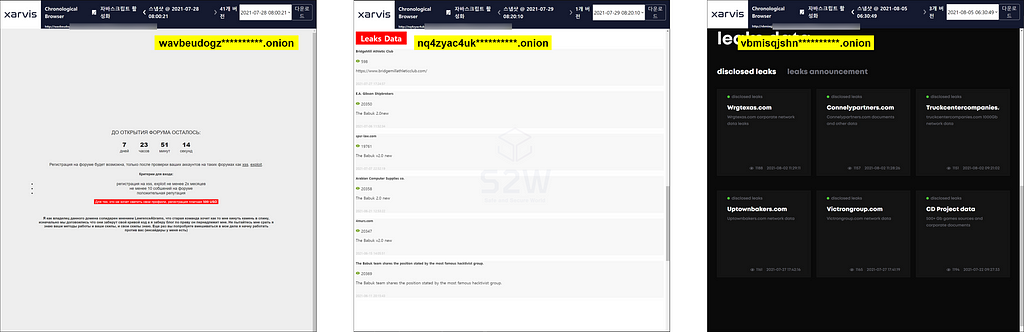
2.1. Same but different three headed ransomware Babuk (a.k.a. Payload.bin / RAMP)
- Recently, the brand name of the Babuk Leak site has undergone three changes to Babuk → Payload.bin → RAMP, and currently three brands, Babuk, Payload.bin, and RAMP, are operating on the Tor network at the same time
- The three brands are derived from the same domain, but the UI of the website and the victim company information they contain are different
2.2. Similarities Between El_Cometa (a.k.a. SynACK) and Payloadbin
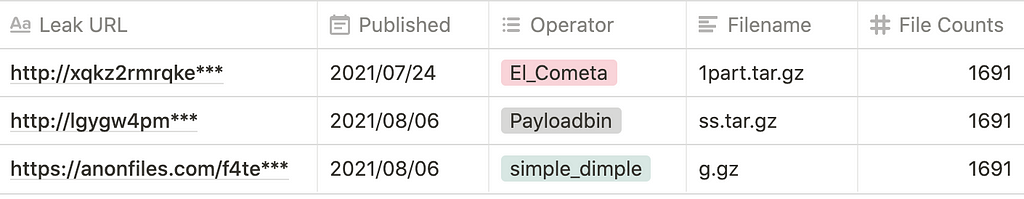
- El_Cometa and Payloadbin, known as SynACK’s rebranding, mentioned the same victim company, and it was confirmed that the leaked files related to the victim company were the same
- On the day Payloadbin released the leaked files related to the victim company, simple_dimple, a user of Raidforums, also mentioned the same victim company, and the leaked file disclosed by the user was also confirmed to be the same as the leaked file disclosed by El_Cometa and Payloadbin
Disclosed leaked files related to the same German manufacturer
Leaked File Information

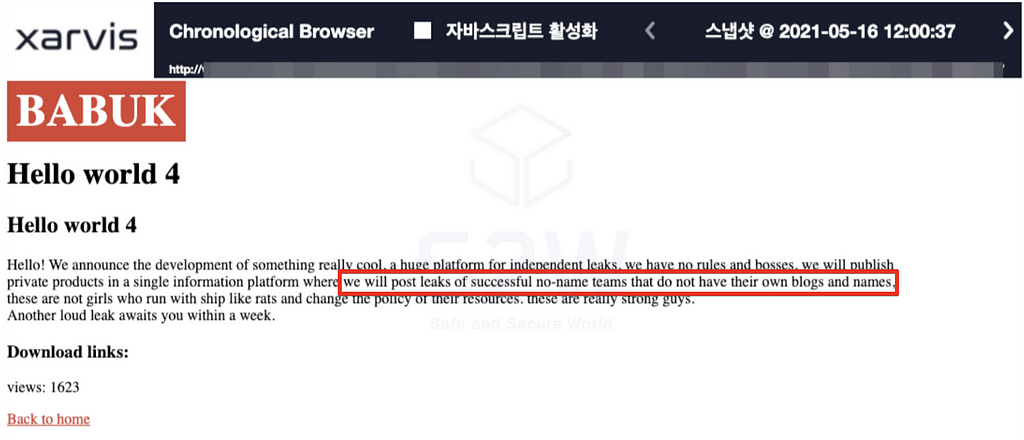
- Payloadbin mentioned in the past before rebranding from Babuk to Payloadbin that it operates the site for a ransomware attack group that doesn’t have a Leak site.
 W1 Jun | KR | Story of the week: Ransomware on the Darkweb — B. Babuk ransomware rebranded as Payload[.]bin
W1 Jun | KR | Story of the week: Ransomware on the Darkweb — B. Babuk ransomware rebranded as Payload[.]bin- For simple_dimple, Raidforums started activity on July 27, 2021 and posted the first post on August 6, 2021
2.3. AvosLocker
2.3.1. What is AvosLocker?
In July 2021, AvosLocker became known when it started posting publicity for its affiliate program with Pentester on the deep web.
Attacking not only companies but also individuals, the company encrypts the victim’s files with the “.avos” extension and at the same time installs the Azorult stealer on the infected host to steal the credentials stored in the browser.
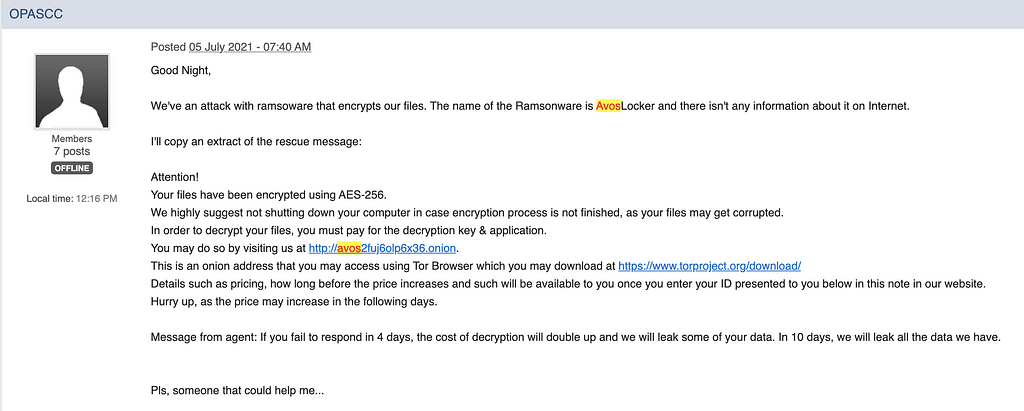 https://www.bleepingcomputer.com/forums/t/754311/ramsomware-attack-avoslocker/
https://www.bleepingcomputer.com/forums/t/754311/ramsomware-attack-avoslocker/The penetration route known so far has been confirmed to be penetration through phishing emails containing malicious code.
- In the case of phishing emails, they are mainly impersonating FedEx, payment requests, and official letters from certain companies
It has the characteristic of outputting the process of encryption on the infected PC to the command line.
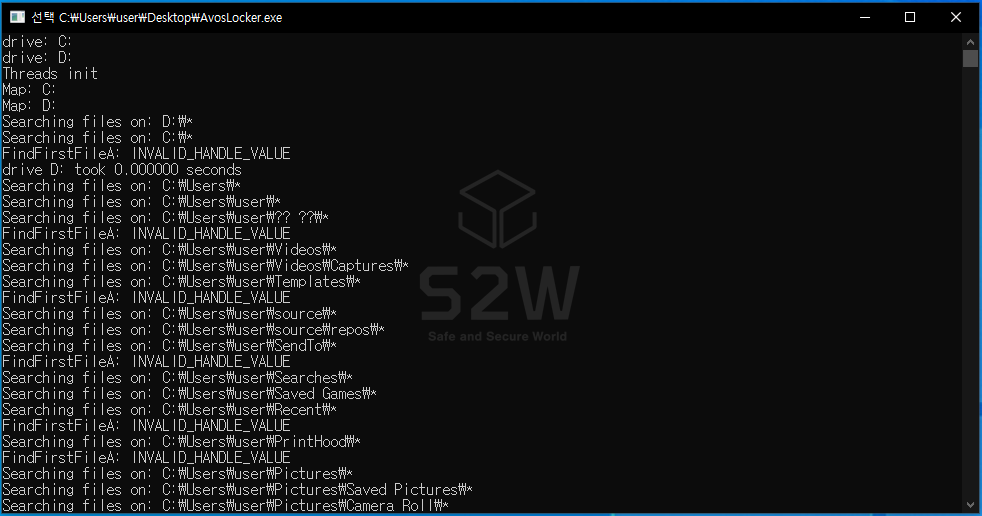
From 2021.07, you can check the history of a user named “Avos”, who is presumed to be the AvosLocker operator who started ransomware-related activities through the user activity information collected in Xarvis as below.
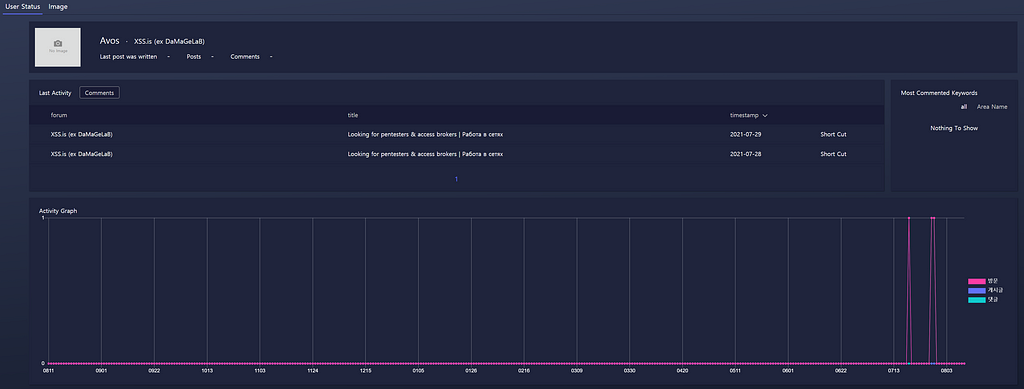
2021.07 — History of recruiting partners in Dark web
- Pentesters with experience in Active Directory networks.
- Access brokers
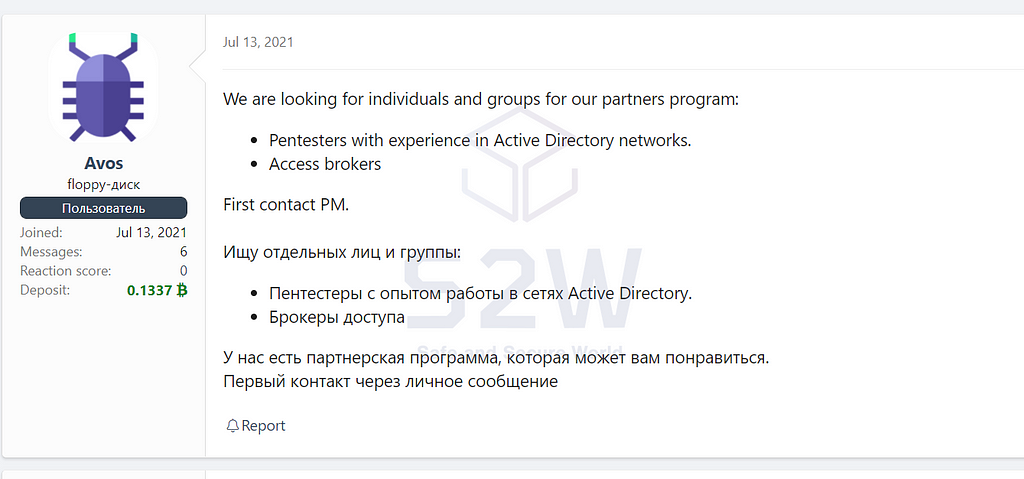
2021.07 — History of recruiting Affiliates in Dark web
2.3.2. Analysis of cases of companies that have recently been infected with AvosLocker
There was a case where the parent company was infected with AvosLocker and data was encrypted and leaked.
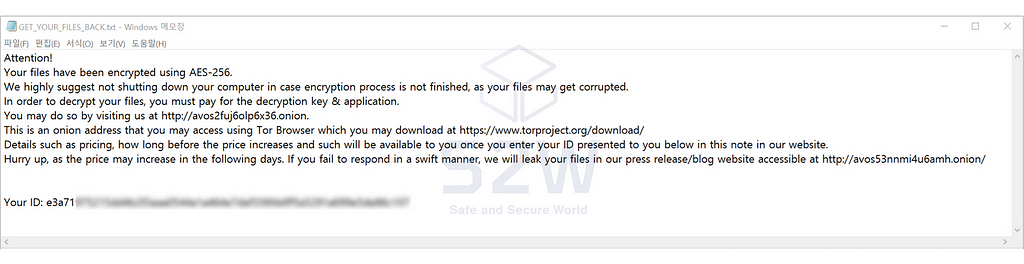
If we enter the ID value on the negotiation page, we can access the 1:1 negotiation page between the victim company and AvosLocker.


Negotiations between AvosLocker and the victim company
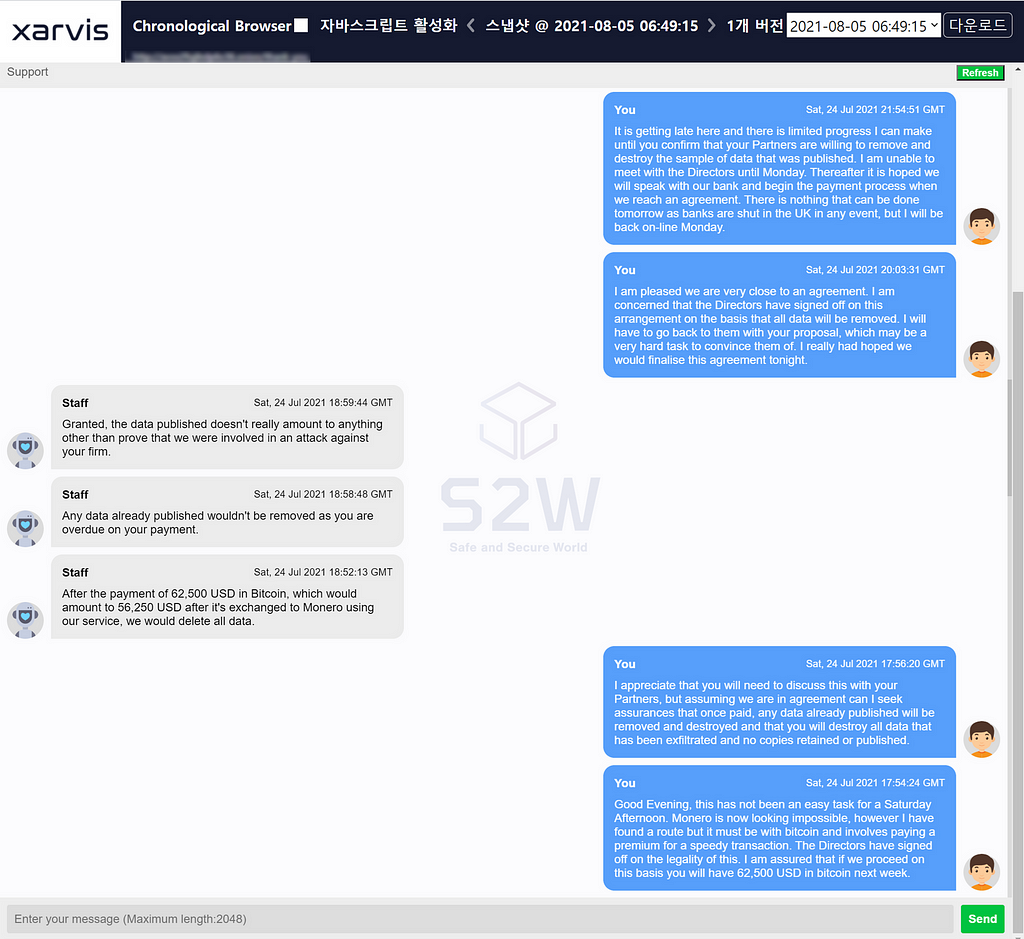
After several rounds of negotiations, the victim company offered to pay AvosLocker an amount of 62,500 USD.
Here, the person in charge of negotiating on the victim’s side said that he could lose his job due to the anti-money laundering law, and it was difficult to pay the amount using Monero.
Following the previous Suncrypt damage case, anti-money laundering laws in negotiations with ransomware appear to play a major role in driving payments to relatively easy-to-track Bitcoin instead of Monero.

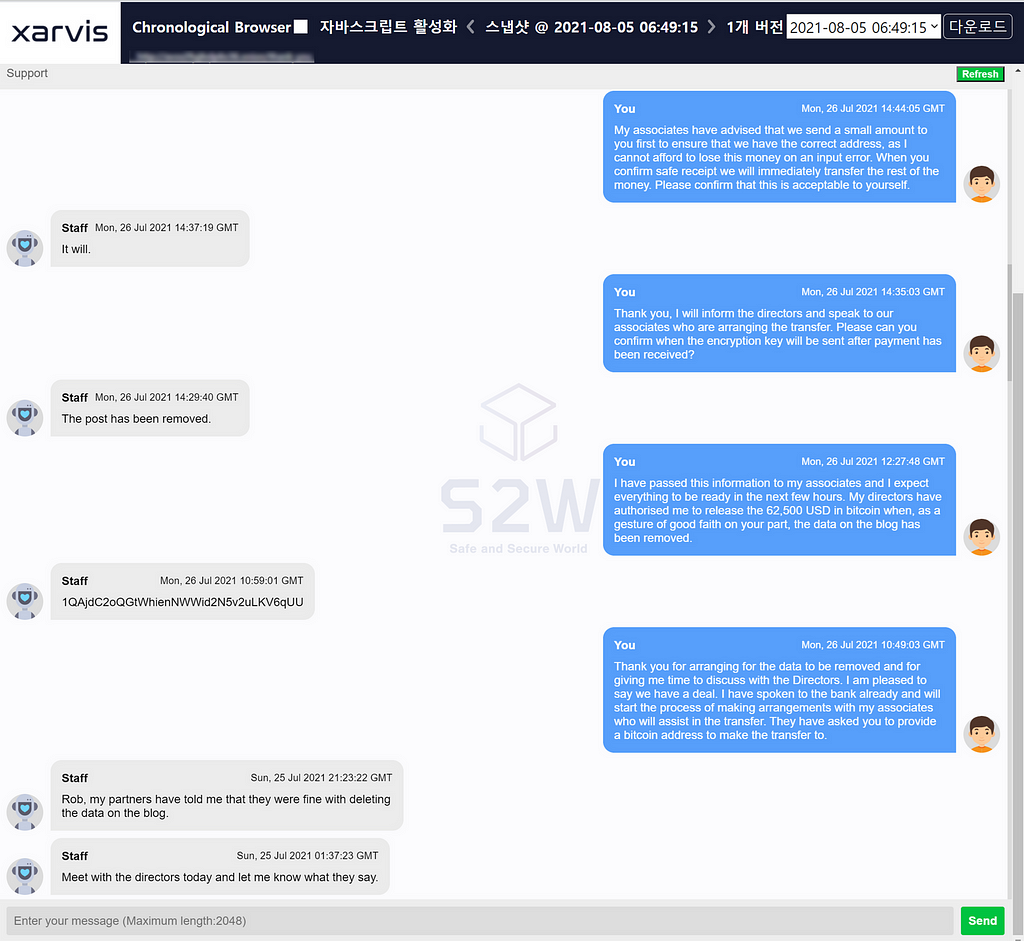
AvosLocker entices people to pay with Monero
AvosLocker explains that the Anti-Money Laundering Act KYC/AML is more about cryptocurrency withdrawals than deposits, and that buying and using Monero is legal in itself. And since paying with Bitcoin incurs an additional cost of 10%, he continued to induce them to pay with Monero.
However, the victim claimed to AvosLocker that the Monero payment was not possible after an internal review. In addition, the victim company requested to delete all leaked data published on the rick site if they paid AvosLocker.
In response, AvosLocker guarantees that upon receiving 62,500 USD worth of Bitcoin, it will be converted to Monero, and all data will be deleted after that.
AvosLocker deletes victim company data that was disclosed on the ransomware hack site and delivers the Bitcoin payment address.
- Bitcoin Payment Address : 1QAjdC2oQGtWhienNWWid2N5v2uLKV6qUU
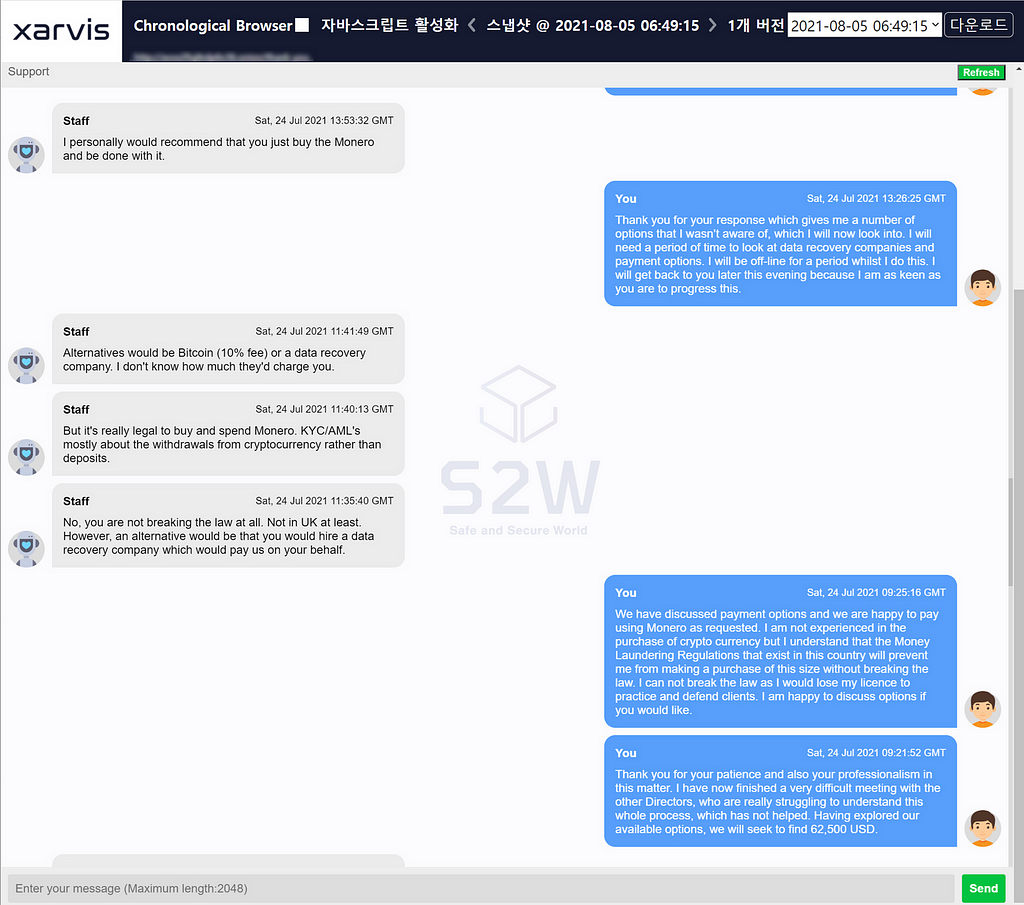
The victim company first sends a small amount of Bitcoin to check if the amount is a normal address, and then asks AvosLocker for confirmation.
- Bitcoin Payment address : 1QAjdC2oQGtWhienNWWid2N5v2uLKV6qUU
- Payment date : 2021–07–27 00:57
- Amounts : 0.0026 BTC
In response, AvosLocker told the victim that it had received an amount equivalent to about $100. The victim company, who confirmed that AvosLocker’s wallet address was valid, paid 62,500 USD worth of Bitcoin in full.
- Bitcoin Payment address : 1QAjdC2oQGtWhienNWWid2N5v2uLKV6qUU
- Payment date : 2021–07–27 19:34
- Amounts : 1.62107015 BTC

After confirming the payment, AvosLocker delivered Decrpyter to the victim company, and then deleted all data of the victim company from their servers to conclude the negotiation.
2.3.3. AvosLocker Payment Bitcoin Tracking
Checked the history of paying Bitcoin to AvosLocker and tracked the flow of funds.
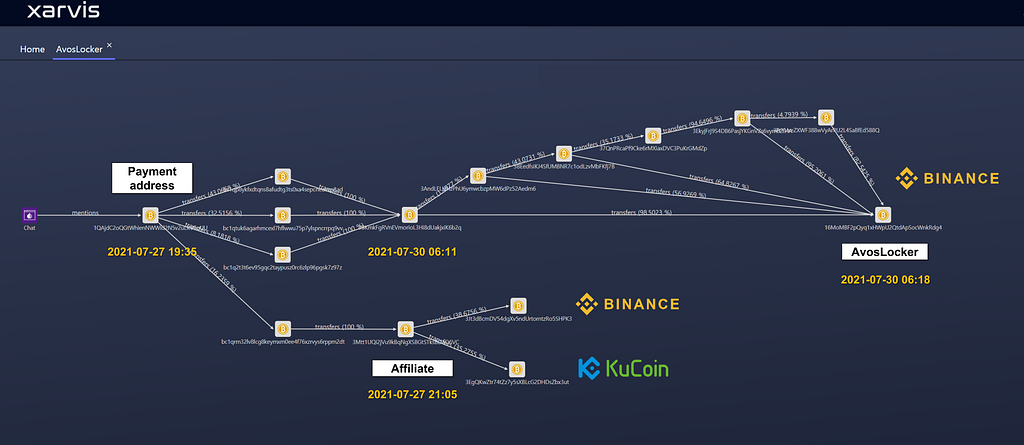
- Bitcoin Payment Address : 1QAjdC2oQGtWhienNWWid2N5v2uLKV6qUU
- Transaction date : 2021–07–27 19:35
- Amounts : 1.62107015 BTC
About 84% of the amount paid by the victim is sent to the Binance exchange wallet via several addresses.
- AvosLocker’s Binance Bitcoin Wallet : 16MoMBF2pQyq1xHWpU2QtdApSocWnkRdg4
- Transaction date : 2021–07–30 06:18
- Amounts : 1.4111839 BTC

The remaining 16% amount was moved to the address “bc1qrm32lv8lcg8keymxm0ee4f76xzrvys6rppm2dt” and then transferred to Binance and Kucoin exchanges. When looking at the ratio of the total amount divided in two, it is estimated that 84% is shared by AvosLocker operators and 16% is shared by partners.
- Affiliate Bitcoin Wallet : 3Mtt1UQi2jVu9kBqNgXSBGtSTksBDaQ6VC
- Transaction date : 2021–07–27 21:05
- Amounts : 0.2635915 BTC
In a negotiation chat with the victim company, AvosLocker said that it would change Bitcoin to Monero, but it was sent to the Binance exchange without using a separate third-party service. It is expected to exchange for Monero, which is difficult to track funds through the Binance exchange.
2.3. Conti ransomware attack manual leaked
- Conti’s partner was dissatisfied with the revenue distribution and released a manual used for ransomware attacks. It is not written in all, but it is in the form of a single manual by collecting information that is publicly available to the outside, open source tools, and vulnerability information.
- The list of leaked files is as follows:
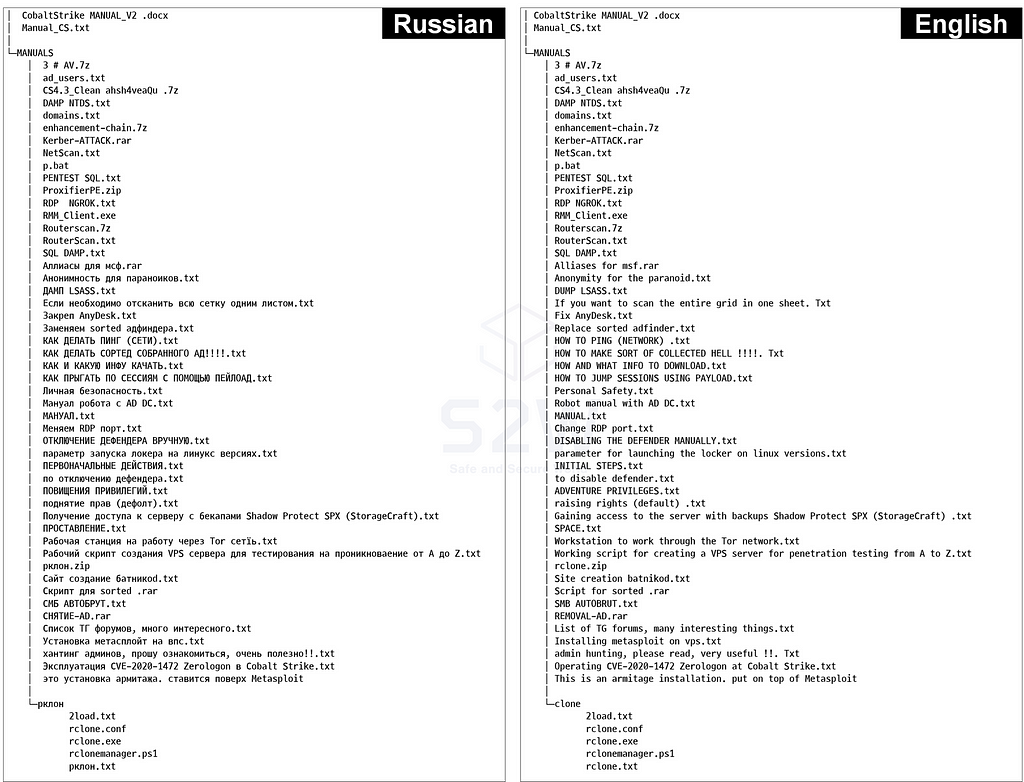
2.3.1. CobaltStrike MANUALS_V2 Active Directory.doc
- The attack procedures they carry out are based on CobaltStrike and utilize multiple tools and vulnerabilities.
- This is not much different from what was previously known, but it was characterized by a manual form reflecting the latest vulnerabilities and a method for finding an administrator account.
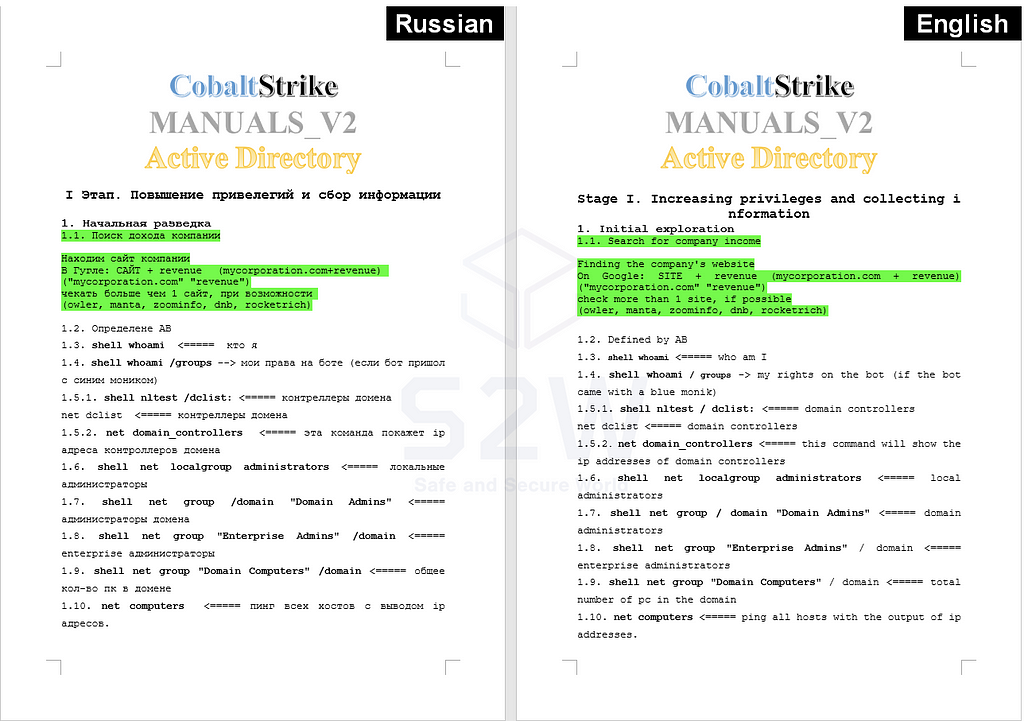
2.3.2. Vulnerability trends utilized in the Conti Ransomware Attack Manual
CVE-2021–34527, released on July 1, 2021, was applied directly to the attack and was being used.
- It is the latest vulnerability, but it is already widely known, so it is mentioned that it will be used until it becomes available.

2.3.3. Social engineering used in the final reconnaissance stage after data steal
Even after data hijacking from AD server, there is a stage (final reconnaissance) to find backup servers, NAS, etc. and steal data. At this time, Admin Hunting is performed to access the server.
- Admin Hunting refers to the process by which an attacker discovers and steals Admin-related credential information and information about infrastructure configuration in order to use Admin privileges.
After checking the list of domain administrators, classifying service accounts and non-service accounts, the last logon record of a specific user and the list of groups to which the user belongs to check whether or not there is an access right

Even if the above process is not successful, it is used to find an account with adfind after finding people related to System, Admin, Engineer, Network, and It among employees through the LinkedIn of the target company.

2.4. CryLock ransomware operators are actively recruiting for Pentester
CryLock ransomware operators a ransomware leak site called LockData, and information about 8 victims has been posted so far.
- The ransomware operator is active under the name Crylock on a Russian-based deep web forum.
2.4.1. 협력자를 구하기 위한 활동
- 2021.03.25 — Ransomware Operator Posts Hiring Cryptologists for $300
- 2021.06.15 — Updated the article asking Crpytologist for 500$ again to see if it was saved

Published the recruitment of Web coder & Designer on A, B Forum
CryLock posted an article looking for Web Developers and Designers in both forums A and B around June.
- 2021.6.17 A Forum — the recruitment of Designer
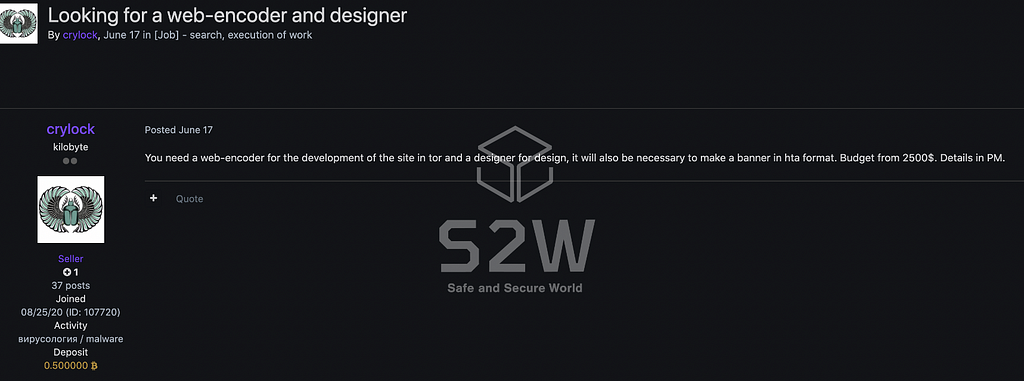
- 2021.6.16 B Forum — the recruitment of Web coder

- 2021.7.1 A Forum — the recruitment of the pentester targeting WIN Networks
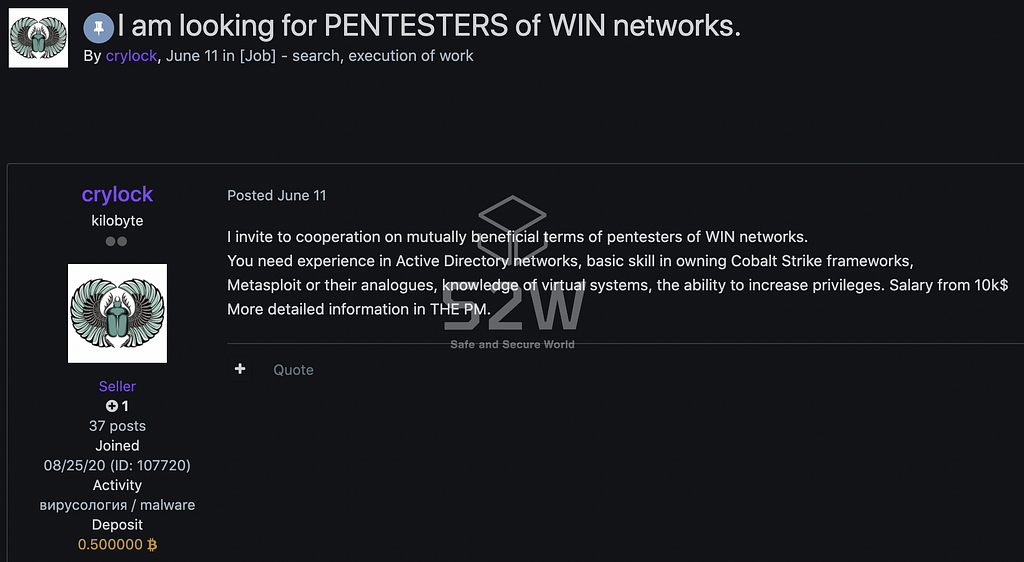
CryLock posted job postings for WIN network penetration testers around July in forum A and forum B.
Experienced in Cobalt Strike and Metasploit is required, and the salary is 10k$ or more.
- CryLock wrote a reply on (2021.7.20, 2021.7.26, 2021.8.2)
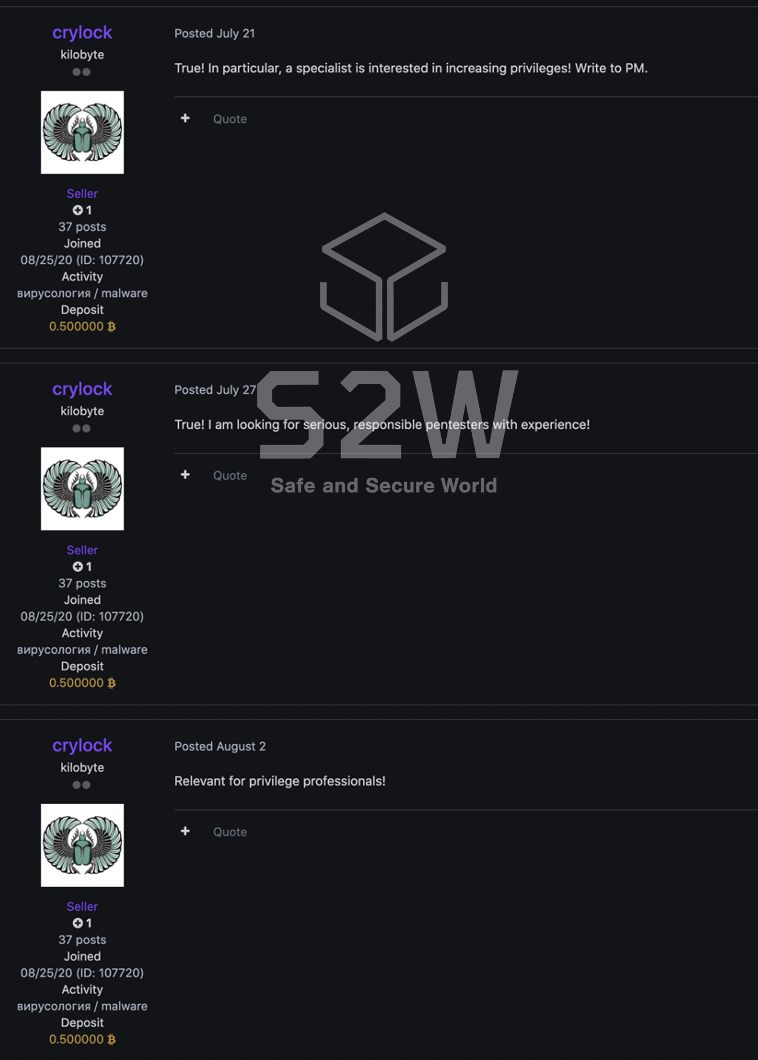
- 2021.7.27 B Forum— the recruitment of the pentester targeting WIN Networks

- It is presumed that they are recruiting users to collaborate with them by posting on forums A and B
2.4.2. Activities to search for victims — (A Forum/ B Forum)
- CryLock posted on forum A, B Forum that they purchase network access rights in relation to the company’s citrix/vpn/rdp/RDWeb/pulse around April and June, respectively.
- Among them, they said that they did not purchase information about the medical field, schools, universities, and non-profit organizations, and requested information from companies with specific conditions.
- CryLock wrote a reply on (2021.7.20, 2021.7.26, 2021.8.5)
2021.6.19 A Forum — Articles on purchasing access rights related to corporate networks

2021.4.25 B Forum — Articles on purchasing access rights related to corporate networks
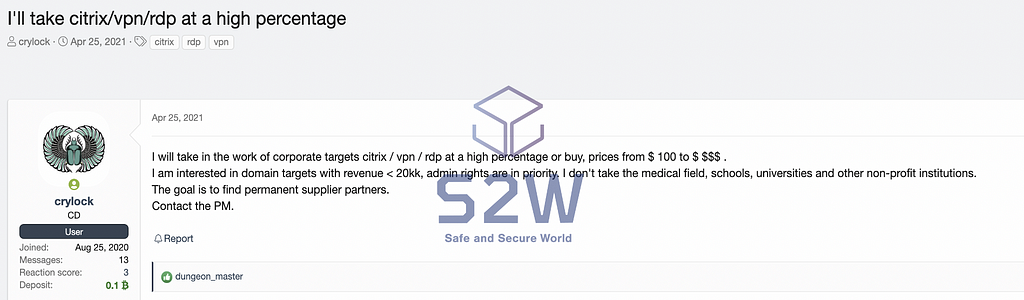
It is presumed that the ransomware operators are searching for the companies they want to attack by continuously posting on A, B Forum about purchasing access rights related to corporate networks.
Conclusion
- [Bitcoin Monitoring] It is necessary to continuously monitor the address of AvosLocker’s Binance Bitcoin wallet where the victim’s funds flowed
- [Forum monitoring] As the CryLock ransomware operator continues to recruit collaborators and actively purchase access to secure attack targets, it is necessary to continuously monitor the Russian Deep Web forum
- [Attack Prediction] The number of victimized companies in the past two weeks has been higher than usual, and as the Conti ransomware attack manual was leaked on the deep web and dark web, the activity of new or existing ransomware attack groups increased likely to do
- [Attack Prediction] According the activity of CryLock ransomware operators who are actively seeking partners, there is a possibility that the number of CryLock-related victims will increase significantly in the future compared to the activity of existing ransomware

- Homepage: https://www.s2wlab.com
- Facebook: https://www.facebook.com/S2WLAB/
- Twitter: https://twitter.com/s2wlab
[SoW] W2 Aug | EN | Story of the week: Ransomware on the Darkweb was originally published in S2W LAB BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: [SoW] W2 Aug | EN | Story of the week: Ransomware on the Darkweb | by S2W | S2W BLOG | Medium